EDDIESTEALER Malware, Brand-Based Intrusions, Ransomware Activity, and Critical Vulnerabilities in ASUS, ConnectWise, and Qualcomm Products
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
EDDIESTEALER: Rust-Based Malware Hides Behind Fake CAPTCHA Lures
The Rundown
Elastic Security Labs has identified a new cybersecurity threat named EDDIESTEALER, a lightweight information-stealing malware developed in Rust. This malware is disseminated through deceptive CAPTCHA verification pages that mimic legitimate services like Google’s reCAPTCHA. Unsuspecting users are tricked into executing a malicious PowerShell script, which downloads and runs EDDIESTEALER on their Windows systems. Once active, the malware communicates with a command-and-control server to receive instructions on which data to target, including credentials, browser information, and cryptocurrency wallet details.
The use of Rust in EDDIESTEALER’s development signifies a growing trend among cybercriminals to employ modern programming languages that offer enhanced stealth and resistance to traditional analysis methods. Rust’s features, such as memory safety and zero-cost abstractions, make the malware more challenging to detect and analyze. Additionally, EDDIESTEALER’s code is obfuscated, and it lacks standard anti-sandbox or virtual machine detection techniques, suggesting that such checks may be performed server-side. The malware also includes a self-deletion feature, allowing it to remove itself after execution to evade detection.
For businesses, this development underscores the importance of robust cybersecurity measures and employee awareness training. Organizations should educate their staff about the dangers of interacting with unsolicited CAPTCHA prompts and ensure that their security systems are equipped to detect and respond to such threats. Implementing advanced threat detection solutions and maintaining up-to-date security protocols can help mitigate the risks posed by sophisticated malware like EDDIESTEALER.
Source Material: Elastic
The Illusion of Legitimacy: How Threat Actors Use Trusted Brands to Breach Systems
The Rundown
DomainTools uncovered a sophisticated malware campaign that exploits human trust through deceptive websites, including spoofed Gitcodes and fake DocuSign verification pages. These sites prompt users to copy and paste malicious PowerShell scripts into their Windows Run prompt, initiating a multi-stage process that culminates in the installation of the NetSupport Remote Access Trojan (RAT). This malware grants attackers remote control over the victim’s system, posing significant security risks.
The attack unfolds in several stages: initial scripts download subsequent ones, each fetching additional payloads from various domains such as tradingviewtool[.]com and tradingviewtoolz[.]com. These scripts employ legitimate tools like 7-Zip to unpack and execute the final payload, “client32.exe,” which is configured to persist by modifying the Windows Registry. By naming the startup entry “My Support,” the malware attempts to evade user suspicion.
Further analysis revealed a broader malicious infrastructure supporting this campaign. Threat actors utilized registrars like Cloudflare, NameCheap, and NameSilo, along with nameservers such as cloudflare[.]com and luxhost[.]org. The consistent use of specific SSL issuers and website titles containing “Gitcodes” indicates a coordinated effort to deceive users and distribute malware. This case underscores the importance for businesses to implement robust cybersecurity measures and educate employees about the dangers of executing unverified scripts.
Source Material: DomainTools
Ransomware and Data Extortion Trends (May 26 – June 2)
The Rundown
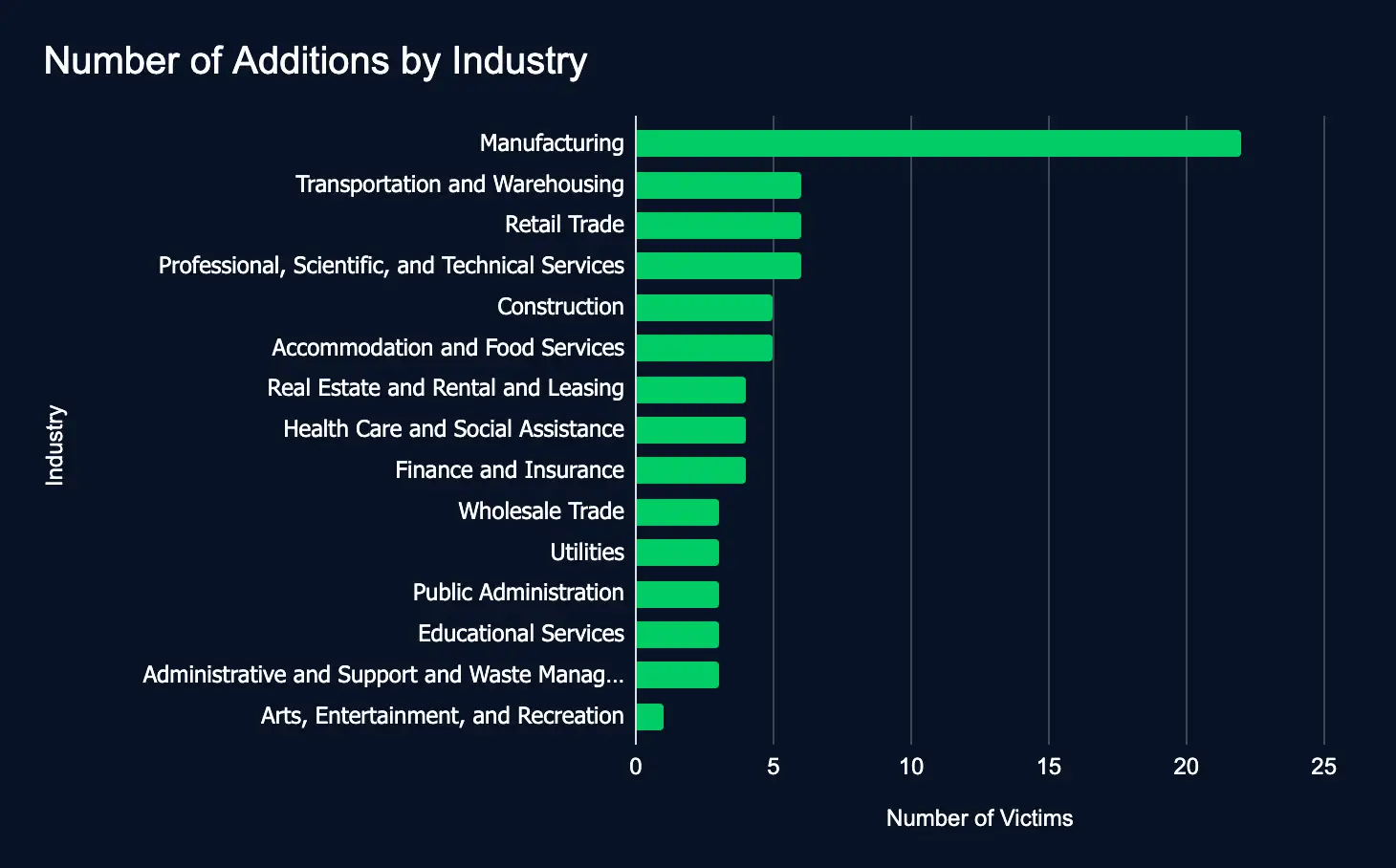
Between May 26 and June 2, reported ransomware and data extortion activity declined notably, despite a 28% week-over-week increase in the number of victim organizations listed on leak sites. A total of 78 organizations across 15 industries were named on 23 ransomware and extortion platforms—down from 109 victims the previous week.
This reduction in victim listings suggests a stabilization in threat actor behavior rather than a significant downturn in overall activity. Adversaries continue to focus on high-value sectors such as Professional Services, Manufacturing, and Construction, with affected organizations spanning key markets including the United States, Canada, the United Kingdom, and Japan.
For business leaders, this trend signals an ongoing and strategically sustained threat landscape. While overall volumes may fluctuate, adversaries remain focused on high-value industries and regions. Organizations should view this as a prompt to continuously evaluate and strengthen their cybersecurity posture, ensuring that risk mitigation, detection, and response capabilities remain aligned with the evolving threat environment.
Key Trends:
- Most affected industries:
- Manufacturing
- Transportation and Warehousing
- Retail Trade
- Most affected countries:
- United States
- Canada
- Germany
- Brazil
- Most active leak sites:
- Qilin
- Akira
- Play
Exploited Vulnerabilities in ASUS, ConnectWise, Craft CMS, and Qualcomm Products Added to CISA’s Catalog
The Rundown
Between May 29 and June 4, eight critical vulnerabilities impacting products from ASUS, ConnectWise, Craft CMS, and Qualcomm were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
If not promptly addressed, these vulnerabilities pose a substantial threat to organizational security, leaving systems susceptible to active exploitation. Given the broad adoption of the affected technologies across multiple sectors, the associated risks are both pervasive and severe.
There is a heightened likelihood of exploitation by both state-sponsored actors and financially motivated adversaries. As such, organizations must treat remediation as a top priority to maintain operational resilience and protect critical infrastructure from potential compromise.
ASUS | Routers CVE-2021-32030
- Vulnerability Description: ASUS Lyra Mini and ASUS GT-AC2900 devices contain an improper authentication vulnerability that allows an attacker to gain unauthorized access to the administrative interface. The impacted products could be end-of-life (EoL) and/or end-of-service (EoS). Users should discontinue product utilization.
- Exploitation Details: The vulnerability lies in the router’s HTTP server, where a crafted asus_token cookie containing a null byte (\0) exploits flawed input validation in the handle_request and auth_check functions. The null byte causes premature string termination, allowing authentication bypass by matching a default value.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-02
- Recommended Mitigation Due Date: 2025-06-23
ConnectWise | ScreenConnect CVE-2025-3935
- Vulnerability Description: ConnectWise ScreenConnect contains an improper authentication vulnerability. This vulnerability could allow a ViewState code injection attack, which could allow remote code execution if machine keys are compromised.
- Exploitation Details: The vulnerability arises from the improper handling of ViewState data in ASP.NET Web Forms, which ScreenConnect utilizes. ViewState maintains page and control state between requests, with data encoded in Base64 and protected by machine keys (ValidationKey and DecryptionKey). If an attacker gains access to these machine keys, requiring privileged system-level access, they can craft a malicious ViewState payload. When this payload is sent to the server, it can lead to remote code execution.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-02
- Recommended Mitigation Due Date: 2025-06-23
Craft CMS CVE-2025-35939, CVE-2024-56145
- Vulnerability Description:
- CVE-2025-35939: Craft CMS contains an external control of assumed-immutable web parameter vulnerability. This vulnerability could allow an unauthenticated client to introduce arbitrary values, such as PHP code, to a known local file location on the server.
- CVE-2024-56145: Craft CMS contains a code injection vulnerability. Users with affected versions are vulnerable to remote code execution if their php.ini configuration has `register_argc_argv` enabled.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-02
- Recommended Mitigation Due Date: 2025-06-23
ASUS | RT-AX55 Routers CVE-2023-39780
- Vulnerability Description: ASUS RT-AX55 devices contain an OS command injection vulnerability that could allow a remote, authenticated attacker to execute arbitrary commands.
- Exploitation Details: Authenticated attackers can exploit this flaw to execute arbitrary operating system commands via the qos_bw_rulelist parameter in the /start_apply.htm endpoint
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-02
- Recommended Mitigation Due Date: 2025-06-23
Qualcomm | Multiple Chipsets CVE-2025-21479, CVE-2025-21480, CVE-2025-27038
- Vulnerability Description:
- CVE-2025-21479: Multiple Qualcomm chipsets contain an incorrect authorization vulnerability. This vulnerability allows for memory corruption due to unauthorized command execution in GPU micronode while executing specific sequence of commands.
- CVE-2025-21480: Multiple Qualcomm chipsets contain an incorrect authorization vulnerability. This vulnerability allows for memory corruption due to unauthorized command execution in GPU micronode while executing specific sequence of commands.
- CVE-2025-27038: Multiple Qualcomm chipsets contain a use-after-free vulnerability. This vulnerability allows for memory corruption while rendering graphics using Adreno GPU drivers in Chrome.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-03
- Recommended Mitigation Due Date: 2025-06-24
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share