From Fake IT Tools to VPN Breaches: Akira Ransomware, SonicWall Exploits, and D-Link Vulnerabilities Accelerate Full-Spectrum Attacks
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
From VPN Breach to Domain Controller in Hours: SonicWall Under Siege
The Rundown
A cybersecurity threat detection and response provider has observed a surge in high‑severity incidents involving SonicWall SSL VPN appliances, particularly those using the Secure Mobile Access (SMA) platform. These attacks are believed to leverage a likely zero‑day vulnerability, enabling adversaries to bypass multi‑factor authentication (MFA) and gain unauthorized access, even against fully patched devices. This activity has been linked to the deployment of Akira ransomware, following rapid post‑access encryption and efforts to disable endpoint protection.
Threat actors appear to exploit either yet‑unknown flaws in the VPN authentication layer or infiltrate via stolen credentials or token reuse. Once inside, they move laterally quickly, often creating backdoor accounts and deploying ransomware within hours. These VPN appliances, widely deployed across enterprises, lack robust real‑time monitoring and are frequently misconfigured or unpatched, making them attractive targets.
To defend against these evolving threats, Huntress, and other security providers, strongly recommend immediate action: disable publicly exposed SonicWall SSL VPN services until patches are applied (if they aren’t already), enforce MFA, remove inactive user accounts, restrict VPN access to trusted IP ranges, and enhance log monitoring and anomalous‑session detection (e.g. via identity threat detection tools). The speed and stealth of these attacks highlight the critical importance of proactive patch management and layered defense strategies.
Source Material: Huntress
Bumblebee to Akira: A Full-Spectrum Attack via Fake IT Tool Installers
The Rundown
In July 2025, cybercriminals launched a targeted attack campaign exploiting Bing search results to trick IT professionals into downloading malicious versions of legitimate software tools. In one observed case, a user searching for “ManageEngine OpManager” was directed to a fake website hosting a trojanized installer. While the software appeared to install normally, it also deployed the Bumblebee malware, providing attackers with an initial foothold inside the corporate network. This tactic, known as SEO poisoning, was used to target highly privileged IT administrator accounts, rapidly escalating the threat level.
After gaining access, the attackers moved swiftly. They installed additional backdoors, including AdaptixC2 and RustDesk, and created high-privilege accounts to secure persistence. Using built-in system tools, they performed extensive network reconnaissance, extracted sensitive credential data, and exfiltrated information using FileZilla. They targeted backup systems and databases to maximize damage and ensure data loss. Approximately 44 hours after initial access, they launched Akira ransomware to encrypt files and cripple operations. Just two days later, they returned to compromise a second domain within the same organization, repeating the ransomware attack.
This attack was not isolated. Other organizations, including one investigated by the Swisscom B2B CSIRT, reported similar incidents in the same month. In both cases, Bumblebee and Akira ransomware were delivered through trojanized software masquerading as trusted IT tools.
The rapid progression from infection to full-blown ransomware, often within a day, highlights a growing risk for enterprises that rely on open web searches for software downloads. The campaign underscores the importance of validating software sources, enforcing multi-factor authentication, monitoring administrative activity, and ensuring timely detection of lateral movement and data exfiltration.
Source Materials: The DFIR Report
Ransomware and Data Extortion Trends (July 29 – August 4)
The Rundown
Between July 29 and August 4, ransomware and data extortion incidents impacted 51 organizations across 15 leak sites, a 20% decline compared to the previous week’s tally of 64. While this drop might suggest a decrease in activity, it more likely reflects a short-term slowdown in threat actor operations rather than a meaningful reduction in overall attack frequency.
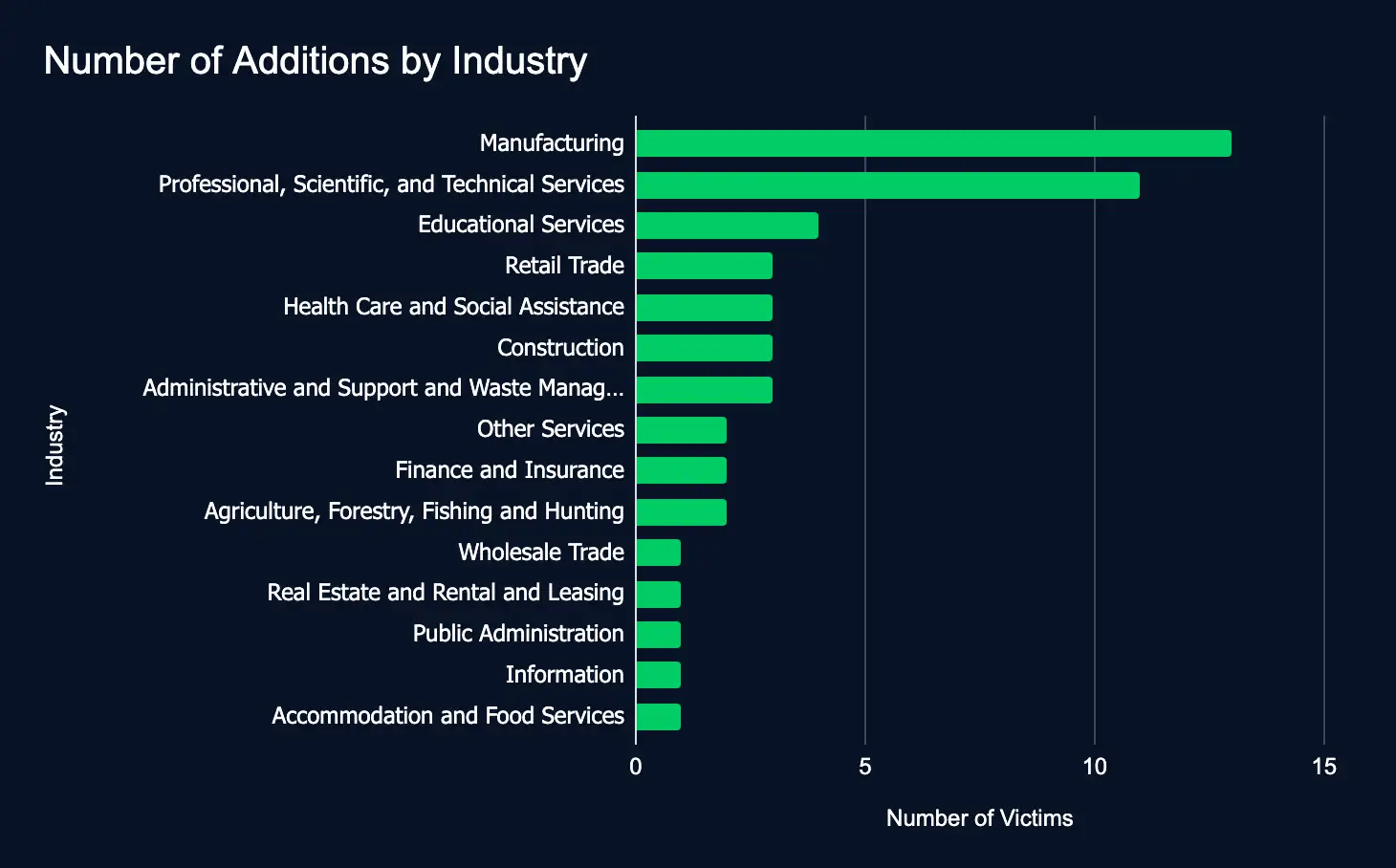
Manufacturing, Professional Services, and Educational Services remained among the most heavily targeted sectors, pointing to a continued emphasis on high-value industries. Many of the affected organizations were based in strategically significant regions, including the United States, Spain, Italy, and Germany, signaling an ongoing focus on critical economic markets.
For business leaders, these trends reinforce the calculated and persistent nature of ransomware campaigns. Despite periodic fluctuations in volume, the threat landscape remains volatile, underscoring the need for continued investment in robust prevention, detection, and response strategies.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Educational Services
- Most affected countries:
- United States
- Spain
- Italy
- Germany
- Most active leak sites:
- INC Ransom
- Akira
- Qilin
Exploited Vulnerabilities in D-Link Products Added to CISA’s Catalog
The Rundown
Between July 31 and August 6, CISA added three critical vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, impacting widely deployed products from D-Link. These vulnerabilities have been confirmed as actively exploited across a range of threat campaigns.
If left unpatched, they present significant risks, including unauthorized access and privilege escalation, that threaten the confidentiality, integrity, and availability of affected systems. Successful exploitation could result in major operational disruptions and long-term reputational harm.
With increasing interest from both nation-state actors and financially motivated threat groups, immediate remediation is essential. Failure to act promptly heightens the risk of compromise and may expose organizations to cascading impacts across their IT and operational environments.
D-Link | DCS-2530L and DCS-2670L Devices CVE-2020-25078, CVE-2020-25079
- Vulnerability Description:
- CVE-2020-25078: D-Link DCS-2530L and DCS-2670L devices contain a command injection vulnerability in the cgi-bin/ddns_enc.cgi. The impacted products could be end-of-life (EoL) and/or end-of-service (EoS). Users should discontinue product utilization.
- CVE-2020-25079: D-Link DCS-2530L and DCS-2670L devices contain a command injection vulnerability in the cgi-bin/ddns_enc.cgi. The impacted products could be end-of-life (EoL) and/or end-of-service (EoS). Users should discontinue product utilization.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions
- Date Added to catalog: 2025-08-05
- Recommended Mitigation Due Date: 2025-08-26
D-Link | DNR-322L CVE-2022-40799
- Vulnerability Description: D-Link DNR-322L contains a download of code without integrity check vulnerability that could allow an authenticated attacker to execute OS level commands on the device. The impacted products could be end-of-life (EoL) and/or end-of-service (EoS). Users should discontinue product utilization.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-08-05
- Recommended Mitigation Due Date: 2025-08-26
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share