Stealth Malware, Nation-State Phishing, and Ransomware Trends Highlight an Evolving Threat Landscape
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Malware Behind the Mask: The Rise of ClickFix and Clipboard Injection Tactics
The Rundown
The ClickFix campaign is a sophisticated cyberattack method that exploits user fatigue with CAPTCHA verifications. Threat actors compromise legitimate websites or create phishing sites that display counterfeit CAPTCHA challenges. Users are tricked into following what they believe are standard verification steps—such as copying and pasting commands into the Windows ‘Run’ dialog—which actually initiate malware installation. This method relies on social engineering and psychological manipulation rather than exploiting software vulnerabilities, making it particularly effective.
Once a user completes the fake CAPTCHA, the attack proceeds by using legitimate Windows tools like PowerShell and mshta.exe to download and execute malicious payloads. These often include well-known Remote Access Trojans (RATs) and infostealers like Lumma Stealer and NetSupport RAT. The infection chain typically starts with clipboard manipulation and results in a full compromise of the user’s system, with sensitive data exfiltrated and remote control handed to the attackers. This technique is increasingly favored due to its high success rate and low technical complexity.
To counter ClickFix-style attacks, SentinelOne emphasizes a dual-layered approach involving both technology and user awareness. Businesses are advised to educate employees on the dangers of copying and pasting commands from web prompts, deploy Endpoint Detection and Response (EDR) tools capable of detecting such behavior, and enforce policy restrictions on command execution tools like PowerShell. A well-informed user base and properly configured security infrastructure are essential to mitigating the risks posed by these deceptive, user-driven malware campaigns.
Source Material: SentinelOne
Behind the Phish: How Void Blizzard Infiltrates NATO-Aligned Networks
The Rundown
On May 27, 2025, Microsoft announced the identification of a new Russia-affiliated cyber threat actor named Void Blizzard. This group has been actively targeting critical sectors such as energy, defense, and telecommunications across North America and Europe. Employing sophisticated spear-phishing campaigns and exploiting known vulnerabilities, Void Blizzard aims to infiltrate networks to conduct espionage and gather sensitive information. Their operations are characterized by stealth and precision, making them a significant concern for organizations within these vital industries.
Void Blizzard’s tactics involve the use of custom malware and advanced persistent threats to maintain long-term access to compromised systems. By leveraging legitimate credentials and employing techniques that blend with normal network activity, they minimize detection and maximize data exfiltration. This approach not only threatens the confidentiality of proprietary information but also poses risks to the operational integrity of essential services. The group’s activities underscore the evolving nature of cyber threats and the need for heightened vigilance among businesses operating in targeted sectors.
In response to this emerging threat, Microsoft emphasizes the importance of proactive cybersecurity measures. Organizations are advised to implement multi-factor authentication, conduct regular security assessments, and ensure timely patching of systems to mitigate potential vulnerabilities. Additionally, fostering a culture of cybersecurity awareness among employees can help in identifying and preventing spear-phishing attempts. By staying informed and adopting robust security protocols, businesses can better protect themselves against sophisticated actors like Void Blizzard.
Source Material: Microsoft Threat Intelligence
Ransomware and Data Extortion Trends (May 19–25)
The Rundown
Ransomware and data extortion activity experienced a slight decline between May 19 and 25, marked by 15% increase in the number of listed victim organizations compared to the previous week.
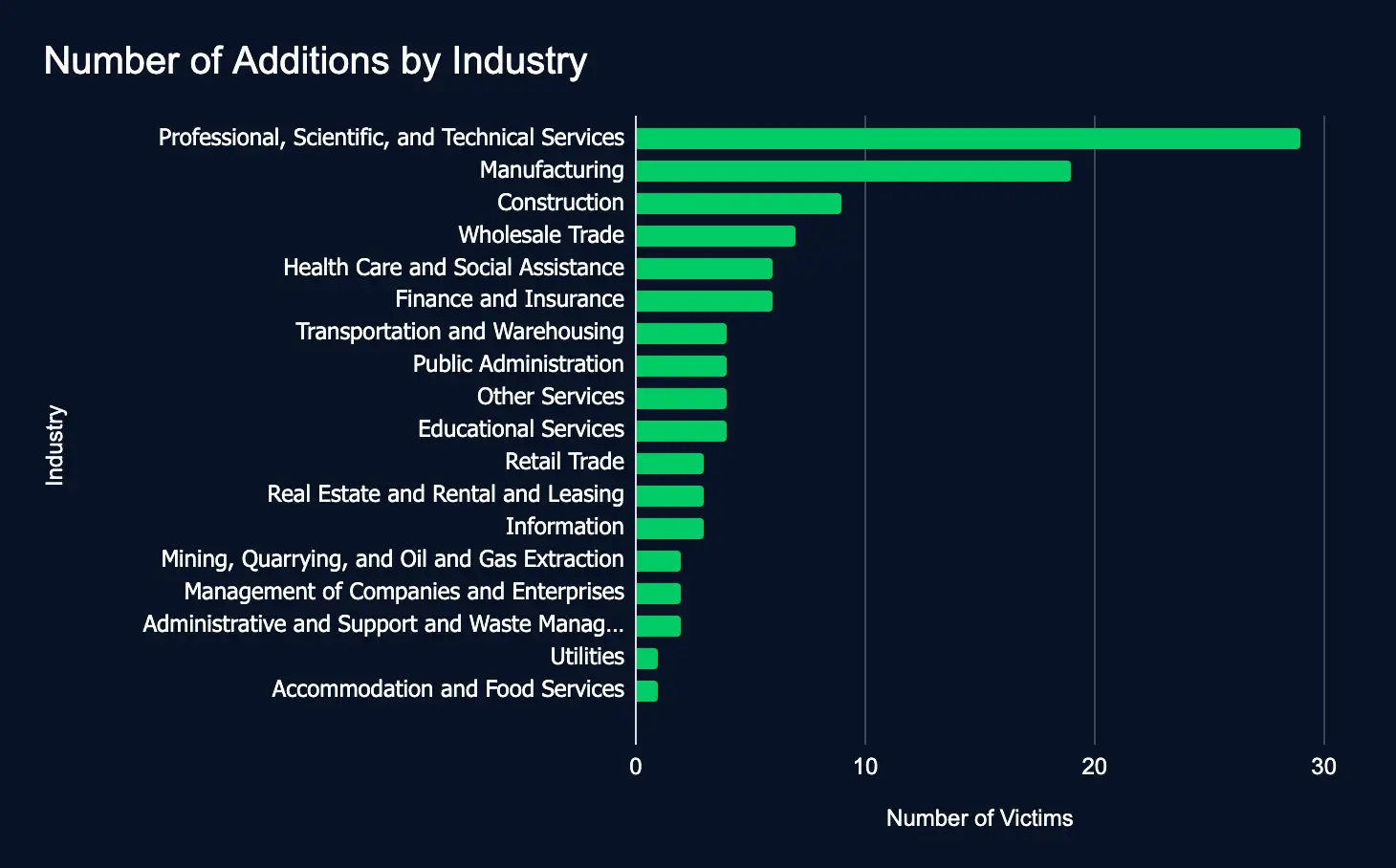
During the reporting period, 109 organizations across 18 industries were listed on 18 ransomware and data extortion leak sites—representing a slight increase from the 94 victims reported the previous week.
This week’s slight uptick in ransomware and data extortion listings reflects a consistent level of threat actor activity, rather than a notable surge or decline. The continued targeting of key industries—such as Professional Services, Manufacturing, and Construction—across regions including the United States, Canada, the United Kingdom, and Japan suggests a strategic broadening of focus. Security teams should interpret this as a sign of ongoing, sustained malicious activity and ensure their detection, response, and hardening efforts are calibrated to address the growing scale and sophistication of these threats.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Construction
- Most affected countries:
- United States
- Canada
- United Kingdom
- Japan
- Most active leak sites:
- Blacklock
- Akira
- Gunra
Industry Impact
The Adversary Tactics and Intelligence team classified these organizations by sector using NAICS standards. While every effort has been made to ensure accuracy, determining the operating sector can be challenging due to companies operating in multiple sectors.
The chart below depicts the distribution of new data leak site listings across 18 industries, representing the majority of the 20 sectors defined by the North American Industry Classification System (NAICS). This week, the Professional Services sector was the most affected, comprising 27% of new listings. Manufacturing followed at 17%, with Construction accounting for 8%, collectively representing the top three targeted sectors.
Exploited Vulnerability in the Samsung MagicINFO 9 Product Added to CISA’s Catalog
The Rundown
Between May 22 and 28, one critical vulnerability affecting a Samsung MaginINFO 9 product was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
This vulnerability, if left unaddressed, presents a significant risk to organizational security, potentially exposing systems to active exploitation.
Due to the widespread use of the affected technologies across various industries, the associated risks are significant. There is a high probability of exploitation by both state-sponsored and financially motivated threat actors. Therefore, immediate and prioritized remediation is essential to ensure operational resilience and safeguard critical infrastructure from potential compromise.
Samsung | MagicINFO 9 Server CVE-2025-4632
- Vulnerability Description: Samsung MagicINFO 9 Server contains a path traversal vulnerability that allows an attacker to write arbitrary files as system authority.
- Exploitation Details: The issue arises from improper validation of file paths, enabling attackers to manipulate file paths using sequences like “../../” to escape restricted directories and write files to arbitrary locations on the server
- Exploited in a Ransomware attack? Unknown
- Public Proof-of-Concept: Yes
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-22
- Recommended Mitigation Due Date: 2025-06-12
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share