Your Organization Already Outsources
Outsourcing is a dirty word in some circles, though, in reality, nearly all organizations outsource multiple solutions within their business – and many of them are critical to their operations. From logistics to HR, from legal to manufacturing, businesses outsource many functions. Often these functions are essential to the operation of the business, and nobody blinks an eye at outsourcing these activities.
What does outsourcing cybersecurity operations look like for my business?
Cybersecurity is an area where the arguments for outsourcing are strong, and they’re similar to the rationale for outsourcing other key functions:
- My organization can’t hire, train and retain enough cybersecurity talent.
- Cybersecurity is a cost-center, it impacts the bottom line and we need to find a more efficient model to provide comprehensive InfoSec to the company.
- Cybersecurity is complicated. There are ever-changing technologies, solutions, best practices and requirements as well as ever-increasing risks – I can’t keep up by myself.
Interestingly, the objections are also the same really:
- Cybersecurity is critical; I can’t afford to lose control of it, and I need the people to manage it.
- My cybersecurity team has to access company IP, PII and other sensitive data; I can’t entrust that to a third party.
- No third party is going to have the same sense of responsibility to my business that an internal team would.
According to the Deloitte 2019 Future of Cyber Survey, 99% of surveyed respondents outsourced at least some of their cybersecurity operations. Many businesses take a hybrid approach — outsourcing cybersecurity for certain functions and performing the others in house. And really, in the cases either for or against outsourcing, any business function could be inserted in place of cybersecurity.
What are some common misconceptions about outsourcing cybersecurity?
So why do some organizations readily outsource many essential business functions, but pause when it comes to cybersecurity? It most likely stems from some basic assumptions and misaligned expectations of what outsourcing cybersecurity can and should mean.
Outsourced cybersecurity is not an “all or nothing” proposition
Your cybersecurity program is complex. It has a number of components from strategy to architecture, engineering to operations, and may even include a compliance or two. When you think about outsourcing your cybersecurity program, know that cybersecurity companies can specialize in one aspect of cybersecurity, multiple or all of it. This means that you can pick and choose which areas are taken care of internally and offload your program’s weaknesses to your provider.
Outsourced cybersecurity should not mean outsourcing responsibility
Don’t assume that a cybersecurity provider is here to take over ownership of your security program. You will still need to provide direction and own responsibility. Your task will be to hold the provider responsible for their work and to make sure they are aligned with your business goals and objectives. As much as they may try, a provider will never be as knowledgeable about your business and its needs as you are.
Organizations that assume they are outsourcing the full responsibility for their security programs, or checking that box, are setting their outsourcing partners up for failure — and setting themselves up to have an ineffective security program. When outsourcing all or partial elements of your cybersecurity program, make sure to have a clear definition of the roles and responsibilities you are outsourcing and for the ones you are keeping.
Outsourced cybersecurity provides value even if the provider isn’t performing remediation
There’s a myth out there that only providers who resolve issues by making changes to an environment from identified security concerns are valuable. In reality, this doesn’t make much sense. Why would someone without knowledge of the day-to-day realities of your business take action in your environment? Value is therefore not solely derived from a third-party provider’s ability to “act” on information but on the ability of the provider to work with your business to sort out the actionable information from false leads and small concerns.
To find value in outsourced cybersecurity, focus instead on ensuring that your provider can feed you validated, enriched and actionable information and trust your staff to handle the resolution with their business acumen and organizational insights. If the provider is doing their job well, they’re chasing down all the false positives and red herrings and handing off the small subset of alerts that your team can and should focus on.
Outsourcing enables you to leverage best practices, harness efficient processes, tap into continuous modernization and deploy leading technologies while deepening your technical expertise. This optimizes your security spend and allows you to focus on your core business, leaving security to the experts.
Outsourced cybersecurity makes better use of the staff you have
Most security professionals agree that there aren’t enough workers to fill the needed roles as it is. ISC2’s 2019 Cybersecurity Workforce Study shows there are about 2.8 million security staffers in the top 11 world economies, with a gap of about 4.07 million staffers today, or roughly 2.5 jobs for every cybersecurity employee.
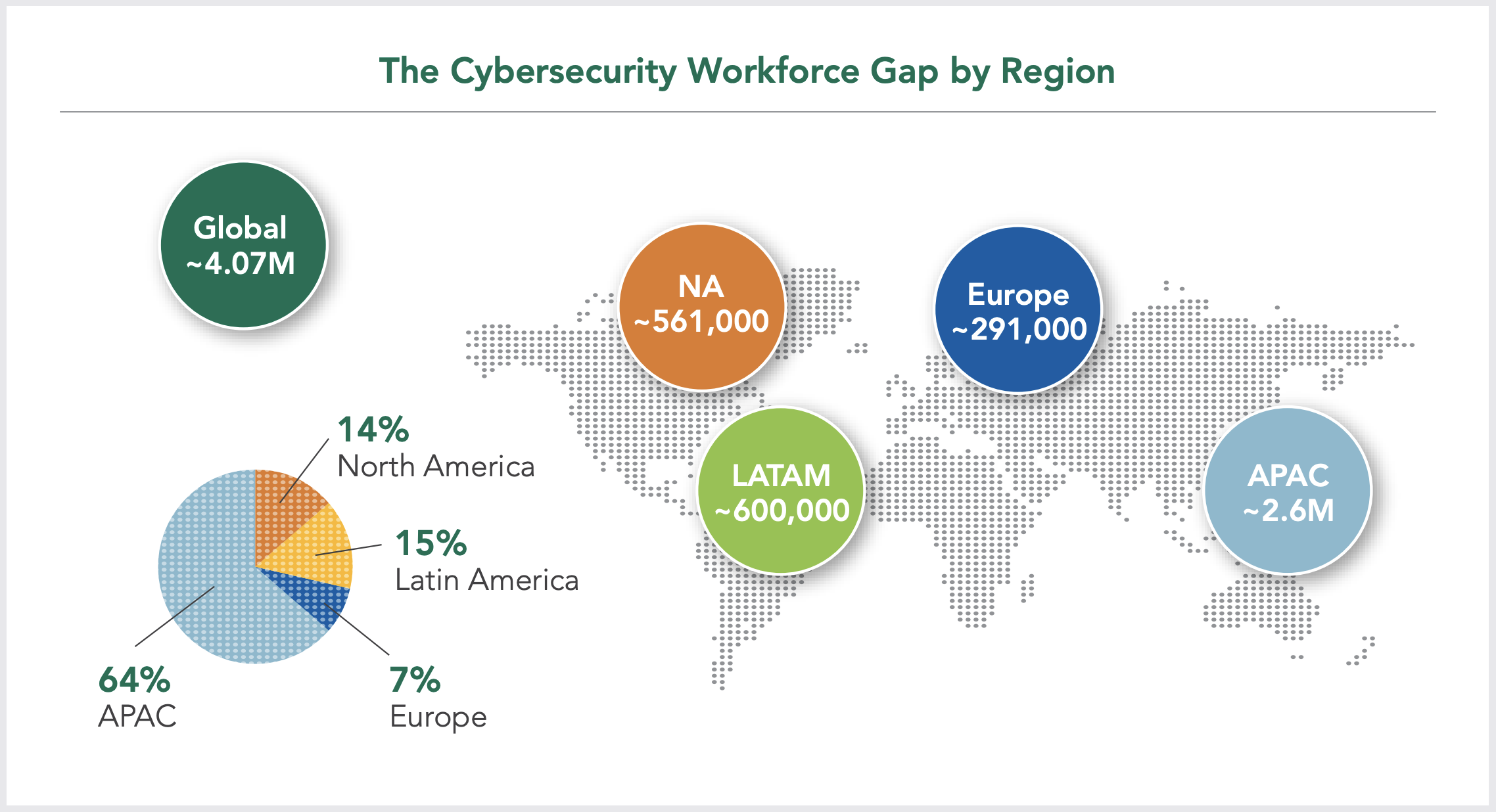
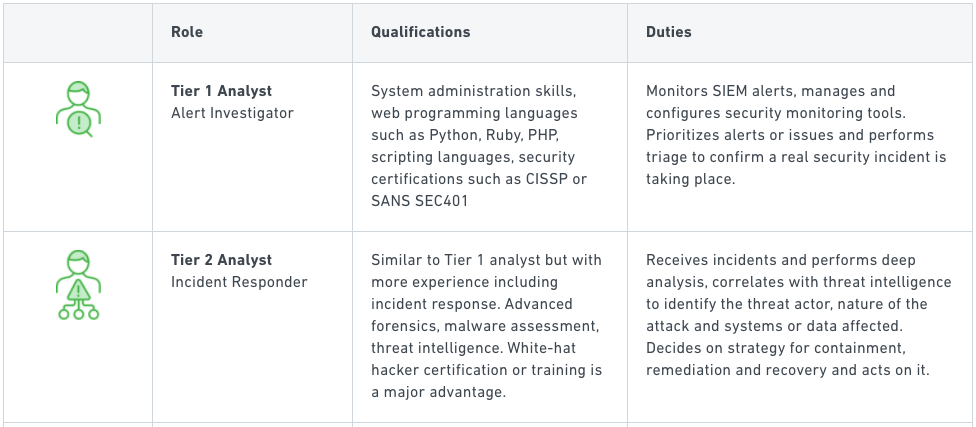
So focus on outsourcing the things that will free up your talent — the employees you’ve worked hard to train and who provide the core of your security program — to do the high-value work that you want them spending time on. Outsource Tier 1 and Tier 2 activities (see this table, courtesy of our partner Exabeam). Outsource operational activities. Outsource the selection and management of security tools and technologies. Keep the people who can make sense of all of that and help you move the security program forward.
More often than not, outsourcing will be more cost-effective than attempting to staff for yourself anyway.
Outsourced cybersecurity is about outcomes — not technologies, staffing, or resources
Nobody cares what calculators your hired accountants use. So why are you focusing on the technologies your cybersecurity provider is bringing to bear?
Instead, focus on the outcomes. Are they protecting your business? Are they alerting you only to serious threats that need to be taken care of? Have they acted quickly when threats have been detected? Are they working to fix identified vulnerabilities and build a solid line of defense? Yes? Great, no need to be worried. No? Ok, then you can talk about tools.
How can I get started outsourcing cybersecurity operations?
Outsourcing cybersecurity is going to be different for every company, just like outsourcing accounting. Some companies will just want an auditor, others will want a tax accountant and others will want a full accounting team substitute. And there are cybersecurity providers out there to match most of that spectrum.
Approach outsourcing cybersecurity the same way you would any other business-critical outsourcing decision. Have an expectation of what value and outcomes you want from your provider and keep focused on those. Be open to the expertise providers bring with them to the table and be ready to evaluate how those providers complement the existing strengths of your program to find a good fit for your organization.
If you need help figuring out the right place to start, don’t hesitate to reach out to the team here at Deepwatch. Our squad delivery model can be custom-built and filled with the exact talent and specialties you’re looking for, and our proprietary Deepwatch SCORE application helps you identify some of your first steps. Whether you need MDR, Managed EDR or Vulnerability Management, we’ll help you find the right fit. Contact us when you’re ready to outsource.
↑
Share