Update
Deepwatch Threat Intel Team is aware that additional security researchers have also reported observing active exploitation of this vulnerability. CronUp security researcher Germán Fernández tweeted the following:
“I am seeing the massive F5 BIG-IP CVE-2022-1388 (RCE) exploit, installing #Webshell in /usr/local/www/xui/common/css/ as a backdoor to maintain access.
Attacks from:
- 216.162.206[.]213
- 209.127.252[.]207
Payload writes to /tmp/f5.sh, executes and removes.”
Based on this new information, Deepwatch is evaluating the detection strategy for this exploitation. Additionally, we have added the following to the “Be On the Lookout (BOLO)” section below:
- Monitor for the creation or deletion of “/tmp/f5.sh” (or any unexpected script in the temp directory) and the existence of PHP or other script files in the “/usr/local/www/xui/common/css/” directory.
- While threat actors have been observed installing webshells at the above location, it is advisable to audit for additional script files, like .php, inside the web directory of BIG-IP appliances as the installation characteristics may differ.
- Monitor command and network history for suspicious outbound curl or wget traffic that may indicate malicious commands fetching additional components from external sources.
What You Need to Know
- Report of active exploitation and exploit code has been made publicly available for a critical remote-code-execution (RCE) vulnerability in F5 BIG_IP products.
- Successful exploitation of this vulnerability could allow an unauthenticated threat actor “with network access to the BIG-IP system through the management port and/or self IP addresses to execute commands, create and delete files, and disable services.”
- Observation of this activity may be possible by auditing your logs for inbound web traffic with the URL of /mgmt/tm/util/bash. Additional observation opportunities can be found in the “Be On the Lookout” section below.
- Fixes are available in versions 17.0.0, 16.1.2.2, 15.1.5.1, 14.1.4.6, and 13.1.5. Firmware versions 11.x and 12.x will not receive security updates and users relying on those versions should consider upgrading to a newer version or apply the workarounds listed in the “Affected Products and Mitigation Recommendations” section below.
Overview
A security researcher has reported active exploitation and exploit code has been made publicly available for CVE-2022-1388 (critical 9.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), a critical vulnerability affecting F5’s BIG-IP products. Successful exploitation of this vulnerability could allow an unauthenticated threat actor to execute commands, create and delete files, and disable services.
Background
On May 4, F5 released a security advisory for the vulnerability that affects several BIG-IP versions. A few days later, Positive Technologies and Horizon3 were able to create proof-of-concept (PoC) exploits for the vulnerability, with Horizon3 releasing their PoC this morning.
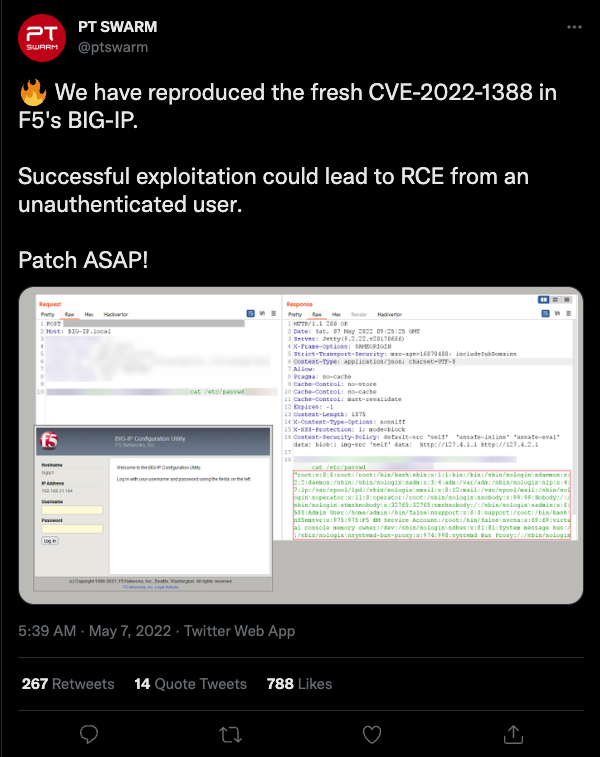
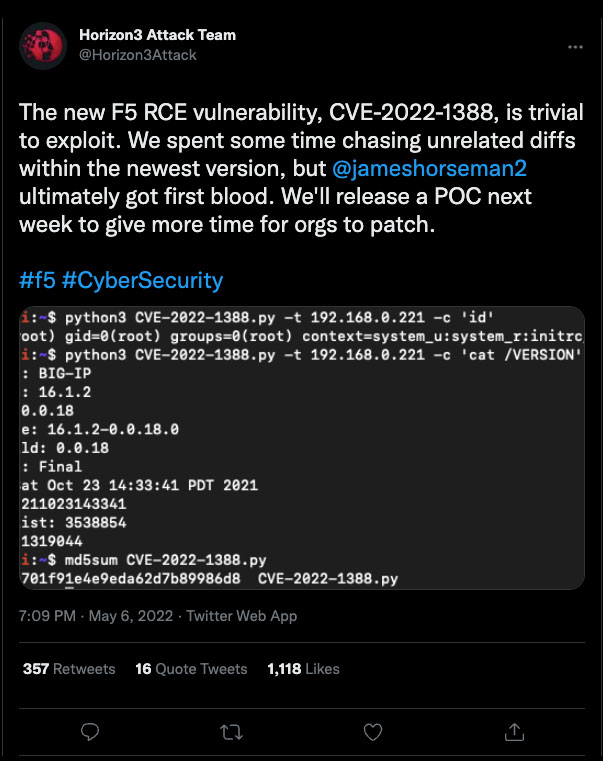
In an emailed statement to Bleeping Computer on May 8, Zach Hanley, Chief Attack Engineer at Horizon3, said that “the mitigations released by F5 for CVE-2022-1388 were a very large hint at where to look when reversing the application, we expect that threat actors may have also discovered the root cause as well.” He also stated that it took them two days to discover the exploit.
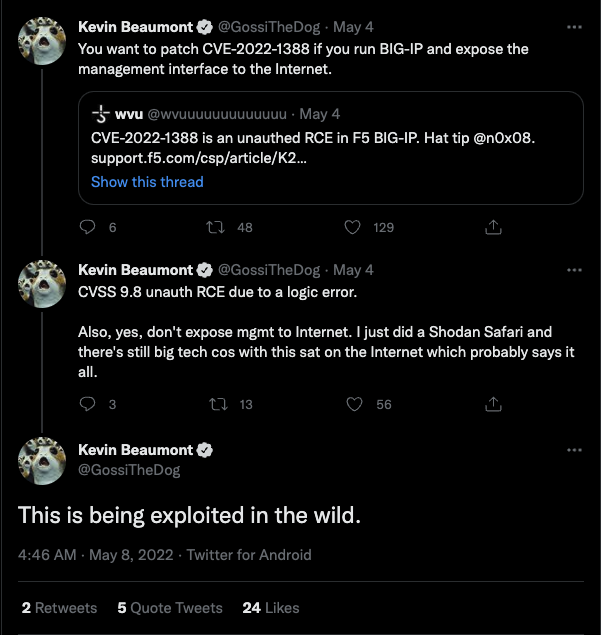
Within four days of the vulnerability being disclosed, security researcher Kevin Beaumont tweeted on May 8 that the vulnerability was being actively exploited in the wild.
Vulnerability Details
According to F5’s security advisory the “vulnerability may allow an unauthenticated attacker with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands, create or delete files, or disable services. There is no data plane exposure; this is a control plane issue only.”
Affected Products and Mitigation Recommendations
The critical security vulnerability impacts the following versions of BIG-IP products:
- 16.1.0 – 16.1.2
- 15.1.0 – 15.1.5
- 14.1.0 – 14.1.4
- 13.1.0 – 13.1.4
- 12.1.0 – 12.1.6
- 11.6.1 – 11.6.5
Fixes are available in versions 17.0.0, 16.1.2.2, 15.1.5.1, 14.1.4.6, and 13.1.5. Firmware versions 11.x and 12.x will not receive security updates and users relying on those versions should consider upgrading to a newer version or apply the following workarounds provided by F5:
- Block iControl REST access through the self IP address.
- Block iControl REST access through the management interface.
- Modify the BIG-IP httpd configuration.
Be On the Lookout (BOLO)
Deepwatch Experts are identifying customers that this vulnerability may impact and evaluating the detection strategy for this exploitation. Additionally, observation of this activity may be possible by auditing your logs for the following items:
- Inbound web traffic with the URL of /mgmt/tm/util/bash to BIG-IP appliances with an internet-exposed management interface.
- Inbound web traffic with basic authentication containing X-F5-Auth-Token and a JSON payload:
Note: * = field is set and/or contains a partial match- Authorization: Basic *
- X-F5-Auth-Token: *
- Content-Type: application/json
- Creation or deletion of “/tmp/f5.sh” (or any unexpected script in the temp directory) and the existence of PHP or other script files in the “/usr/local/www/xui/common/css/” directory.
- While threat actors have been observed installing webshells at the above location, it is advisable to audit for additional script files, like .php, inside the web directory of BIG-IP appliances as the installation characteristics may differ.
- Command and network history for suspicious outbound curl or wget traffic that may indicate malicious commands fetching additional components from external sources.
Deepwatch Threat Intel Outlook
With publicly available exploits and a report of active exploitation, it is very likely that threat actors will use the publicly available exploit code to gain initial access into an organization for further intrusion activities, like the deployment of ransomware, malware, coinminers, backdoors, and bots.
Sources
https://support.f5.com/csp/article/K23605346
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2022-1388
https://github.com/horizon3ai/CVE-2022-1388
https://www.bleepingcomputer.com/news/security/exploits-created-for-critical-f5-big-ip-flaw-install-patch-immediately/
https://twitter.com/ptswarm/status/1522873828896034816?s=20&t=dbIfGAiz-nb1VK9yacemmw
https://twitter.com/Horizon3Attack/status/1522715182014902272?s=20&t=cQU7FKMQF1CRd52gXny53w
https://twitter.com/GossiTheDog/status/1523222846474014720?s=20&t=xnQSGuHR0oqxfYsJ-K3img
https://twitter.com/Horizon3Attack/status/1523634533400461312?s=20&t=17VkGd7OC1neZLHUp4g_Cw
Share