Stealth Access, Memory-Only Malware, and Exploited Tech: Ransomware Actors Leverage SimpleHelp, AsyncRAT, and Critical Vulnerabilities to Breach Defenses
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Access Granted: Ransomware Actors Exploit SimpleHelp for Stealth Entry
The Rundown
Cybercriminals are using a legitimate remote access tool called SimpleHelp to sneak into company networks and deploy ransomware—malicious software that locks up data and demands payment to restore access. These attackers exploit vulnerable remote access software that may appear legitimate, but in reality, it grants them unauthorized remote control over the system.
Once inside, the attackers can move through internal systems, steal sensitive data, and ultimately lock down operations using ransomware. This can cause serious business disruption, financial loss, and reputational damage. Victims often don’t realize they’ve been compromised until it’s too late.
To defend against this activity, CISA recommends patching vulnerable SimpleHelp instances, removing unauthorized remote access tools, implementing application allowlisting, and segmenting networks to limit lateral movement. Continuous monitoring and prompt incident response are critical to reducing the risk and impact of such compromises.
Source Material: DHS CISA
Memory-Only Malware: AsyncRAT Campaign Bypasses Defenses via Clickfix Lure
The Rundown
A recent CloudSEK investigation uncovered a “file-less” malware campaign that specifically lures German-speaking users to bogus “I’m not a robot” pages branded as “Clickfix.” When a visitor clicks the CAPTCHA button, the site silently copies a PowerShell command to the clipboard and instructs the user to paste and run it—launching the AsyncRAT remote-access Trojan entirely in memory. Because no file is written to disk, traditional antivirus tools have little to scan, giving the attackers a stealthy foothold.
Behind the scenes, the command abuses legitimate Windows utilities (conhost.exe and PowerShell) to pull down an obfuscated C# payload, reverse it in memory, and compile it on the fly. Once active, AsyncRAT connects back to its command-and-control server on non-standard port 4444, granting criminals full remote control, key-logging and data-exfiltration capabilities. Persistence is achieved by adding auto-run keys in the user’s registry hive, ensuring the malware survives reboots while remaining invisible to most endpoint tools.
For businesses, the impact can range from stolen credentials to prolonged, covert access to internal systems. CloudSEK recommends blocking or closely monitoring headless PowerShell activity, auditing changes to RunOnce and related registry keys, filtering outbound traffic to unknown destinations—especially on uncommon ports—and deploying memory-scanning rules to spot in-memory loaders. Proactive controls in these areas can prevent similar “click-to-compromise” attacks from bypassing defenses.
Source Material: CloudSEK
Ransomware and Data Extortion Trends (June 10 – 16)
The Rundown
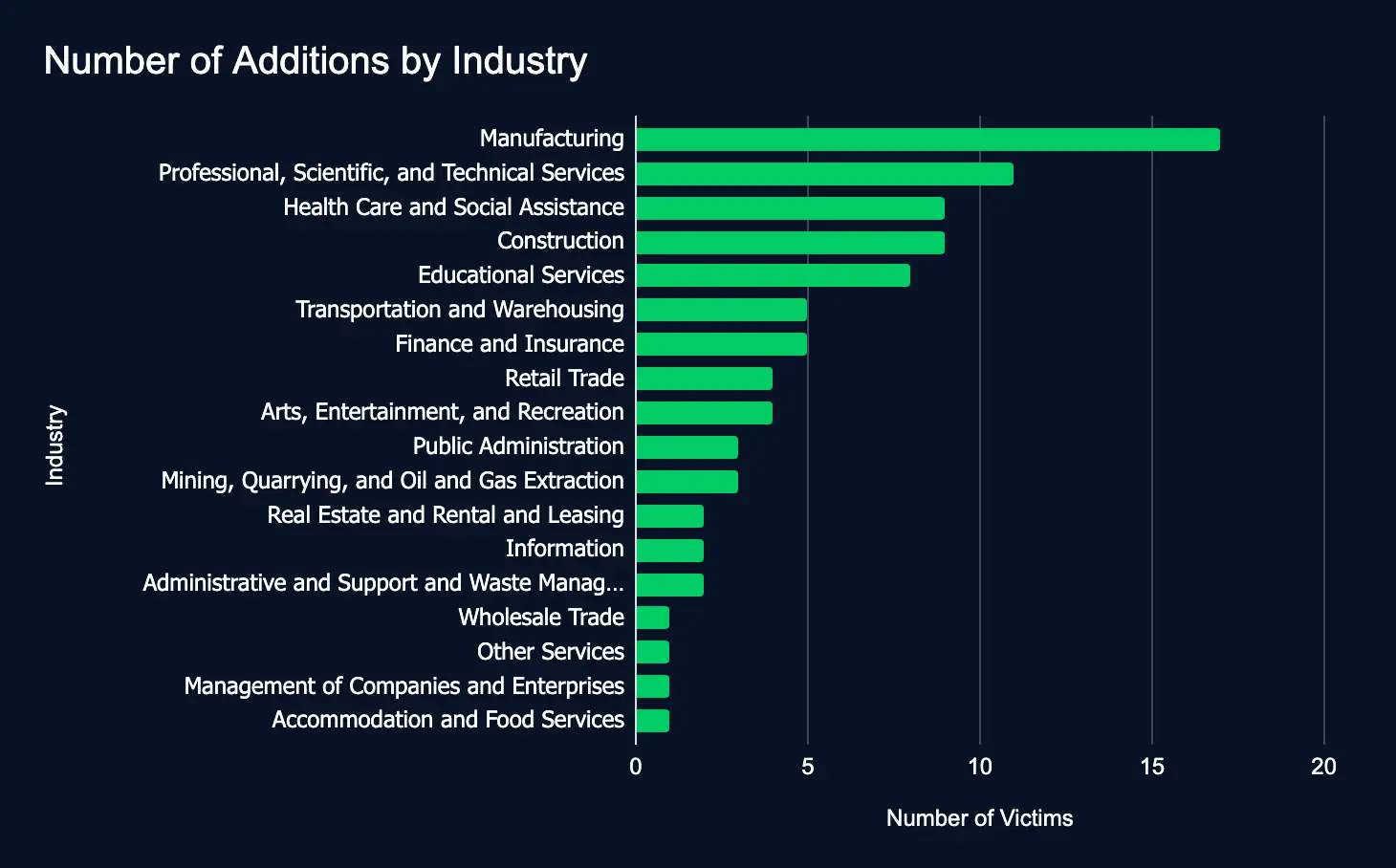
Between June 10 and 16, ransomware and data extortion activity experienced a slight increase, with 88 victim organizations listed across 20 leak sites, just one more than the previous week’s total of 87. This marginal rise suggests a plateau in threat actor operations rather than a notable escalation in attacks.
High-value sectors such as Manufacturing, Professional Services, Healthcare, and Construction remain primary targets. Most impacted organizations were located in strategic regions, including the United States, Canada, and Israel, underscoring adversaries’ continued focus on specific industries and geographies.
For business leaders, this ongoing trend emphasizes the persistent nature of ransomware threats. Despite minor week-to-week fluctuations, threat actors are maintaining pressure on key sectors. Organizations should use this time to regularly evaluate and enhance their cybersecurity frameworks, ensuring that prevention, detection, and response efforts stay aligned with current threat dynamics.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Health Care and Social Assistance
- Construction
- Most affected countries:
- United States
- Canada
- Israel
- Most active leak sites:
- Qilin
- Anubis
- NightSpire
Apple, and Linux Products Added to CISA’s Catalog – Immediate Mitigation Recommended
The Rundown
Between June 12 and 18, three high-impact vulnerabilities targeting products from TP-Link, Apple, and Linux were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, confirming their exploitation in active threat campaigns.
If left unpatched, these vulnerabilities pose a substantial threat to organizational security, offering attackers a foothold for compromise. Given the broad adoption of these technologies across sectors, the potential consequences are both widespread and critical.
With increased interest from both state-sponsored and financially motivated threat actors, the urgency for remediation cannot be overstated. Swift action is vital to maintain operational resilience and protect critical assets from exploitation.
TP-Link | Multiple Routers CVE-2023-33538
- Vulnerability Description: TP-Link TL-WR940N V2/V4, TL-WR841N V8/V10, and TL-WR740N V1/V2 contain a command injection vulnerability via the component /userRpm/WlanNetworkRpm. The impacted products could be end-of-life (EoL) and/or end-of-service (EoS). Users should discontinue product utilization.
- Exploitation Details: sid1 is concatenated directly into a shell-level command that the router’s httpd passes to the underlying BusyBox shell. No input sanitisation or length check is performed, so shell metacharacters (;, ||, & …) break out of the intended context and allow arbitrary commands to run as root.
- Public Proof-of-Concept (PoC): Yes
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-16
- Recommended Mitigation Due Date: 2025-07-07
Apple | Multiple Products CVE-2025-43200
- Vulnerability Description: Apple iOS, iPadOS, macOS, watchOS, and visionOS, contain an unspecified vulnerability when processing a maliciously crafted photo or video shared via an iCloud Link.
- Exploitation Details: A logic vulnerability in how these operating systems process a maliciously crafted photo or video delivered via an iCloud Link embedded in an iMessage. This is a zero-click exploit.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-16
- Recommended Mitigation Due Date: 2025-07-07
Linux | Kernel CVE-2023-0386
- Vulnerability Description: Linux Kernel contains an improper ownership management vulnerability, where unauthorized access to the execution of the setuid file with capabilities was found in the Linux kernel’s OverlayFS subsystem in how a user copies a capable file from a nosuid mount into another mount. This uid mapping bug allows a local user to escalate their privileges on the system.
- Public Proof-of-Concept (PoC): Yes
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-17
- Recommended Mitigation Due Date: 2025-07-08
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share