Scattered Spider Strikes vSphere: Advanced Social Engineering, Ransomware Extortion, and Exploits in Cisco and PaperCut Elevate Enterprise Threats
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Breaking the Hypervisor Barrier: How Scattered Spider Targets VMware vSphere
- CISA-FBI Joint Cyber Advisory: Advanced Social Engineering and Extortion by Scattered Spider Collective
- Ransomware and Data Extortion Trends (July 22-28)
- Exploited Vulnerabilities in PaperCut and Cisco Products Added to CISA’s Catalog
Breaking the Hypervisor Barrier: How Scattered Spider Targets VMware vSphere
The Rundown
UNC3944, also known as Scattered Spider, 0ktapus, or Octo Tempest, is conducting hypervisor‑level attacks targeting VMware vSphere environments. The intrusion begins with social engineering: actors impersonate employees or administrators to trick IT help desks into resetting Active Directory passwords. Once they gain domain access, they pivot to vCenter Server and ESXi infrastructure, leveraging their domain foothold to escalate privileges while evading typical endpoint-based detection tools.
The group’s operations bypass traditional security controls by launching ransomware and data exfiltration directly at the hypervisor layer. UNC3944 manipulates vSphere control components to disable backups, detach and mount virtual disks (including sensitive files like NTDS.dit), and encrypt datastores, all executed from ESXi hosts. Because EDR systems rarely monitor the hypervisor or vCenter appliance, much of this activity remains invisible to endpoint defenses.
To counteract these threats, the article outlines a multi‑pillar defense strategy. It emphasizes robust logging of vCenter events and ESXi host audit records, forwarded to centralized systems such as SIEMs for automated detection. It also calls for proactive hardening measures: encrypt Tier‑0 virtual machines, enforce ESXi lockdown mode, restrict unsigned binaries via execInstalledOnly, and tighten identity controls around password resets and administrative access to vSphere.
Source Material: Google Mandiant
CISA-FBI Joint Cyber Advisory: Advanced Social Engineering and Extortion by Scattered Spider Collective
The Rundown
Scattered Spider (also known under aliases such as Starfraud, UNC3944, Scatter Swine, and Muddled Libra) is a financially motivated cybercriminal collective that has targeted large enterprises, particularly in telecom, IT services, retail, insurance, aviation, and entertainment, with high-profile breaches like those at MGM and Caesars. The FBI and CISA jointly issued advisory AA23‑320A on November 16, 2023, after observing extortion-based data theft and emerging ransomware operations linked to this group.
Scattered Spider excels in social engineering: they impersonate help-desk or IT support personnel via phone, SMS or email to trick employees into surrendering account credentials, one-time MFA codes, or running remote access software such as TeamViewer, ngrok, or Fleetdeck.io. They also use MFA “bombing” (overloading users with authentication prompts) and SIM‑swap attacks to bypass multi-factor authentication.
Once inside, they utilize legitimate tools for lateral movement and data harvesting, deploy ETL tools in the victim’s cloud environment to aggregate data, and, through their affiliation with the BlackCat/ALPHV ransomware operation, encrypt and extort stolen data.
CISA recommends a layered defense: enable phishing-resistant MFA (for example, FIDO2 or hardware keys), restrict employee ability to install or execute remote access software, and maintain offline, immutable backups to guard against encryption ransom or data loss. Organizations should tightly control application execution (via application whitelisting or allow‑listing) and segment cloud environments to minimize lateral movement. Proactive assessment tools, such as technologies in the breach attack simulation (BAS) space, to simulate Scattered Spider’s techniques so businesses can test detection and response readiness.
Source Materials: DHS CISA
Ransomware and Data Extortion Trends (July 22 – 28)
The Rundown
Between July 22 and 28, ransomware and data extortion activity affected 64 organizations across 16 leak sites, representing a 21% decrease from the previous week’s total of 81. While this decline may appear to signal a downward trend, it more likely reflects a temporary reduction in threat actor operations rather than a sustained drop in overall attack volume.
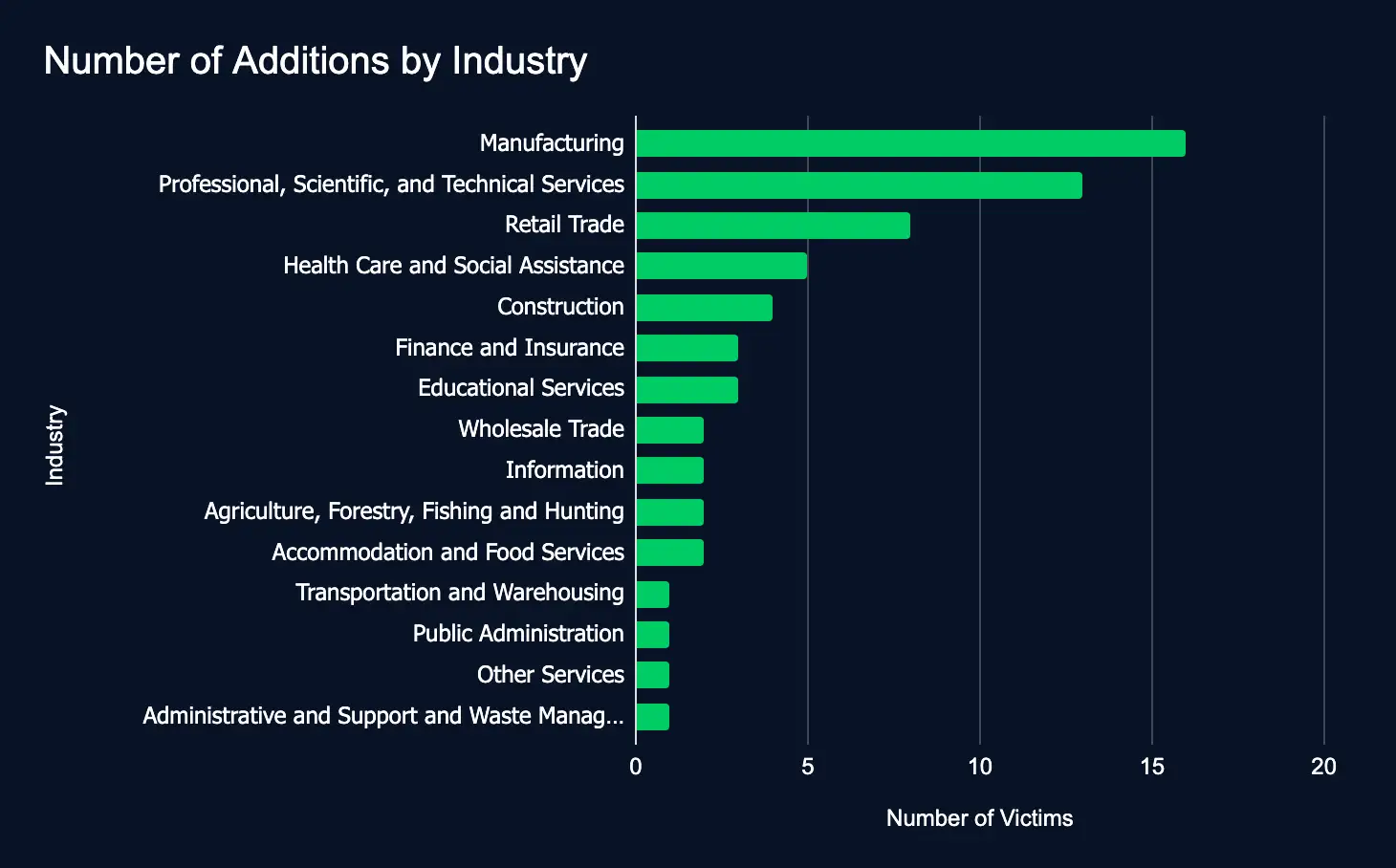
Manufacturing, Professional Services, and Retail Trade continued to be among the most targeted sectors, underscoring the persistent focus on high-value industries. A significant portion of affected organizations were located in key regions such as the United States, Germany, and the United Kingdom, highlighting the continued prioritization of strategically important markets. For business leaders, these patterns emphasize the calculated and ongoing nature of ransomware threats. Despite weekly fluctuations, the risk to critical sectors remains elevated, reinforcing the importance of sustained investment in prevention, detection, and response capabilities.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Retail Trade
- Most affected countries:
- United States
- Germany
- United Kingdom
- Most active leak sites:
- INC Ransom
- Qilin
- Akira
Exploited Vulnerabilities in PaperCut and Cisco Products Added to CISA’s Catalog
The Rundown
Between July 24 and July 30, CISA added three critical vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, impacting widely deployed products from PaperCut and Cisco. These vulnerabilities have been confirmed as actively exploited across a range of threat campaigns.
If left unpatched, they present significant risks, including unauthorized access and privilege escalation, that threaten the confidentiality, integrity, and availability of affected systems. Successful exploitation could result in major operational disruptions and long-term reputational harm.
With increasing interest from both nation-state actors and financially motivated threat groups, immediate remediation is essential. Failure to act promptly heightens the risk of compromise and may expose organizations to cascading impacts across their IT and operational environments.
PaperCut | NG/MF CVE-2023-2533
- Vulnerability Description: PaperCut NG/MF contains a cross-site request forgery (CSRF) vulnerability, which, under specific conditions, could potentially enable an attacker to alter security settings or execute arbitrary code.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-28
- Recommended Mitigation Due Date: 2025-08-18
Cisco | Identity Services Engine CVE-2025-20337, CVE-2025-20281
- Vulnerability Description: Cisco Identity Services Engine contains an injection vulnerability in a specific API of Cisco ISE and Cisco ISE-PIC due to insufficient validation of user-supplied input allowing an attacker to exploit this vulnerability by submitting a crafted API request. Successful exploitation could allow an attacker to perform remote code execution and obtaining root privileges on an affected device.
- Exploitation Details: Vulnerability arises from unsafe deserialization in the enableStrongSwanTunnel() method. An attacker can submit crafted payloads using serialized Java String[] to execute commands, use ${IFS} to bypass argument parsing, and ultimately escape a Docker container to compromise the host.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-28
- Recommended Mitigation Due Date: 2025-08-18
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share