Multi-stage Social Engineering, Multi Programming Languages used in Single Attacks, and Zero Days in Cloud
This week: social engineering phone calls lend authenticity to malicious emails; finance-themed spam campaigns are spreading malware through batch scripts including PowerShell, Go, shellcode to .NET; and a SugarCRM zero-day authentication bypass and remote code execution vulnerability is granting access to AWS accounts. In our latest Cyber Intelligence Brief, we look at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading MDR provider, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Trellix: Exploring New Techniques of Fake Browser Updates Leading to NetSupport RAT
- CISA Cyber Safety Review Board: Review of the Attacks Associated with Lapsus$ and Related Threat Groups
- Palo Alto Unit 42: When a Zero Day and Access Keys Collide in the Cloud: Responding to the SugarCRM Zero-Day Vulnerability
- Cyble: LummaC Stealer Leveraging Amadey Bot to Deploy SectopRAT
- Sophos: Attacker combines phone, email lures into believable, complex attack chain
- HP Wolf Security: Do You Speak Multiple Languages? Malware Does.
- Latest Additions to Ransomware Data Leak Sites
- CISA Adds CVE-2023-24489 to its Known Exploited Vulnerabilities Catalog
Threat Actors Use New Infiltration Technique to Deliver NetSupport RAT
Fake Chrome Updates – NetSupport Manager RAT – Compromised Websites – Multi-Stage Infection – Javascript and BAT Files
In an ongoing campaign detected by Trellix’s Advanced Research Center, threat actors use fake Chrome browser updates to lure users into installing the NetSupport Manager, a remote administration tool. This malicious tool allows them to steal data and gain full control over the victim’s computer. Drawing similarities with a prior campaign that used the SocGholish malware, this campaign employs a series of staged downloads and scripts to achieve its nefarious goals. While there’s no direct evidence connecting the two campaigns, it’s evident that the modus operandi of using browser updates as bait persists, albeit with variations in the tools and scripts used for execution.
Cybercriminals have long used fake browser updates to deceive users into downloading malicious payloads. One notable campaign that employed this tactic is SocGholish, which, like the present campaign, also led to installing the NetSupport Manager RAT. However, while the current campaign under scrutiny by Trellix uses batch files, VB scripts, and the Curl tool, SocGholish predominantly used PowerShell with WMI functionalities. The evolution of the tools and scripts used highlights the adaptability and persistence of cyber criminals in refining their techniques and tools to evade detection and improve their success rates.
Based on the patterns observed, the most likely scenario is that threat actors will continue to exploit the fake browser update theme as a lure, given its historical success rate. Given the adaptability and technical proficiency displayed by the actors, we can expect more websites, including those of high-profile or sensitive nature, to be targeted and compromised in the upcoming months. There will be incremental improvements in their tactics, techniques, and procedures (TTPs) to evade detection and increase the success rate.
As organizations implement countermeasures to defend against this threat, an alternative scenario could be threat actors implementing new infrastructure and additional techniques to obfuscate it. Another alternative scenario based on the compromise of the Chamber of Commerce website suggests that the actor may be targeting specific sectors. This might be an early indication of a shift where threat actors are moving from targeting the general public to focusing on particular industries or sectors which can offer them more valuable data or higher financial returns.
Wild card scenarios include the threat actors venturing into other mediums, like mobile apps or social media platforms, to lure victims instead of relying solely on compromised websites. The threat actors might cease operations for a while, hoping that over time the knowledge of this campaign will have faded and any observables have aged out. Although there is no direct evidence linking state-sponsored groups to these attacks, it’s plausible that, in the future, similar tactics could be adopted by nation-state actors for cyber espionage purposes.
Analysis of LAPSUS$ and Affiliated Threat Groups: TTPs and Mitigation Strategies
Karakurt – Yanluowang – Spear Phishing – Vishing (voice phishing) – Smishing (SMS phishing)
As part of our initiative to provide threat intelligence reports on the latest developments in threat actor tactics, techniques, and procedures (TTPs), the Adversary Tactics and Intelligence team compiled this report, analyzing the recent report by CISAs Cyber Safety Review Board which describes the tactics, techniques, and procedures (TTPs) and offers recommendations.
The CISA report finds that threat actors, including the Lapsus$, Yanluowang, and Karakurt, conduct extensive research to familiarize themselves with their targets before launching operations. Standard methods include port scanning and traditional research methods. They exploit trust relationships between third-party service providers, bypass multi-factor authentication systems using varied techniques, and, once inside, escalate privileges through multiple means ranging from simple password theft to advanced tool usage.
The infrastructures of their operations include dedicated cloud systems and anonymization services. The primary motivation appears to be financial, seeking extortion, ransomware, and cryptocurrency theft, but ideological motives are evident. The report highly recommends transitioning away from SMS and Voice MFA, mandating phishing-resistant MFA like FIDO2-backed tokens, ongoing employee education about current threats, and regularly updating and testing Cyber Incident Response Plans.
The threat actors (TAs) leveraged various TTPs, often mixing less complex methods and tools with advanced technical knowledge. Before targeting an organization, TAs employ diverse research methods, such as social engineering, to increase their understanding of a target’s business operations.
TAs used standard penetration testing methods for network reconnaissance, such as port scanning. Several TAs used fraudulent Emergency Disclosure Requests (EDRs) to obtain sensitive information about targets used to facilitate extortion attempts against targeted individuals. An EDR allows certain entities, usually governmental agencies or law enforcement, to request access to user data from organizations in emergency situations, typically involving imminent threats to human safety or severe criminal activities.
Evidence also suggests the TAs sought login credentials on underground criminal forums and, in the case of Lapsus$, in its public Telegram channel. Many TAs extensively exploited the trust relationships between third-party service providers and their clients or customers to target downstream entities.
Social engineering was used extensively and creatively by most of the TAs to gain initial access to their targets. They used spear phishing to lure target employees to visit spoofed or hacked websites. Voice phishing (vishing) was also observed to impersonate a trusted entity over voice.
TAs also employed SMS phishing (smishing) to deliver instructions or website links via SMS to a victim’s phone. Some actors used monetary incentives to recruit employees and contractors of targeted organizations, who then acted on behalf of the threat actors. TAs sometimes leveraged initial access brokers (IABs) to gain access to targeted networks, including paying with cryptocurrency that had been stolen or extorted from other targets. A limited set of TAs exploited known software and configuration vulnerabilities to gain initial access. All the observed vulnerabilities during this study were well known, with patched software available.
When a targeted organization used multi-factor authentication, the actors would spam employees with MFA prompts (MFA fatigue) to overwhelm them with access approval requests until they approve it. In some cases, impersonated help desk personnel over direct chat messages and encouraged employees to approve the MFA prompts. Sometimes, they exploited SMS and voice MFA through fraudulent Subscriber Identity Module (SIM) swaps.
Once they gained initial access, various techniques were observed to elevate privileges and move laterally within the environment, including exploiting the tendency for enterprises and their employees to document internal procedures, share information on collaboration platforms, and use ticketing systems to perform internal help desk operations. In specific cases, the actors were able to locate: Administrative passwords in a spreadsheet; Amazon Web Services (AWS) access keys stored in Slack; privileged credentials embedded in a PowerShell script stored on a misconfigured network share; credentials from password databases, browser password caches, and keychains.
In other cases, credential dumping tools, such as MiniDump and Impacket, and offensive security tools, like Cobalt Strike, PowerSploit, Metasploit, and LinPEAS, were used. In others, abuse of Window’s “ntdsutil.exe” utility was observed to dump NT Directory Services (NTDS) and administrative tools like RustScan and AdFind. Some actors also leveraged internal communication channels, such as internal Slack, to impersonate employees and conduct internal social engineering attacks. Sometimes employees were convinced to download remote monitoring and management (RMM) tools. Used compromised AWS tokens to request and assume permissions of an instance role and created temporary credentials for non-existent users with open-source cloud management tools like AWS_consoler.
Some TAs established persistence in the targeted environment for ongoing access, but this was inconsistent across all groups. Techniques observed included adding an administrator account using the built-in Windows “net.exe” and then adding it to the local Administrators group. Sometimes, they registered actor-controlled devices for MFA and possibly modified settings to disable or register their own MFA. They used stolen employee credentials to log into virtual desktop infrastructure (VDI) environments and RMMs. They deployed reverse SSH tunnels to establish communication with an actor-controlled C2 server. Leveraged reverse proxy tools, including rsocx132 and ngrok, or installed RATs and RMM tools like RealVNC, Remote Desktop Protocol (RDP), ManageEngine, AnyDesk, LogMeIn, TeamViewer, and ThinScale. Other times, they implanted simple backdoors via commands sent in JSON that communicated via HTTP.
Several TAs intentionally bypassed or disabled enterprise security solutions, including using the bring your own vulnerable driver (BYOVD) technique to deploy malicious kernel drivers signed by stolen code-signing certificates (obtained from another targeted entity) to bypass security detection and disable security controls. Other times they modified the host firewall or used the Unified Extensible Firmware Interface (UEFI) bootkit BlackLotus.
The infrastructure observed included a dedicated cloud infrastructure from known virtual service providers (VSPs) or attempted to use anonymization services like Tor to connect to targeted networks but then, in some instances, established new virtual private network (VPN) sessions through residential IP addresses to appear less suspicious, selecting servers in similar geographic locations to their targets to avoid “impossible travel” detections. In some cases, the threat actors reused infrastructure across multiple targeted organizations, including Internet Protocol (IP) addresses and server-side components like web shells.
To mitigate the threat, organizations should implement the following guidance:
- Organizations should immediately transition away from Short Message Service (SMS) and Voice MFA.
- Organizations should require an explicit authentication event using a form of phishing-resistant MFA, such as FIDO2-backed tokens, for each sensitive transaction executed on their systems.
- Organizations should educate employees on a frequent and regular basis, in a relatable and easily digestible manner, on the latest threat landscape trends and how to prevent them.
- Develop and test (ideally quarterly) a Cyber Incident Response Plan specific to extortion, ransomware, and harassment-related events.
Exploitation of the SugarCRM Vulnerability and Implications for AWS Environments
CVE-2023-22952 – Pacu AWS Exploitation Framework – Compromised AWS Access Keys – Scout Suite Cloud Security Auditing Tool
A blog post from Palo Alto’s Unit 42 delves into an authentication bypass and remote code execution vulnerability in the SugarCRM tracked as CVE-2023-22952. While it might appear as a standard vulnerability, its implications are far-reaching, especially when the web application isn’t properly secured. Over the past year, threat actors have exploited this vulnerability as an initial access vector to compromise AWS accounts because of misconfigurations the actors capitalized on post-initial compromise. The article provides a comprehensive breakdown of the techniques and concludes with preventive measures organizations can adopt.
SugarCRM, a customer relationship management platform, is widely used across various industries for its extensive features. The CVE-2023-22952 vulnerability was published on 11 January 2023, with a CVSS score of 8.8 (high). Due to a lack of input validation, this vulnerability allows actors to inject custom PHP code into the email templates module of SugarCRM before 12.0. Hotfix 91155. The data stored in SugarCRM databases could be highly sensitive. If this data is compromised, it can be sold or used for extortion. The vulnerability’s exploitation grants threat actors direct access to the servers running the application, which in the observed cases, were Amazon EC2 instances with long-term AWS access keys, enabling the actors to broaden their reach.
The threat actors initiated their intrusion by exploiting the SugarCRM vulnerability CVE-2023-22952, allowing the threat actors to access the application’s underlying servers. In the cases observed by Palo Alto’s Unit 42, these servers were Amazon EC2 instances with long-term AWS access keys, which the actors used to broaden their access.
Once inside, they accessed Amazon EC2 instances and compromised long-term AWS access keys stored on these hosts. In some cases, they then utilized Pacu, an AWS exploitation framework, and Scout Suite, a cloud security auditing tool, for discovery. In others, they made API calls to services like AWS Organizations and Cost and Usage service to gather more information about the account structure and usage. The threat actors transitioned from the compromised SugarCRM EC2 instances to the Relational Database Service (RDS), creating new RDS snapshots from the SugarCRM RDS databases and modifying security group rules.
They also attempted privilege escalation by trying to log in as the Root user, which stood out in the CloudTrail logs, although unsuccessful. To evade defenses, the threat actors deployed resources in non-standard regions and turned the EC2 instances on and off throughout their time in the environments. One reason could be to decrease their visibility as the AWS console defaults to showing only running EC2 instances. Another possibility would be to prevent the organization from receiving cost alerts, alerting the organization to the actor’s activities.
The vulnerability poses a significant risk to organizations that utilize SugarCRM, especially if they have not taken measures to secure their environment correctly. Given that SugarCRM is a widely used customer relationship management platform across various verticals, many organizations could be exposed. The vulnerability has been exploited in the past year to gain access to AWS accounts, and while it’s not a direct flaw in AWS, misconfigurations can amplify the risk.
The impact of successful exploitation of this vulnerability can be severe. Once threat actors gain access through the SugarCRM vulnerability, they can access underlying servers, such as Amazon EC2 instances. Threat actors can expand their access within the AWS environment if these instances store long-term AWS access keys. This can lead to: data compromise, infrastructure manipulation, resource misuse, information gathering, and possible reputational damage.
ZIP File Deploys LummaC Stealer, Amadey, and SectopRAT in Multi-tiered Malware Campaign
Disguised Files – Infostealer – Malicious Zip File – Amadey Bot – SectopRAT
A new blog post from Cyble Research and Intelligence Labs details their discovery of several ZIP files disguised as software setup files that initiate an infection chain deploying the latest variant of LummaC Stealer, which drops the Amadey bot, which drops the Sectop RAT. However, the delivery of these files is unknown; Cyble postulates that it could have been through spam emails or a YouTube campaign.
The LummaC2 Stealer is a highly sophisticated, next-generation malware designed to target and steal data from various browsers based on Chromium and Mozilla. The malware can steal PDF files, documents, session cookies, and data from around 70 browser-based cryptocurrencies and 2FA extensions. In a previous CIB, we discussed the implications, risks, and cyber defense strategies of LummaC Stealer, available here.
Amadey Bot was first discovered around October 2018. It is a botnet sold on Russian-speaking hacking forums for approximately $500. The malware can perform system reconnaissance, steal information, and load additional payloads. It can send information about the compromised system and installed antivirus software to its command and control (C2) server and receive commands from it. This discovery highlights that it is still an active threat.
SectopRAT is a remote access trojan (RAT) designed to allow unauthorized individuals to gain remote access and control over a targeted computer system. SectopRAT is known for its ability to infiltrate systems and steal sensitive information, such as login credentials, financial data, and personal information. It can also perform various malicious activities, including keylogging, screen capturing, file manipulation, and executing arbitrary commands on the infected system.
The infection begins with a malicious ZIP file, disguised as software setup files with names like “IMG_20230515.ZIP”, to appear benign to lure unsuspecting users into opening it. The ZIP file contains an executable disguised as a benign file. When the target unknowingly executes this file, LummaC Stealer is launched.
Once executed, LummaC Stealer initiates its operations by gathering preliminary system details such as the operating system version, hardware information, CPU, RAM, and more. The stealer then collects browsing history, cookies, login details, personal data, credit card information, and other valuable data from various browsers, sending the data to its command and control (C2) server.
To maintain persistence, LummaC Stealer injects its malicious code into “RegAsm.exe,” a legitimate Microsoft .NET Assembly Registration Tool. The malware then proceeds to deploy the Amadey bot. It downloads it from a remote server via the malicious URL, saves it to the Temp directory, and executes it. Additionally, Amadey creates an LNK file that, when clicked, runs the dropped copy of itself. This LNK file is dropped into the startup folder to maintain persistence.
During the execution, Amadey establishes communication with its C2 server, regularly transmitting system details such as installed antivirus software. Additionally, it queries the server to receive commands. The bot also downloads the second malware in the infection chain, SectopRAT, downloaded from a separate malicious URL to the Temp directory.
Once SectopRAT is downloaded and executed, it enumerates the system, extracting sensitive data from various files, such as cookies, login data, and web data. This extracted information isn’t limited to browser data; it also stretches to gaming platforms, other software applications, and, critically, cryptocurrency wallets. Additionally, SectopRAT can employ a concealed secondary desktop, granting the threat actors an additional layer of stealth and control. Through this, they can manipulate browser sessions without alerting the user.
LummaC Stealer, Amadey, and SectopRAT pose a significant threat to organizations. This threat primarily capitalizes on human errors, particularly employees unsuspectingly downloading malicious ZIP files. Companies that have not invested in cybersecurity awareness training are at heightened risk, especially those without up-to-date antivirus measures and advanced threat detection tools. The risk magnifies for entities dealing with cryptocurrency due to the malware’s specialized targeting abilities.
Should organizations fall victim to this threat, they can face immediate and long-lasting consequences. Unauthorized access can compromise sensitive financial, operational, and personal data, leading to substantial financial implications. This compromised data can find its way to the dark web, becoming a tool for identity theft, fraud, and other targeted attacks. The integrity of the victim’s IT infrastructure becomes uncertain, potentially disrupting business processes. Beyond immediate operational impacts, the breach can erode trust among partners and clients, affecting market reputation and possibly leading to regulatory repercussions for entities under strict data protection mandates.
Phone and Email Lead to Modified Notepad++ Deployment and Data Theft
Trojan – Deceptive Phone Calls – Email Lures – Fake Delivery Driver Theme – Data Theft
Sophos X-Ops recently detailed an intricate browser-based data theft cyber intrusion that began with a seemingly harmless phone call. The actor, posing as a delivery driver, initiated a social engineering scheme that led an employee of a Switzerland-based organization to inadvertently compromise their computer.
The threat actor’s strategy involved a phone call followed by a deceptive email that appeared to contain a PDF attachment. However, the “attachment” was merely an image embedded within the email. When the employee clicked on it, they were redirected to a malicious website. The complexity of this operation suggests a well-coordinated effort, leveraging multiple layers of social engineering to deceive the target.
The cyber intrusion detailed by Sophos X-Ops showcased a blend of advanced social engineering and technical activity. An actor, masquerading as a delivery driver, initiated contact with an employee of a Switzerland-based organization. Concurrently, the employee received a deceptive email, purportedly from the caller’s shipping company. This email cleverly contained an image designed to resemble a PDF attachment. However, the image served as a redirection tool, leading the employee to a malicious website through a benign website’s redirection script, likely designed to bypass standard URL-checking features.
Upon investigating the compromised system, Sophos found that the actors had removed the malware post-compromise. This removal posed a challenge for direct malware analysis. However, Sophos identified artifacts and residual files left behind by the actors. Among these artifacts were unusual system logs and traces of unfamiliar processes.
Further analysis of the system’s artifacts revealed a folder for a modified version of the Notepad++ text editor. Hidden within this version was a LICENSE file appended with a blob of base64-encoded data. Decoding this data unveiled multiple PowerShell scripts designed for various malicious activities, including installing untrusted certificates, establishing connections to the Tor network, and data theft, including financial software files, passwords, and browser cookies.
Researching open-source repositories for files related to those found in the Notepad++ folder led to the discovery of an Electron app, a set of JavaScript instructions designed to run inside a stripped-down version of the Chromium browser that contained an almost identical Notepad++ program directory with the same modified, malicious updater and LICENSE file. This discovery suggested that the Electron app’s execution directly resulted in the deployment of this modified Notepad++ version. Sophos analyzed the app and discovered that, upon execution, it displayed a package tracking interface and ran the malicious scripts in the background.
Threat Actors Use Multi-Language Malware Distribution Techniques in Finance-Themed Spam Campaigns
AsyncRAT – Phishing – Shellcode – Powershell – Go
HP Wolf Security has recently observed a surge in finance-themed malicious spam campaigns that employ malware distributed via batch scripts (.bat). These campaigns utilize a diverse set of programming languages, including batch scripts, PowerShell, Go, shellcode, and .NET, to achieve different objectives throughout the infection chain. The malware initiates with simple batch scripts that download a second-stage malware using PowerShell. The malware is double-packed to dodge detection, with one of the packers named ShellGo, written in Go, decrypting and executing shellcode in memory. The shellcode then bypasses two Windows security features and runs the payload, identified as AsyncRAT, a . NET remote access trojan (RAT), directly in memory. This multi-language approach and in-memory execution highlight the threat actors’ focus on evading detection.
The initial infection vector begins with deceptive batch scripts, often disguised as invoices or payment confirmations, sent in phishing emails. These scripts employ double file extensions, such as “.pdf.bat”, to mislead users into believing they are opening legitimate documents. The deception is further enhanced by the default behavior of Windows File Explorer, which hides file extensions, making unsuspecting users more likely to execute the script. The threat actor further crafts the emails to appear as if they originate from legitimate senders by spoofing the sender address, increasing the chances of the recipient opening the attachment.
Upon execution of the batch script, it initiates the download of a ZIP archive. This archive contains an executable that has been inflated to nearly 2GB using binary padding. This technique can bypass specific on-access malware scanners that may struggle with or opt not to scan large files. Once the ZIP archive is downloaded and unpacked, the executable inside is ready for the next stage of the infection process.
The executable undergoes a two-stage unpacking process. The first layer involves the ShellGo crypter, written in Go. ShellGo decrypts and executes shellcode directly in memory. This shellcode is packed and equipped with mechanisms to bypass two critical Windows security features: the Anti-malware Scan Interface (AMSI) and Windows Lockdown Policy (WLDP). After bypassing these security features, the shellcode proceeds to decrypt a PE file, which represents the final payload of the malware.
The final payload, identified as AsyncRAT, is a .NET-based remote access trojan (RAT). Instead of being written to disk, which could trigger detection, the payload is executed directly in memory. This is achieved through a complex sequence of function calls involving mscoreei.dll and clr.dll. By executing the payload in memory, the malware reduces its footprint and increases its chances of evading traditional detection mechanisms.
The primary payload, AsyncRAT, is a well-documented RAT developed in .NET. It offers functionalities such as keylogging and data theft. The malware’s multi-language approach, combined with in-memory execution, highlights its advanced evasion capabilities. The use of ShellGo, a crypter written in Go, further complicates detection and analysis due to Go’s statically linked binaries. The malware’s ability to bypass AMSI and WLDP showcases its capability to disarm critical security features, allowing it to operate undetected.
Given the observed surge in finance-themed malicious spam campaigns, the likelihood of organizations encountering this threat is significant. The campaigns employ a multi-layered, multi-language approach, making them more versatile and harder to detect. Deceptive batch scripts disguised as common business documents, such as invoices or payment confirmations, increase the chances of unsuspecting employees executing them. Additionally, the threat actor’s tactic of spoofing email sender addresses to mimic legitimate senders further amplifies the risk. The malware’s ability to bypass specific on-access malware scanners by using binary padding and its evasion of critical Windows security features, such as AMSI and WLDP, means that even organizations with standard security measures in place might be vulnerable.
The impact of this threat on organizations can be severe. Once the malware is successfully executed, it deploys AsyncRAT, a remote access trojan with capabilities like keylogging and data theft. This means sensitive organizational data, including financial information, intellectual property, and employee details, could be at risk. The malware’s in-memory execution technique reduces its footprint, making it harder to detect and increasing the duration of potential unauthorized access. Furthermore, the fact that the IP address used for the command and control (C2) server matches the one used to send the malicious emails suggests that the threat actor might have direct control over both the distribution and the data exfiltration mechanisms. This could lead to rapid data breaches, potential financial losses, and reputational damage. Additionally, compromising internal systems could disrupt business operations and result in costly remediation efforts.
Latest Additions to Data Leak Sites
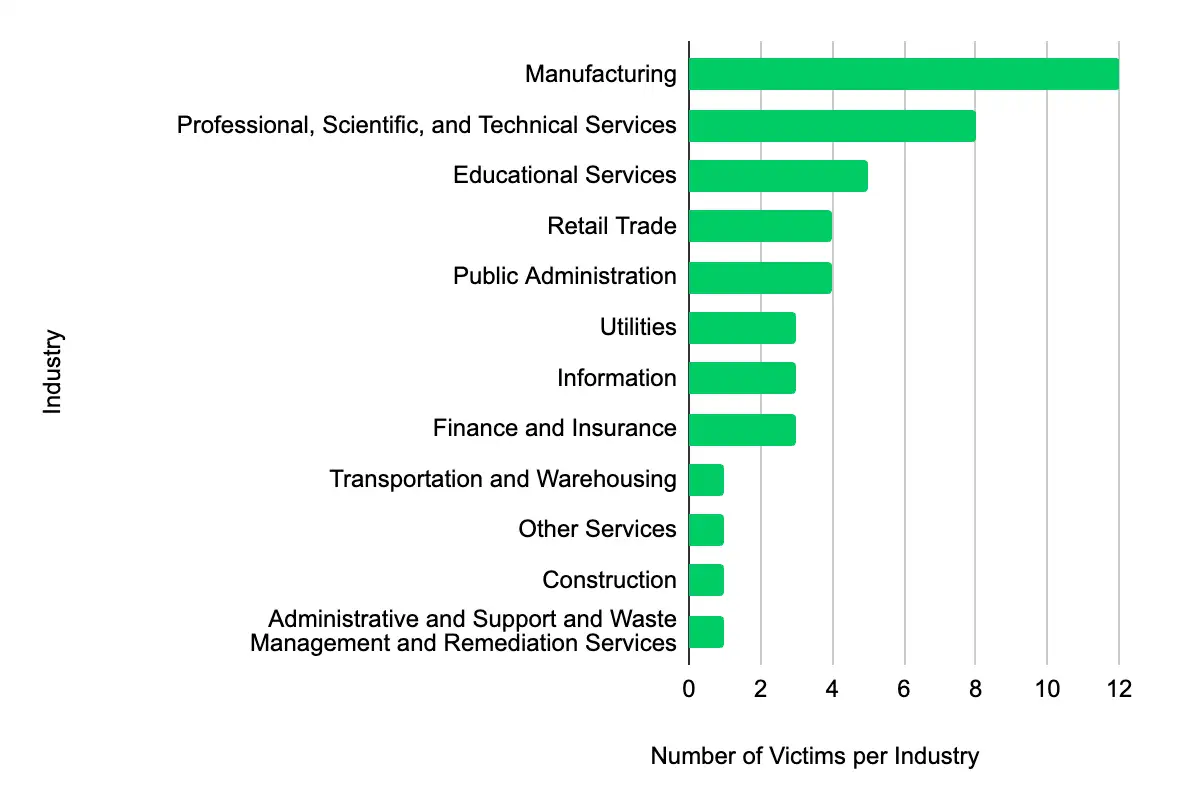
Manufacturing – Professional, Scientific, and Technical Services – Educational Services – Retail Trade – Public Administration
In the past week, monitored data extortion and ransomware threat groups added 46 victims to their leak sites. Of those listed, 17 are based in the US. The most popular industry listed was Manufacturing, with 12 victims. They were followed by eight in Professional, Scientific, and Technical Services, five in Educational Services, and four each in Retail Trade and Public Administration. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds CVE-2023-24489 to its Known Exploited Vulnerabilities Catalog
Citrix/CVE-2023-24489
Within the past week, CISA added CVE-2023-24489 to its Known Exploited Vulnerabilities Catalog. This vulnerability affects Citrix Content Collaboration. The vulnerability could allow an unauthenticated actor to remotely compromise customer-managed ShareFile storage zones controllers. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with a CISA due date set for 6 September 2023.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-24489 | Citrix | Content Collaboration | Citrix Content Collaboration contains an improper access control vulnerability that could allow an unauthenticated attacker to remotely compromise customer-managed ShareFile storage zones controllers. | 9/06/23 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share