Malware Misusing Legitimate Internet Services, No Rest for the Wicked HiatusRAT, and Adversaries Use Spacecolon Tool Set to Deploy Ransomware
This week: malware is strategically misusing legitimate internet services, a RAT on “hiatus” shifts its targeting and infrastructure, and threat actors are using open redirects in phishing campaigns. In our latest Cyber Intelligence Brief, we look at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Recorded Future Insikt Group: Threat Actors Leverage Internet Services to Enhance Data Theft and Weaken Security Defenses
- Lumen: No Rest For The Wicked: HiatusRAT Takes Little Time Off In A Return To Action
- Kroll: Increased Use of Open Redirects in Phishing Campaigns
- ESET: Scarabs Colon-izing Vulnerable Servers
- The Latest Additions from Data Leak Sites
- CISA Adds 3 CVEs to its Known Exploited Vulnerabilities Catalog
Malware and the Strategic Misuse of Legitimate Internet Services
A new report by Recorded Future’s Insikt Group examined the tactics employed by threat actors in misusing legitimate internet services, like cloud storage, instant messaging, and email services. These malicious activities are aimed at enhancing data theft and subverting security measures. The document provides insights into the specific services being exploited, the methods of misuse, and the underlying motivations of the threat actors involved.
The misuse of legitimate internet services by threat actors is not new. Historically, adversaries have always sought ways to blend in with regular traffic, making detection and mitigation more challenging. Leveraging legitimate internet services allows them to maintain a low profile while carrying out their malicious activities. This tactic provides them with a cover and exploits the trust that users and organizations place in these well-known services. Over the years, as internet services have evolved and expanded, so have the techniques and strategies employed by threat actors to exploit them.
Insikt Group’s research systematically analyzes over 400 malware families detected by Recorded Future platforms, supplemented with additional malware families tracked using other sources to determine which Legitimate Internet Services (LIS) are leveraged for malicious purposes and in what ways. The report categorizes how actors can abuse LIS into four main categories: Full C2, Dead Drop Resolving (DDR), Payload Delivery, and Exfiltration. Each category offers unique advantages to the threat actors, from simplifying the C2 server installation process to reducing infrastructure costs and improving operational security.
For Full C2, threat actors utilize LIS as an intermediary proxy or “abstraction layer,” enabling the actor and the malware to communicate indirectly. This method leverages any service with a publicly accessible API for reading and writing data, effectively acting as a bridge between the malware and its controller. For DDR, malware retrieves its actual C2 server information from a web service. Drawing inspiration from traditional intelligence methods, this approach uses platforms where malware can store and retrieve data. For Payload Delivery, threat actors misuse LIS to distribute malicious payloads. Services that allow data reading, such as cloud storage or messaging platforms, are prime targets for this purpose. Lastly, for Exfiltration, threat actors use LIS to store exfiltrated data. Any service that permits data writing or sending can be harnessed for this purpose, ensuring a discreet and efficient transfer of sensitive information.
Analysis of the malware families reveals that 25% abused LIS as part of their infrastructure. Infostealers, representing 37% of this group, misused these services the most, primarily due to their objective to exfiltrate data and the ease of infrastructure setup. Cloud storage platforms, especially Pastebin and Google Drive, are the most commonly abused, with 43 malware families exploiting such platforms. Messaging applications like Telegram and Discord are also prevalent and, to a far lesser extent, Slack, with infostealers primarily associated with most instances involving these platforms.
Threat actors’ increasing use of Legitimate Internet Services (LIS) reveals a calculated intention to exploit the inherent trust users and organizations place in these platforms, primarily by blending in with legitimate traffic, making their malicious activities harder to detect and ensuring a more persistent presence in their target environments. The objectives behind this are clear: to camouflage their operations, enhance data theft efficiency, reduce operational overhead, and lower infrastructure costs. By leveraging trusted platforms, they aim to evade traditional defenses, maintain high availability and uptime for their operations, and improve operational security.
However, the misuse of LIS is not without challenges for threat actors. Limitations imposed by the functionality and restrictions of the misused services, the ease with which these services can be blocked within the victim network, and dedicated teams within LIS detecting and countering system misuse and abuse are some of the obstacles they face.
The misuse of Legitimate Internet Services (LIS) by threat actors presents a significant risk to organizations. The risk arises from the strategic blending of malicious activities within legitimate traffic, making detection and mitigation more challenging. Threat actors are increasingly leveraging these trusted platforms to enhance their efficiency in data theft and significantly weaken traditional defenses.
HiatusRATs Latest Campaign Sees Shift in Targeting and Infrastructure
The report by Lumen Black Lotus Labs details the resurgence of a cyber campaign named HiatusRAT, first discovered in March 2023. The threat actor’s latest campaign introduces new malware samples and infrastructure. However, a significant shift was observed in their reconnaissance and targeting activities compared to earlier campaigns, which mainly focused on Latin American and European entities, where the malware exploited edge routers to passively gather traffic, creating a covert command and control (C2) infrastructure network. The recent campaign targeted U.S. military procurement systems and Taiwan-based organizations.
In HiatusRAT’s latest campaign, Black Lotus Labs’ investigation uncovered prebuilt Hiatus binaries that target new architectures such as Arm, Intel 80386, and x86-64 and previously targeted architectures such as MIPS, MIPS64, and i386. Additionally, the threat actor employed the same upload server for malware communications detailed in Black Lotus Labs’ previous report. A significant observation was the transition of HiatusRAT payloads between hosting servers: initially on a VPS with IP 207.246.80[.]240 in June and July, and then moving to another VPS at IP 107.189.11[.]105 in August.
Analyzing the telemetry data, Black Lotus Labs identified a significant volume of inbound connections from Taiwan, accounting for over 91% of the total. Black Lotus Labs also observed a notable preference for Ruckus-manufactured edge devices. Aiming to understand the infrastructure further, Black Lotus Labs identified “upstream” or Tier 2 servers, which seemed to manage the primary Tier 1 servers. One was located in China, with three others identified in the US, one of which was used as a reconnaissance server.
In one case from June, the threat actor’s payload server and reconnaissance server connected to a U.S. Department of Defense server associated with proposals for defense contracts. In a roughly two-hour time span, over 11MBs of data was transferred. It’s suspected the actor was searching for publicly available information about military requirements and organizations involved in the Defense Industrial Base, potentially for subsequent targeting.
The threat actor’s intentions appear to be multifaceted. Initially, the campaign targeted Latin American and European organizations. However, a significant shift in reconnaissance and targeting was observed in the latest campaign, focusing on the U.S. military procurement system and Taiwan-based organizations. This shift in targeting, especially the reconnaissance against a U.S. military system, suggests a strategic alignment with the interests of the People’s Republic of China, as corroborated by the 2023 ODNI threat assessment. Even after their initial exposure, the bold continuation of their operations indicates a high level of confidence and possibly a sense of impunity.
The threat actor’s objectives seem to be information gathering and potential espionage. The recent targeting suggests an interest in gathering publicly available information about military requirements and a broader geopolitical objective. The malware’s capability, including remotely interacting with the system, converting the system into a covert proxy, and packet capture, provides the threat actor with a wealth of information, which the actors can use for various purposes, including espionage. The threat actor behind HiatusRAT demonstrated several technical capabilities, including the ability to recompile malware samples for different architectures, acquire and transition payload servers, and infect a U.S. Department of Defense server.
The HiatusRAT campaign, as observed by Black Lotus Labs, presents a significant risk to organizational operations, assets, and individuals. The malware’s ability to exploit edge routers, passively collect traffic, and establish a covert C2 network directly threatens data confidentiality, integrity, and availability. The threat actor’s persistence and adaptability indicate a high likelihood of continued malicious activities. The shift in targeting suggests a strategic alignment with the interests of the People’s Republic of China.
Threat Actors Increase Use of Open Redirects for Phishing
Kroll’s Cyber Threat Intelligence (CTI) team’s blog post, “Increased Use of Open Redirects in Phishing Campaigns,” highlights the growing trend of phishing campaigns exploiting open redirects. Open redirects are vulnerabilities often found in websites, allowing threat actors to manipulate legitimate URLs to redirect users to potentially harmful external sites. The post emphasizes the recent surge in such attacks, particularly targeting the financial and professional services sectors. By leveraging trustworthy websites, malicious actors can deceive users and network technology, leading victims to malicious sites that aim to steal sensitive information.
Open redirects have been a known vulnerability for some time, but their use in phishing campaigns has seen a noticeable uptick in Q2 2023. These vulnerabilities arise when websites allow user-supplied input as a part of a URL parameter in a redirect link without adequate validation or sanitization. Threat actors can exploit this weakness to craft malicious URLs that seem legitimate but redirect users to harmful sites. While this tactic isn’t new, its increased use, especially targeting the financial and professional services sectors, is of concern. Typically, a threat actor sends a phishing email containing a benign link, often mimicking political or news websites. This deceptive approach, combined with the credibility of a legitimate website, makes it easier for users to be tricked into clicking malicious links.
Kroll’s Cyber Threat Intelligence (CTI) team has been tracking a significant uptick in phishing campaigns leveraging open redirects, with a pronounced increase observed in Q2 2023. These actors have narrowed their focus, targeting the financial and professional services sectors. This sector-specific targeting suggests that these industries are viewed as high-value targets, possibly due to the sensitive information they hold.
The modus operandi of these campaigns often involves sending phishing emails that mimic political or news websites, a tactic that capitalizes on the inherent trust users place in these outlets. By crafting URLs that leverage legitimate websites, these threat actors can effectively deceive users, further facilitated by bypassing some solutions that typically scan for malicious content. Once clicked, these deceptive links redirect victims to malicious sites, primarily designed to collect login credentials.
Adding to the complexity of these campaigns, Kroll’s analysis revealed the threat actors’ sophisticated evasion techniques by employing services like the Cloudflare CAPTCHA tool, deliberately designed to hinder automated analysis. Additionally, geo-blocking, which restricts access based on a user’s location, ensures more focused and effective targeting within specific geographies.
Furthermore, Kroll’s CTI team observed other campaigns leveraging “DocuSign” email lures. These campaigns contained multiple redirect paths, eventually leading to a phishing page, often using a similar phishing kit optimized for credential capture. This broad and adaptable toolset, combined with the varied techniques employed by the threat actors, emphasizes their evolving capabilities and the breadth of their toolkit.
The primary intention behind this campaign appears to be financial. By collecting credentials, the threat actors can sell access to other threat actors to facilitate their malicious activities. The ultimate objectives of this campaign, as observed, are multifaceted. Primarily, open redirects appear to be the establishment of credibility. By leveraging the domain of a legitimate website, threat actors can make their phishing links appear more trustworthy to potential victims. This increased credibility enhances the likelihood of users clicking on the malicious link, thereby increasing the success rate of the phishing campaign. Additionally, these threat actors can bypass some security solutions and measures that typically scan for malicious domains by using legitimate domains.
The primary risk arises from the fact that open redirects can be crafted to appear as legitimate URLs, thereby increasing the likelihood of users falling victim to these campaigns. Leveraging open redirects poses a significant risk to an organization’s operations, potentially leading to compromised credentials or malware deployment. Given the observed uptick in such campaigns, especially in Q2 2023, the likelihood of an incident is high.
The threat actor’s ability to target specific geographies and sectors amplifies the risk. The seemingly benign links add another layer of risk, as users are more likely to trust and click on these links. The ability of these campaigns to bypass basic defensive tools and spam filters indicates that many existing security measures may be inadequate against this evolving threat.
Threat Actors Exploit Vulnerable Web Servers or Brute-Forces RDP Credentials to Deploy Toolset and Ransomware
ESET’s blog post titled “Scarabs colon-izing vulnerable servers” provides an in-depth analysis of Spacecolon, a toolset designed to deploy various tools and, occasionally, variants of the Scarab ransomware. Spacecolon has been active since at least May 2020. It was first documented in early February 2023 by a Polish cybersecurity blog based on an analysis by the Polish cybersecurity firm Cyberarms. Spacecolon’s usage continues, with the most recent build identified as of May 2023.
The toolset comprises three main components: HackTool, Installer, and Service. ESET has also observed the development of a new ransomware family, believed to be crafted by the same developer behind Spacecolon. This new ransomware has been found on VirusTotal, originating from Turkey, but it hasn’t been seen in active campaigns, suggesting it might still be in the development phase. ESET has not been able to attribute the use of Spacecolon to any known threat actor group.
The threat actors gain initial access by exploiting vulnerable web servers or brute-forcing RDP credentials. Their operations are characterized by using Spacecolon, which comprises three components, “HackTool,” Installer, and Service.
Once the actors gain access, they deploy a script that patches the ZeroLogon vulnerability (CVE-2020-1472) and HackTool, the primary component of Spacecolon that allows them to deploy the other two. Using this component, the actors can deploy additional third-party tools on demand to disable security products, collect sensitive information, and gain further access. HackTool is GUI-operated and retrieves a text file (used to set up additional tools) from the command and control (C2) server before displaying the GUI interface. Some functions of HackTool are no longer functional. The tool is frequently updated, with a new version likely being released in the future.
The exact reasoning behind the threat actors deploying a script that patches the ZeroLogon vulnerability remains uncertain. It could be a false flag operation to divert attention or obfuscate their true initial access methods. Alternatively, they might have exploited this vulnerability in a domain controller to elevate privileges and subsequently gained access to the web server, patching it afterward to cover their tracks.
At the discretion of the threat actors, they can deploy Installer, which is solely used to install Service, which provides further remote access. However, ESET has observed Service installed manually using Impacket, and they have not found any new builds of Installer, suggesting Installer is no longer maintained, or ESET lacks the data.
If Service is deployed, it will run as a Windows service and act as a simple backdoor. Once launched, Service creates three timers: one that sends a KEEP message to the C2 server every 10 seconds, another that flushes the DNS cache every five hours, and another that connects to the C2 server every five minutes. The threat actors can use Service to execute arbitrary commands and executables, open and close an SSH tunnel, obtain machine info, and update the INI file. The latest variation of Service (earliest known is March 2023) runs a local HTTP server on port 8347. A single request is issued to the local HTTP server to obtain machine information. The server returns the machine information in an HTTP response and stores it in its INI file.
Another tool the threat actors have deployed is a custom .NET payload designed to install chosen Windows Updates. The list of updates installed is available here. As seen from the list, most vulnerabilities patched revolve around ZeroLogon. The threat actors may be doing this to make intrusion analysis more challenging as their initial access vector, ZeroLogon, will be up-to-date and, therefore, not a likely entry vector.
Then, the actors may choose to deploy the Scarab ransomware through the Service component or manually. Scarab contains code overlaps with the Buran and VegaLocker families and relies on an embedded configuration whose format is almost identical to Zeppelin ransomware. The embedded configuration determines the file extension for encrypted files, filenames, list of file extensions to encrypt, and the ransom note. The vast majority of Scarab builds ESET drop and execute an embedded Delphi-written ClipBanker that replaces any string resembling a cryptocurrency wallet in the clipboard with an actor-controlled one. Based on file naming patterns, more than 50% of Scarab configurations in ESET’s telemetry may be related to Spacecolon, with two samples conclusively linked.
Furthermore, ESET observed a new ransomware family being developed, with samples uploaded to VirusTotal from Turkey. They have high confidence that it is written by the same developer as Spacecolon. However, they have not observed this ransomware family being deployed in the wild and assess that it’s still in development.
ESET has not observed any pattern in Spacecolon victims besides them being vulnerable to the initial access methods employed by the threat actors. According to ESET’s telemetry, victims are in Canada, Mexico, Brazil, China, France, Spain, Morocco, Thailand, and Japan. Additionally, the threat actors do not attempt to hide their malware, leaving plenty of artifacts on compromised systems, and implement little to no anti-analysis or anti-emulation techniques.
Spacecolon-associated threat actors and their deployment of Spacecolon, especially the HackTool and Scarab ransomware, present a pronounced risk to organizations. Their ability to exploit vulnerable web servers or brute-forcing RDP credentials further heightens the risk. Using a custom .NET tool, which patches ZeroLogon vulnerabilities, showcases their operational sophistication and complicates intrusion analysis, elevating the risk of undetected intrusions.
A successful intrusion by these actors can have dire consequences. Their capabilities range from disabling security measures to data exfiltration and encryption, jeopardizing organizational data’s confidentiality, integrity, and availability. The Service component of Spacecolon grants them significant control over infected systems, further endangering organizational operations. The Scarab ransomware’s inclusion of ClipBanker, which manipulates cryptocurrency wallet addresses, poses additional financial risks to entities engaged in cryptocurrency transactions.
The absence of a clear victim pattern suggests that organizations across diverse sectors and regions are vulnerable. Given the broad potential impact, organizations must evaluate and fortify their defenses against this threat.
Latest Additions to Data Leak Sites
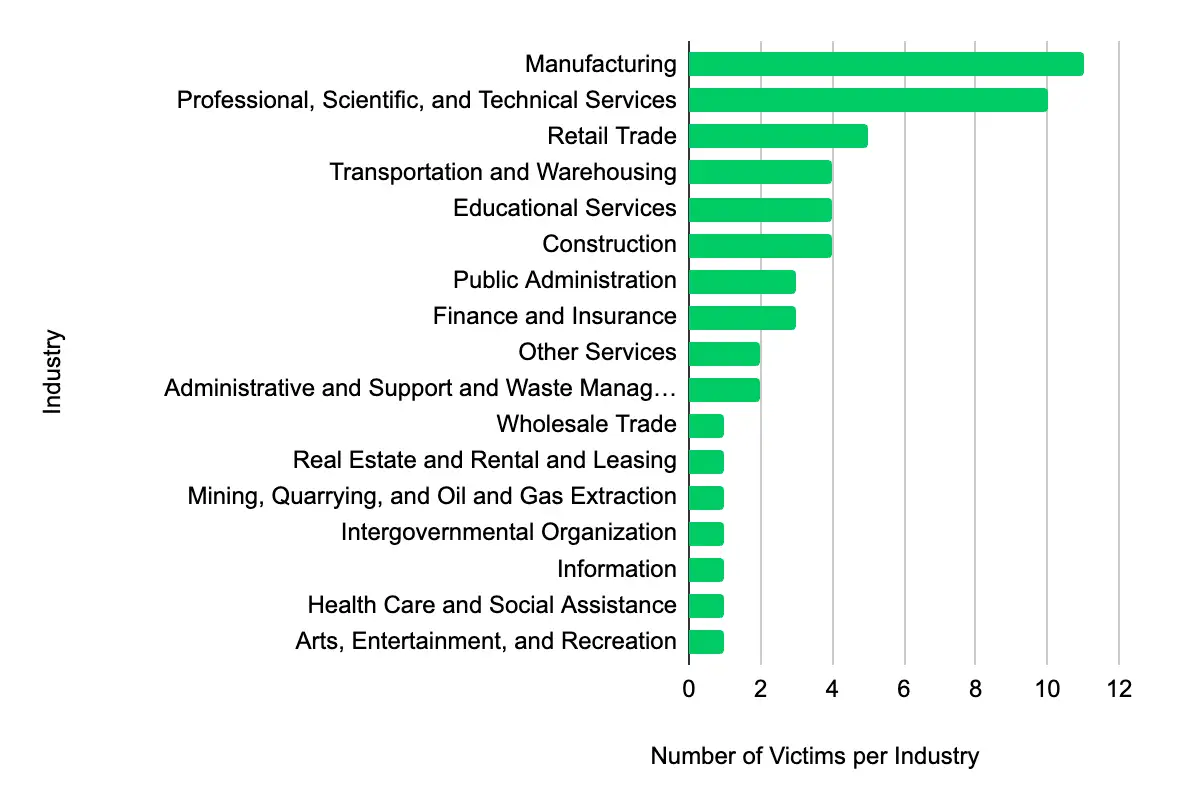
In the past week, monitored data extortion and ransomware threat groups added 55 victims to their leak sites. Of those listed, 32 are based in the US. The most popular industry listed was Manufacturing, with 11 victims. They were followed by 10 in Professional, Scientific, and Technical Services, five in Retail Trade, and four each in Transportation and Warehousing and Educational Services.
This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 3 CVEs to its Known Exploited Vulnerabilities Catalog
Within the past week, CISA added three CVEs to the catalog in the past week, affecting products from Adobe ColdFusion, Veeam Backup & Replication, and Ivanti Sentry. These vulnerabilities allow threat actors to conduct various actions, including bypassing authentication to code execution. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA setting mitigation due dates between 11 September and 12 September 2023.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-26359 | Adobe | ColdFusion | Adobe ColdFusion contains a deserialization of untrusted data vulnerability that could result in code execution in the context of the current user. | 9/11/2023 |
| CVE-2023-27532 | Veeam | Backup & Replication | Veeam Backup & Replication Cloud Connect component contains a missing authentication for critical function vulnerability that allows an unauthenticated user operating within the backup infrastructure network perimeter to obtain encrypted credentials stored in the configuration database. This may lead to an attacker gaining access to the backup infrastructure hosts. | 9/12/2023 |
| CVE-2023-38035 | Ivanti | Sentry | Ivanti Sentry, formerly known as MobileIron Sentry, contains an authentication bypass vulnerability which may allow an attacker to bypass authentication controls on the administrative interface due to an insufficiently restrictive Apache HTTPD configuration. | 9/12/2023 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share