Executive Summary
This Customer Advisory report provides an analysis of the exploitation of Fortinet devices vulnerable to a critical vulnerability, CVE-2023-27997, by threat actors. The vulnerabilities primarily affect FortiOS and FortiProxy with SSL-VPN enabled, posing significant risks to organizations using these devices. Threat actors, particularly state-sponsored ones, have been known to exploit such vulnerabilities. In particular, Chinese state-sponsored threat actors, like Volt Typhoon, have a history of gaining initial access through Fortinet devices.
The potential consequences of successful exploitation are substantial, including sensitive data exfiltration leading to intellectual property theft and possible service disruptions, particularly for critical infrastructure organizations.
Our assessment suggests that the exploitation of such vulnerabilities will continue, especially by state-sponsored actors targeting high-value information. As such, immediate mitigative action is crucial. We recommend that affected organizations upgrade to the latest firmware immediately or disable SSL-VPN as a workaround. Additionally, reviewing systems for evidence of previous exploitation and following Fortinet’s hardening recommendations is advised. It’s essential to disable unused features and manage devices using an out-of-band method to minimize the risk of future exploitations.
ATI Insights & Determinations
- This vulnerability has reportedly been exploited in limited instances, and CISA has included it in its Known Exploited Vulnerabilities Catalog, indicating it has been exploited or is currently being exploited.
- The exploitation of Fortinet devices vulnerable to CVE-2023-27997, a critical heap-based buffer overflow vulnerability, presents a significant threat that could allow remote threat actors to execute arbitrary code or commands.
- Chinese state-sponsored threat actors, such as Volt Typhoon, have a history of exploiting vulnerabilities in Fortinet devices. While not linked directly to the exploitation of CVE-2023-27997, these groups’ modus operandi underscores the potential risks associated with this vulnerability.
- The exploitation of this vulnerability could have severe impacts, including potential data exfiltration leading to substantial financial losses, service disruptions affecting business and societal operations, and significant reputational damage.
- Given the trend of threat actors exploiting vulnerable internet-facing managed security devices, it is highly likely that such exploitations will continue, primarily targeting high-value targets with information valuable to the nation’s interests.
- Recommend mitigative actions should occur immediately, which includes upgrading to the latest firmware or disabling SSL-VPN as a workaround.
Introduction
This Customer Advisory provides an analysis of the exploitation of Fortinet devices vulnerable to CVE-2023-27997. This report aims to provide historical details on the tactics, techniques, and procedures (TTPs) used by threat actors, assess the potential risks and impacts, and provide actionable mitigation strategies. The report’s scope covers the analysis of internal data and publicly available information. The objective is to equip decision-makers with the necessary information to anticipate and effectively respond to this emerging threat. Questions or feedback about this intelligence can be submitted here.
Overview
A critical heap-based buffer overflow vulnerability in FortiOS and FortiProxy, CVE-2023-27997, has been exploited. Successful exploitation could allow a remote threat actor to execute arbitrary code or commands via specifically crafted requests. The vulnerability affects the following versions of FortiOS and FortiProxy, which are typically internet-facing:
FortiOS
- version 7.2.4 and below
- version 7.0.11 and below
- version 6.4.12 and below
- version 6.0.16 and below
FortiProxy
- version 7.2.3 and below
- version 7.0.9 and below
- version 2.0.12 and below
- version 1.2, all versions
- version 1.1, all versions
Overview & Background
After the in-the-wild exploitation of the FG-IR-22-398 / CVE-2022-42475 incident on January 11, 2023, which involved a heap-based buffer overflow in FortiOS SSL VPN, the Fortinet Product Security Incident Response Team (PSIRT) took proactive measures to conduct a thorough examination of the SSL-VPN module. As a result of this audit and a responsible disclosure from an external researcher, several vulnerabilities were identified and promptly addressed in the latest firmware updates.
The PSIRT team released a statement on 12 June 2023, where they determined that threat actors may have exploited CVE-2023-27997 in a limited number of instances. In light of this finding, Fortinet strongly advises customers who have SSL-VPN enabled to take immediate action by upgrading to the latest firmware release. Although the risk associated with this issue is reduced for customers not utilizing SSL-VPN, Fortinet still recommends performing the upgrade as a precautionary measure. However, on
13 June, CISA added the vulnerability to its Known Exploited Vulnerabilities Catalog.
Threat Analysis
CISA added CVE-2023-27997 to its Known Exploited Vulnerabilities Catalog on 13 June 2023, with a mitigation due date of 4 July 2023. The main criteria for inclusion into CISA’s Known Exploited Vulnerabilities Catalog, is whether the vulnerability has been exploited or is under active exploitation. The active exploitation term, as defined by CISA, also includes attempted exploitation and successful exploitation.
Currently, CISA lists 11 known Fortinet vulnerabilities exploited by threat actors, including three other vulnerabilities targeting FortiOS SSL-VPN devices. Threat actors have a history of exploiting vulnerabilities in Fortinet devices. In one example published in mid-March 2023, Mandiant detailed how state-sponsored threat actors exploited a zero-day vulnerability in FortiOS (CVE-2022-41328) in 2022 and deployed multiple custom malware families on Fortinet devices to maintain persistence.
Recently Microsoft Threat Intelligence published a report on a cyber espionage campaign they are attributing to the Chinese state-sponsored threat actor Volt Typhoon. In the report, Microsoft states that Volt Typhoon achieves initial access through internet-facing Fortinet devices. However, Fortinet is not linking the possible exploitation of CVE-2023-27997 to the Volt Typhoon campaign. According to Fortinet, Volt Typhoon appears to exploit vulnerabilities, primarily CVE-2022-40684, for initial access. In this campaign, Volt Typhoon eschewed the use of malware and instead used “living off the land” binaries, also known as LOLBins.
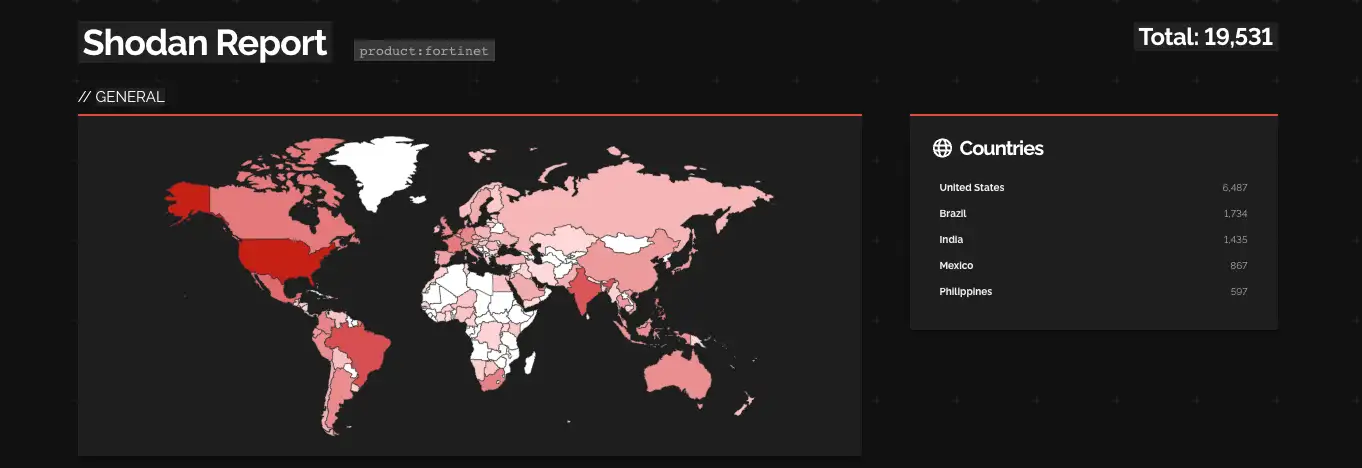
A recent Shodan search reveals over 19,000 internet-exposed Fortinet devices. However, only a fraction of these devices are vulnerable to CVE-2023-27997. According to Shodan’s data, the US has the most internet-exposed devices with over 6,000, followed by Brazil, India, and Mexico.
Risk & Impact Assessment
The risks posed by threat actors exploiting the vulnerability can be significant. The potential impact on organizations can be multi-fold. Firstly, sensitive data exfiltration could lead to intellectual property theft, and espionage activities, resulting in substantial financial losses, stemming not only from immediate recovery efforts but also potential lawsuits and regulatory fines due to breaches in data privacy laws.
Secondly, service disruptions, particularly for critical infrastructure organizations, could have cascading effects, interrupting business operations and potentially affecting broader societal functions, thus leading to further financial losses.
Finally, a successful intrusion could inflict significant reputational damage, leading to loss of customer trust, damaging business relationships, and possibly resulting in loss of market share. The convergence of these impacts underscores the importance of implementing prompt and effective risk mitigation strategies to manage this severe threat.
Outlook
Threat actors are highly likely to continue exploiting vulnerable internet-facing managed security devices (e.g., firewalls, VPN Gateways and access portals, etc.), especially Chinese state-sponsored threat actors who have a history of exploiting these devices. However, the resources required to develop the exploits and compromise these devices can be intensive, and typically used in operations against high priority targets with information valuable to a nation’s interest.
ATI Actions & Recommendations
ATI conducts further detection assessment and threat hunting from data reported in this intelligence report. However, not all activity can be hunted, detected, or monitored due to limitations in log sources received by Deepwatch.
ATI recommends mitigative action occur immediately, which includes upgrading to the latest firmware or disabling SSL-VPN as a workaround, reviewing systems for evidence of exploitation of previous vulnerabilities (FG-IR-22-377 / CVE-2022-40684), following Fortinet’s hardening recommendations, disabling unused features, and managing devices via an out-of-band method.
Organizations employing Tenable’s Nessus vulnerability scanning solution can use plugin ID 177116 to identify vulnerable systems. Organizations employing Qualys vulnerability scanning solution can use Qualys ID 44059 to identify vulnerable systems.
In addition to the recommendations, CISA issued the Binding Operational Directive 23-02, which directs federal, executive branch, departments and agencies specific actions to safeguard federal information and information systems. This directive requires these agencies to remove the networked management interface (routers, switches, firewalls, VPN concentrators, proxies, etc.) from the internet by making it only accessible from an internal enterprise network, and deploy capabilities that enforce access control to the interface. While the primary audience for this directive is federal executive branch agencies, private organizations can greatly benefit from implementing these measures.
BOLO and Relevant Detections Guidance
We recommend all organizations retrospectively hunt for malicious activity, which will likely indicate compromise, using the threat hunting guidance provided below. Deepwatch hunts for this activity in our customer base when the applicable data is available within Splunk. When customers opt not to send the relevant logs to Splunk, we recommend those customers retrospectively hunt following the guidelines listed below.
Be On the Lookout (BOLO)
- Unexpected/unauthorized addition of admin users on impacted appliances
- Rare/anomalous commands being run on vulnerable appliances
- Examples of malicious commands from previous RCE’s that create new admin user:
- show system admin
- edit “fortigate-tech-support”
- set accprofile “super_admin”
- set vdom “root”
- set password ENC […]
- Examples of malicious commands from previous RCE’s that create new admin user:
- Rare outbound network connections to geographically anomalous destinations
Share