Rhadamanthys Infostealer, Credit Card Skimmer in Fake Meta Pixel Tracker, and Operation Midnight Eclipse
This week: one threat actor shifts its arsenal to employ LNK files and the Rhadamanthys infostealer; another embeds a credit card skimmer in a concealed malicious Meta (Facebook) Pixel tracker script; and problems continue for vulnerable Palo Alto Networks PAN-OS software.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- TA547 Shifts Technique and Arsenal, Now Employing LNK Files and Rhadamanthys Infostealer
- Cybercriminals Compromise eCommerce Sites to Deploy Credit Card Skimmer in Fake Facebook Pixel Tracker Script
- CVE-2024-3400 Exploitation Activity Disclosed
- Latest Additions to Data Leak Sites
- CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
TA547 Shifts Technique and Arsenal, Now Employing LNK Files and Rhadamanthys Infostealer
Phishing – Malware – Information Theft – Social Engineering – Infostealer – Rhadamanthys – PowerShell – TA547 – All Industries
Overview
Proofpoint identified that the financially motivated cybercriminal TA547 targeted German organizations with a phishing email campaign delivering Rhadamanthys malware. This campaign is the first time Proofpoint has observed TA547 use Rhadamanthys, an information stealer that multiple cybercriminals use. Additionally, TA547 used a remote PowerShell script that may have been generated by a large language model (LLM) such as ChatGPT, Gemini, and CoPilot.
TA547 Background
TA547 is considered an initial access broker (IAB) that targets various geographic regions. Since 2023, TA547 has typically delivered NetSupport RAT but has occasionally delivered other payloads, including StealC and Lumma Stealer, which have similar functionality to Rhadamanthys. In 2023, they favored zipped JavaScript attachments as initial delivery payloads. In addition to campaigns in Germany, other recent geographic targeting includes the United States, Spain, Switzerland, and Austria.
Threat Analysis
The phishing emails targeted dozens of German organizations across various industries and impersonated the German retail company Metro, purporting to relate to invoices.
The emails were sent from the address Metro!<rechnung.metro.de@metro-delivery[.]com>, with the subject line Rechnung No:31518562 with a ZIP file attached named in3 0gc-(94762)_6563.zip. This ZIP file was password-protected and contained an LNK file. When the recipient clicks on the LNK file, a PowerShell command is triggered to run a remote PowerShell script. This PowerShell script decoded a Base64-encoded Rhadamanthys executable file stored in a variable, loaded it into memory, and then executed it.
Notably, when deobfuscated, the remote PowerShell script contained interesting characteristics not commonly observed in code used by threat actors (or legitimate programmers). Specifically, the script included a pound sign (#) followed by grammatically correct and hyper-specific comments. These artifacts are typical outputs of large language model (LLM)- generated coding content and suggest the code was generated with some type of LLM-enabled tool. Alternatively, a TA547 actor(s) may have obtained the script from another source.
Risk & Impact Assessment
The primary adverse outcome of this phishing campaign is the unauthorized exfiltration of sensitive information due to the deployment of the Rhadamanthys stealer. The malware is designed to harvest a wide array of data, including credentials, financial information, and other proprietary data. The breach of such information directly threatens organizational data’s confidentiality and potential integrity and may lead to significant business and operational disruptions. Secondary impacts could involve the misuse of stolen credentials to facilitate further attacks, including financial fraud or deeper network penetration, which can escalate to more severe compromises.
The probability that organizations, particularly within Germany, will be targeted by TA547’s phishing campaign deploying Rhadamanthys infostealer is assessed as likely. This estimation is based on TA547’s historical pattern of targeting diverse geographic regions with phishing campaigns. The use of a convincing impersonation of the German retail giant Metro to disseminate malicious payloads further underscores the targeted and deliberate nature of these campaigns. This tailored approach, coupled with the reported volume of attacks, suggests that any organization fitting the target profile of TA547 should consider itself at potential risk.
The impact on affected organizations is expected to be moderate to severe. If the phishing attack successfully results in the deployment of Rhadamanthys malware, the organization could face immediate compromise of credentials. The operational impact includes the potential for significant downtime, loss of customer trust, and the disruption of business processes. Financially, the consequences could be considerable, encompassing not only the costs associated with incident response and remediation but also potential regulatory fines and loss of revenue due to damaged reputation. Strategically, the theft of credentials and sensitive data could result in long-term harm to competitive positioning and trustworthiness in the marketplace. Given these factors, it is imperative for organizations to recognize the heightened risk posed by this campaign and to implement robust defensive strategies to mitigate potential impacts effectively.
Source Material: Proofpoint, Security Brief: TA547 Targets German Organizations with Rhadamanthys Stealer
Cybercriminals Compromise eCommerce Sites to Deploy Credit Card Skimmer in Fake Facebook Pixel Tracker Script
Threat Analysis
A cybercriminal embedded a credit card skimmer in a concealed malicious Meta (Facebook) Pixel tracker script. Meta Pixel tracking scripts use the same concept as Google Tags, but instead of adding functionality, they measure, optimize, and build audiences for ad campaigns.
The fake script converts all references to connect.facebook.net with the domain b-connected[.]com. The b-connected domain was highly likely compromised as it is a legitimate cosmetic eCommerce website and was first registered on 3 April 2002. The b-connected domain loads an additional malicious script designed to monitor the loading of a checkout page and then collect and exfiltrate any credit card details inputted.
This fetched malicious script replaces the legitimate checkout page by creating an overlay iframe with a fake checkout form. The data entered into the fake form is then sent to the cybercriminals on another highly likely compromised site: donjuguetes[.]es/health_check.php.
Risk & Impact Assessment
The likelihood that eCommerce organizations have been or will be targeted by this campaign is currently unknown. Therefore, out of an abundance of caution, organizations with an online retail presence should implement the actions and recommendations detailed below. Moreover, organizations with poorly secured web infrastructure or those lacking robust monitoring of web-facing assets are particularly at risk. The threat is compounded by seemingly innocuous tools (like tracking pixels), which can be easily overlooked by security measures not specifically tuned to detect such misuse. This attack’s unwanted or adverse outcomes are significant, ranging from financial losses due to loss of sales to severe breaches of customer trust and data privacy. The manipulation of legitimate eCommerce processes through malicious scripts allows cybercriminals to steal credit card data, leaving the business’s customers vulnerable to financial theft and identity fraud.
The impact of this credit card skimmer campaign on an organization extends beyond immediate financial loss. The operational disruption can be profound if threat actors successfully implant skimming code on an eCommerce platform. Affected organizations may face forensic investigations to remove the skimmer, system downtimes, and mandatory notification procedures under data protection regulations, which could lead to hefty fines. The reputational damage from such an incident could lead to a long-term decrease in customer confidence and potential loss of business. Strategically, the exposure to such attacks can also erode competitive advantage and heighten susceptibility to further cyber incidents. Ensuring that web assets are regularly updated and monitored is crucial for mitigating these risks and safeguarding the organization’s assets and reputation.
Source Material: Sucuri, Credit Card Skimmer Hidden in Fake Facebook Pixel Tracker
CVE-2024-3400 Exploitation Activity Disclosed
Vulnerability Exploitation – Threat Actor – Backdoor – Reverse Shell – Lateral Movement – Palo Alto Networks PAN-OS CVE-2024-3400 – UTA0218 – UPSTYLE – Hacking Tool – GOST – SOCKS5 Tunnel – RTCP Tunnel – All Industries
As detailed in our Customer Advisory, a threat actor exploited a critical vulnerability (CVE-2024-3400) in Palo Alto Networks PAN-OS software. Following the release of our advisory, Volexity and Palo Alto’s Unit 42 reported details of a threat actor, identified as UTA0218, exploiting this vulnerability in a small number of organizations. The exploitation activity dates back to late March 2024. The early exploitation activity appeared to be the threat actor testing the exploit code and validating exploitability. Unit 42 is tracking the campaign as Operation MidnightEclipse.
The threat actor remotely exploited the firewall device, created a reverse shell, and downloaded further tools onto the device. The actor’s objective focused on exporting device configuration data and leveraging compromised devices to move laterally within victim organizations. Volexity also observed that the threat actor attempted to install a custom Python backdoor, UPSTYLE, on the firewall. The UPSTYLE backdoor allows the threat actor to execute additional commands on the device via specially crafted network requests.
After successfully exploiting devices, the threat actor downloaded additional tooling from remote servers they controlled to facilitate persistent access to victims’ internal networks. Then, they laterally moved through victims’ networks, extracting sensitive credentials and other files that would enable access during and potentially after the intrusion. The tradecraft and speed employed by the actor suggest a competent threat actor with a clear playbook of what to access to achieve their intentions and objectives. While the scale of exploitation is unknown, exploitation, followed by hands-on-keyboard activity, was likely limited and targeted. However, evidence of more widespread exploitation involving reconnaissance activity aimed at identifying vulnerable systems does appear to have occurred.
Threat Analysis
Exploitation Activity
In two observed exploitation incidents, the threat actor attempted to download and execute the backdoor UPSTYLE. In one variation, the filename was update.py. The purpose of the update.py script is to deploy a malicious file to the following path: /usr/lib/python3.6/site-packages/system.pth.
The threat actor requests a non-existent web page to execute the commands. The backdoor then parses the web server error log (/var/log/pan/sslvpn_ngx_error.log), looking for a specific pattern and parsing and decoding data added to the non-existent URI, executing the command contained within. The command output is then appended to a CSS file (bootstrap.min.css), a legitimate firewall file.
After the command’s execution is complete and the output has been written, the log entry that was initially read and contained the command is removed from the error log. Additionally, fifteen seconds after execution, the original version of bootstrap.min.css is restored to its previous state. The access and modified timestamps are also restored for both files.
Using the UPSTYLE backdoor, the threat actor ran a handful of commands on the firewall. The commands include copying configuration files to the web application folder and exfiltrating them via HTTP requests to those files.
Persistence
After exploitation, the threat actor established persistence by continuously fetching and executing the contents of a file named patch. When executed, this file downloads and executes a remotely hosted file named policy. By modifying the policy file, the threat actor could perform various commands on the compromised device.
When executed, the file patch checks for the existence of a cron file named update. If this cron file does not exist, it creates one and uses it to establish a cron job. As previously mentioned, it downloads a remotely hosted file named policy and executes it via bash every 60 seconds. The actor then manually updates the contents of the policy file to perform specific actions.
The threat actor modified the policy file five times, each representing different actions taken on the compromised device. The following numbered versions detail these actions and the order in which the threat actor modified the policy file.
The policy file (Version 1) started with a one-line Python script establishing a reverse shell. The threat actor modified the file (Version 2) to remove previously created CSS files containing various actor command outputs. Then, the configuration data from the firewall device was copied into a new file, storing the device’s hostname in the CSS file. These files were saved to an externally accessible web directory, where the threat actor could subsequently retrieve them.
The third modification (Version 3) removed the CSS files the Version 2 file created. The fourth modification (Version 4) downloads a Golang tunneling tool named GOST and executes it with two different command-line options to establish SOCKS5 and RTCP tunnels. However, this attempt appeared to have failed. Due to this apparent failure, the threat actor modified Version 4, creating version 5. This modification was able to successfully download GOST in a base64-encoded format. The final modification (Version 6) contained commands to download and execute an open-source reverse shell that operates over SSH. The threat actor configured this shell to run on port 31289.
Lateral Movement & Data Theft
The threat actor leveraged a highly privileged service account used by the Palo Alto Networks firewall device to laterally move within the environment via SMB and WinRM. The data targeted included the Active Directory database, key data, and Windows event logs. In addition to Windows-related data, the actor also exfiltrated Login Data, Cookies, and Local State data for Chrome and Microsoft Edge from specific targets. With this data, the actor was able to grab the browser master key and decrypt sensitive data, such as stored credentials.
The following is a list of files exfiltrated by the actor:
- %LOCALAPPDATA%\Google\Chrome\User Data\Default\Login Data
- %LOCALAPPDATA%\Google\Chrome\User Data\Default\Network
- %LOCALAPPDATA%\Google\Chrome\User Data\Default\Network\Cookies
- %LOCALAPPDATA%\Google\Chrome\User Data\Local State
- %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Login Data
- %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Network
- %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Network\Cookies
- %LOCALAPPDATA%\Microsoft\Edge\User Data\Local State
- %APPDATA%\Roaming\Microsoft\Protect\<SID> -> DPAPI Keys
- %SystemRoot%\NTDS\ntds.dit
- %SystemRoot%\System32\winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Except for the previously mentioned malicious files, the threat actor was not observed deploying any additional malware or employing additional persistence methods. The stolen data allowed the threat actor to compromise credentials for all domain accounts. Further, the actor accessed specific user workstations, potentially leveraging valid credentials or cookies from browser data.
Infrastructure
The threat actor leveraged a mix of infrastructure during their operations. The C2 infrastructure hosted the malicious files and was used for communication channels. The threat actor appears to have used a mix of VPNs and potentially compromised ASUS routers. The threat actor used this infrastructure to access files created by the actor. Additionally, the threat actor abused a compromised AWS bucket and various Virtual Private Servers (VPS) providers to store malicious files. Currently, the infrastructure does not overlap with other threat actors in Volexity’s telemetry.
Risk & Impact Assessment
Given the targeted exploitation of CVE-2024-3400 by the threat actor, the likelihood of organizations being targeted hinges significantly on their visibility and the strategic value of their data to the actor. Organizations with high-value data in manufacturing, research institutions, and government sectors are likely more susceptible to these attacks. The precision of the threat actor in choosing their targets and the technical expertise required to exploit this vulnerability suggests a methodical approach, enhancing the likelihood of successful breaches against specifically selected organizations.
The unwanted outcomes of such exploitation include unauthorized and persistent access to compromised organizations, the exfiltration of sensitive information, and the potential exfiltration of proprietary information. The introduction of the UPSTYLE backdoor facilitates a range of post-exploitation activities, such as lateral movement and further data theft, elevating the direct impact on operational security and data integrity.
The impact of such exploitation on an organization could potentially be severe. Initial access through this exploit allows threat actors to establish footholds from which they can conduct extensive reconnaissance, manipulate data flows, and exfiltrate critical information. The operational disruptions could include degraded system performance, unauthorized configuration changes, or complete system takeovers. From a financial perspective, organizations could face significant expenses related to forensic investigations, system remediations, legal fees, and potential fines for compliance failures.
Additionally, the reputational damage incurred from such breaches can lead to loss of customer trust, diminished shareholder value, and long-term brand erosion. The strategic implications are equally grave, with potential exposure to continuous security threats and compromised competitive positions in the market. Prioritizing robust cybersecurity practices is crucial to mitigate these risks and shield organizational assets from sophisticated threat actors.
Source Material: Volexity & Palo Alto Unit 42
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Information – Construction
In the past week, 74 organizations were listed on various data leak sites, with the majority operating in the Manufacturing sector.
Analysis
First, we focus on the most active leak sites identified during the specified period. Based on the number of organizations listed, Black Basta, Play, and Dragon Force have emerged as the top three leak sites. These platforms have become critical components of the ransomware ecosystem, utilized by threat actors to publicize breaches and exert pressure on victim organizations to meet ransom demands.
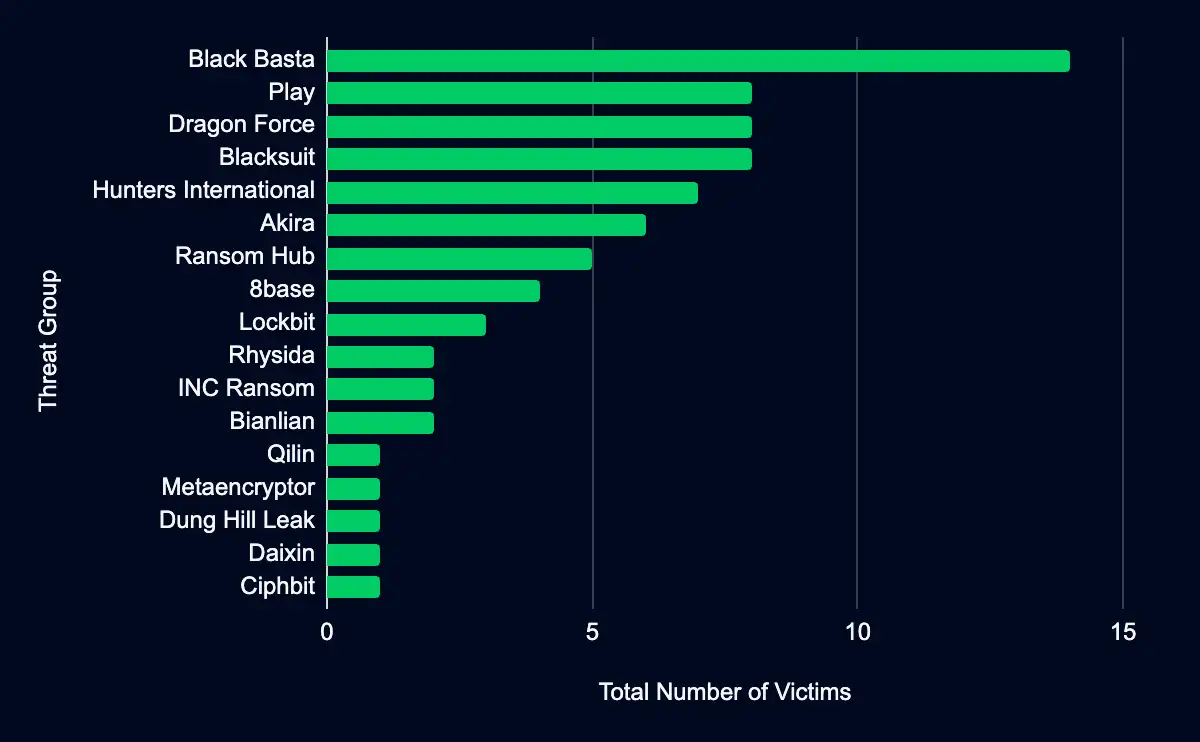
Correlating the organizations listed on data leak sites to their respective industry reveals that specific sectors are more frequently listed than others, indicating a pattern in operators’ targeting strategies. The Manufacturing industry emerges as the most targeted sector, accounting for 27% of the total listings across the examined leak sites. This is closely followed by the Professional, Scientific, and Technical Services and Health Care and Social Assistance sectors, which represent 12% and 11% of the listings, respectively.
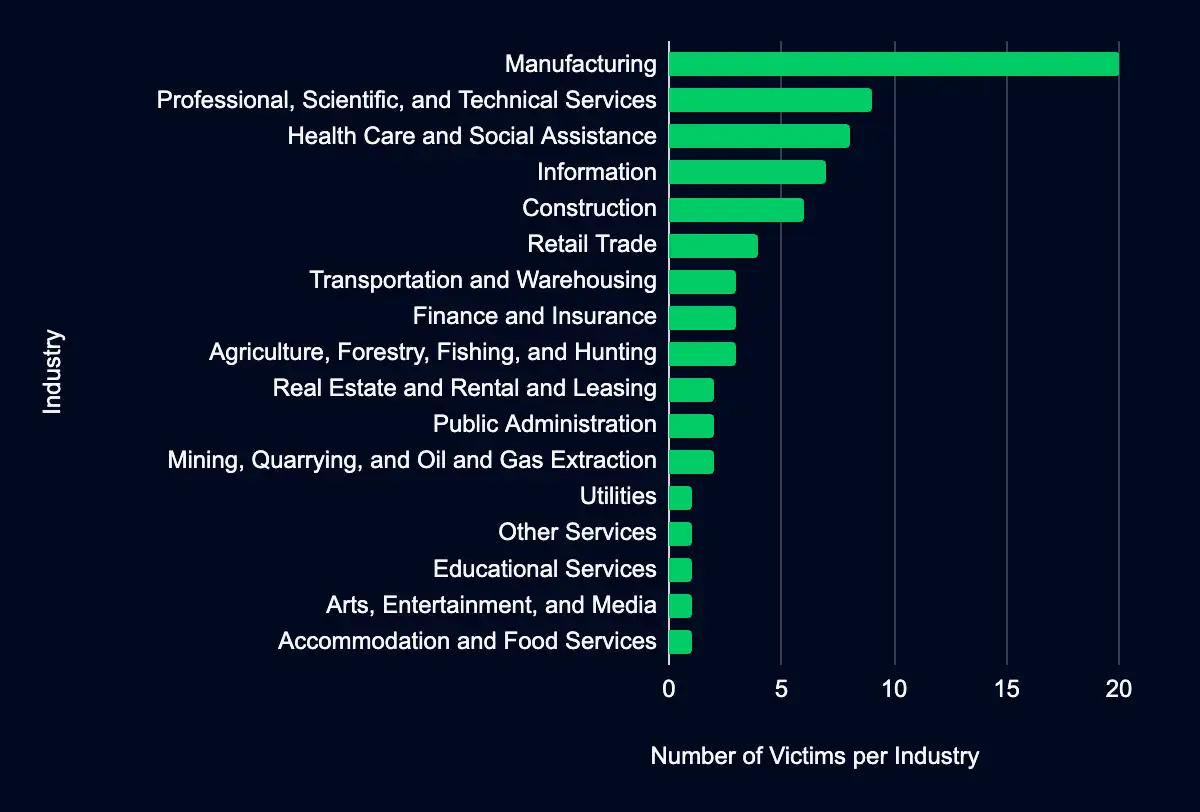
Organizations within these highlighted industries are advised to undertake comprehensive risk assessments and strengthen their cybersecurity frameworks to address potential vulnerabilities. By understanding their prominence on leak sites, leaders can better prioritize security initiatives and investments to mitigate the risks associated with such targeted cyber threats. This proactive stance is essential in defending against the operational disruptions and financial losses that breaches can entail.
CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
This week CISA added three (3) new CVEs to the Known Exploited Vulnerabilities catalog this past week. Vulnerabilities this week affect Palo Alto and D-Link products, and it’s unknown if they are linked to any ransomware attacks.
Analysis
Within the past week, CISA has updated its Known Exploited Vulnerabilities catalog to include critical vulnerabilities affecting Palo Alto Networks PAN-OS and multiple D-Link NAS devices. These vulnerabilities present significant risks due to their potential for command execution and unauthorized data access.
As detailed in our Customer Advisory and the report, “CVE-2024-3400 Exploitation Activity Disclosed,” in this Cyber Intel Brief, Palo Alto Networks PAN-OS CVE-2024-3400 presents a severe security threat with its command injection vulnerability in the GlobalProtect feature. This flaw allows an unauthenticated threat actor to execute commands directly on the firewall with root privileges. This vulnerability’s severity is exacerbated by its presence in a security product designed to protect network boundaries, thereby amplifying the potential impact of its exploitation. The urgency of addressing this issue is reflected in the mitigation due date set for April 19, 2024. Currently, there is no known use of this vulnerability in ransomware campaigns, which leaves a significant intelligence gap regarding the exploit’s potential applications by cybercriminals.
D-Link NAS Devices CVE-2024-3272 and CVE-2024-3273 involve two interconnected vulnerabilities that enable threat actors to perform authenticated command injection and remote unauthorized code execution. CVE-2024-3272 exploits hard-coded credentials, allowing threat actors access without authentication. CVE-2024-3273 allows for command injection through the web management interface. Both vulnerabilities affect legacy D-Link products that no longer receive firmware updates or support, highlighting a critical risk area for entities still operating these devices. The mitigation due date for these vulnerabilities is 2 May 2024. Observations by the threat intelligence firm GreyNoise noted attempts to weaponize these vulnerabilities, particularly for spreading the Mirai botnet malware, suggesting that these vulnerabilities are actively being exploited in the wild.
The combination of these D-Link vulnerabilities in widely used network equipment underscores the persistent challenge of securing legacy and end-of-life devices, which are often neglected in regular security updates and management practices. The discovery and active exploitation of these vulnerabilities highlight the ongoing need for vigilance and proactive management in cybersecurity practices. Entities must prioritize decommissioning and replacing vulnerable devices to mitigate the risks posed by these vulnerabilities.
In conclusion, adding these CVEs to CISA’s catalog highlights the risks associated with Palo Alto Networks and D-Link devices. It underscores the broader cybersecurity challenges of managing legacy systems and responding swiftly to emerging threats. Organizations are reminded of the importance of maintaining a robust security posture that includes regular updates, strong authentication practices, and timely mitigation of identified vulnerabilities to protect against potential exploits and uphold network integrity.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share