What You Need to Know
- A now-patched vulnerability, tracked as CVE-2022-30525, in Zyxel firewalls and VPN devices (a list of affected devices can be found below) is now being reported as being actively exploited after proof-of-concept exploit code and a Metasploit module were released.
- If successfully exploited, a remote unauthenticated threat actor could conduct arbitrary code execution as the nobody user on vulnerable devices.
- Observation of this activity may be possible by auditing your logs for HTTP POST activity to the URI “/ztp/cgi-bin/handler” of relevant systems. Additional observation opportunities can be found in the Be On the Lookout section below.
- Fixes for the affected products are available in firmware version ZLD V5.30. If you are unable to update to the latest version at this time, it is recommended to disable WAN access to the administrative web interface on affected systems.
- Deepwatch Experts are identifying customers that this vulnerability may impact and evaluating the detection strategy for this exploitation.
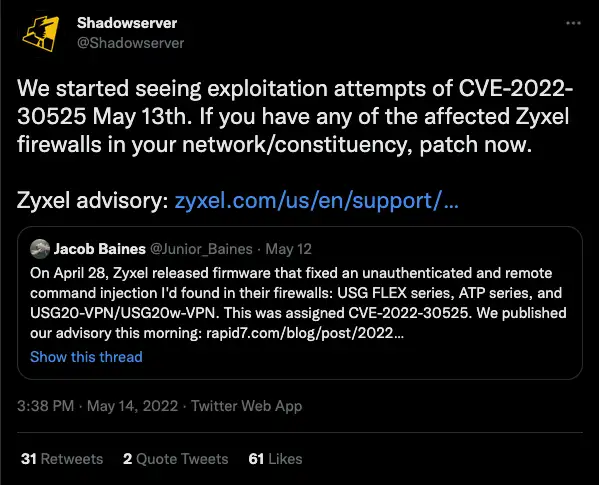
Starting on May 13th, ShadowServer Foundation reported that they have observed exploitation attempts of a now-patched critical command injection vulnerability in Zyxel Firewall and VPN products, tracked as CVE-2022-30525.
The critical vulnerability allows a remote unauthenticated threat actor to conduct arbitrary code execution as the nobody user on vulnerable devices and was first discovered in early April by Rapid7, with Zyxel releasing “silent” fixes on April 28. Finally, on May 12, Rapid7 disclosed the vulnerability on their blog with proof-of-concept exploit code and a Metasploit module being released on the same day. Two days later, ShadowServer Foundation, a non-profit security organization, reported that they observed active exploitation beginning May 13.
Vulnerability Details
Jake Baines, a security researcher at Rapid7, first discovered the vulnerability (CVE-2022-30525) in early April and published a vulnerability disclosure report on May 12. According to the report, the vulnerability “allows an unauthenticated and remote attacker to achieve arbitrary code execution as the nobody user on the affected device.”
Exploitation of the vulnerability is “through the “/ztp/cgi-bin/handler” URI and is the result of passing unsanitized attacker input into the os.system method in lib_wan_settings.py. The vulnerable functionality is invoked in association with the setWanPortSt command. An attacker can inject arbitrary commands into the mtu or the data parameter.”
Affected Products & Mitigation Recommendations
Zyxel released a security advisory on May 12 announcing that the following products are affected:
USG FLEX (Firmware version: ZLD V5.00 through ZLD V5.21 Patch 1)
- 100
- 100W
- 200
- 500
- 700
USG FLEX (Firmware version: ZLD V5.10 through ZLD V5.21 Patch 1)
- 50
- 50W
- USG20-VPN
- USG20W-VPN
Additionally, ATP series firmware versions ZLD V5.10 through ZLD V5.21 Patch 1 and VPN series firmware versions ZLD V4.60 through ZLD V5.21 Patch 1 are also affected.
According to a Shodan search conducted by the Deepwatch Threat Intel Team, there are approximately 16,500 Zyxel Firewall and VPN internet-exposed devices that are potentially vulnerable to CVE-2022-30525.
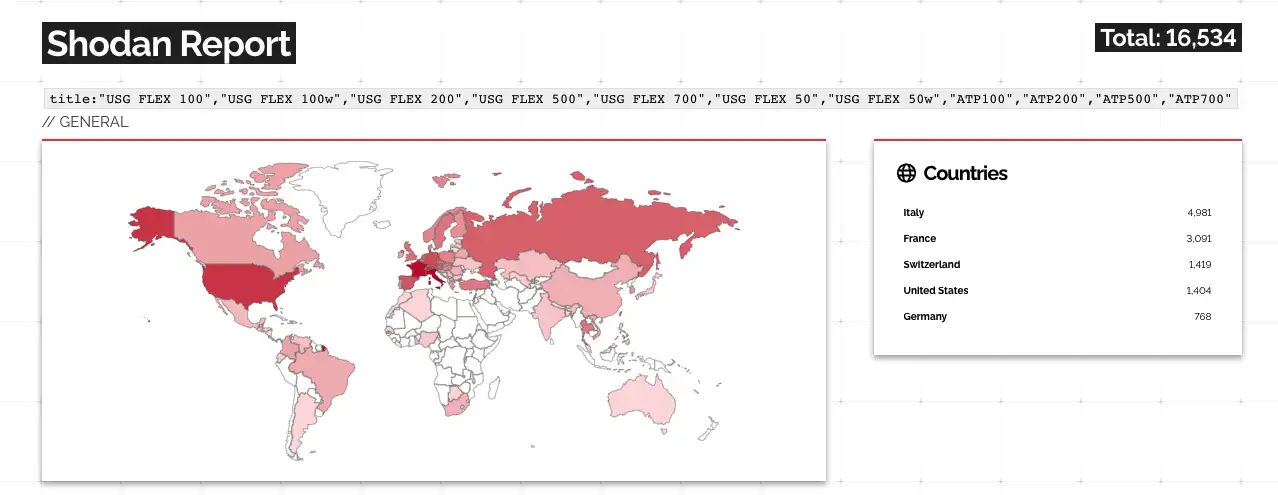
Fixes for the affected products were first made available on April 28 in firmware version ZLD V5.30. Organizations that are unable to update to the latest version at this time are advised to disable WAN access to the administrative web interface on affected systems.
Proof-of-Concept Exploit Code Released & Active Exploitation
Coinciding with Rapid7’s blog post, Jake Baines published proof-of-concept (PoC) exploit code to his personal GitHub account along with Rapid7 publishing a Metasploit module to their GitHub account.
Within two days of Rapid7’s blog post and the accompanying PoC and Metasploit module being released, ShadowServer foundation reported via Twitter that they observed active exploitation attempts beginning on May 13.
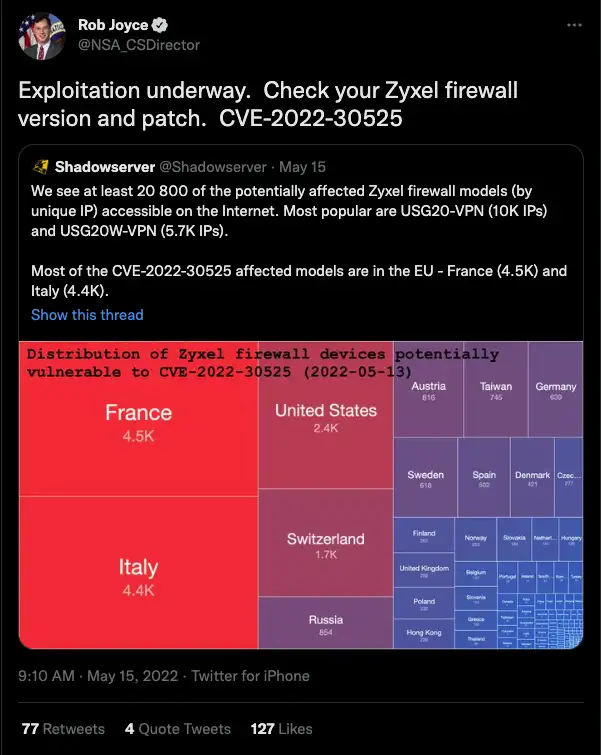
The vulnerability even caught the eye of the NSA’s Director of Cybersecurity, Rob Joyce, who on May 15 retweeted ShadowServer’s tweet stating that they identified 20,800 Zyxwl devices, with Rob adding “Exploitation underway. Check your Zyxel firewall version and patch. CVE-2022-30525.”
Be On the Lookout (BOLO)
Deepwatch Experts are identifying customers that this vulnerability may impact and evaluating the detection strategy for this exploitation. Additionally, observation of this activity may be possible by auditing your logs for the following items:
- HTTP POST activity to the URI “/ztp/cgi-bin/handler” of relevant systems.
- POST requests to “/ztp/cgi-bin/handler” using the command “setWanPortSt” (specifically ‘mtu’ and ‘data’ parameters) for malicious commands.
- Unexpected outbound network traffic and service/firewall modification that could indicate compromise.
Deepwatch Threat Intel Outlook
With a Metasploit module, publicly available exploits, and a report of active exploitation, it is likely that threat actors will target customers with vulnerable devices to gain initial access or conduct lateral movement, in order to deploy various types of malicious software, such as: ransomware, coinminers, backdoors, bots, etc.
Conclusion
The amount of time (one day) it took for threat actors to take publicly available exploit code and begin active exploitation only highlights the importance for customers to implement a patch management program. Your patch management program should focus on regularly scanning systems for vulnerabilities (like those featured in CISA’s Known Exploited Vulnerabilities Catalog) and patching them as soon as possible, with a priority placed on those that are internet-exposed.
Sources
https://www.zyxel.com/us/en/support/Zyxel-security-advisory-for-OS-command-injection-vulnerability-of-firewalls.shtml
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2022-30525
https://twitter.com/NSA_CSDirector/status/1525825839262203906?s=20&t=RcQiStAMAdKGSVeu0xep3A
https://www.rapid7.com/blog/post/2022/05/12/cve-2022-30525-fixed-zyxel-firewall-unauthenticated-remote-command-injection/
https://www.shodan.io/search/report?query=title%3A%22USG+FLEX+100%22%2C%22USG+FLEX+100w%22%2C%22USG+FLEX+200%22%2C%22USG+FLEX+500%22%2C%22USG+FLEX+700%22%2C%22USG+FLEX+50%22%2C%22USG+FLEX+50w%22%2C%22ATP100%22%2C%22ATP200%22%2C%22ATP500%22%2C%22ATP700%22
https://twitter.com/Shadowserver/status/1525561213115158529?s=20&t=XZMbQipz-s3VHKuiCpiUDw
https://github.com/jbaines-r7/victorian_machinery/blob/main/README.md
https://github.com/rapid7/metasploit-framework/pull/16563
Share