From npm Infiltration to Federal Exposure: Shai-Hulud Supply Chain Attack, Ransomware Trends, and Critical Cisco & Google Exploits Highlight Security Gaps
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Shai-Hulud: A Self-Propagating Supply Chain Attack on npm
The Rundown
In September 2025, security researchers uncovered a large-scale supply chain attack targeting the JavaScript ecosystem through the npm registry. Malicious versions of popular npm packages were uploaded with hidden code designed to steal sensitive data such as environment variables, credentials, and access tokens, then send them to GitHub repositories controlled by the attacker under the name “Shai-Hulud.” The attack was particularly dangerous because it behaved like a worm: once it obtained npm tokens, it could automatically spread by publishing further compromised packages, amplifying its reach across the ecosystem.
The seriousness of this incident lies not only in its ability to spread quickly but also in the scale of exposure it created. Because npm is a core part of modern software development, the compromised packages had the potential to affect thousands of organizations, including businesses that rely heavily on open-source code in their products or infrastructure. The fact that attackers were able to leverage stolen tokens and create new public repositories means that both private company code and sensitive secrets were at risk of being leaked or misused.
For businesses, the risks are significant. Stolen credentials and exposed private repositories could lead to unauthorized access, data loss, and follow-on attacks against corporate infrastructure. Organizations using npm must urgently remove compromised package versions, rotate any potentially exposed secrets (GitHub and npm tokens, API keys, etc.), and review their systems for suspicious repositories or accounts linked to “Shai-Hulud.” Strengthening supply chain defenses, auditing CI/CD pipelines, and tightening monitoring for unusual publishing activity are essential steps to prevent further exposure and maintain customer trust.
Source Material: Wiz
CISA Lessons Learned: How a Federal Breach Exposed Gaps in Patching and Response
The Rundown
The Cybersecurity and Infrastructure Security Agency (CISA) recently published an after-action advisory based on its incident response to a cybersecurity breach at a U.S. federal civilian agency. The breach began when threat actors exploited a publicly known vulnerability (CVE-2024-36401) in GeoServer, 11 days after its disclosure in one instance and 25 days in another. The attackers used that access to move laterally through the network, deploy web shells, escalate privileges, and establish command-and-control infrastructure. The agency’s defensive tools eventually picked up an alert from a compromised SQL server after three weeks of undetected activity.
From its investigation, CISA extracted three core lessons. First, patching delays proved critical: the exploited vulnerability had been publicly disclosed, and even cataloged by CISA’s Known Exploited Vulnerabilities (KEV) list, but remained unremediated in time. Second, the agency’s incident response plan (IRP) was neither well tested nor flexible enough to quickly onboard external responders or grant them access to tools, which impeded swift action. Third, alerting and monitoring gaps existed: Endpoint Detection & Response (EDR) alerts were not continuously reviewed, and key public-facing systems weren’t fully protected, which allowed the threat actors to remain inside the environment for weeks.
To address these deficiencies, CISA recommends a set of mitigations aligned with best practices and performance goals. Key actions include prioritizing and accelerating patching, especially for known exploited vulnerabilities, maintaining and exercising a living incident response plan (including external assistance procedures), and deploying robust, centralized logging and alert monitoring systems (e.g. SIEMs) to detect anomalous behavior. CISA also advises continuous validation of security controls by testing them against known threat techniques (as mapped in the MITRE ATT&CK framework).
Source Material: DHS CISA
Ransomware and Data Extortion Trends (September 16 – 22)
The Rundown
From September 16 to 22, ransomware and data extortion incidents were reported across 24 leak sites, impacting 94 organizations. This represents a 26% decline from the 127 cases recorded the prior week. However, rather than indicating a genuine downturn in malicious activity, this dip is more plausibly attributed to a short-term pause or operational regrouping by threat actors, rather than a lasting reduction in campaign intensity.
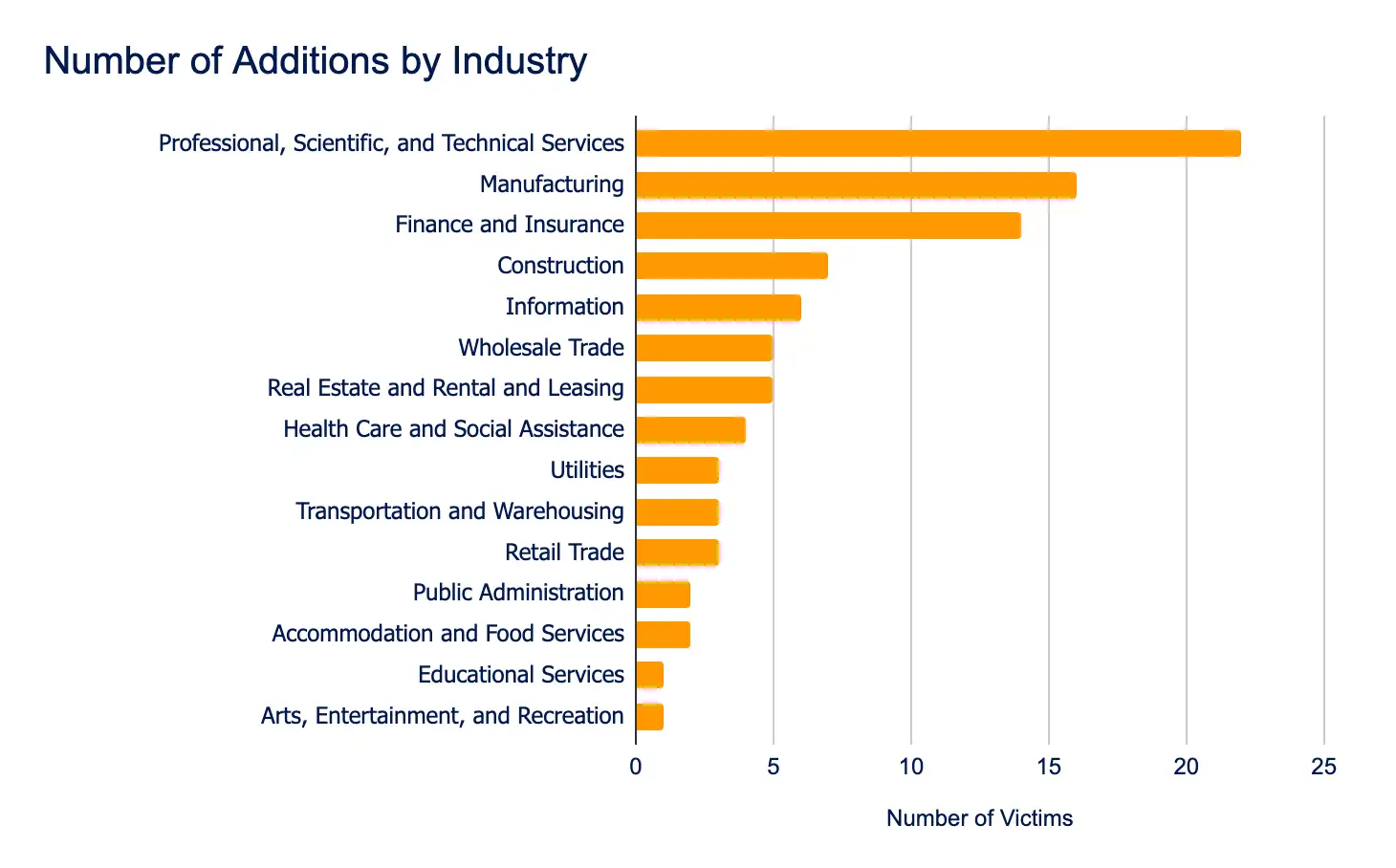
The Professional Services, Manufacturing, and Finance and Insurance sectors remained the most frequently targeted, reflecting continued adversary focus on high-value, disruption-prone industries. From a geographic perspective, the United States, South Korea, the Netherlands, and Germany experienced the highest volume of incidents, underscoring ransomware operators’ prioritization of strategically significant markets.
For business leaders, these patterns highlight the deliberate and persistent nature of ransomware campaigns and reinforce the importance of sustained investment in robust prevention, detection, and incident response capabilities.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Finance and Insurance
- Most affected countries:
- United States
- South Korea
- Netherlands
- Germany
- Most active leak sites:
- Qilin
- Play
- Akira
Exploited Vulnerabilities in Cisco and Google Products Added to CISA’s Catalog
The Rundown
Between September 18 and 25, CISA added three critical vulnerabilities affecting Cisco and Google products to its Known Exploited Vulnerabilities (KEV) catalog, confirming their active use in diverse threat campaigns. If unpatched, these flaws could allow unauthorized access and privilege escalation, jeopardizing the confidentiality, integrity, and availability of impacted systems.
Exploitation of these vulnerabilities carries the potential for operational disruption, data compromise, and long-term reputational harm. Given the heightened interest from both nation-state adversaries and financially motivated actors, prompt remediation is essential. Any delay significantly elevates the likelihood of compromise and increases the risk of cascading impacts across interconnected IT and operational environments.
Cisco | Secure Firewall Adaptive Security Appliance and Secure Firewall Threat Defense CVE-2025-20362
- Vulnerability Description: Cisco Secure Firewall Adaptive Security (ASA) Appliance and Secure Firewall Threat Defense (FTD) Software VPN Web Server contain a missing authorization vulnerability. This vulnerability could be chained with CVE-2025-20333.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions
- Date Added to catalog: 2025-09-25
- Recommended Mitigation Due Date: 2025-09-26
Cisco | Secure Firewall Adaptive Security Appliance and Secure Firewall Threat Defense CVE-2025-20333
- Vulnerability Description: Cisco Secure Firewall Adaptive Security (ASA) Appliance and Secure Firewall Threat Defense (FTD) Software VPN Web Server contain a buffer overflow vulnerability that allows for remote code execution. This vulnerability could be chained with CVE-2025-20362.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions
- Date Added to catalog: 2025-09-25
- Recommended Mitigation Due Date: 2025-09-26
Google | Chromium V8 CVE-2025-10585
- Vulnerability Description: Google Chromium contains a type confusion vulnerability in the V8 JavaScript and WebAssembly engine.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions
- Date Added to catalog: 2025-09-23
- Recommended Mitigation Due Date: 2025-10-14
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Share