Silent Intrusions and Stealthy Control: North Korean macOS Malware, DoNot APT Tactics, and Ransomware Trends Uncovered
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- North Korea’s Silent Infiltration: How Nim-Based Malware Exploits macOS Users in Crypto Firms
- Click, Exploit, Control: Inside the Stealthy Intrusion Tactics of DoNot APT
- Ransomware Activity Bulletin: Ransomware and Data Extortion Trends (July 1-7)
- Exploited Vulnerabilities in Synacor, Rails, PHP, and Looking Glass Products Added to CISA’s Catalog
North Korea’s Silent Infiltration: How Nim-Based Malware Exploits macOS Users in Crypto Firms
The Rundown
North Korean state-sponsored cyber actors have launched a sophisticated campaign targeting Web3 and cryptocurrency organizations, employing a novel macOS malware family dubbed “NimDoor.” This malware is notable for its use of the Nim programming language, a rarity in macOS threats, and its deployment of advanced techniques such as process injection and encrypted WebSocket communications. The campaign begins with social engineering tactics, where attackers impersonate trusted contacts via platforms like Telegram and Calendly to distribute malicious AppleScripts disguised as Zoom SDK updates. These scripts, heavily obfuscated with thousands of lines of whitespace, initiate a multi-stage attack chain that ultimately delivers the NimDoor payload.
Once installed, NimDoor exhibits several advanced features: it handles encrypted configurations, executes asynchronously using Nim’s native runtime, and employs a unique persistence mechanism that leverages system signals (SIGINT/SIGTERM) to reinstall itself upon termination or system reboot. Additionally, the malware utilizes AppleScripts as lightweight backdoors and Bash scripts to exfiltrate sensitive data, including Keychain credentials, browser information, and Telegram user data. The attackers also use domains resembling legitimate Zoom URLs to host malicious content, enhancing the credibility of their phishing attempts.
For businesses operating in the Web3 and cryptocurrency sectors, this campaign underscores the critical need for robust cybersecurity measures. Organizations should implement stringent employee training to recognize and report phishing attempts, enforce strict access controls, and deploy advanced endpoint detection and response solutions capable of identifying and mitigating such sophisticated threats. Regular security audits and staying informed about emerging threat vectors are essential to protect sensitive assets and maintain operational integrity in the face of evolving cyber threats.
Source Material: SentinelOne
Click, Exploit, Control: Inside the Stealthy Intrusion Tactics of DoNot APT
The Rundown
Trellix researchers uncovered a targeted cyber-espionage campaign by the DoNot APT group aimed at government entities in Southern Europe. The attack began with spear-phishing emails containing a Google Drive link, which hosted a password-protected RAR archive. This approach allowed the attackers to evade traditional email security measures by using a legitimate cloud service and encrypted file delivery, increasing the likelihood that the payload would reach its intended target undetected.
Once the victim downloaded and extracted the archive using the provided password, they encountered a malicious executable file. When executed, this binary initiated a multi-stage, memory-resident infection chain that executed embedded shellcode in a staged manner. Each stage loaded the next directly in memory, ultimately resulting in the deployment of a custom backdoor. This backdoor enabled remote command execution, data access, and system control, while leaving minimal forensic evidence on disk.
The operation demonstrated a high level of technical sophistication, particularly in its use of multi-stage shellcode, memory-only execution, and cloud-based delivery mechanisms. Command-and-control communications were conducted over HTTP, allowing traffic to blend in with normal web activity. For security teams, this campaign reinforces the importance of monitoring for behavioral anomalies, strengthening endpoint detection and response capabilities, and inspecting cloud-hosted links and password-protected archives in phishing scenarios.
Source Materials: Trellix
Ransomware Activity Bulletin: Ransomware and Data Extortion Trends (July 1-7)
The Rundown
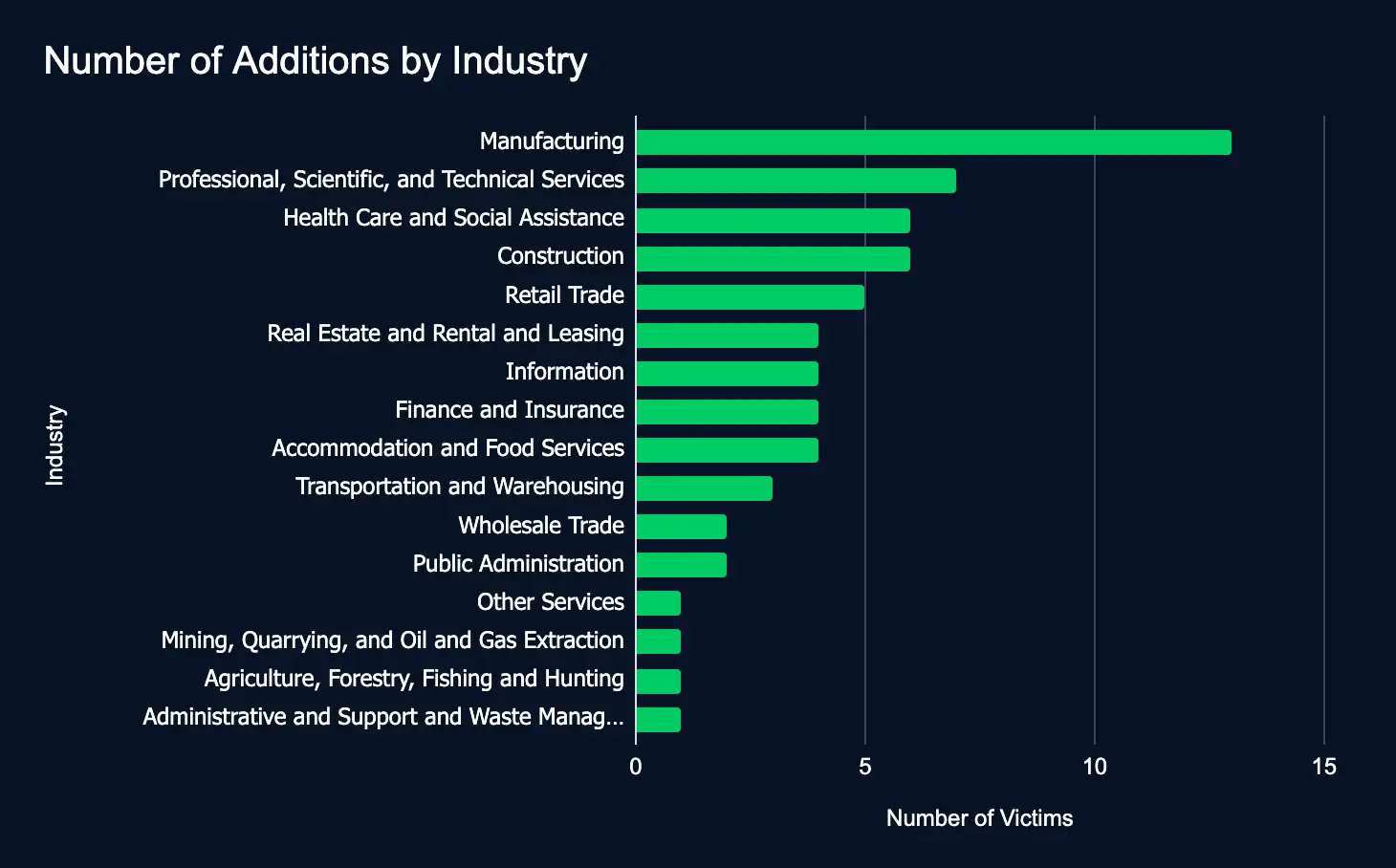
Between July 1 and 7, ransomware and data extortion activity declined, with 64 victim organizations reported across 18 leak sites, a 27% drop from the previous week’s total of 88. While this decrease may suggest a temporary slowdown, it more likely reflects a short-term stabilization in threat actor operations rather than a meaningful reduction in overall attack volume.
Key sectors such as Manufacturing, Professional Services, Health Care and Social Assistance, and Construction remained prime targets, emphasizing ongoing focus on high-value industries. A notable share of impacted organizations were based in strategic regions, including the United States, Canada, and Israel, indicating that geographic targeting remains a consistent priority. For business leaders, these trends reinforce the persistent, calculated nature of ransomware threats. Despite fluctuations in weekly figures, the risk to critical sectors remains high, underscoring the need for ongoing investment in prevention, detection, and incident response capabilities.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Health Care and Social Assistance
- Construction
- Most affected countries:
- United States
- Canada
- Israel
- Most active leak sites:
- Qilin
- Akira
- Play
- Handala
Exploited Vulnerabilities in Synacor, Rails, PHP, and Looking Glass Products Added to CISA’s Catalog
The Rundown
Between July 3 and July 9, CISA identified four high-severity vulnerabilities in products from Synacor, Rails, PHP, and Looking Glass, adding them to the Known Exploited Vulnerabilities catalog. This move reflects their confirmed use in active threat campaigns targeting a broad range of systems.
When left unpatched, these vulnerabilities create a serious security risk by offering attackers potential entry points for initial access and further compromise. Due to the widespread use of these technologies across multiple industries, the impact of exploitation could lead to significant operational disruption and damage to organizational reputation.
With growing attention from both state-sponsored actors and financially motivated attackers, rapid remediation is critical. Delayed action greatly increases the risk of exploitation and may result in broader security and business consequences.
Synacor | Zimbra Collaboration Suite (ZCS) CVE-2019-9621
- Vulnerability Description: Synacor Zimbra Collaboration Suite (ZCS) contains a server-side request forgery (SSRF) vulnerability via the ProxyServlet component.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-07
- Recommended Mitigation Due Date: 2025-07-28
Rails | Ruby on Rails CVE-2019-5418
- Vulnerability Description: Rails Ruby on Rails contains a path traversal vulnerability in Action View. Specially crafted accept headers in combination with calls to `render file:` can cause arbitrary files on the target server to be rendered, disclosing the file contents.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-07
- Recommended Mitigation Due Date: 2025-07-28
PHP | PHPMailer CVE-2016-10033
- Vulnerability Description: PHPMailer contains a command injection vulnerability because it fails to sanitize user-supplied input. Specifically, this issue affects the ‘mail()’ function of ‘class.phpmailer.php’ script. An attacker can exploit this issue to execute arbitrary code within the context of the application. Failed exploit attempts will result in a denial-of-service condition.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-07
- Recommended Mitigation Due Date: 2025-07-28
Looking Glass | Multi-Router Looking Glass (MRLG) CVE-2014-3931
- Vulnerability Description: Multi-Router Looking Glass (MRLG) contains a buffer overflow vulnerability that could allow remote attackers to cause an arbitrary memory write and memory corruption.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-07
- Recommended Mitigation Due Date: 2025-07-28
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share