What Happened?
Wordfence, a WordPress security company with over 4 million active installs of their WordPress plugin, has observed scanning and exploitation activity of internet-exposed systems targeting the unauthenticated, remote code execution vulnerability known as “Text4Shell,” tracked as CVE-2022-42899 beginning on 18 October. However, Wordfence’s telemetry may be limited to only WordPress sites; this doesn’t mean that scanning and exploitation activity is limited to only WordPress sites.
The payloads Wordfence has observed and tracked appear in query string parameters or headers and use one of the following formats:

Why Did it Happen?
Apache Commons Text is affected by an arbitrary code execution vulnerability dubbed “Text4Shell and is an open-source Java library with an “interpolation system” that allows the modification, decoding, generation, and escaping of strings based on inputted string lookups.
What is the Impact?
Despite the similarities to Log4Shell, Text4Shell is not as critical because applications using the interpolation defaults in the affected versions are not as widespread or exploitable. Applications rarely use the class and method involved in this vulnerability. In addition, a GitHub search shows very few open source code using the vulnerable method, and most do not parse user-controlled input.
However, CVE-2022-42899 has a CVSS score of 9.8 (critical); and affects versions 1.5 through 1.9. Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional communication with remote servers if using untrusted configuration values. If a threat actor were to successfully exploit the vulnerability, they can execute code on the targeted system, resulting in post-exploitation activity, for example dropping malware or executing LOLBins to laterally move within the environment.
What Will Adversaries Do Next?
Threat actors will likely continue scanning for and exploiting vulnerable hosts using the DNS and Script request methods. We base this assessment on Wordfence’s observation that most payloads use the DNS prefix method, the Script prefix as the second most common method observed, and the public availability of PoC exploit code.
How Do You Respond?
Identify products incorporating Apache Commons Text versions 1.5 through 1.9 and upgrade Apache Commons Text to 1.10.0, applying workarounds or patches as directed by the vendor. Qualys customers can scan for this vulnerability with the signature ID 377639.
Audit and Monitor Logs for:
Script Variant

- External web requests containing the string “script:javascript” (“script%3Ajavascript” with URL encoding). Malicious requests will also include a command like “curl” in the URL parameters as well as a remote server.
- Outbound web requests from affected appliances to rare servers (possibly with curl useragent) and general curl/wget command activity in process/auditd logs.
- Rare TLD’s like .fun, .pro, .xyz, .me, .onE, .online, etc may be useful in identifying this traffic
DNS Variant
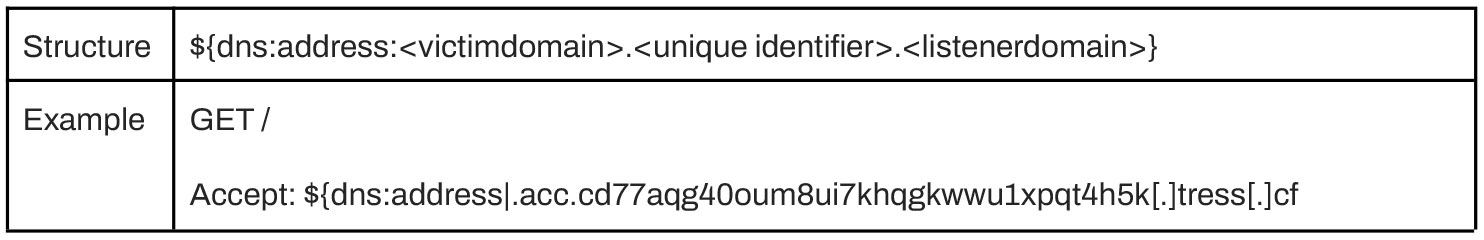
- External web requests containing the string “dns:address” followed by a remote server. While standard web logs may not contain header data, IDS solutions like Snort/Suricata will be able to parse header data and flag matches when detection via web logs is not available.
- Rare/anomalous outbound DNS queries from impacted appliances that could indicate vulnerability scanning and network fingerprinting.
- Rare TLD’s like .fun, .pro, .xyz, .me, .onE, .online, etc may be useful in identifying this traffic
URL Variant
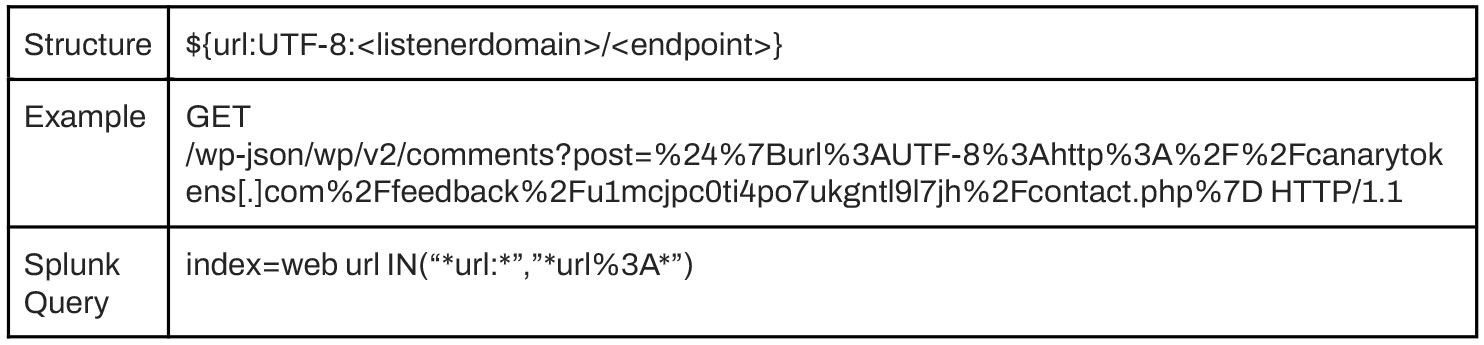
Observables
Note:
Observables are properties (such as an IP address, MD5 hash, or the value of a registry key) or measurable events (such as the creation of a registry key or a user) and are not indicators of compromise. The observables listed below are intended to provide contextual information only. Deepwatch evaluates the observables and applies those it deems appropriate to our detections.
Observing sets of these properties (observables) could be an indicator of compromise. For instance, observing an IP address, creation of a user with admin privileges and a registry key could be indicators of compromise and should be investigated further.
| Description | Value | |
| IP addresses sending requests targeting the vulnerability. Note: IP addresses marked with an “*” have targeted multiple sites. |
103.127.158.166* 207.180.241.85* 159.180.168.60* 159.180.168.61* 206.189.150.65* 13.53.121.211* 165.227.196.68* 46.101.177.159* 37.120.189.196* 161.97.122.174* 52.94.133.128* 72.21.196.64* 66.94.113.40* 199.16.53.138* 3.232.79.59* 66.94.110.66* 52.202.251.117* 207.154.234.251 103.162.75.6 |
20.9.198.105 164.90.174.6 161.97.132.171 159.223.26.207 181.215.176.86 139.59.210.202 194.163.185.138 62.171.165.202 159.89.185.54 144.126.131.64 38.242.242.52 157.230.29.154 209.126.10.16 164.92.136.114 80.152.226.29 66.94.110.65 161.97.74.59 20.112.84.178 38.242.147.244 |
| Listener hosts Note: According to Wordfence, most listeners are running Interactsh servers, and legitimate security teams frequently use these servers to test for out-of-band interactions and may have sent requests from some of these listener hosts. |
tress.cf oast.online oast.site oast.live oast.me blsops.com dnslog.cn acpk.xyz |
oast.fun ligame.xyz oast.pro vii.onE 13.58.100.198 canarytokens.com |
Share