From ClickFix to RomCom: Deceptive Delivery Tactics, WinRAR Exploits, and Ransomware Escalation Fuel New Wave of Targeted Attacks
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Deception as Delivery: The ClickFix Technique Behind a Full Command and Control Takeover
- RomCom Exploits WinRAR Zero-Day to Deliver Targeted Backdoors via Spearphishing Campaigns
- Ransomware and Data Extortion Trends (August 5 – 11)
- Exploited Vulnerabilities in RARLAB, Microsoft, and N-Able Products Added to CISA’s Catalog
Deception as Delivery: The ClickFix Technique Behind a Full Command and Control Takeover
The Rundown
FortiGuard Labs recently discovered a sophisticated cyberattack campaign called “From ClickFix to Command” that targeted Israeli businesses and infrastructure. The attackers used phishing emails that appeared to come from trusted internal sources and contained themes related to medical supplies and wartime support. These emails directed recipients to a fake Microsoft Teams login page that instructed them to open the Windows Run dialog and enter a PowerShell command. This social engineering method, known as ClickFix, triggered the full attack chain using only PowerShell commands, eliminating the need for downloading any executable files.
After the initial command was run, a multi-stage PowerShell attack sequence began. The first stage involved downloading an HTML file that contained embedded binary code. A second script parsed and decoded this binary content using a technique labeled as “kendrick” which ultimately led to the reconstruction and execution of a Remote Access Trojan (RAT). The RAT communicated with a command and control server named pharmacynod[.]com using encrypted and obfuscated data formats including compressed and reversed Base64 encoding. This approach made the malicious traffic blend in with legitimate network activity and helped it bypass many traditional security defenses.
This attack highlights the growing sophistication of modern cyber threats, where adversaries no longer rely on traditional malware or obvious file downloads. Instead, they use trusted tools like PowerShell and clever social engineering to quietly infiltrate networks. The campaign appears to align with the tactics of MuddyWater, a known threat group linked to Iranian state-sponsored activity. Their goal is often espionage or disruption, and by exploiting trust and internal communication channels, they can bypass many security controls. This underscores the importance of user awareness, layered defenses, and proactive monitoring to detect and stop these stealthy intrusions.
Source Material: Fortiguard Labs
RomCom Exploits WinRAR Zero-Day to Deliver Targeted Backdoors via Spearphishing Campaigns
The Rundown
A critical security vulnerability in WinRAR, a popular file compression tool, has recently been discovered and actively exploited by the Russian-aligned cyberespionage group RomCom. The flaw, tracked as CVE-2025-8088, allows hackers to hide malicious files within seemingly harmless compressed archives, such as fake job application documents. When a user extracts these files, harmful software is silently deployed to key areas of the computer, potentially giving attackers long-term access and control. ESET researchers identified this activity in mid-July 2025, and a patched version of WinRAR (7.13) was released on July 30 to close this security hole.
RomCom targeted companies in finance, manufacturing, defense, and logistics sectors across Europe and Canada, using spearphishing emails to distribute the infected archives. Their malware delivered advanced backdoor tools like Mythic, SnipBot, and RustyClaw, which are capable of stealing sensitive data and installing additional malware. These attacks were highly targeted, using tactics like checking if the victim’s company name matches pre-programmed values to ensure only specific organizations were compromised. The attackers also included misleading file names and deliberately crafted error messages to avoid detection.
This marks at least the third time RomCom has exploited a zero-day vulnerability in real-world attacks, underscoring their sophistication and geopolitical motives. The group is believed to have conducted extensive reconnaissance before launching these operations. In addition to RomCom, another unidentified actor began exploiting the same vulnerability shortly after. This incident reinforces the need for businesses to keep software up to date and remain vigilant against advanced phishing techniques. Organizations using WinRAR or related tools should urgently update to the latest version to mitigate this risk.
Source Materials: ESET
Ransomware and Data Extortion Trends (August 5–11)
The Rundown
Between August 5 and 11, ransomware and data extortion incidents impacted 76 organizations across 21 leak sites, marking an approximate 49% increase from the previous week’s total of 51. While this uptick could suggest heightened ransomware activity, it more likely reflects a short-term surge in threat actor operations rather than a sustained escalation in attack frequency.
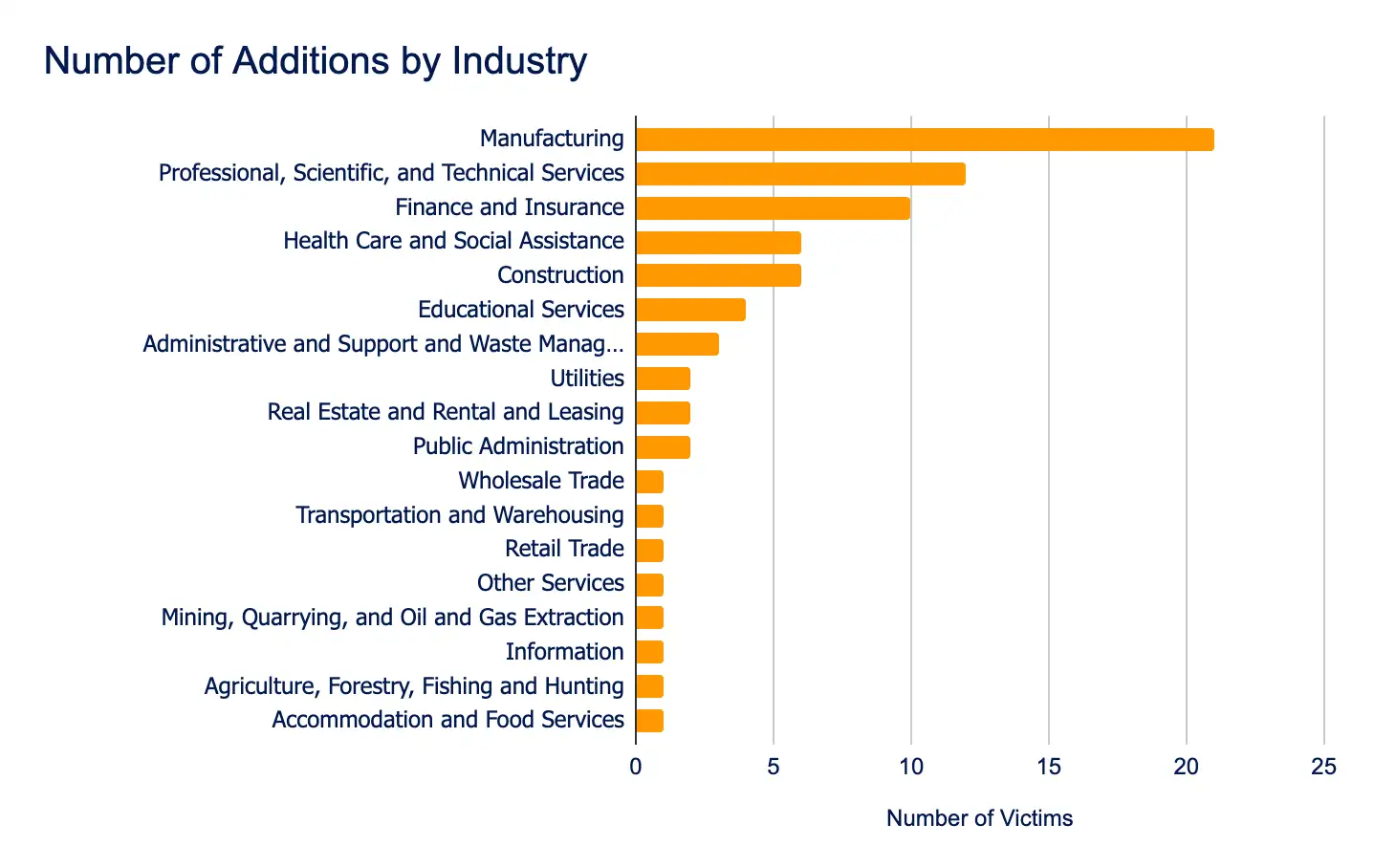
Manufacturing, Professional Services, and Finance and Insurance sectors remained the most heavily targeted, underscoring the continued focus on high-value, disruption-prone industries. Geographically, the United States, the United Kingdom, and Germany saw the highest number of incidents, reinforcing threat actors’ concentration on strategically significant markets.
For business leaders, these patterns highlight the calculated and persistent nature of ransomware campaigns. Despite periodic shifts in weekly volume, the overall threat landscape remains volatile, emphasizing the importance of sustained investment in comprehensive prevention, detection, and incident response capabilities.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Finance and Insurance
- Most affected countries:
- United States
- United Kingdom
- Germany
- Most active leak sites:
- Qilin
- Play
- DragonForce
- D4rk4rmy
Exploited Vulnerabilities in RARLAB, Microsoft, and N-Able Products Added to CISA’s Catalog
The Rundown
Between August 7 and August 13, CISA added five critical vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, affecting widely used products from RARLAB, Microsoft, and N-Able. These flaws have been confirmed as actively exploited in diverse threat campaigns.
If left unpatched, the vulnerabilities pose severe risks, including unauthorized access and privilege escalation, jeopardizing the confidentiality, integrity, and availability of impacted systems. Successful exploitation could lead to significant operational disruptions, data compromise, and lasting reputational damage.
Given the growing interest from both nation-state actors and financially motivated threat groups, immediate remediation is imperative. Delayed action substantially increases the likelihood of compromise and could trigger cascading impacts across interconnected IT and operational environments.
RARLAB | WinRAR CVE-2025-8088
- Vulnerability Description: RARLAB WinRAR contains a path traversal vulnerability affecting the Windows version of WinRAR. This vulnerability could allow an attacker to execute arbitrary code by crafting malicious archive files.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions
- Date Added to catalog: 2025-08-12
- Recommended Mitigation Due Date: 2025-09-02
Microsoft | Office CVE-2007-0671
- Vulnerability Description: Microsoft Office Excel contains a remote code execution vulnerability that can be exploited when a specially crafted Excel file is opened. This malicious file could be delivered as an email attachment or hosted on a malicious website. An attacker could leverage this vulnerability by creating a specially crafted Excel file, which, when opened, allows an attacker to execute remote code on the affected system.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-12
- Recommended Mitigation Due Date: 2025-09-02
Microsoft | Internet Explorer CVE-2013-3893
- Vulnerability Description: Microsoft Internet Explorer contains a memory corruption vulnerability that allows for remote code execution. The impacted products could be end-of-life (EoL) and/or end-of-service (EoS). Users should discontinue product utilization.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-12
- Recommended Mitigation Due Date: 2025-09-02
N-able | N-Central CVE-2025-8875, CVE-2025-8876
- Vulnerability Description:
- CVE-2025-8875: N-able N-Central contains an insecure deserialization vulnerability that could lead to command execution.
- CVE-2025-8876: N-able N-Central contains a command injection vulnerability via improper sanitization of user input.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-13
- Recommended Mitigation Due Date: 2025-08-20
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
Share