New Linux Backdoor from North Korea, LATRODECTUS Phishing Surge, Malicious LNK Files, Data Leak Sites Grow, and CISA Warns of 5 Active Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
North Korean Actors Develop New Linux Backdoor
North Korean Threat Actor – Malware – Backdoor – Trojanized Installation Packages – Supply Chain Attack – Springtail – Linux.Gomir – All Industries
Insights & Determinations
- Evolving Cyber Capabilities of Springtail: Springtail’s development of the Linux.Gomir backdoor and the deployment of Troll Stealer in trojanized software packages reflect North Korea’s evolving and sophisticated cyber capabilities, specifically targeting Linux systems to expand their espionage toolkit.
- Supply Chain Vulnerabilities: The campaign’s use of trojanized software installation packages underscores the significant threat posed by software supply chain attacks. These attacks infiltrate secure environments by leveraging third-party sites and masquerading as official applications, highlighting the need for stringent supply chain security measures.
- Long-term Espionage and Data Exfiltration: Springtail’s malware, including Troll Stealer and Linux.Gomir is designed for long-term espionage and extensive data theft. The malware’s capabilities to exfiltrate files, capture screenshots, and gather system information indicate a focus on persistent surveillance and intelligence gathering.
- Strategic and Geopolitical Implications: The potential for unauthorized access to critical systems, operational disruption, and exposure of sensitive information poses severe risks. Organizations must be prepared for the broader impacts, including reputational damage, legal and regulatory repercussions, and geopolitical tensions due to state-sponsored cyber activities.
Background
Springtail, a North Korean espionage group, first emerged in 2014 after attacking Korea Hydro and Nuclear Power with spear-phishing emails that installed disk-wiping malware. Recently, the FBI, State Department, and NSA issued an alert on Springtail’s attempts to exploit weak DNS DMARC policies to mask spear-phishing campaigns, posing as journalists and East Asian experts.
Campaign Overview
First documented by South Korean security firm S2W on February 7, 2024, Springtail delivered a new malware family named Troll Stealer using Trojanized software installation packages.
Troll Stealer, written in Go, contains many code overlaps with earlier malware used by Springtail. It can steal a range of information from infected computers, including:
- Files
- Screenshots
- Browser data
- System information
It can also copy the South Korean public key infrastructure schema GPKI (Government Public Key Infrastructure) folder on infected computers.
The malware was distributed inside installation packages for TrustPKI and NX_PRNMAN, software developed by SGA Solutions.
- These installation packages were downloaded when a user downloaded security programs from a Korean construction-related association’s website.
- Users were required to log in, and the trojanized packages were among those users had to install.
Troll Stealer was also delivered in Trojanized Installation packages for Wizvera VeraPort. However, how these installation packages were delivered during this campaign is unclear.
Threat Analysis
Linux.Gomir is structurally almost identical and shares extensive code with the Windows Go-based backdoor GoBear. Any functionality that is operating system-dependent is either missing or reimplemented in Linux.
If the command line contains “install” as the only argument, it attempts to install itself with persistence by checking its group ID.
If group ID is 0 (superuser privileges):
- Copies itself to /var/log/syslogd
- Creates a systemd service named “syslogd” at /etc/systemd/system/syslogd.service
- Deletes the original executable
- Terminates the original process
If the group ID is not 0:
- Configures a crontab to start the backdoor on every reboot
- Creates a helper file (cron.txt) in the current directory
- Lists pre-existing crontab entries and appends to cron.txt
- Updates the crontab configuration
- Deletes the helper file
- Executes itself without any command-line parameters
Once installed and running, it periodically communicates with its command-and-control (C2) server by sending HTTP POST requests.
- Expects a response containing a string starting with “S”
- Decodes the remaining string using Base64
- Decrypts the command using a custom encryption algorithm
Linux.Gomir can execute 17 different commands, similar to the GoBear Windows backdoor.
Key Commands:
- Shell Execution: Execute arbitrary shell commands using the specified environment variable “SHELL” or a fallback shell.
- Terminate Process: Stop its own process to halt the backdoor.
- Directory Statistics: Gather and report statistics about directory trees (subdirectories, files, total size).
- System Configuration: Report system details (hostname, username, CPU, RAM, network interfaces).
- Reverse Proxy: Start a reverse proxy to connect to control endpoints, using SSL encryption consistent with revsocks.
- File Operations: Create or exfiltrate arbitrary files on the affected computer.
This backdoor’s extensive command set enables significant control over infected systems, posing a substantial threat to network security.
Risk & Impact Assessment
The primary risk from this attack lies in Springtail’s potential to gain unauthorized access to highly sensitive data and critical systems, exfiltrate data, disrupt services, and engage in long-term espionage.
- Both Troll Stealer and Linux.Gomir have extensive capabilities to steal files. Troll Stealer can also steal screenshots, browser data, system information, and the GPKI folder.
- Springtail may aim to disrupt critical services by using their persistent access to systems, impacting government, financial, and critical infrastructure operations.
- Maintaining long-term access and control through persistent malware installations allows for ongoing surveillance and continuous data collection, supporting long-term espionage campaigns.
The direct impacts stemming from these risks include:
- Exposure of Confidential Information: Stolen sensitive materials could be exploited to gain a competitive advantage or further North Korean national interest.
- Operational Disruption: The inaccessibility of critical systems and data due to malware activity leads to halted operations, impacting business continuity and critical infrastructure services.
Beyond these risks and impacts, organizations suffering from such attacks could face other risks and impacts, such as:
- Reputation Damage: Loss of trust among customers, partners, and stakeholders could severely damage an organization’s reputation and lead to a business decline and difficulty acquiring new customers.
- Legal and Regulatory Risks: Legal risks associated with data breaches, including litigation from affected parties and penalties from regulatory bodies for failing to comply with data protection laws.
- Long-term Strategic Changes: Beyond the immediate consequences, there can be long-term strategic impacts, such as the need to overhaul cybersecurity practices, implement new security technologies, and possibly retrain staff, all of which require significant investment.
- Geopolitical Risks: Given the state actor involvement (North Korea), broader geopolitical implications could exist, including strained international relations and targeted sanctions.
Source Material: Symantec, Springtail: New Linux Backdoor Added to Toolkit
LATRODECTUS Loader Phishing Surge
Malware – Malware Loader – Phishing – JavaScript Files – Windows Management Instrumentation (WMI) – msiexec.exe – All Industries
Insights & Determinations
- The addition of new commands, such as retrieving process ancestry and desktop contents, indicates LATRODECTUS is actively being updated and enhanced, highlighting its evolving threat profile.
- The malware’s ability to perform comprehensive system discovery through multiple commands allows attackers to gather extensive information about the infected system, facilitating targeted attacks and exploitation.
- LATRODECTUS can download and execute various payloads, including PE files, DLLs, and shellcode, demonstrating its versatility and potential for causing significant damage and disruption.
- With advanced evasion methods, including anti-analysis checks and file deletion tactics, LATRODECTUS is designed to avoid detection and maintain long-term persistence within infected systems, complicating incident response efforts.
Threat Analysis
Note: The following is based on Elastic Security Lab’s analysis of a packed LATRODECTUS sample.
The sample is a DLL whose file version information shows it masquerades as a Bitdefender kernel-mode driver. Evidence shows that the obfuscation algorithm has changed since initial reporting, indicating continuous development of the loader.
At the start, it resolves all imports. Then, it performs several anti-analysis checks, such as:
- If it’s running in a debugger, virtual machine, or sandbox
- Running as a 32-bit application on a 64-bit OS
- If the system has a valid MAC address
If any of the above conditions are true, it terminates.
The sample was configured to store the malware in the AppData directory. It used the hard-coded string Custom_update and the filename Update_88d58563.dll seeded from the volume serial number.
The sample checked for the existing file AppData\Roaming\Custom_update\update_data.dat to read from. If the file does not exist, it will create the directory before writing a copy of itself in the directory.
After copying the file, it retrieved two command and control (C2) domains. Then, it uses the Windows Component Object Model (COM) to create the hardcoded task name Updater and schedule it to execute upon successful login.
The sample also deleted itself while the process was still running using an alternate data stream, likely implemented to hinder incident response by interfering with collection and analysis. This technique is observed at the start of the infection and when the malware performs an update.
Its communications were encrypted using base64 and RC4 with a hardcoded password. The first communication registered the infected system via an HTTPS POST request, including victim information and configuration details.
Each request is pipe-delimited by an object type (CLEARURL, URLS, ERROR, and COMMAND), ID value, and corresponding argument. The CLEARURL object type is used to delete any configured domains. The URLS object type swaps to a new C2 URL. The ERROR object type was not configured. The sample’s core functionality is executed through the COMMAND object type with the ID and respective argument.
- Example: COMMAND | 12 | http://www.meow123.com/test
This sample’s COMMAND object type had 11 commands. Two of these (retrieve processes and desktop listing) have been added since it was first discovered, indicating the codebase is still active and changing.
- The desktop listing command (ID 2) retrieves a list of the contents of the user’s desktop.
- The retrieve processes command (ID 3) collects the entire running process ancestry from the infected machine.
The collect system information command (ID 4) creates a new thread that runs 11 system discovery/enumeration commands. The results of each command are placed into a URI with corresponding collected data.
The download and execute PE command (ID 12) downloads a PE file from the C2 server, writes the content to disk with a randomly generated file name, and executes the file. Similarly, the download and execute DLL command (ID 13) downloads a DLL from a C2 server, writes it to disk with a randomly generated file name, and executes the DLL using rundll32.exe.
The download and execute shellcode command (ID 14) downloads shellcode from the C2 server via InternetReadFile, allocates and copies it into memory, and then directly calls it with a new thread pointing at the shellcode.
The download and execute hosted ICEID payload command (ID 18) downloads two ICEDID components from a LATRODECTUS server and executes them using a spawned rundll32.exe process. Elastic has not observed the usage of this command.
The beacon timeout command (ID 19) supports jitter for beaconing to C2. Jitter allows attackers to randomize their beaconing activity by varying the timing interval between beacons. This can make it harder to detect due to the randomness it introduces to beaconing intervals. The sample calculated the interval by generating a random number by seeding a combination of the user’s cursor position multiplied by the system’s uptime, passing the result as a parameter.
Elastic’s analysis of this sample indicates a connection or working relationship between ICEDID and LATRODECTUS. While it’s inconclusive, they appear, at least superficially, affiliated. One hypothesis is that LATRODECTUS is being actively developed as a replacement for ICEDID, with the assumption that its ability to download and execute ICEDID payloads was included until LATRODECTUS’ capabilities were at an acceptable level.
Risk & Impact Assessment
The primary risks of LATRODECTUS lie in its ability to download and execute various payloads, which poses a significant threat to organizational operations, systems, and data.
The direct impacts of these risks include:
- Breaches of confidentiality stemming from the theft of sensitive information.
- Significant operational downtime resulting from the potential delivery of ransomware, rendering them inaccessible, decreasing productivity, and potentially causing revenue loss.
- Delay In detection and response due to its advanced evasion techniques and obfuscation, allowing the malware to remain undetected for extended periods.
Additional risks of LATRODECTUS include:
- Undetected prolonged presence in systems due to its anti-analysis checks and obfuscation.
- A launching point for future attacks, as the malware can deliver malware and enable persistent access.
Beyond these risks and impacts, organizations suffering from such an infection could face other risks and impacts, such as:
- Reputation Damage: Loss of trust among customers, partners, and stakeholders could severely damage an organization’s reputation and lead to a business decline and difficulty acquiring new customers.
- Legal and Regulatory Risks: Legal risks associated with data breaches, including litigation from affected parties and penalties from regulatory bodies for failing to comply with data protection laws.
- Long-term Strategic Changes: Beyond the immediate consequences, there can be long-term strategic impacts, such as the need to overhaul cybersecurity practices, implement new security technologies, and possibly retrain staff, all of which require significant investment.
- Geopolitical Risks: Implications could exist, including strained international relations and targeted sanctions.
Source Material: Elastic Security Labs, Spring Cleaning with LATRODECTUS: A Potential Replacement for ICEDID
New Backdoor Delivered via Malicious LNK Files
Russian Threat Actor – Turla – Malware – Backdoor – Tiny Backdoor – Malware Delivery – LNK Files – MSBuild – All Industries
Insights & Determinations
- The backdoor leverages PowerShell scripts and MSBuild projects, demonstrating advanced evasion techniques that bypass traditional security measures, making it challenging for security systems to detect and analyze.
- To evade detection, Tiny Backdoor uses scheduled tasks and legitimate processes. It employs multiple threads for various malicious activities, such as command execution, data exfiltration, and system monitoring, increasing its effectiveness and complexity.
- Tiny Backdoor poses significant threats to organizational operations, systems, and data, including unauthorized access, remote command execution, data exfiltration, operational disruption, and potential delivery of secondary payloads.
- The potential for unauthorized access to critical systems, operational disruption, and exposure of sensitive information poses severe risks. Organizations must be prepared for the broader impacts, including reputational damage, legal and regulatory repercussions, and geopolitical tensions caused by state-sponsored cyber activities.
Threat Analysis
Note: The following is based on Cyble’s analysis of the file “Official_Invitation_Final_202406.lnk.”
Infection Chain
- The malicious .LNK file was archived within a ZIP file, potentially delivered to users via phishing emails.
- When a user executes the .LNK file, it triggers the execution of a PowerShell script embedded within it.
- The PowerShell executes a sequence of commands, including reading the content of the .LNK file and writing it into three distinct files in the %temp% location. These files include a lure PDF, encrypted data, and a custom MSBuild project.
- The PowerShell script executes the MSBuild project using “MSBuild.exe” and opens the lure document.
- This MSBuild project decrypts the encrypted data, which is then saved in a %temp% location with the .log extension.
- This .log file, also an MSBuild project, is scheduled to be executed using “MSBuild.exe” through Task Scheduler.
When the scheduled task is triggered, it executes the decrypted MSBuild project (Tiny Backdoor). When the project is built, it runs inline tasks present within the project file directly in memory.
The core functionality of these inline tasks begins with the “Execute” function. This function involves creating two threads. The first thread continuously monitors the running processes in the victim’s machine for any process main window titles containing “MSBuild.exe” and hides if detected.
Before creating the second thread, the function generates a unique identifier (ID) by combining the victim’s machine’s domain name, username, and current process ID retrieved. This ID is used to uniquely identify the infected machine for further communications.
After generating the ID, the function starts the second thread using the generated ID. The thread initiates an HTTP request to the command and control (C2) server, a compromised website, to fetch and execute commands.
Once the HTTP request is formed, the thread sends the request to the C2 server and verifies the response status code. If the response is unsuccessful, the thread terminates. If the response is successful, the thread reads the content and executes the commands.
Tiny Backdoor uses multiple threads, each designed to execute specific tasks:
- Shell thread: Executes commands on the victim’s machine by creating a new process to run the command.
- Sleep thread: Dynamically adjusts the sleep interval of the backdoor.
- Upload thread: Downloads a file from the C2 server and saves it locally on the victim’s machine.
- Download thread: Exfiltrates a file from the victim’s machine to the C2 server.
- Cd thread: Modifies its current directory to the location specified by the attacker.
- Pwd thread: Retrieves the victim’s current directory and sends it to the C2 server.
- PS thread: Runs a PowerShell script asynchronously, captures its output, and sends it back to the C2 server.
Based on the following evidence, Cyble attributes this activity to the Turla APT, a cyberespionage group based in Russia, with a moderate level of confidence.
- This backdoor’s code base has Russian-language comments, indicating the developer speaks Russian.
- The campaign used a lure document referencing a human rights NGO. Turla has a history of targeting NGOs, particularly those with connections to supporting Ukraine.
- This backdoor’s basic first-stage functionalities, coupled with the exploitation of compromised web servers for their command and control (C2) infrastructure, align with Turla’s behavior.
- Using PHP files from the compromised website for C2 communication mirrors Turla’s behavior.
- This backdoor uses an ID in HTTP requests, mirroring the Turla backdoor’s behavior.
- The implementation of thread functionality to execute commands received from the C2 mirrors the TinyTurla backdoor behavior.
Risk & Impact Assessment
The primary risks of Tiny Backdoor lie in its sophisticated ability to infiltrate systems undetected, maintain persistence, and execute a wide range of malicious activities, posing significant threats to organizational operations, systems, and data.
The direct impacts of these risks include:
- Unauthorized Access and Control:
- The backdoor facilitates unauthorized access over the infected machine.
- Remote execution of commands enables attackers to control the system and data as they see fit.
- Breach of Confidentiality:
- The backdoor can exfiltrate personal data, intellectual property, and confidential communications, compromising data confidentiality.
- Operational Disruption:
- Operational downtime due to potential interference with system processes and the execution of arbitrary commands.
- Potential delivery of secondary payloads, such as data wipers and ransomware, causing further disruption.
- Advanced Evasion Techniques:
- The backdoor uses multiple threads for different tasks, increasing the complexity and difficulty of detection.
- The backdoor’s sleep interval can be dynamically adjusted, and legitimate processes (e.g., MSBuild.exe) are used for malicious activities, making it harder for traditional security measures to detect.
Beyond these risks and impacts, organizations suffering from such attacks could face other risks and impacts, such as:
- Reputation Damage: Loss of trust among customers, partners, and stakeholders could severely damage an organization’s reputation and lead to a business decline and difficulty acquiring new customers.
- Legal and Regulatory Risks: Legal risks associated with data breaches, including litigation from affected parties and penalties from regulatory bodies for failing to comply with data protection laws.
- Long-term Strategic Changes: Beyond the immediate consequences, there can be long-term strategic impacts, such as the need to overhaul cybersecurity practices, implement new security technologies, and possibly retrain staff, all of which require significant investment.
- Geopolitical Risks: Given the likely state actor involvement (Russia), broader geopolitical implications could exist, including strained international relations and targeted sanctions.
Source Material: Cyble, Tiny BackDoor Goes Undetected – Suspected Turla leveraging MSBuild to Evade detection
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Educational Services – Construction – Information
Executive Summary
Recent updates to data leak sites reveal a significant decrease from last week’s 205 additions: 117 organizations were added between 13 and 19 May 2024.
Of these leak sites, 3 sites added the most: BlackByte, Lockbit, and 8base.
- BlackByte added 57 organizations.
- Lockbit added 21 organizations.
- 8base added 9 organizations.
Correlating these organizations to their respective industries reveals that Manufacturing, Professional, Scientific, and Technical Services, Educational Services, and Construction were the most heavily involved.
- 30 organizations correlated to the Manufacturing sector.
- 14 organizations correlated to the Professional, Scientific, and Technical Services sector.
- 10 organizations each correlated to the Educational Services and Construction sectors.
Geographically, the United States leads with the highest number of organizations geolocating to this region, followed by the United Kingdom and Italy.
- 60 organizations are headquartered in the United States.
- 8 organizations are headquartered in the United Kingdom.
- 5 organizations are headquartered in Italy.
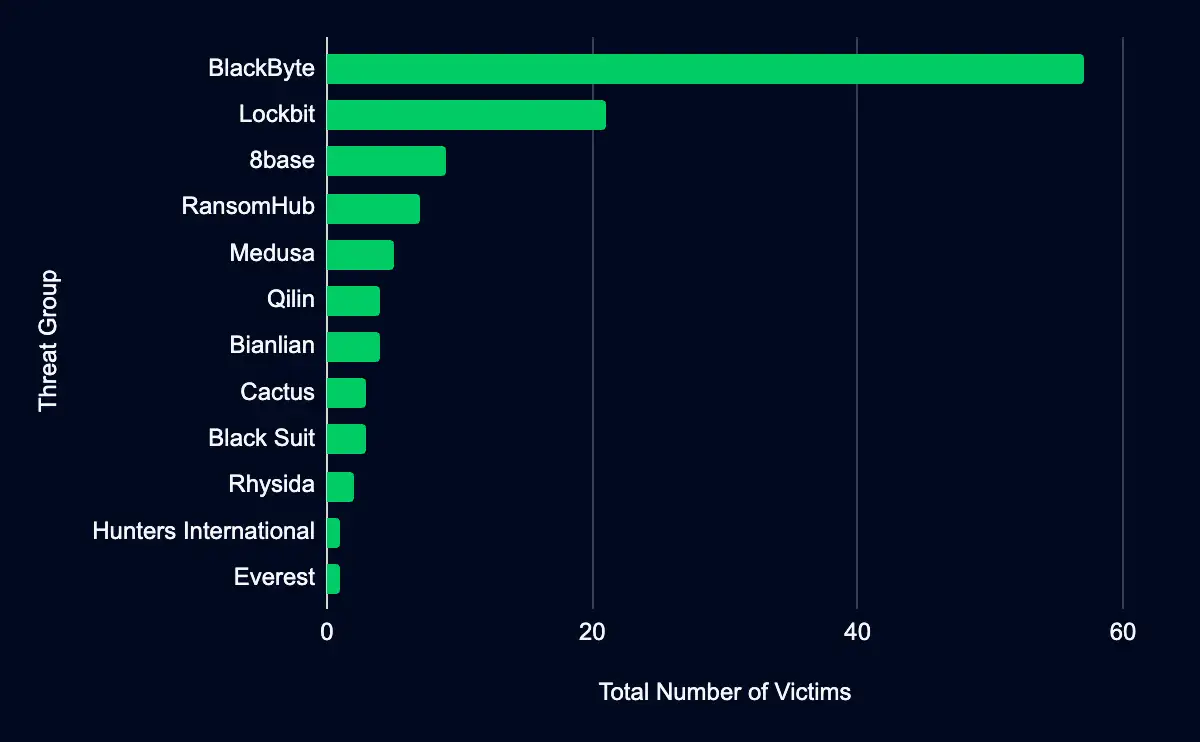
The prominence of groups like BlackByte indicates a trend towards more aggressive operations, likely spurred by volume-driven strategies.
Being listed on a data leak site can lead to significant operational disruptions and severe reputational damage for the affected organizations, pushing the need for advanced countermeasures and robust data protection strategies.
Also, ransomware attacks and leaks impact the listed organization’s suppliers, partners, and customers. Sensitive information, including contracts, pricing strategies, service details, business plans, intellectual property, strategic information, and personal data (such as contact information, payment details, and purchase history), might be exposed, leading to competitive disadvantages, reputational damage, privacy breaches, identity theft risks, and undermining competitive positioning and strategic initiatives.
CISA Warns of Active Exploitation of Flaws in NextGen Healthcare, Google Chromium, and D-Link Devices
NextGen Healthcare Mirth Connect CVE-2023-43208 – Google Chromium V8 CVE-2024-4761 & CVE-2024-4947 – D-Link DIR-600 Router CVE-2014-100005 – D-Link DIR-605 Router CVE-2021-40655
The Cybersecurity and Infrastructure Security Agency (CISA) has flagged five vulnerabilities in NextGen Healthcare Mirth Connect, Google Chromium, and D-Link DIR-600 and DIR-605 routers as actively exploited, escalating concerns over future cyber-attacks.
Analysis
CVE-2023-43208 – NextGen Healthcare Mirth Connect Deserialization of Untrusted Data Vulnerability
- What it allows: Unauthenticated remote code execution
- Risk: This vulnerability could be exploited by attackers to execute arbitrary code on affected systems, potentially leading to complete system compromise. Immediate application of mitigations is crucial to prevent potential breaches.
- Due Date: 2024-06-10
CVE-2024-4947 – Google Chromium V8 Type Confusion Vulnerability
- What it allows: Remote code execution
- Risk: Attackers can exploit this flaw to execute malicious code via a crafted HTML page, affecting various web browsers. Users should prioritize updates to mitigate this risk.
- Due Date: 2024-06-10
CVE-2024-4761 – Google Chromium V8 Out-of-Bounds Memory Write Vulnerability
- What it allows: Out-of-bounds memory write
- Risk: This vulnerability affects multiple Chromium-based browsers, enabling attackers to corrupt memory and potentially execute arbitrary code. Swift application of vendor mitigations is necessary to protect users.
- Due Date: 2024-06-06
CVE-2014-100005 – D-Link DIR-600 Router Cross-Site Request Forgery (CSRF) Vulnerability
- What it allows: Change router configurations
- Risk: By hijacking an existing administrator session, attackers can alter router settings, potentially exposing networks to further attacks. Affected devices, now end-of-life, should be replaced.
- Due Date: 2024-06-06
CVE-2021-40655 – D-Link DIR-605 Router Information Disclosure Vulnerability
- What it allows: Obtain username and password
- Risk: Attackers can forge a post request to gain admin credentials, leading to unauthorized access and control over the router. Legacy devices should be retired and replaced.
- Due Date: 2024-06-06
These vulnerabilities highlight the critical need for timely updates and proactive security measures. Organizations must quickly mitigate these risks and safeguard their systems against potential exploits.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share