Fake ChatGPT Apps, Phishing-as-a-Service, and Zero-Days: Modular Backdoors and Exploited Vulnerabilities Push Cyber Threats Further Underground.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
PipeMagic: How a Fake ChatGPT App Fueled a Modular Backdoor and Zero-Day Exploits
The Rundown
PipeMagic is a newly exposed modular backdoor used by the financially motivated threat group Storm-2460, which disguised the malware as a legitimate open-source ChatGPT Desktop application. The framework is designed for flexibility and persistence, allowing attackers to dynamically execute payloads, maintain reliable command-and-control communication, and extend its capabilities over time. This modularity makes PipeMagic stealthy and difficult to analyze, distinguishing it as one of the more advanced backdoors observed in recent attacks.
Storm-2460 deployed PipeMagic in campaigns that exploited a zero-day vulnerability in Windows (CVE-2025-29824) to gain elevated privileges and deliver ransomware. Victims spanned industries such as information technology, finance, and real estate, with targets identified across the United States, Europe, South America, and the Middle East. While the number of confirmed incidents remains limited, the use of a zero-day exploit paired with a sophisticated, modular backdoor underscores both the threat actors’ capabilities and the potential business impact of such attacks.
Organizations can reduce risk by focusing on the fundamentals of resilience and layered defense. Timely vulnerability management and patching remain critical, especially for privilege-escalation flaws. Strong endpoint monitoring, detection, and response practices can help uncover malicious use of living-off-the-land tools (e.g., certutil, MSBuild) often used in initial infection chains. Network monitoring, anomaly detection, and strict access controls can further disrupt command-and-control activity. Finally, building an incident response process that integrates rapid investigation, containment, and recovery will help organizations minimize the impact of advanced, modular threats like PipeMagic.
Source Material: Microsoft
Salty 2FA: A New Phishing-as-a-Service Framework Discovered
Breaking it Down
The Salty 2FA attack typically begins with initial access via email, utilizing common phishing lures such as “Voice message was left…” or “Access full document…”. Upon clicking a malicious link, victims are directed to a phishing page where the attack unfolds in a multi-stage execution chain designed to resist detection. The initial page load often involves an interaction with Cloudflare Turnstile for validation checks, after which a small “trampoline” JavaScript executes.
This script is obfuscated and responsible for decoding the address of the next stage’s payload, which is then retrieved and written into the current page’s Document Object Model (DOM). This next payload is a large HTML page, also heavily padded with non-functional “noise” and containing another obfuscated JavaScript snippet, which ultimately presents a fake Microsoft login page to the victim. The infrastructure supporting these stages employs a unique domain pattern, consistently combining .com subdomains (e.g., .com.de, .it.com) with domains registered under the .ru TLD.
The subsequent stages of the attack focus on sophisticated client-side logic and evasion. All front-end logic, including page state transitions and user input collection, is managed by an obfuscated JavaScript code that extensively uses jQuery calls with dynamically generated and encoded element identifiers. The element IDs themselves are encoded using Base64 and XOR with a fixed, generated value.
To counter analysis, the phishing payload incorporates anti-analysis mechanisms, such as blocking keyboard shortcuts for debugging tools (e.g., DevTools) and measuring execution time to detect and halt activity if a debugger is suspected. Once credentials or other user inputs are entered, the data is “encrypted” using the same Base64 + XOR technique, though the XOR key is derived from the victim’s session identifier.
This stolen data is then exfiltrated via POST requests to servers residing on .ru domains observed within the attacker’s cluster. Crucially, the framework is capable of multi-state 2FA handling, interacting with the server to process various authentication methods like push notifications, SMS OTP, and voice calls, effectively bypassing these layers of security beyond just stealing initial credentials.
Source Material: Any Run
Ransomware and Data Extortion Trends (August 12–18)
The Rundown
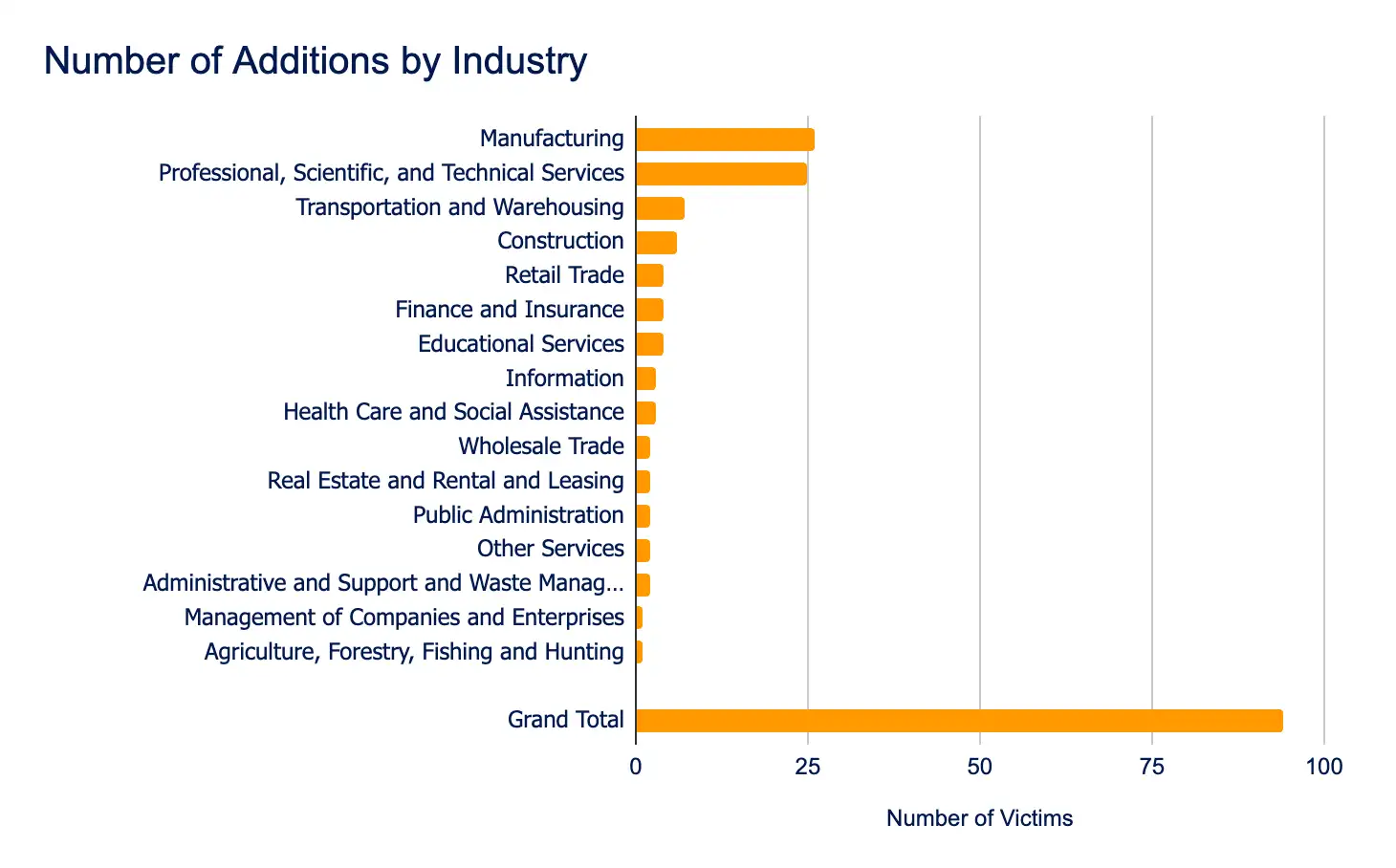
Between August 12 and 18, ransomware and data extortion incidents impacted 94 organizations across 19 leak sites, marking an approximate 24% increase from the previous week’s total of 76. While this uptick could suggest heightened ransomware activity, it more likely reflects a short-term surge in threat actor operations rather than a sustained escalation in attack frequency.
Manufacturing, Professional Services, and Transportation and Warehouse sectors remained the most heavily targeted, underscoring the continued focus on high-value, disruption-prone industries. Geographically, the United States, Germany and the United Kingdom saw the highest number of incidents, reinforcing threat actors’ concentration on strategically significant markets.
For business leaders, these patterns highlight the calculated and persistent nature of ransomware campaigns. Despite periodic shifts in weekly volume, the overall threat landscape remains volatile, emphasizing the importance of sustained investment in comprehensive prevention, detection, and incident response capabilities.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Transportation and Warehouse
- Most affected countries:
- United States
- Germany
- United Kingdom
- Most active leak sites:
- Akira
- Qilin
- Direwolf
- Play
Exploited Vulnerabilities in RARLAB, Microsoft, and N-Able Products Added to CISA’s Catalog
Between August 14 and August 20, CISA added one critical vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, affecting on-prem products from Trend Micro. This flaw has been confirmed as actively exploited in diverse threat campaigns.
If left unpatched, the vulnerabilities pose severe risks, including unauthorized access and privilege escalation, jeopardizing the confidentiality, integrity, and availability of impacted systems. Successful exploitation could lead to significant operational disruptions, data compromise, and lasting reputational damage.
Given the growing interest from both nation-state actors and financially motivated threat groups, immediate remediation is imperative. Delayed action substantially increases the likelihood of compromise and could trigger cascading impacts across interconnected IT and operational environments.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Share