Credential Harvesting Spreads via File-Hosting Platforms, Nation-State Hackers Exploit Ivanti Flaws, 113 Firms Leaked with Professional Services Hit Hardest, and CISA Adds Key Vendor Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Credential Harvesting Attacks Spread via File-Hosting Platforms
- Suspected Nation-State Hackers Exploit Ivanti Vulnerabilities to Infiltrate Corporate Network
- Leak Sites: 113 Firms Listed, Professional Services Tops the List
- CISA Adds Ivanti, Fortinet, SolarWinds, Mozilla, and Microsoft Vulnerabilities to Exploited List
Credential Harvesting Attacks Spread via File-Hosting Platforms
The Rundown
Attackers are compromising accounts to access platforms like SharePoint to spread malicious files to external organizations, which direct victims to credential harvesting sites.
This attack method is hard to detect and easy to scale, allowing a single compromised account to endanger multiple organizations. The attackers’ use of trusted services makes traditional defenses less effective, leaving companies vulnerable to financial and reputational harm.
Source Material: Microsoft
Suspected Nation-State Hackers Exploit Ivanti Vulnerabilities to Infiltrate a Corporate Network
The Rundown
A suspected nation-state actor exploited multiple vulnerabilities in Ivanti Cloud Services Appliance (CSA) and exploited a vulnerability in Ivanti Endpoint Manager. This enabled them to gain unauthorized access, execute malicious commands, and exfiltrate sensitive data across compromised networks.
This nation-state-level attack demonstrates the growing threat of vulnerabilities in widely used cloud management systems. By chaining together multiple exploits and even patching the exploited vulnerabilities, attackers could remain undetected while spreading through corporate networks.
The incident highlights the urgent need for rapid patching and enhanced cybersecurity measures, as failure to defend against such sophisticated threats could lead to severe financial and reputational damage.
Source Material: Fortinet
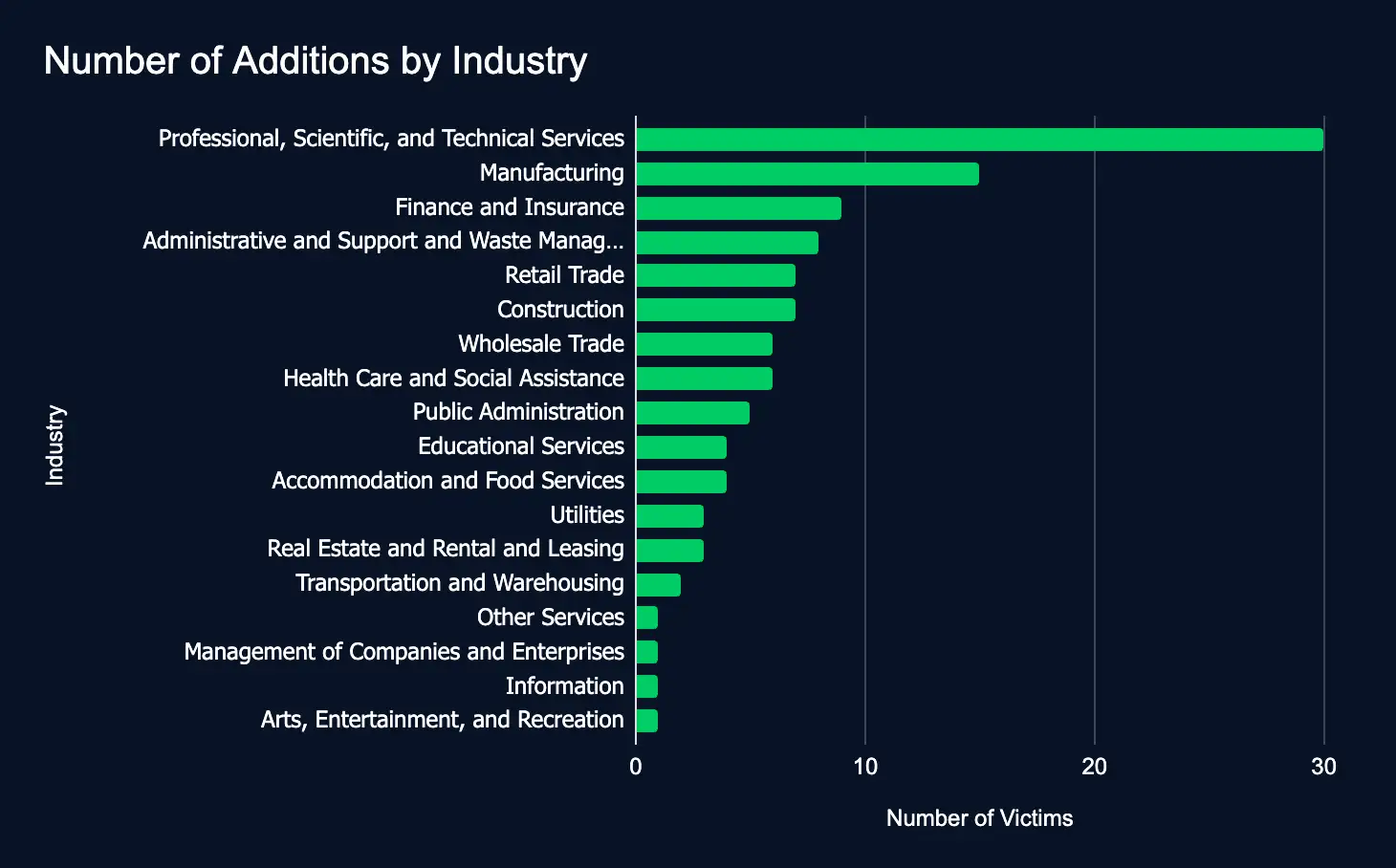
Leak Sites: 113 Firms Listed, Professional Services Tops the List
The Rundown
In just one week, 113 organizations listed across 18 industries were added to ransomware and data leak sites, an increase of 50 organizations from last week. This marks a sharp global escalation in cyber extortion threats.
Critical sectors like manufacturing, professional, finance, and administrative services are increasingly targeted, emphasizing the urgent need for robust cybersecurity measures to protect sensitive data and operations worldwide.
CISA Adds Ivanti, Fortinet, SolarWinds, Mozilla, and Microsoft Vulnerabilities to Exploited List
The Rundown
Six critical vulnerabilities, including those affecting Ivanti, Fortinet, and Microsoft products, were added to CISA’s Known Exploited Vulnerabilities catalog between October 9th and 15th. If not addressed swiftly, these vulnerabilities could expose organizations to potential cyberattacks.
These newly cataloged vulnerabilities highlight looming risks for organizations using widespread technologies. Failure to patch these flaws could lead to privilege escalation, data breaches, or even ransomware attacks. If state-sponsored and cybercriminal attackers focus on these weaknesses, timely action will be crucial to prevent exploitation.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share