Brand Impersonation, SaaS Abuse, and $1M Scams: From Salesforce Data Theft to Citrix Exploits, Threat Actors Expand Their Playbook
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Boxing Clever: Uncovering a $1M Scam Exploiting Major Brands
The Rundown
Netcraft recently uncovered a significant “Boxing Clever” task scam cluster, which leverages an API-driven, templated approach to exploit the branding of numerous major American companies. Brands impersonated include Delta, AMC Theatres, Universal Studios, Epic Records, DJI, Accor Hotels, and 20th Century Fox. This sophisticated operation deceives victims into making advance cryptocurrency payments, with Netcraft attributing over $1 million in cryptocurrency transactions to this cluster. The initial discovery, deltaairlineivip[.]com, served as an entry point into this wider network of malicious activity.
The scam entices would-be workers to enroll as “VIP” agents to “earn” money by completing tasks, such as booking flights for a commission. To achieve VIP status, victims must deposit cryptocurrency, with tiers ranging from a minimum of $100 up to $50,000. The domain registrations frequently feature a distinct “Boxer” registrant pattern from “DALLAS, US,” which allowed Netcraft to identify hundreds of related domains.
Furthermore, the scam infrastructure often relies on Dominet, the registrar arm of Alibaba Cloud, and other hosting companies like Dimension Network & Communication Limited (DNC) for hosting malicious content. These scams typically begin with direct messages on peer-to-peer platforms and require invite codes, and they often use counterfeit “certificates of incorporation” to appear legitimate.
Netcraft’s investigation involved tracing technical footprints, including curiously named JSON configuration files that control the scam sites’ operations and impersonated copyright strings for various brands. These files have unveiled numerous wallet addresses, which show significant inbound cryptocurrency transactions, including over $200,000 in USDT, $64,000 in Bitcoin, and $240,000 in ERC-20 tokens, in addition to previously identified funds.
Source Material: NetCraft
SalesForce Data Theft via Salesloft Drift: UNC6395 Campaign
The Rundown
Google Threat Intelligence Group (GTIG) and Mandiant issued an advisory regarding a widespread data theft campaign conducted by the threat actor UNC6395, which occurred between August 8 and August 18, 2025. This campaign specifically targeted Salesforce customer instances through compromised OAuth tokens associated with the Salesloft Drift third-party application. UNC6395 systematically exported large volumes of data from numerous corporate Salesforce instances, primarily intending to harvest sensitive credentials such as Amazon Web Services (AWS) access keys, passwords, and Snowflake-related access tokens. The actor demonstrated operational security awareness by deleting query jobs, though logs remained intact. Salesloft clarified that customers not integrated with Salesforce were not affected.
In response to this campaign, Salesloft, in collaboration with Salesforce, revoked all active access and refresh tokens for the Drift application on August 20, 2025, and Salesforce subsequently removed the Drift application from its AppExchange. Organizations using Drift integrated with Salesforce should consider their Salesforce data compromised and are urged to take immediate remediation steps.
Recommendations include revoking API keys, rotating credentials, investigating for compromise by searching for specific IP addresses and User-Agent strings (including those from Tor networks), reviewing Salesforce Event Monitoring logs, and scanning Salesforce objects for secrets. Furthermore, organizations should harden access controls by reviewing and restricting connected app scopes, enforcing IP restrictions, defining login IP ranges, and carefully managing ‘API Enabled’ permissions.
Source Material: Google Cloud
Ransomware and Data Extortion Trends (August 19-25)
The Rundown
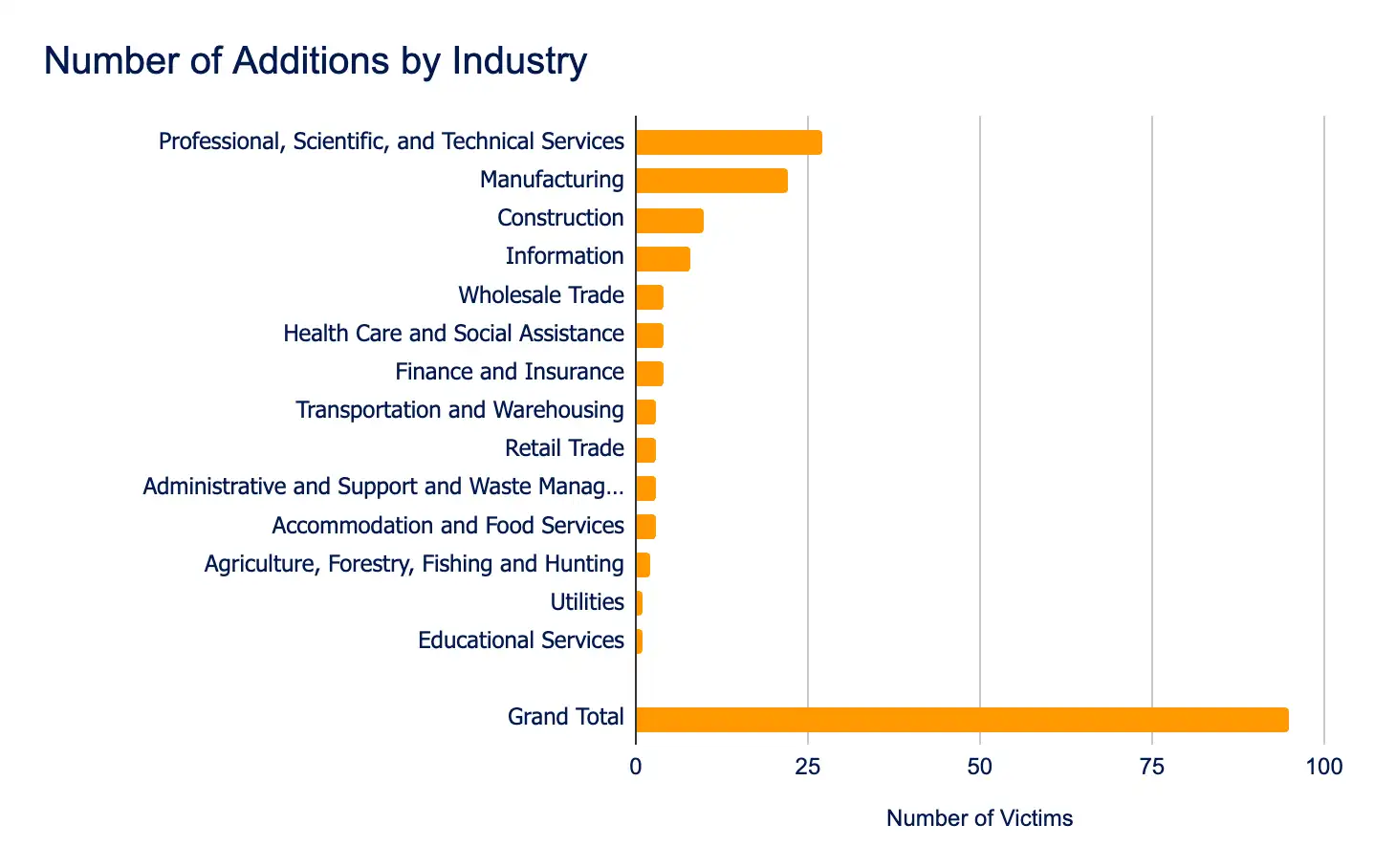
Between August 19 and 25, ransomware and data extortion incidents impacted 95 organizations across 14 leak sites, marking an approximate 1% increase from the previous week’s total of 94. While this uptick could suggest heightened ransomware activity, it more likely reflects a short-term surge in threat actor operations rather than a sustained escalation in attack frequency.
Professional Services, Manufacturing, and Construction sectors remained the most heavily targeted, underscoring the continued focus on high-value, disruption-prone industries. Geographically, the United States, Germany, and Canada saw the highest number of incidents, reinforcing threat actors’ concentration on strategically significant markets.
For business leaders, these patterns highlight the calculated and persistent nature of ransomware campaigns. Despite periodic shifts in weekly volume, the overall threat landscape remains volatile, emphasizing the importance of sustained investment in comprehensive prevention, detection, and incident response capabilities.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Construction
- Most affected countries:
- United States
- Germany
- Canada
- Most active leak sites:
- Warlock
- Qilin
- Akira
Exploited Vulnerabilities in Citrix, Git, and Apple Products Added to CISA’s Catalog
The Rundown
Between August 21 and August 27, CISA added 5 critical vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, affecting Citrix NetScaler, Citrix Session Recording, Git, and several Apple Operating System versions. These flaws have been confirmed as actively exploited in diverse threat campaigns.
If left unpatched, the vulnerabilities pose severe risks, including unauthorized access and privilege escalation, jeopardizing the confidentiality, integrity, and availability of impacted systems. Successful exploitation could lead to significant operational disruptions, data compromise, and lasting reputational damage.
Given the growing interest from both nation-state actors and financially motivated threat groups, immediate remediation is imperative. Delayed action substantially increases the likelihood of compromise and could trigger cascading impacts across interconnected IT and operational environments.
Citrix | NetScaler CVE-2025-7775
- Vulnerability Description: Citrix NetScaler ADC and NetScaler Gateway contain a memory overflow vulnerability that could allow for remote code execution and/or denial of service.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-25
- Recommended Mitigation Due Date: 2025-09-15
Citrix | Session Recording CVE-2024-8069
- Vulnerability Description: Citrix Session Recording contains a deserialization of untrusted data vulnerability that allows limited remote code execution with privilege of a NetworkService Account access. The attacker must be an authenticated user on the same intranet as the session recording server.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-25
- Recommended Mitigation Due Date: 2025-09-15
Citrix | Session Recording CVE-2024-8068
- Vulnerability Description: Citrix Session Recording contains an improper privilege management vulnerability that could allow for privilege escalation to NetworkService Account access. An attacker must be an authenticated user in the same Windows Active Directory domain as the session recording server domain.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-25
- Recommended Mitigation Due Date: 2025-09-15
Git | Git CVE-2025-48384
- Vulnerability Description: Git contains a link following vulnerability that stems from Git’s inconsistent handling of carriage return characters in configuration files.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-25
- Recommended Mitigation Due Date: 2025-09-15
Apple | iOS, iPadOS, and macOS CVE-2025-43300
- Vulnerability Description: Apple iOS, iPadOS, and macOS contain an out-of-bounds write vulnerability in the Image I/O framework.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-21
- Recommended Mitigation Due Date: 2025-09-11
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Share