Active Exploits on Check Point, North Korean Moonstone Sleet Unveiled, and Snowflake Data Breach Underscores MFA Necessity
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Check Point Vulnerability (CVE-2024-24919) Actively Exploited
- Unveiling the North Korean Cyber Group Moonstone Sleet
- Snowflake Data Breach Highlights Importance of MFA
- Public PoC Exploits Critical Telerik Report Server Flaws
- Latest Additions to Data Leak Sites
- CISA Warns of Active Exploitation of Flaws in Oracle, Check Point, and Linux
Check Point Vulnerability (CVE-2024-24919) Actively Exploited
Check Point Security Gateways – CVE-2024-24919 – Vulnerability Exploitation – Information Disclosure – All Industries
Insights & Determinations
- Critical Vulnerability: CVE-2024-24919 affects Check Point Security Gateways with Remote Access VPN enabled, specifically the Mobile Access blade and Check Point Mobile Secure Workspace with Capsule.
- Ease of Exploitation: The vulnerability can be exploited remotely without requiring user interaction or privileges, making it highly dangerous. A Proof of Concept (POC) to exploit the vulnerability is publicly available as of 31 May 2024.
- Observed Exploitation: Since April 30, 2024, there have been multiple observed exploitation attempts in organization’s environments.
- Potential Consequences: Unauthorized actors can extract password hashes, SSH keys, certificates, and other critical files, leading to full shell access on vulnerable systems.
Threat Analysis
A critical vulnerability has been discovered in Check Point Security Gateways with Remote Access VPN enabled, also known as the “Mobile Access” blade. This vulnerability also affects instances where Check Point Mobile Secure Workspace with Capsule is used. This is particularly dangerous because it requires no user interaction or privileges, making remote exploitation straightforward. This vulnerability is deemed critical as it permits unauthorized actors to extract information from internet-connected gateways. Since April 30, 2024, there have been multiple observed exploitation attempts in customer environments.
The vulnerability impacts all Check Point gateways with the Mobile Access blade enabled, including Capsule Workspace, and has been assigned a CVSS v3.1 base score of 8.6 (HIGH). It allows threat actors to enumerate and extract password hashes for all local accounts, including those used to connect to Active Directory.
While the full extent of the consequences is still unknown, it is clear that password hashes of legacy local users with password-only authentication can be extracted, including service accounts used to connect to Active Directory. Weak passwords can be compromised, leading to further misuse and potential lateral movement within the network.
Additionally, the vulnerability allows threat actors to retrieve all files on the local filesystem, including password hashes for all local accounts, SSH keys, certificates, and other critical files. This enables threat actors to gain full shell access on vulnerable systems with relative ease. Observations indicate that threat actors have been extracting ntds.dit from compromised customers within 2-3 hours after logging in with a local user.
The vulnerability is not tied to specific software versions, and remediations and fixes will need to be implemented via a hotfix released following the vulnerability’s announcement. Gateways using only Site-to-Site IPSEC VPN are not affected.
Risk & Impact Assessment
When it comes to CVE-2024-24919, the ease of exploitation without requiring user interaction or privileges significantly raises the risk level for this security flaw. Confidentiality can be impacted due to unauthorized access to password hashes, SSH keys, certificates, and other critical files being gained by exploiting this vulnerability. Compromise of password hashes and service accounts can lead to unauthorized changes and further network exploration and damage.
Impact regarding availability can include potential disruption of services and unauthorized system control. Data breaches, loss of sensitive information, potential legal liabilities, and damage to reputation due to exploitation of this vulnerability can all impact business operations.
Source Material: Mnemonic, Advisory: Active exploitation of Check Point Remote Access VPN vulnerability (CVE-2024-24919) & NIST
Unveiling the North Korean Cyber Group Moonstone Sleet
Threat Actor – North Korean Threat Actor – Moonstone Sleet – Tactics, Techniques, and Procedures – Malware – Ransomware – FakePenny Ransomware – Trojanized PuTTY – SplitLoader – YouieLoad – DeTankWar Game – Data Theft – Credential Theft – Information – Educational Services – Defense Industrial Base
Insights & Determinations
- Moonstone Sleet, formerly Storm-1789, has become a well-resourced, independent threat group. It now uses unique infrastructure and attack methods while keeping some common North Korean tactics.
- Moonstone Sleet’s operations focus on financial gain and intelligence collection. Activities include deploying custom ransomware, creating malicious games, setting up fake companies, and using IT workers for covert operations.
- Recent campaigns involve complex infection chains for multi-stage payload delivery. The group uses malicious npm packages and custom malware loaders to steal credentials and compromise networks. They use fake companies and personas in phishing campaigns for relationship-building.
- Moonstone Sleet targets software and IT, education, and defense sectors. Their methods lead to risks like ransomware extortion, intellectual property theft, and supply chain attacks, causing severe financial, operational, and reputational damage.
Overview
Microsoft has uncovered a sophisticated threat group, assessed as a North Korean state-aligned group. Formerly known as Storm-1789, the group shared similarities with Diamond Sleet, reusing code from Diamond Sleet malware, like Comebacker, and using techniques such as social media to deliver trojanized software. The group has since developed its own infrastructure and attack methods, emerging as a distinct, well-resourced threat group. It is now identified as Moonstone Sleet.
Microsoft has observed Moonstone Sleet and Diamond Sleet conducting concurrent operations. While Diamond Sleet still utilizes its established tradecraft, Moonstone Sleet employs a mix of typical North Korean techniques and unique attack methodologies.
Moonstone Sleet’s operations support financial and cyberespionage objectives, including deploying custom ransomware, creating malicious games, setting up fake companies, and using IT workers. To date, targeted sectors include individuals and organizations in the software and information technology, education, and defense industrial base sectors.
Threat Analysis
Most recently, in April 2024, Moonstone Sleet delivered a new custom ransomware variant named FakePenny against a company it previously compromised in February. Moonstone Sleet’s objective is likely financial gain, suggesting the actor conducts cyber operations for intelligence collection and revenue generation.
- This is the first time Microsoft has observed Moonstone Sleet deploying ransomware.
- FakePenny includes a loader and an encryptor.
- The ransomware note is very similar to the note used by Seashell Blizzard in its malware NotPetya.
- The ransom demand was $6.6M in BTC, starkly contrasting the lower ransom demands of previous North Korean ransomware attacks, like WannaCry 2.0 and H0lyGh0st.
In February 2024, Moonstone Sleet infected devices using a fully functional downloadable but malicious tank game it developed called DeTankWar (also called DeFiTankWar, DeTankZone, or TankWarsZone). The game requires player registration, username/password, and invite code.
- Typically approached targets through messaging platforms or email, presenting themselves as a game developer seeking investment or developer support and masquerading as a legitimate blockchain company or using fake companies.
- They have also created a public campaign that includes the websites detankwar[.]com and defitankzone[.]com and many X (Twitter) accounts for the personas it uses to approach targets and for the game itself.
- In one case, the fake company was called C.C. Waterfall. They emailed targets with a link to download the game. They presented the game as a blockchain-related project and offered collaboration opportunities.
When launching the game, delfi-tank-unity.exe, additional malicious DLLs are also loaded., including a custom malware loader tracked as YouieLoad.
- It loads malicious payloads in memory and creates malicious services that perform functions such as network and user discovery and browser data collection.
- Group operators execute hands-on-keyboard commands on specific infected devices with further discovery and conduct credential theft.
In January 2024, Moonstone Sleet started creating several fake company websites, employee personas, and social media accounts, impersonating software development and IT services, typically involving blockchain and AI. They used these companies as cover to contact targets.
- From January to April 2024, they used the fake company StarGlow Ventures in a campaign to target organizations in the education and software development sectors.
- StarGlow Ventures posed as a legitimate software development company.
- In phishing emails sent in this campaign, they offered collaboration and support for upcoming projects, citing expertise in developing web apps, mobile apps, blockchain, and AI.
- These emails contained a 1×1 tracking pixel, which likely enabled them to track which targets engaged with the emails.
- While the emails did not contain malicious content or links, the actors likely used this campaign to establish relationships with target organizations.
In a similar campaign, they sent phishing emails using the fake company, C.C. Waterfall, a purported IT consulting organization.
- The campaign targeted higher education organizations, claiming they were hiring new developers or looking for business collaboration opportunities.
- This campaign likely had goals similar to those of the StarGlow Ventures campaign: building relationships with organizations that could be leveraged for revenue generation or malicious access.
In addition to creating fake companies, Moonstone Sleet pursued employment in software development positions at multiple legitimate companies.
- This activity is consistent with previous reporting from the United States Department of Justice that North Korea was using highly skilled remote IT workers to generate revenue.
- However, this Moonstone Sleet activity could be aimed at gaining access to organizations.
Their earliest activity dates to early August 2023, where they delivered a trojanized version of PuTTY via apps like LinkedIn and Telegram and developer freelancing platforms.
- Targets were sent a .zip archive containing the trojanized PuTTY and a text file containing an IP address and a password.
- In 2022, Diamond Sleet employed a similar method—trojanized PuTTY and SumatraPDF—with comparable anti-analysis techniques, underscoring the importance of staying alert.
A complex four-stage infection chain is initiated when the IP address and password are entered into the PuTTY application:
- Stage 1: The trojanized PuTTY decrypts, decompresses, and executes the embedded stage 2 payload SplitLoader.
- Stage 2: SplitLoader decrypts, decompresses, and writes the Stage 3 payload, the SplitLoader DLL file, to disk. It also drops two other encrypted files to disk. Then, it executes SplitLoader via a scheduled task or registry run key.
- Stage 3: SplitLoader decrypts and decompresses the two encrypted files the stage 2 payload dropped. It combines them to create the stage four payload, Trojan loader.
- Stage 4: Once the Trojan loader receives a compressed and encrypted PE file from the C2, it decompresses, decrypts, and executes it.
Moonstone Sleet has used other custom malware loaders delivered by PuTTY that behaved similarly and had arguments that overlapped with Diamond Sleet malware artifacts.
Moonstone Sleet has targeted victims with projects that use malicious npm packages. These projects were often delivered through freelancing websites or other platforms like LinkedIn.
- Used a fake company to send .zip files, invoking a malicious npm package masquerading as a technical skills assessment. When loaded, the malicious package used cURL to connect to an actor-controlled IP and drop additional malicious payloads, such as SplitLoader.
- In another incident, they delivered a malicious npm loader, leading to credential theft from LSASS.
Risk & Impact Assessment
Moonstone Sleet poses significant risks through its sophisticated attack methods, which target various sectors, including software and IT, education, and the defense industrial base.
The group’s activities have far-reaching implications, including ransomware and extortion, intellectual property theft, credential theft, and malware deployment, and supply chain attacks.
Ransomware and Extortion
- Moonstone Sleet deploys custom ransomware, demanding ransoms as high as $6.6M in BTC. This poses a significant financial risk to targeted organizations.
- Such high ransom demands can severely strain organizations’ financial resources, especially smaller ones, potentially leading to bankruptcy or severe budget reallocations.
- Successful ransomware attacks can cause significant downtime, disrupt business operations, and lead to loss of revenue.
Intellectual Property Theft
- Moonstone Sleet aims to steal valuable intellectual property, which can undermine businesses’ competitive advantage.
- Theft of proprietary technology and confidential information can stall innovation and result in financial losses due to lost intellectual property.
Credential Theft and Malware Deployment
- Techniques involving credential theft and deployment of custom malware loaders (e.g., YouieLoad) enable extensive network compromise, leading to persistent access and further exploitation.
- Persistent access can facilitate the exfiltration of large volumes of data, including sensitive personal and corporate information.
Supply Chain Attacks
- Extensive targeting of software development firms increases the risk of large-scale supply chain attacks, which can propagate malware to numerous downstream users.
- A successful supply chain attack can affect a wide range of organizations, amplifying the impact of a single intrusion.
Beyond these risks and impacts, organizations suffering from such attacks could face other risks and impacts, such as:
- Reputation Damage: Loss of trust among customers, partners, and stakeholders could severely damage an organization’s reputation and lead to a business decline and difficulty acquiring new customers.
- Legal and Regulatory Risks: Legal risks associated with data breaches, including litigation from affected parties and penalties from regulatory bodies for failing to comply with data protection laws.
- Long-term Strategic Changes: Beyond the immediate consequences, there can be long-term strategic impacts, such as the need to overhaul cybersecurity practices, implement new security technologies, and possibly retrain staff, all of which require significant investment.
- Geopolitical Risks: Given the state actor involvement (North Korea), broader geopolitical implications could exist, including strained international relations and targeted sanctions.
Source Material: Microsoft, Moonstone Sleet emerges as new North Korean threat actor with new bag of tricks
Snowflake Data Breach Highlights Importance of MFA
Data Breach – Infostealer – Compromised Credentials – Snowflake – Data Lake – All Industries
Snowflake’s preliminary investigative findings indicate that the breach involved an attacker leveraging credentials previously purchased or obtained through infostealing malware, targeting users with single-factor authentication, not a vulnerability, misconfiguration, or breach in Snowflake’s platform.
Why it matters: This incident is a prime example of how a stolen credential can be used to steal massive amounts of data and potentially affect hundreds of customers. This incident underscores the importance of using multi-factor authentication and vigilant credential management to prevent unauthorized access and protect sensitive data.
- Snowflake is a cloud data platform that provides a unified system for managing data.
- It’s designed to be faster, easier to use, and more flexible than traditional data warehouses.
Background: On 31 May, Hudson Rock published a blog post, which has since been removed, of their online interactions with an attacker who claimed they had breached Snowflake’s system to steal a massive trove of data.
- The attacker claimed to have stolen personal data belonging to 560 million Ticketmaster customers and 30 million Santander customers.
- The data was posted for sale on the Russian-language cybercrime forum exploit[.]in, and data samples were included in the post.
According to Hudson Rock, the attacker was able to sign into a Snowflake employee’s ServiceNow account using stolen credentials. The attacker then claimed to be able to generate session tokens, which enabled them to access and exfiltrate sensitive data.
- “A single credential resulted in the exfiltration of potentially hundreds of companies that stored their data using Snowflake, with the threat actor himself suggesting 400 companies are impacted.”
- The attacker shared a CSV file with Hudson Rock, which lists over 2,000 customer instances relating to Snowflake’s Europe servers.
- The file included a Snowflake employee infected by an infostealer on 5 October 2023.
- The attacker confirmed they used this employee’s credentials to access the environment.
While the original blog post has since been removed, it was archived by the Wayback Machine and can be viewed here.
Snowflake’s investigation: On 2 June, Snowflake posted preliminary findings from their investigation, which was conducted in coordination with CrowdStrike and Mandiant. In their statement they stated that:
- The attack appears to be a targeted campaign directed at users with single-factor authentication.
- The attackers leveraged credentials previously purchased or obtained through infostealing malware.
- The attacker obtained personal credentials and accessed demo accounts belonging to a former Snowflake employee. The demo accounts do not contain sensitive data and do not allow access to Snowflake’s production or corporate systems.
- The access was possible because the demo account was not behind Okta or Multi-Factor Authentication (MFA), unlike Snowflake’s corporate and production systems.
Snowflake and Mandiant are informing potentially affected organizations they believe may have been affected.
Lessons learned: This breach underscores the critical importance of implementing strong authentication measures and constantly monitoring and managing credentials. Measures that could have potentially mitigated the impact of this breach include:
- Enforcing multi-factor authentication and regular credential rotation on all accounts.
- Establishing Network Policy Rules that only allow authorized users or traffic from trusted locations.
In addition, Snowflake recommends reviewing its investigative and hardening guidelines for recommended actions to investigate potential threat activity within Snowflake accounts.
The bottom line: Organizations must learn from incidents like this and prioritize security measures to protect sensitive data and prevent unauthorized access. This breach is a stark reminder of the ongoing and evolving threats in the cybersecurity landscape and the need for constant vigilance and proactive security practices.
Source Material: Snowflake, Detecting and Preventing Unauthorized User Access; Hudson Rock (Wayback Machine), Snowflake Massive Breach Access Through Infostealer Infection; and The Record, Cloud company Snowflake denies that reported breach originated with its products
Public PoC Exploits Critical Telerik Report Server Flaws
Proof of Concept Exploit – Remote Code Execution (RCE) – Progress Telerik Report Server CVE-2024-4358 – Progress Telerik Report Server CVE-2024-1800 – All Industries
The Rundown
Two vulnerability researchers published a proof-of-concept (PoC) exploit script that chains a Progress Telerik Report Servers authentication bypass vulnerability with a vulnerability that allows remote authenticated attackers to execute arbitrary code, allowing attackers to achieve unauthenticated remote code execution.
Why it matters: Although exploiting the vulnerabilities is complex, the detailed write-up and exploit script’s public availability significantly lowers the barrier for entry, raising the risk of exploitation.
- Exploiting CVE-2024-4358 allows an attacker to bypass authentication and create an admin account.
- With the authentication bypassed, it’s possible to exploit CVE-2024-1800 to achieve remote code execution (RCE), like launching cmd.exe.
Background: The Telerik Report Server is an API-powered end-to-end encrypted report management solution organizations use to streamline reports’ creation, sharing, storage, distribution, and scheduling.
The vulnerabilities: The authentication bypass vulnerability is tracked as CVE-2024-4358 (CVSS score: 9.8). It allows the creation of admin accounts without checks.
- This issue was addressed via an update (Telerik Report Server 2024 Q2 10.1.24.514) on 15 May, and the vendor published a bulletin.
- While there are no reports of active exploitation of CVE-2024-4358, system administrators should review the users list for any new Local users added at ‘{host}/Users/Index’ they don’t recognize.
The second vulnerability required for achieving RCE is CVE-2024-1800 (CVSS score: 8.8). This deserialization issue allows remote authenticated attackers to execute arbitrary code on vulnerable servers.
- Progress released a security update on 7 March 2024 through Telerik Report Server version 2024 Q1 10.0.24.305.
The bottom line: High-level cybercriminals don’t typically ignore critical flaws in Progress Software, as many organizations use the vendor’s products worldwide. Therefore, organizations must apply the available updates as soon as possible, aka upgrade to version 10.1.24.514 or later, which addresses both flaws.
Source Material: Summoning Team
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Information – Health Care – Construction – Retail
Executive Summary
Recent updates to data leak sites reveal that 149 organizations were listed on ransomware data leak sites between 20 May and 2 June 2024, with the majority operating in the Manufacturing sector.
Of these leak sites, 4 sites added the most: Lockbit, Play, RansomHub, and Dan0n:
- Lockbit added 25 organizations.
- Play added 17 organizations.
- RansomHub and Dan0n added 13 organizations each.
Manufacturing, Professional, Scientific, and Technical Services, Information, Health Care, Construction, and Retail are the industries most heavily involved, with 96 organizations falling within these sectors.
Geographically, the United States leads with the highest number of organizations geolocating to this region, followed by Canada and France.
Industry Analysis
Almost every sector was involved in these leaks, with manufacturing as the primary target. 17% (26) of the organizations listed operate in this industry.
- 16 (11%) organizations correlated to the Professional, Scientific, and Technical Services.
- 16 (11%) organizations correlated to the Information sector.
- The Health Care sector had 15 (10%) organizations.
- 13 industries, from Real Estate to Arts, Entertainment, and Media to Agriculture, Forestry, Fishing, and Hunting, had 9 organizations or fewer each.
Cybercriminals’ preference for targeting the manufacturing sector with ransomware attacks is due to several perceptions:
- High Operational Impact: Disruptions to continuous production lines and just-in-time inventory systems can lead to significant financial losses.
- Sensitive Data: These organizations likely have valuable proprietary information, trade secrets, and extensive supplier and customer data.
- Cybersecurity Gaps: These types of organizations use legacy systems and IoT devices.
These perceptions make the manufacturing sector an attractive target for ransomware attacks with data leakage and are leveraged to extort the victim.
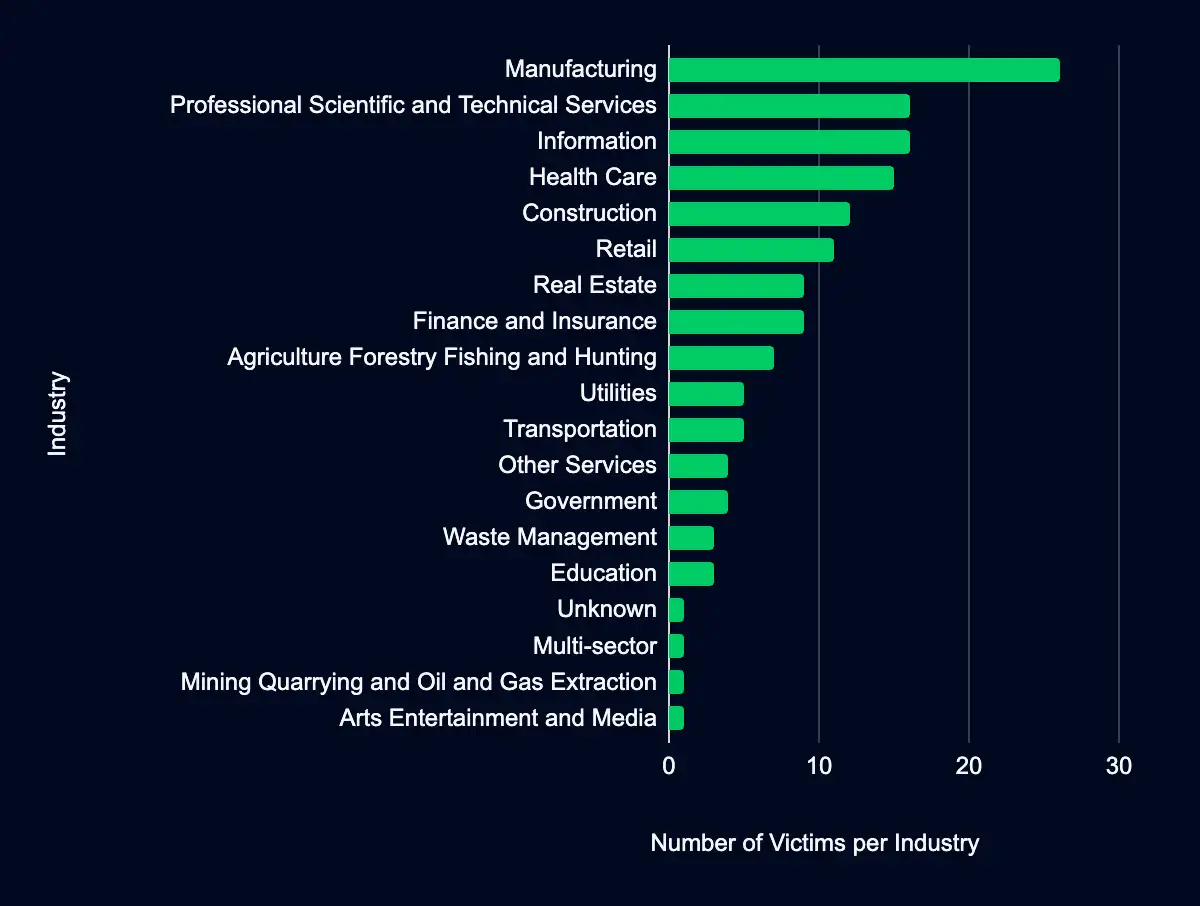
However, as the data shows, all industries are at risk, and a heightened cybersecurity posture and proactive threat intelligence are necessary.
Geographic Analysis
This week’s leak site additions represent 33 countries, with the United States leading with 76 organizations headquartered in this region.
- Canada follows with 11.
- The remaining 31 countries have 62 organizations headquartered in regions such as France, the United Kingdom, Germany, Italy, and the Czech Republic.
The US’s prime target status suggests that ransomware groups target this region because of its many potential targets, dense technological infrastructures, and potentially lucrative ransom payouts.
The continued prominence of the United States in ransomware data leak statistics highlights the critical need for enhanced cybersecurity.
CISA Warns of Active Exploitation of Flaws in Oracle, Check Point, and Linux
Oracle WebLogic Server CVE-2017-3506 – Check Point Quantum Security Gateways CVE-2024-24919 – Linux Kernel CVE-2024-1086
The Rundown
The Cybersecurity and Infrastructure Security Agency (CISA) has flagged three vulnerabilities in Oracle WebLogic Server, Check Point Quantum Security Gateway, and Linux Kernel as actively exploited, escalating concerns over future cyber-attacks.
These vulnerabilities could grant attackers high-level access and control over affected systems if exploited, posing severe organizational security and data integrity risks.
Oracle WebLogic Server CVE-2017-3506
Oracle WebLogic Server is vulnerable to OS command injection, allowing arbitrary code execution via a crafted HTTP request with a malicious XML document.
- Why it matters: This vulnerability can be exploited to deploy ransomware or other malicious payloads, posing significant security risks for organizations using WebLogic Server.
- Exploitation Details: The 8220 Gang has exploited this vulnerability, using advanced obfuscation techniques to deploy cryptocurrency miners through PowerShell scripts, making detection and defense challenging.
- Actions to take: Apply vendor mitigations by June 24, 2024. CISA recommends that organizations discontinue use if vendor mitigations are unavailable by the due date.
Check Point Quantum Security Gateways CVE-2024-24919
An unspecified information disclosure vulnerability allows attackers to access data on internet-connected Gateways with VPN enabled.
- Why it matters: This vulnerability could lead to unauthorized access to sensitive information, potentially allowing lateral movement and domain admin privilege escalation.
- Actions to take: Apply vendor mitigations by June 20, 2024. CISA recommends that organizations discontinue use if vendor mitigations are unavailable by the due date.
- Exploitation Details: The vulnerability is being exploited by attackers using path traversal to access sensitive files. There is also a public proof of concept, heightening the risk of continued exploitation.
Linux Kernel CVE-2024-1086
A use-after-free vulnerability in the netfilter: nf_tables component allows local privilege escalation on affected Linux systems.
- Why it matters: Attackers can escalate privileges from a regular user to root, affecting major Linux distributions like Debian, Fedora, Red Hat, and Ubuntu.
- Actions to take: Apply vendor mitigations by June 20, 2024. CISA recommends that organizations discontinue use if vendor mitigations are unavailable by the due date.
- Exploitation details: While details of exploitation attempts have not been disclosed, a proof of concept has been published, which achieves local privilege escalation by exploiting the flaw on Linux kernel versions between 5.14 and 6.6.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share