What You Need to Know
- Security researchers at Faraday presented at Defcon 30 their discovery of a remote code execution vulnerability, CVE-2022-27255, in Realtek’s SDK for eCos OS.
- With their technical analysis presentation, the researchers also released four proofs-of-concept exploit codes on Faraday’s GitHub repository. A single UDP packet is all it takes to exploit this vulnerability.
- According to the researchers, the vulnerability affects 31 devices from at least 19 vendors. However, more may be vulnerable and have not been identified yet. Realtek released a patch in March, and it is up to OEM vendors to provide this patch to end-users.
- Deepwatch Squads are identifying customers that may be impacted by this vulnerability and evaluating the detection strategy for this exploitation.
On August 14, at the annual Defcon security conference held each year in Las Vegas, security researchers Octavio Gianatiempo and Octavio Galland, from the cybersecurity firm Faraday, were on stage at 3:00 PM to present their talk “Exploring the hidden attack surface of OEM IoT devices: pwning thousands of routers with a vulnerability in Realtek’s SDK for eCos OS.”
Their presentation discussed how they discovered a vulnerability, tracked as CVE-2022-27255, that requires no authentication or victim interaction and could achieve remote code execution. Along with their presentation, the researchers also released exploit code on Faraday’s GitHub. The vulnerability is believed to affect hundreds of thousands, if not millions, of devices using Realtek’s Software Development Kit (SDK) for eCos OS.
If successfully exploited, a threat actor could crash the device, harming accessibility to sensitive data or disrupting business operations. Furthermore, adversaries could execute malicious code on the device leading to further malicious activities.
Vulnerability Details
According to Realtek’s security advisory, devices using Realtek’s eCos SDK OS firmware before March 2022 are vulnerable to CVE-2022-27255. The vulnerability lies in the ‘SIP ALG’ module, which is vulnerable to buffer overflow. The root cause of the vulnerability is “insufficient validation on the received buffer, and unsafe calls to strcpy. The ‘SIP ALG’ module calls strcpy to copy some contents of SIP (session initiation protocol) packets to a predefined fixed buffer and does not check the length of the copied contents.”
A threat actor can “exploit the vulnerability through a WAN interface by crafting arguments in SDP [session description protocol] data or the SIP header to make a specific SIP packet, and the successful exploitation would cause a crash or achieve remote code execution.”
Affected Products
The vulnerability affects any product using Realtek’s eCos SDK OS series rtl819x-eCos-v0.x or rtl819x-eCos-v1.x.
According to the researchers, the vulnerability affects 31 devices from at least 19 vendors. However, more may be vulnerable and have not been identified yet. Faraday has provided code to automate the identification of firmware that may be vulnerable to CVE-2022-27255.
During their presentation, the researchers showed the following slides (Figures 1 & 2) that show the number of vulnerable devices sold in Argentina from a popular Argentian online retailer and another showing over 63,000 devices that have their admin panel exposed to the internet.
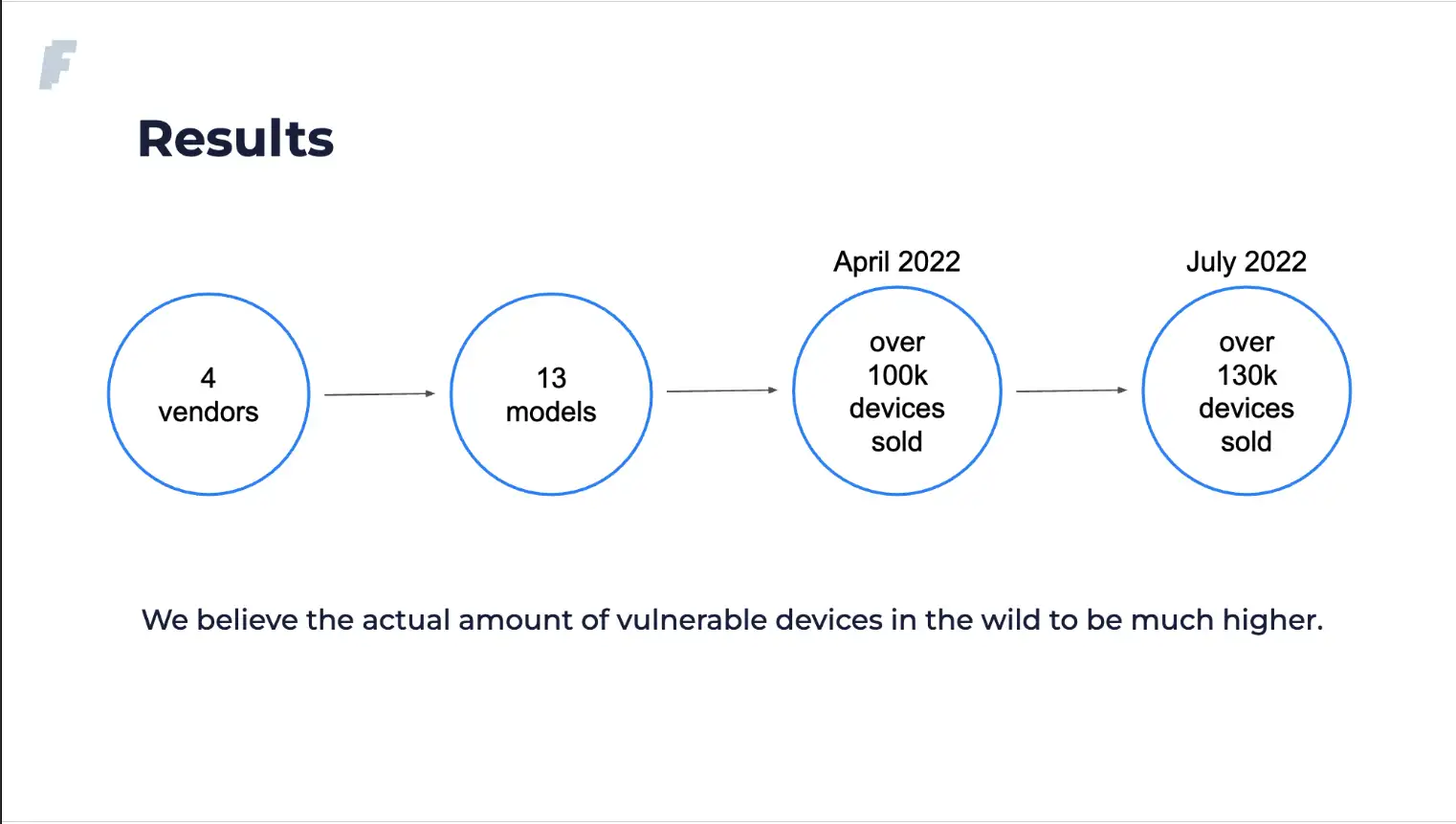
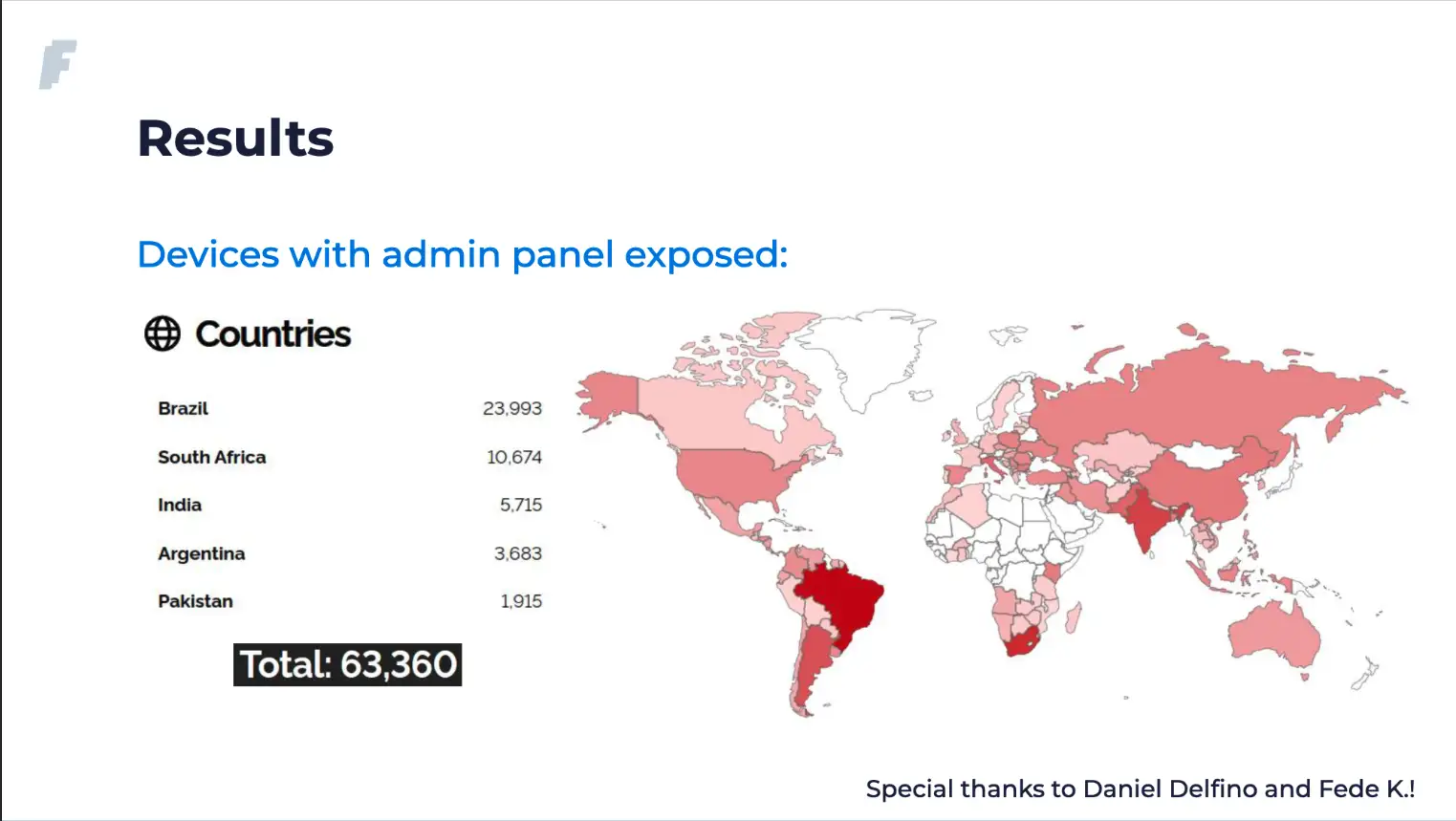
According to Johannes Ullrich of SANS Internet Storm Center, devices using the Realtek eCOS SDK firmware before March 2022 are vulnerable; devices are vulnerable even if the admin interface is not exposed to the internet; a single UDP packet to an arbitrary port can exploit the vulnerability; some IoT devices using the firmware may also be vulnerable.
What You Need to Do
Realtek has issued a patch (20220314_ecos_fix_crash_caused_by_vulnerability_of_sip_alg.rar) to OEM vendors, and it is advised that all organizations ensure that their devices are updated and inform employees who may access corporate networks from personal devices, about the importance of keeping devices updated with the latest security patches.
Additional recommendations include blocking unsolicited UDP requests at the firewall and ensuring that routers and other IoT devices are updated and supported by their manufacturers.
The following snort rule provided by Johannes Ullrich could be used to observe possible exploitation activity related to the PoC:
/ alert udp any any -> any any (sid:1000000; \
msg:"Realtek eCOS SDK SIP Traffic Exploit CVE-2022-27255"; \
content: "invite"; depth: 6; nocase; \
content: "m=audio "; \
isdataat: 128,relative; content:!"|0d|"; within: 128;)Johannes Ullrich does note that “you may want to adjust the target IP from “any” to the IP address of the device that you are protecting.”
Additionally, organizations are advised to Be On the Lookout (BOLO) and Monitor Logs for:
- Firewall/network logs matching the conditions below:
- Allowed inbound Telnet (port 23/TCP) traffic/login activity preceded by SIP UDP traffic from the same IP (likely within a very small time frame).
- Outbound network traffic to an IP after recent inbound SIP traffic from the same external source.
- UDP Packet/Body Characteristics (see Suricata signature above).
- UDP packet body containing the strings “m=audio” AND “invite.”
- More than 128 bytes after the “m=audio” string (allocated buffer for Realtek SDK).
- String of at least 256 characters in the UDP body.
- Unexpected password resets on vulnerable devices (achievable with specific shellcode in exploit).
Conclusion
Remote working has brought about the mixing of corporate networks and residential networks, and sensitive data may be accessed by routers designed for consumer use. The researchers state that these devices may not be designed with the necessary security of these products in mind.
Analyst Note: From the research presented, threat actors are likely to exploit this vulnerability to execute malicious code on the device, modify settings, intercept network traffic, and scan for other devices on the local network, some of which may be corporate assets.
Customers and organizations are encouraged to implement the guidance and recommendations set out in the “What You Need to Do” section above. Furthermore, Deepwatch Squads are identifying customers that this vulnerability may impact while Deepwatch Threat Intelligence Researchers evaluate the detection strategy for this exploitation.
Deepwatch, a leader in managed security services, protects our customers from ever-increasing cyber threats 24/7/365. Powered by curated threat intelligence produced by our Threat Intel Team, our cloud-based security operations platform provides the industry’s most comprehensive detection and automated response to cyber threats. In addition, dedicated experts provide our tailored guidance to mitigate risk and measurably improve security postures. As a result, hundreds of organizations, from Fortune 100 to mid-sized enterprises, trust Deepwatch to protect their business. Visit www.deepwatch.com to learn more.
↑
Share