Darkgate Malware Hits Skype and Teams, ToddyCat APT Creates Backdoors, Ether-Hiding Technique Moves Malware to Blockchain, and Ransomware Data Leak Sites Continue to Add Victims
This week: a new phishing campaign exploits WinRAR vulnerability, ToddCat APT employes new loaders to deploy Ninja, ClearFake campaign shifts to Binance Smart Chain to host malware on a blockchain, and thousands of Cisco IOS XE devices lay vulnerable–all of this plus the latest from data leak sites, and 2 new CVEs. Oh, and CISA will now include ransomware relationship details in CVEs, when discovered.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Cluster125: CVE-2023-38831 Exploited by Pro-Russia Hacking Groups in RU-UA Conflict Zone for Credential Harvesting
- Securelist/Kaspersky: ToddyCat: Keep calm and check logs
- Guardio Labs: “EtherHiding” — Hiding Web2 Malicious Code in Web3 Smart Contracts
- TrendMicro: DarkGate Opens Organizations for Attack via Skype, Teams
- CISCO Talos: Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerability
- The Latest Additions from Data Leak Sites
- CISA Adds 2 CVEs to KEV Catalog, Adds Known Ransomware Use
Phishing Campaign Exploited WinRAR Vulnerability, Created a Reverse Shell, and Harvested Browser Credentials
WinRAR CVE-2023-38831 – Phishing – Browser Credential Theft – Reverse Shell – Industries/All
Overview & Background
A blog post from Cluster25 titled “CVE-2023-38831 Exploited by Pro-Russia Hacking Groups in RU-UA Conflict Zone for Credential Harvesting Operations” details the exploitation of the WinRAR vulnerability CVE-2023-38831 by a suspected Russia-nexus, nation-state threat actor. The blog post aims to highlight phishing-based attacks that leverage malicious archive files, explicitly targeting WinRAR. The blog post analyzes the tactics, techniques, and procedures (TTPs) employed by the threat actor, the nature of the malicious files, and the subsequent actions taken upon successful exploitation.
CVE-2023-38831 is a vulnerability that affects RARLabs WinRAR versions prior to 6.23. It allows for arbitrary code execution when a user attempts to view a benign file within an archive file. The issue occurs because an archive may include a benign file (such as a PDF or JPG file) and a folder with the same name as the benign file. While accessing the benign file, the folder’s contents, which may include executable content, are processed. CISA added the vulnerability to the Known Exploited Vulnerabilities catalog on 24 September 2023. The current Common Vulnerability Scoring System (CVSS) score for CVE-2023-38831 is 7.8.
Threat Analysis
The phishing attack employed a RAR file (IOC_09_11.rar) that contained a PDF (IOC_09_11.pdf) listing Indicators of Compromise (IoCs) associated with various malware strains and a folder with the same name but had a trailing space character. The folder had a BAT script (IOC_09_11.pdf .cmd) triggered when a user clicked the PDF file. When the BAT script is triggered, it executes three PowerShell commands.
The first command writes a Private RSA Key in the rsakey file in the %LOCALAPPDATA%\Temp directory. The second command uses the RSA key to establish a reverse shell, allowing the threat actor access to the compromised machine via the SSH tool on TCP port 443 at the IP address 216.66.35[.]145. The third command exfiltrates login credentials from Google Chrome and Microsoft Edge using the legitimate web service webhook[.]site (http://webhook[.]site/e2831741-d8c8-4971-9464-e52d34f9d611).
There are two possibilities for threat actor intentions: intelligence collection or financial gain. The threat actors’ objectives support both choices: execute commands via vulnerability exploitation, gain unauthorized access, and maintain persistence by establishing a reverse shell and exfiltrating browser credentials. Their capabilities encompass fundamental technical knowledge and skill in crafting malicious RAR files, proficiency in network intrusion through establishing reverse shells using SSH tools, and adeptness in data exfiltration using the legitimate web service webhook[.]site. Given the intricacies of the attack chain and the tools employed, Cluster25 postulates with low-to-moderate confidence that the threat actor behind these attacks is the Russian state-sponsored group APT28 (Fancy Bear or Sednit).
Risk & Impact Assessment
The most immediate and evident risk stems from the loss of confidentiality due to the direct exfiltration of credentials stored in the browser. However, given the capabilities of the threat actor to establish a reverse shell, there is also a remote probability of the loss of integrity and availability. The ability to execute commands and potentially modify or disrupt systems means that all three pillars of information security (confidentiality, integrity, and availability) are at risk from this phishing attack. The successful exfiltration of browser credentials can have a cascading effect on an organization, touching on various facets, from direct financial losses to long-term strategic impacts. The breadth and depth of these impacts underscore the critical importance of safeguarding credentials and other sensitive data.
ToddyCat APT Employs New Loaders To Deploy Ninja Trojan for Intelligence Collection
ToddyCat – Exchange Server Exploitation – Ninja Trojan – LoFiSe – Cobalt Strike – Industries/All
Overview & Background
A blog post from Kaspersky via Securelist titled “ToddyCat: Keep calm and check logs” provides an in-depth analysis of ToddyCat, an Advanced Persistent Threat (APT) actor. The blog post’s primary objective is to shed light on ToddyCat’s new toolset, their malware to steal and exfiltrate data, and their lateral movement and espionage operations techniques. The analysis is based on a comprehensive examination of the malware, its infrastructure, and the tactics, techniques, and procedures (TTPs) employed by this threat actor.
ToddyCat is a relatively new APT actor that emerged in the cyber threat landscape around December 2020. This group has been responsible for several attacks against high-profile entities in Europe and Asia. Notably, ToddyCat’s operations are characterized by using the ‘Samurai backdoor’ and the ‘Ninja Trojan.’ In December 2020, the group initiated its activities by compromising selected Exchange servers in Taiwan and Vietnam. Over time, their operations escalated, exploiting vulnerabilities like ProxyLogon to target multiple organizations across Europe and Asia. The group’s modus operandi involves a multi-stage infection chain, with the initial compromise often leading to the deployment of the Samurai backdoor. This backdoor, in turn, can be used to deploy the Ninja Trojan, a sophisticated tool designed for deep network penetration and control. Since its inception, ToddyCat has shown a consistent pattern of activity, with a particular focus on targets in Asia.
Threat Analysis
ToddyCat’s evolving arsenal showcases a blend of tools and techniques designed for stealth, persistence, and data exfiltration. A significant revelation is their new loaders, 64-bit libraries invoked by rundll32.exe or side-loaded with the VLC executable. These loaders (Variant “Update” A and Variant “VLC” A & B) are pivotal during infection, primarily to load the Ninja Trojan. Their operation involves fetching an encrypted payload from a file in the same directory, decoding it using XOR, and executing the decrypted payload. Notably, the VLC B variant employs a unique method, creating a new wusa.exe process and injecting the decrypted payload into its address space.
In certain scenarios, ToddyCat deploys a tailored loader, distinct from the standard ones. This loader’s encrypted file is specifically designed for the target system, leveraging system-specific attributes like the drive model and the “C:\” Volume GUID for decryption. The tailored approach suggests a strategy for long-term persistence on high-value targets. This persistence is further cemented by manipulating registry keys with a value of FontCacheSvc to force the legitimate svchost.exe process to load the service during system startup.
Their post-exploitation activities are methodical, involving discovery activities to enumerate domain accounts and servers, lateral movement using compromised credentials, and data collection scripts focusing on recently modified documents. The collected data is then systematically archived and exfiltrated, showcasing ToddyCat’s meticulous approach to cyber espionage.
ToddyCat uses a passive UDP backdoor to receive commands via UDP packets. This backdoor, combined with CobaltStrike before deploying the Ninja agent, underscores the group’s adaptability and preference for layered operations.
The threat actor usually collects files from various hosts, stores them in archives, and then exfiltrates them from the targeted network using public file storage services, like the DropBox uploader and Pcexter, leveraging popular cloud storage services like Dropbox and Microsoft OneDrive. One tool employed to facilitate data theft is LoFiSe. This tool identifies and collects files of interest, monitors system drives, filters out files based on size and location, and focuses on specific file extensions like .doc, .pdf, and .xlsx. Once identified, the tool archives these files for exfiltration.
The group has also used other scripts to enumerate the files on the targeted host’s disks using WMI and collect recently modified documents having .pdf, .doc, .docx, .xls, and .xlsx extensions. File compression is performed using tools such as 7zip or the RAR utility, likely chosen based on what is already available within the infrastructure, directly on the target host or exfiltration host. Unlike LoFiSe, the collection scripts store the paths of the enumerated documents in a plain text TXT file in the tmp_ folder, or a name parameterized according to the hostname.
The Ninja agent, a core component of ToddyCat’s operations, offers functionalities ranging from process management and file system control to managing multiple reverse shell sessions. Its recent iteration has seen configuration modifications, particularly in how it obfuscates its embedded config.
The group’s intentions are likely centered on intelligence collection, targeting high-profile entities across Europe and Asia to extract sensitive information, trade secrets, and potentially government secrets for political, economic, or strategic leverage. Their objectives are evident in their meticulous operations, from initial access via exploiting vulnerabilities in Exchange servers to deploying tailored loaders for specific targets, ensuring long-term persistence, and systematically exfiltrating valuable data. Underpinning these objectives is a robust set of capabilities, including the development and deployment of sophisticated tools like the Ninja Trojan and Samurai Backdoor, the ability to remain covert by leveraging legitimate processes, and the adaptability to integrate known malicious tools with custom-developed ones, showcasing their technical expertise, resilience, and resourcefulness in cyber operations.
Risk & Impact Assessment
The risks posed by ToddyCat’s operations are multifaceted, potentially compromising the confidentiality, integrity, and availability of an organization’s data and systems. A successful breach leads to unauthorized access to sensitive data and disclosure of proprietary information. The breach could result in significant operational disruptions with a remote probability of modifying or destroying critical systems and data. The material impact of such a breach is profound. Organizations could face severe reputational damage, leading to a loss of trust among customers and stakeholders. Financially, the direct costs of addressing the breach, coupled with potential regulatory fines, lawsuits, and loss of competitive advantage, could significantly impact net sales, revenues, and income. Operational disruptions, loss of critical data, increased regulatory scrutiny and missed business opportunities further compound the challenges, potentially altering an organization’s strategic trajectory and market positioning.
ClearFake Campaign Shifts From Cloudflare to the Binance Smart Chain Platform to Host Malicious Code
ClearFake – Fake Browser Update – Infostealer – Binance Smart Chain – Industries/All
Overview & Background
The blog post from Guardio Labs titled “‘EtherHiding’ — Hiding Web2 Malicious Code in Web3 Smart Contracts” details a novel technique where malicious code is served using Binance’s Smart Chain contracts, marking a significant evolution in the way threat actors exploit decentralized technologies in the “ClearFake” campaign. The blog post aims to shed light on this new technique, which has the potential to surpass the stealth and resilience of standard phishing and malware campaigns. The blog post analyzes the tactics, techniques, and procedures (TTPs) the threat actors employ, leveraging a vast array of hijacked WordPress sites to mislead users into downloading malicious fake “browser updates.”
The ClearFake campaign has been a persistent threat in the cybersecurity landscape. Over the past few months, this campaign has been notorious for its “fake-update” malware delivery strategy. Users visiting compromised WordPress sites are shown a convincing overlay prompting them to update their browser. However, users download infostealer variants such as RedLine, Amadey, or Lumma instead of a legitimate update. Initially, the ClearFake campaign relied on hosting its malicious code on abused Cloudflare Worker hosts. However, after Cloudflare took down these worker hosts, the threat actors behind ClearFake quickly adjusted, pivoting to blockchain’s decentralized, anonymous, and public nature, making their campaign even more resilient and challenging to counteract.
Threat Analysis
First, the threat actors embed concealed JavaScript (JS) code into compromised WordPress sites by exploiting vulnerable plugins or outdated WordPress versions or using stolen site credentials to gain access. This JS code is an initial “bridgehead” injected into article pages. Once embedded, the code retrieves a second-stage payload from a server under the threat actor’s control, executing the rest of the site defacement. This method allows the threat actor to remotely and instantly modify the infection process, displaying any desired message, change tactics, update blocked domains, and switch out detected payloads without re-accessing compromised WordPress sites.
However, once executed, this embedded JS code queries the Binance Smart Chain (BSC) Blockchain, creating a new contract instance initialized with a blockchain address controlled by the threat actors. This contract fetches additional JavaScript code. The BSC, designed primarily for running decentralized apps and smart contracts, offers a unique advantage to these threat actors. Due to the blockchain’s public and unchangeable nature, the malicious code hosted on it becomes virtually untouchable, immune to traditional takedown methods.
This method of hosting the additional code on the blockchain, dubbed “EtherHiding,” provides the threat actors with a free, untracked, and robust way to retrieve their malicious payload without leaving any traces. The methods are read-only and cost-free, designed to simulate contract execution for reading data or testing without real-world impact. As such, it’s not recorded on the blockchain. This method of retrieving the code is both innovative and challenging to counteract.
In essence, the victim visits a compromised site. The embedded code retrieves additional code from the Binance Smart Chain. The smart contract fetches second-stage code from a command and control server, which then evaluates the code and defaces the website with a fake browser update message. When the victim clicks the update browser button, they inadvertently download an infostealer.
The BSC transaction history reveals that another actor-controlled address created the contract on 9 September 2023. This address, created in late June 2022, was loaded with BNB (The Binance Coin) in an amount just enough to create and update the contract. While not payable, these activities incur minor customary fees, ranging between 0.02 to 0.60 USD each.
The malicious smart contract is simple yet effective, primarily using the contract’s storage function, saving input to this storage byte by byte, and returning its value as a string. Data can be written or updated on the chain by interacting with the contract.
Each update to the contract demonstrates the threat actors’ adaptability. While the first update was a test, subsequent updates contained JavaScript code snippets. The code’s complexity increased, with later entries incorporating more JavaScript obfuscation techniques. However, the core activities remained consistent. For instance, one decoded entry from the contract fetched a payload from a domain, which is evaluated and executed on the victim’s browser. This code is similar to what was observed in earlier variants of ClearFake, but the threat actors change the second-stage domain almost daily.
The threat actors exhibit a clear intention of financial gain, as evidenced by their deployment of infostealers like RedLine, Amadey, or Lumma. These infostealers are designed to extract sensitive data, such as session cookies and stored passwords, which are then sold on cybercriminal marketplaces for profit. Their primary objective involves compromising WordPress sites to display fake browser update messages, thereby tricking users into downloading their malicious payloads. This approach showcases their capability to merge traditional web-based attack vectors with advanced blockchain technology, creating a multifaceted threat. Their technical expertise, adaptability, and innovative use of the Binance Smart Chain further highlight their capabilities, making them a formidable threat in the cyber landscape.
Risk & Impact Assessment
The ClearFake campaign presents a multi-dimensional threat to organizations, with the most pronounced risk stemming from the loss of confidentiality due to the deployment of infostealers. Organizations risk unauthorized access if successfully infected, potentially encompassing access to sensitive systems and data. This breach could ultimately lead to direct financial losses stemming from other threat actors, like ransomware operators, purchasing the infostealer logs. The aftermath might see increased costs tied to incident response, potential legal fees, and regulatory penalties, especially in jurisdictions with stringent data protection mandates. Furthermore, the disclosure of proprietary data by these threat actors could erode an organization’s competitive advantage, affecting long-term market standing and profitability.
Threat Actors Leveraged Messaging Platforms to Deliver DarkGate Malware
DarkGate – Phishing – Microsoft Teams – Skype – Industries/All
Overview & Background
The blog post from Trend Micro titled “DarkGate Opens Organizations for Attack via Skype, Teams” details a recent DarkGate campaign conducted from July to September that employed three methods, leveraging Skype and Teams instant messaging platforms, to deliver a loader script to victims. This script subsequently downloads and executes a second-stage AutoIT script payload containing the DarkGate malware code. The blog post highlights the three methods and their potential implications. The analysis presented in the blog post is based on observations of DarkGate attacks, primarily detected in the Americas region. Also, it includes insights from other areas such as Asia, the Middle East, and Africa.
DarkGate, a malware that emerged in late 2017, continues to pose a significant threat in the cyber landscape. Classified as a commodity loader, it has been offered on the Russian language forum eCrime since May 2023. Over the years, initial entry attacks using this malware have seen a noticeable increase. DarkGate boasts various features, from executing discovery commands, self-updating, and implementing remote access software to enabling cryptocurrency mining and stealing browser information. A distinguishing characteristic of DarkGate is its use of the Windows-specific automation and scripting tool AutoIt to deliver and execute its malicious capabilities. While AutoIt is a legitimate tool, its frequent misuse by malware families for defense evasion and obfuscation has been a cause for concern in the cybersecurity community.
Threat Analysis
The first method involved the threat actor accessing a Skype account for a supplier of a target organization, allowing them to hijack a message thread between the two organizations. The threat actor sent the target a message with an attachment with a name following “<filename.pdf> www.skype[.]vbs.” The spacing in the file name is almost certain to mislead some users into believing the file is a PDF document instead of VBS.
The second method involved the threat actor sending the victim an LNK attachment masquerading as a ZIP file through Microsoft Teams. Due to the organization’s Microsoft Teams configuration, the threat actor was allowed to send the message even though it was from an unknown external user.
In the third delivery method, the threat actor sent a ZIP file containing several LNK files masquerading as PDFs from a SharePoint site. A loader VBA script is downloaded and executed when the user clicks on one of the LNK files.
In all three delivery methods, when the target clicked the attachment or file, it created a new folder named “<Random Char >,” then copied curl.exe, naming it as <Random Char>.exe using the same name as the folder created. Then, cmd.exe executed a curl command to retrieve an AutoIt3 executable and an AU3 script (AutoIt Version 3 script file) from an external server hosting the files.
The AU3 file first checks the existence of %Program Files%, and the username is not “SYSTEM.” If not, the script is terminated. If the conditions are met, the file spawns iexplore.exe, GoogleUpdateBroker.exe, and Dell.D3.WinSvc.UILauncher.exe processes, injecting them with shellcode to execute the DarkGate payload in memory. Then, a randomly named LNK file is dropped to the Windows User Startup folder to maintain persistence, enabling automatic execution of the file at every system startup. In addition, it creates a folder on the host within the Program Data directory using a randomly generated seven-character string, saving two files that store log and configuration data using a randomly generated seven-character string.
Post-infection, Trend Micro observed DarkGate being used to drop variants of either DarkGate or Remcos, likely to strengthen the threat actor’s foothold in the infected system.
The threat actor demonstrates a primary intention of financial gain or intelligence collection, as evidenced by the malware’s capabilities for persistent unauthorized access, sensitive data exfiltration, and victim surveillance. These objectives align with potentially monetizing the stolen data or accessing or collecting sensitive information for political, economic, or strategic advantage. Their multi-stage attack chain, abuse of instant messaging platforms, and utilization of legitimate tools for malicious purposes underscore their capabilities. While financial gain and intelligence collection appear to be the primary motivations, there remains a remote possibility of intentions related to sabotage, notoriety, or hacktivism.
Risk & Impact Assessment
The DarkGate malware campaign poses a significant threat to organizations, with the most pronounced risks stemming from potential breaches of confidentiality and disruptions to operations. Organizations could face substantial operational interruptions and the unintended release of sensitive information if successfully infected. These risks could lead to severe reputational harm and considerable financial setbacks. While secondary impacts include strained business partnerships, diminished competitive standing in the market, and potential regulatory and legal repercussions. The cumulative effect of these risks underscores the critical importance of robust cybersecurity measures to counteract such threats.
Threat Actor Exploits Critical Vulnerability in Thousands of Cisco IOS XE Devices, Deploying Implant and Creating User Accounts With Level 15 Access
CISCO IOS XE CVE-2023-20198 – Cisco IOS XE CVE-2021-1435 – Vulnerability Exploitation – Arbitrary Code Execution – Industries/All
Overview & Background
The blog post from Cisco Talos titled “Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerability” details the identification and active exploitation of a previously unknown vulnerability in the Web User Interface (Web UI) feature of Cisco IOS XE software (CVE-2023-20198) when exposed to the internet or untrusted networks and if the HTTP or HTTPS Server features are enabled. The blog post aims to alert and inform entities about this critical vulnerability, its potential impact, and the recommended mitigation measures. The blog post analyzes physical and virtual devices running Cisco IOS XE software with the enabled HTTP or HTTPS Server feature, providing insights into the threat actor’s tactics, techniques, and procedures.
Threat Analysis
Cisco Talos discovered early signs of the exploitation of the vulnerability on 28 September 2023. Further investigations revealed related activities as early as 18 September, which included an authorized user creating a local user account under the username “cisco_tac_admin” from a suspicious IP address. This activity ceased on 1 October, with no other associated behaviors observed other than the suspicious account creation.
However, on 12 October, Cisco Talos Incident Response (Talos IR) and the Technical Assistance Center (TAC) detected another cluster of related activity. In this instance, an unauthorized user was observed creating a local user account under the name “cisco_support” from a different suspicious IP address. Unlike the September case, this October activity involved several subsequent actions, including deploying an implant consisting of a configuration file. This configuration file defines a new web server endpoint to interact with the implant. The endpoint receives specific parameters, allowing the threat actor to execute arbitrary commands at the system or IOS level. For the implant to become active, the web server must be restarted. In some cases, the server was not restarted, rendering the implant inactive despite its installation.
The implant, saved under “/usr/binos/conf/nginx-conf/cisco_service.conf,” contains variable strings of hexadecimal characters. While the implant is not persistent and can be removed with a device reboot, the newly created local user accounts remain active even after system reboots. These accounts possess level 15 privileges, granting them full administrative access to the device, allowing them access to all commands and the ability to make configuration changes.
Cisco Talos assesses that the same threat actor likely orchestrated these clusters of activity. The two clusters appeared in close succession, with the October activity seemingly building upon the September activity. The initial cluster might represent the threat actor’s preliminary attempts and code testing, while the October activity indicates the threat actor’s efforts to establish persistent access via the implant deployment.
Existing detections revealed the threat actor exploited CVE-2021-1435 to install the implant post-access. However, some fully patched devices against CVE-2021-1435 still had the implant successfully installed through an undetermined mechanism.
The implant’s analysis shows it is based on the Lua programming language and facilitates arbitrary command execution. The threat actor must send an HTTP POST request to the device, which delivers specific functions. The first function returns a string of numbers surrounded by forward slashes, which Cisco Talos suspects might represent the implant’s version or installation date. The second function returns an 18-character hexadecimal string hardcoded into the implant. Finally, the third function checks to see if the parameter matches a 40-character hexadecimal string hardcoded into the implant. A second parameter determines whether the code is executed at the system or IOS levels. Commands executed at the IOS level are executed at privilege level 15.
In most instances, the values in the second and third functions were the same across different devices. The similarity in values may act as a form of authentication required for the arbitrary command execution provided in the third function.
To aid in identifying compromised devices, Cisco provided a technique wherein an active implant on an IOS XE device would respond with a distinct 18-character hexadecimal string when a specific HTTP POST request is made to the system. Recently, VulnCheck used this technique and undertook an extensive internet scan, revealing thousands of hosts implanted with malicious software. The implications of such unauthorized access are grave. Threat actors with privileged access to the IOS XE can potentially monitor network traffic, gain entry into safeguarded networks, and orchestrate various man-in-the-middle attacks. In response to this escalating threat, VulnCheck has released a specialized scanner designed to detect the presence of the implant on potentially affected devices.
The threat actor, exhibiting advanced capabilities, has demonstrated a primary intention of intelligence collection, as evidenced by their exploitation of a zero-day vulnerability in Cisco IOS XE software and the deployment of a sophisticated implant. These actions suggest the workings of a well-resourced and skilled entity, possibly indicative of a state-sponsored group or an advanced persistent threat (APT) group. Their objectives encompass unauthorized account creation for full administrative access, persistent access to compromised devices, and the ability to execute arbitrary commands. While intelligence collection stands out as the most probable intention, there remains a lesser likelihood of financial gain motives. Other intentions, such as sabotage or disruption, notoriety, and hacktivism, are considered remote possibilities based on the current evidence.
Risk & Impact Assessment
The exploitation of CVE-2023-20198 presents a multifaceted risk to organizations, with the most pronounced threat being the compromise of data confidentiality. Successful exploitation can lead to operational disruptions, resulting in the loss of business and reduced customer trust. Data breaches arising from unauthorized access can incur regulatory fines, legal repercussions, and substantial reputational damage. Furthermore, the potential for data manipulation or outright loss can introduce inaccuracies in business decisions and necessitate costly recovery efforts. Financial ramifications extend beyond direct losses, encompassing increased operational costs for enhanced cybersecurity measures and potential net sales and revenue declines. In essence, the cascading effects of a successful exploitation can profoundly impact an organization’s operations, financial health, and long-term market standing.
Latest Additions to Data Leak Sites
Professional, Scientific, and Technical Services – Manufacturing – Transportation and Warehousing – Health Care and Social Assistance – Real Estate and Rental and Leasing
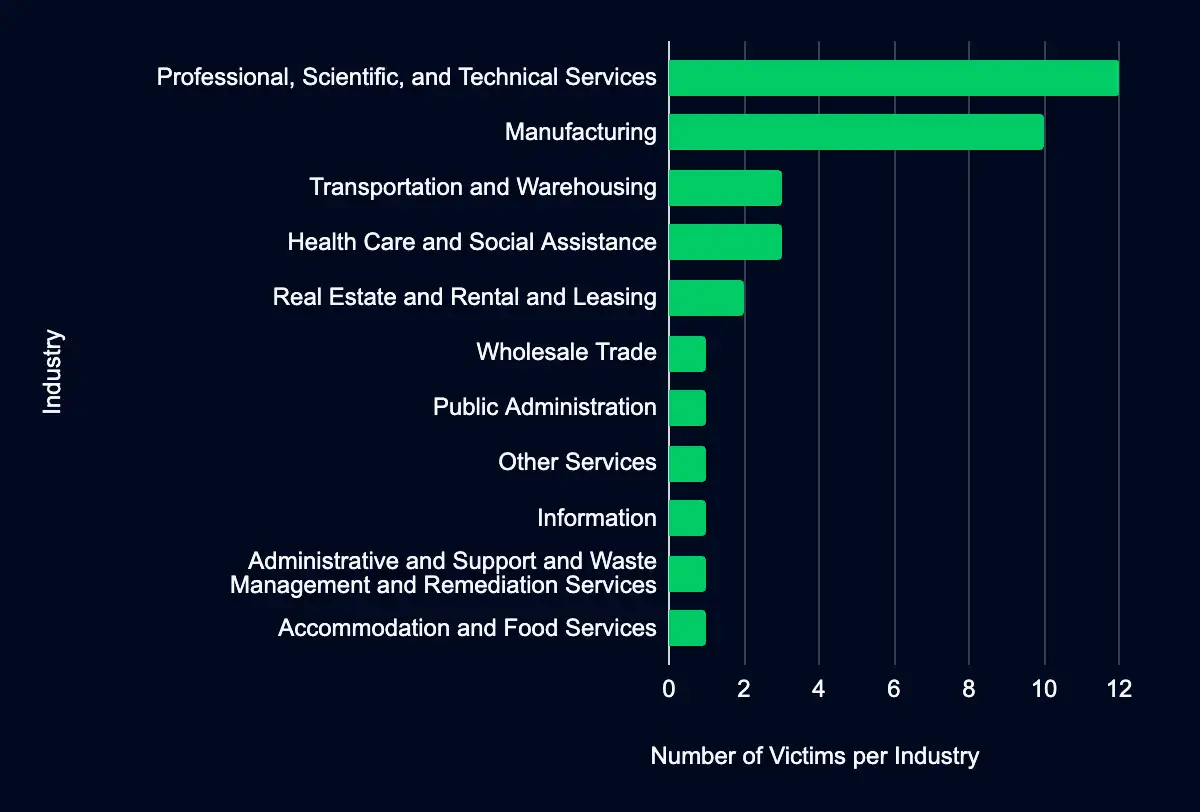
In the past week, monitored data extortion and ransomware threat groups added 36 victims to their leak sites. Of those listed, 18 are based in the USA. Professional, Scientific, and Technical Services was the most affected industry, with 12 victims. Ten victims follow this industry in Manufacturing, three victims in Transportation and Warehousing and Health Care and Social Assistance, and two victims in Real Estate and Rental and Leasing. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 2 CVEs, Begins to Identify Vulnerabilities Linked to Ransomware Campaigns
Cisco IOS XE CVE-2023-20198 – Citrix NetScaler ADC and NetScaler Gateway CVE-2023-4966
Within the past week, CISA added two CVEs to the catalog, affecting Cisco and Citrix products. Threat actors can exploit these vulnerabilities to disclose sensitive information or account creation. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action occur on 20 October 2023 for the Cisco vulnerability and 8 November 2023 for the Citrix vulnerability.
Additionally, on 12 October, CISA announced that the Known Exploited Vulnerabilities (KEV) catalog will have a new column listing whether a vulnerability is known or unknown to have been used in ransomware campaigns. It is currently unknown if the two vulnerabilities added in the past week are linked to any ransomware campaigns.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor and Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|
| CVE-2023-20198 | Cisco IOS XE Web UI | Cisco IOS XE Web UI contains a privilege escalation vulnerability in the web user interface that could allow a remote, unauthenticated attacker to create an account with privilege level 15 access. The attacker can then use that account to gain control of the affected device. | 10/20/23 | Unknown |
| CVE-2023-4966 | Citrix NetScaler ADC and NetScaler Gateway | Citrix NetScaler ADC and NetScaler Gateway contain a buffer overflow vulnerability that allows for sensitive information disclosure when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. | 11/8/23 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share