In today’s digital world, the cybersecurity battlefield has dramatically shifted. Organizations can no longer afford to rely on detection and response alone. Adversaries are growing faster, stealthier, and more capable—employing artificial intelligence, automation, and advanced evasion techniques to exploit even the smallest gaps in security defenses. In response, a new and powerful model is emerging: Preemptive MDR (Preemptive Security in Managed Detection and Response).
At the forefront of this transformation is Deepwatch, a leading innovator in MDR solutions. Deepwatch is redefining what’s possible in cybersecurity by not just reacting to threats, but anticipating, validating, and neutralizing them—before they cause harm.
The Shift Toward Preemptive MDR
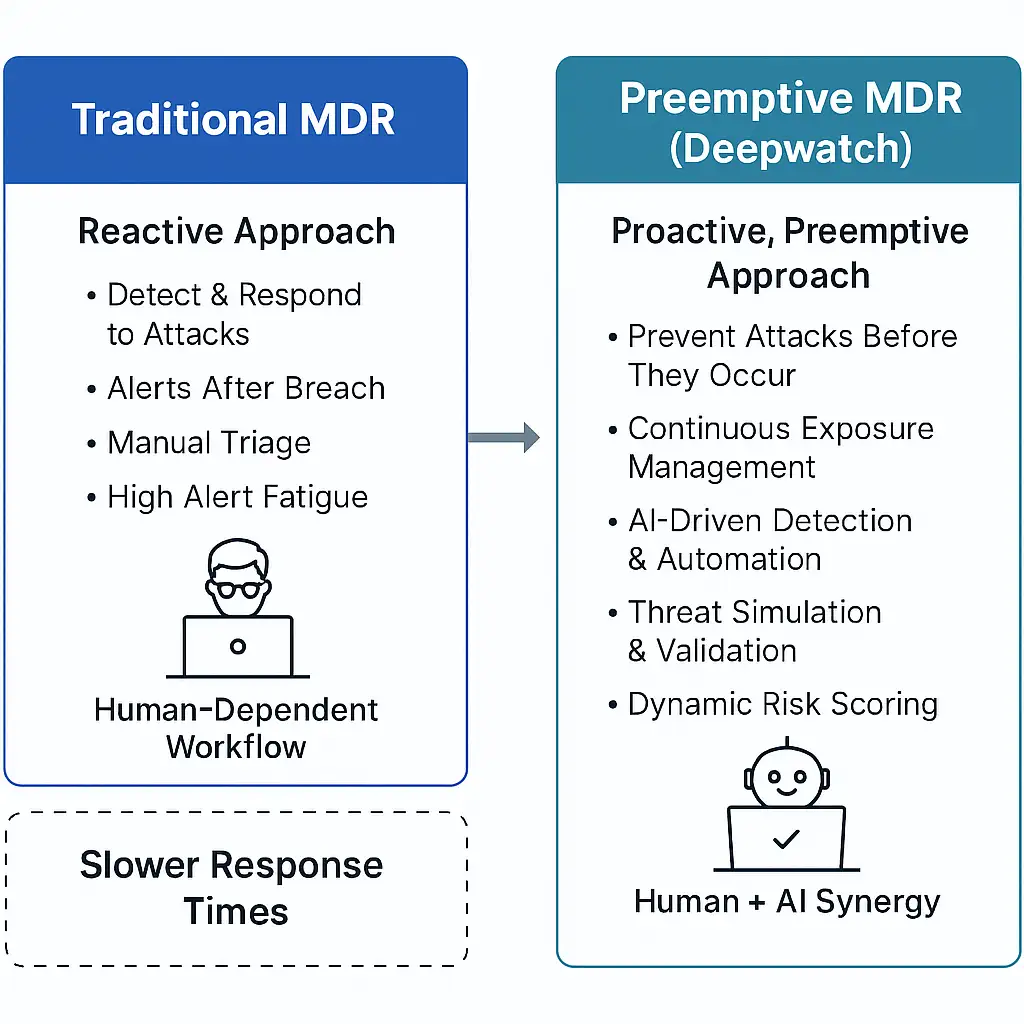
Traditional MDR is a reactive model, designed to identify threats once they’ve already penetrated the infrastructure. It focuses on real-time detection, alerting, and response. While effective to an extent, this model assumes that compromise is inevitable—and that damage control is the end goal.
Preemptive MDR flips that paradigm. Instead of simply reacting, preemptive security solutions proactively analyze, simulate, and harden defenses continuously. They integrate cutting-edge technologies like threat simulation, continuous exposure management, AI-powered analytics, and automated threat prevention, all aimed at identifying and resolving vulnerabilities before attackers can exploit them.
This model is becoming essential as the cyber threat landscape evolves. Several trends are accelerating the need for preemptive MDR:
- AI-powered attacks that adapt in real time and move at machine speed
- A rapidly expanding attack surface from cloud services, remote work, and IoT
- Security talent shortages that limit internal response capabilities
These challenges require a more agile, intelligent, and proactive defense strategy—and that’s exactly where Deepwatch excels.
Visualizing the Evolution: Traditional MDR vs. Preemptive MDR
How Preemptive MDR Works
Preemptive MDR doesn’t replace traditional detection and response; it enhances and extends it by building resilience before the breach. This approach includes:
1. Continuous Threat Exposure Management
This involves constantly assessing an organization’s environment for vulnerabilities, misconfigurations, and security control gaps. Instead of waiting for an exploit, Deepwatch identifies potential exposures and prioritizes remediation based on real risk factors.
2. Threat Simulation and Validation
By simulating adversary behavior, Deepwatch validates whether security controls are actually effective. It’s like running fire drills—testing every layer of defense to ensure readiness under real-world conditions.
3. Dynamic Risk Scoring
Deepwatch uses AI and behavioral analytics to assign dynamic risk scores to users, endpoints, and assets. This scoring enables more accurate prioritization and automated response workflows based on real-time context.
4. Automated Threat Prevention
By integrating tools that block threats at inception—such as memory protection, process isolation, and adaptive exposure controls—Deepwatch stops many threats before they reach the detection stage.
This multi-layered preemptive approach not only reduces attack success rates but also improves efficiency, cuts down false positives, and empowers lean security teams to act with greater precision.
Why Deepwatch is Leading the Charge for Preemptive MDR
Deepwatch isn’t just adapting to this evolution in MDR—it’s driving it. Through a unique blend of technology, talent, and threat intelligence, Deepwatch offers a fully integrated preemptive security experience.
Here’s how:
- AI-Driven Automation: Deepwatch leverages artificial intelligence to automate more than 80% of routine security tasks—accelerating triage and response, while freeing human analysts to focus on high-value threats.
- Curated Threat Intelligence: Deepwatch doesn’t rely on generic feeds. It provides tailored intelligence aligned with each customer’s industry, environment, and threat profile—ensuring defenses are always relevant and up to date.
- Comprehensive Security Posture Management: Beyond monitoring, Deepwatch continuously assesses and reports on an organization’s security maturity, helping leaders make informed decisions and track measurable improvements over time.
- 24/7 Expert Monitoring: Deepwatch becomes a seamless extension of the customer’s security operations center (SOC), offering round-the-clock “eyes-on-glass” support, real-time investigation, and immediate incident response.
- Board-Level Visibility: Deepwatch translates complex technical data into executive-ready reporting. CISOs can clearly demonstrate risk reduction, investment ROI, and strategic alignment with business objectives.
Preemptive MDR’s Tangible Benefits for Enterprises
Organizations that embrace preemptive MDR see clear and measurable benefits, including:
- Reduced Breach Risk: By identifying and resolving vulnerabilities before exploitation, preemptive MDR drastically lowers the odds of a successful cyberattack.
- Cost Savings: Automated remediation and efficient alerting reduce manual effort, lower staffing needs, and minimize costly incident responses.
- Greater Resilience: With proactive controls in place, enterprises can maintain operational continuity, regulatory compliance, and customer trust—even in the face of evolving threats.
- Faster Maturity Growth: Continuous assessments and expert guidance help build sustainable cybersecurity programs that evolve alongside threats and technologies.
The Future Is Preemptive
As the cyber landscape continues to evolve, organizations must move beyond reactive defenses. The future of cybersecurity will be defined by speed, intelligence, and foresight. Preemptive MDR, led by innovators like Deepwatch, represents this next frontier.
It’s not just about surviving the next breach—it’s about stopping it before it starts.
To learn more about Deepwatch visit: www.deepwatch.com
↑
Share