From MacOS Credential Theft to China’s Cyber Campaigns: Nation-State Intrusions, Ransomware Trends, and Fortinet Exploits in Focus
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
From Video Call to Credential Theft: Anatomy of a North Korean MacOS Attack
The Rundown
On May 28, 2025, a North Korean-linked cybercrime group known as BlueNoroff (also tracked as APT38, Stardust Chollima, BeagleBoyz, NICKEL GLADSTONE, among others) executed a highly targeted phishing attack via a Zoom meeting with a cryptocurrency‑related contact. During the call, the victim experienced audio difficulties and pop-up prompts indicating an “audio repair” was needed. The attacker then convinced the victim to run a script disguised as a Zoom audio fix, a malicious AppleScript that ostensibly appeared benign but contained blank lines masking dangerous commands buried deep within the code.
On executing the script, the victim unknowingly connected to a fake domain, zoom‑tech[.]us, not affiliated with Zoom, and recently registered on April 14, 2025. That domain hosted additional scripts that downloaded a second-stage payload using curl and zsh. This payload prompted the victim for local credentials, storing them temporarily before cleaning up trace. Linked WHOIS records showed that the attacker-controlled domain had siblings, suggesting a broader malicious infrastructure in play.
This attack illustrates BlueNoroff’s evolving tactics: impersonating trusted Zoom contacts, exploiting legitimate-looking domains, and using multi-stage scripts to stealthily harvest credentials. Their end goal aligns with previous campaigns—financial gain, especially within the crypto space, to benefit the North Korean regime. The sophistication of blending social engineering, domain spoofing, and stealthy script execution underscores the necessity for organizations to scrutinize unexpected script requests, verify domain legitimacy, and monitor for odd credential prompts during remote meetings.
Source Material: Field Effect
Inside the FBI’s Battle Against Chinese State-Sponsored Cyber Threats
The Rundown
The FBI is intensifying its focus on Chinese state-sponsored cyber threats, particularly from hacking groups collectively known as the “Typhoon” clusters, including Salt Typhoon and Volt Typhoon. Brett Leatherman, head of the FBI’s Cyber Division, emphasized that these intrusions are part of a long-term strategy by China to infiltrate U.S. critical infrastructure and telecommunications networks. Despite global attention on other geopolitical conflicts, Leatherman warns that China’s cyber activities continue to pose a persistent and strategic threat to national security.
Recent investigations have uncovered that Salt Typhoon has breached nine U.S. telecommunications firms, including major providers like Verizon, AT&T, and Lumen, as well as international targets such as Viasat and a Canadian telecom company. These breaches have allowed Chinese hackers to access sensitive data, including call metadata and unclassified communications of senior U.S. government officials. Leatherman notes that these cyber-espionage campaigns are not isolated incidents but part of a broader effort by China to map U.S. infrastructure and aggregate stolen data to enhance their intelligence capabilities.
The FBI’s ongoing investigations, bolstered by public tips and international collaboration, underscore the importance of vigilance against these cyber threats. Leatherman highlights that the threat from China’s cyber activities is enduring and requires continuous attention and proactive measures to safeguard national interests.
Source Materials: Recorded Future, FBI
Ransomware and Data Extortion Trends (June 17 – 23)
The Rundown
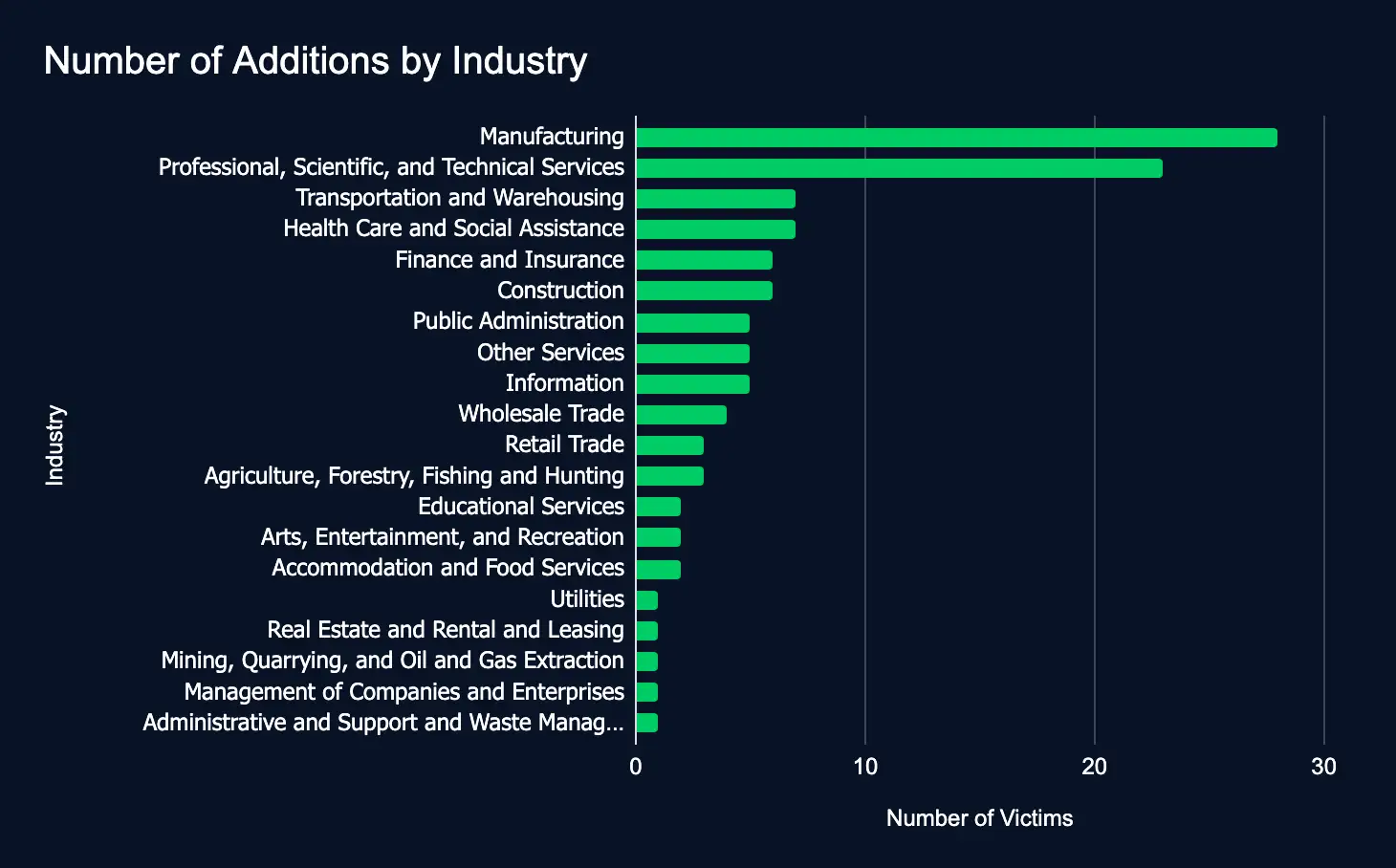
Between June 17 and 23, ransomware and data extortion activity showed a moderate uptick, with 113 victim organizations listed across 18 leak sites, a 25% increase from the previous week’s total of 88. This growth appears to indicate a stabilization in threat actor operations rather than a significant surge in attack volume.
High-value industries such as Manufacturing, Professional Services, Transportation, and Healthcare continued to be the primary focus of threat actors. The majority of impacted organizations were concentrated in key regions, notably the United States, Israel, and the United Kingdom, highlighting an ongoing emphasis on strategically important sectors and geographies.
For business leaders, this trend reinforces the persistent and targeted nature of ransomware threats. While week-to-week numbers may fluctuate, the overall pressure on critical industries remains consistent. Organizations are strongly encouraged to use this period to reassess and strengthen their cybersecurity posture, ensuring that their prevention, detection, and response strategies are tightly aligned with the evolving threat landscape.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Transportation and Warehousing
- Health Care and Social Assistance
- Most affected countries:
- United States
- Israel
- United Kingdom
- Most active leak sites:
- NightSpire
- DragonForce
- Qilin
Exploited Vulnerabilities in Fortinet, D-Link, and AMI Products Added to CISA’s Catalog
The Rundown
Between June 19 and 25, three high-impact vulnerabilities affecting products from Fortinet, D-Link, and AMI were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, confirming their use in active threat campaigns.
Unpatched, these vulnerabilities present a serious risk to organizational security, offering adversaries a direct path to initial access and potential system compromise. Given the widespread deployment of these technologies across industries, the operational and reputational consequences could be far-reaching.
With growing attention from both state-sponsored and financially motivated threat actors, immediate remediation is imperative. Delayed response significantly elevates the risk of exploitation and downstream impact.
Fortinet | FortiOS CVE-2019-6693
- Vulnerability Description: Fortinet FortiOS contains a use of hard-coded credentials vulnerability that could allow an attacker to cipher sensitive data in FortiOS configuration backup file via knowledge of the hard-coded key.
- Exploitation Details: An attacker must obtain the FortiOS configuration backup file, which can be exported via the web UI or CLI commands. The vulnerability stems from the use of a hard-coded symmetric key in the FortiOS firmware. With knowledge of this key, an attacker can decrypt the sensitive data within the configuration file. Publicly available scripts and tools have been developed to automate this decryption process.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-25
- Recommended Mitigation Due Date: 2025-07-16
D-Link | DIR-859 Router CVE-2024-0769
- Vulnerability Description: D-Link DIR-859 routers contain a path traversal vulnerability in the file /hedwig.cgi of the component HTTP POST Request Handler. Manipulation of the argument service with the input ../../../../htdocs/webinc/getcfg/DHCPS6.BRIDGE-1.xml allows for the leakage of session data, potentially enabling privilege escalation and unauthorized control of the device. This vulnerability affects legacy D-Link products. All associated hardware revisions have reached their end-of-life (EOL) or end-of-service (EOS) life cycle and should be retired and replaced per vendor instructions.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-25
- Recommended Mitigation Due Date: 2025-07-16
AMI | MegaRAC SPx CVE-2024-54085
- Vulnerability Description: AMI MegaRAC SPx contains an authentication bypass by spoofing vulnerability in the Redfish Host Interface. A successful exploitation of this vulnerability may lead to a loss of confidentiality, integrity, and/or availability.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-25
- Recommended Mitigation Due Date: 2025-07-16
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share