Peach Sandstorm Evolves, Scattered Spider Diversifies, Bumblebee Loader Resurfaces, and Earth Lusca Employs Linux Backdoor
This week: Iranian nation-state actor Peach Sandstorm evolves tactics in a global intelligence collection; UNC3944 (Scattered Spider) diversifies to include smishing, social engineering, ransomware, and extortion; a new campaign features Bumblebee Loader – more plus the latest from data leak sites and 10 new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Microsoft: Peach Sandstorm password spray campaigns enable intelligence collection at high-value targets
- Mandiant: Why Are You Texting Me? UNC3944 Leverages SMS Phishing Campaigns for SIM Swapping, Ransomware, Extortion, and Notoriety
- Intel 471: Bumblebee Loader Resurfaces in New Campaign
- Trend Micro: Earth Lusca Employs New Linux Backdoor, Uses Cobalt Strike for Lateral Movement
- FBI and CISA: Snatch Ransomware Targeting U.S. Entities
- The Latest Additions from Data Leak Sites
- CISA Adds 10 CVEs to its Known Exploited Vulnerabilities Catalog
Iranian Nation-State Adversary Evolves Tactics in Global Intelligence Collection
Peach Sandstorm – Zoho ManageEngine CVE-2022-47966 – Confluence CVE-2022-26134 – Password Spray – AzureHound – RoadTools – Manufacturing – Professional, Scientific, and Technical Services – Public Administration
Overview & Background
A recent Microsoft Threat Intelligence blog post titled “Peach Sandstorm password spray campaigns enable intelligence collection at high-value targets” details the recent activities of the Iranian nation-state adversary Peach Sandstorm (also tracked as HOLMIUM). In 2023, they demonstrated a sustained interest in organizations within the satellite and defense sectors and, to a lesser extent, the pharmaceutical industry. Their methods evolved to include more stealthy and sophisticated cloud-based tactics. The blog post aims to raise awareness of the recent tradecraft employed by Peach Sandstorm and to empower organizations to strengthen their defenses against this group’s intrusion attempts. The blog post analyzes the group’s tactics, techniques, and procedures (TTPs) based on the data collected from the targeted organizations and the tools utilized in their campaigns, including AzureHound and Roadtools for internal reconnaissance.
Peach Sandstorm has a history of targeting organizations globally, including those in the aviation, construction, defense, education, energy, financial services, healthcare, government, satellite, and telecommunications sectors. The group has been associated with other known entities such as APT33, Elfin, and Refined Kitten, indicating a complex web of affiliations and overlapping activities in the cyber threat landscape. Their activities have been observed since at least 2019, with a notable wave of attacks correlating with heightened tensions between the United States and Iran. The group is known for its password spray campaigns, which use common passwords to attempt authentication across numerous accounts, maximizing the chances of gaining unauthorized access while avoiding automatic lockouts.
Threat Analysis
Peach Sandstorm’s latest campaign utilized two primary intrusion chain paths to compromise organizations. The first intrusion chain path involves a series of password spray attacks, where the adversary attempts to authenticate to numerous environments using common passwords. Following successful authentication, they engaged in internal reconnaissance in a small subset of instances using tools like AzureHound or Roadtools to gather information on the targeted systems through Microsoft Entra ID (formerly Azure Active Directory) and Azure Resource Manager. The adversary ensured persistence through various mechanisms, including creating new Azure subscriptions on the target’s tenant and abusing Azure Arc to control devices in the compromised environment from their cloud. Additionally, Peach Sandstorm consistently conducted password spray campaigns initiated from TOR IPs and used a “go-http-client” user agent.
The second intrusion chain path is characterized by the remote exploitation of internet-facing applications vulnerable to publicly available proof-of-concept (POC) exploits, specifically targeting Zoho ManageEngine and Confluence products. The adversary leveraged known vulnerabilities such as CVE-2022-47966, a remote code execution vulnerability affecting a subset of on-premises Zoho ManageEngine products, and CVE-2022-26134, a remote code execution vulnerability in Confluence Server and Data Center, to gain initial access to the target environments.
Post-compromise, Peach Sandstorm deployed AnyDesk, a commercial remote monitoring and management tool, for persistence and command and control (C2) operations in a subset of intrusions. In one instance, in a March 2023 intrusion, they conducted a Golden SAML attack to access cloud resources, bypassing AD FS authentication by stealing private keys from a target’s on-premises Active Directory Federated Services (AD FS) server and using the stolen keys to mint a SAML token trusted by a target’s Microsoft 365 environment. The adversary also utilized a VMWare executable for DLL search order hijacking in at least one intrusion and, in multiple cases, leveraged a custom tool named EagleRelay to tunnel traffic between there and the targets’ systems.
Activity observed in this campaign aligned with an Iranian pattern of life, particularly in late May and June, where activity occurred almost exclusively between 9:00 AM and 5:00 PM Iran Standard Time (2:00 AM to 10:00 AM Eastern Standard Time), primarily from Sunday to Wednesday.
Peach Sandstorm primarily intends to facilitate intelligence collection to support Iranian state interests, leveraging their campaigns to gather sensitive data from high-value targets globally. Their objectives are multi-faceted, aiming to gain unauthorized access to systems, exfiltrate sensitive data, and potentially disrupt or destroy the data and systems of the targeted organizations. The adversary showcases extensive capabilities, employing a blend of publicly available and custom tools to achieve their objectives. Their operations are characterized by stealth and sophistication, with a notable enhancement in their cloud-based tactics compared to previous campaigns. Using legitimate credentials harvested from password spray attacks to authenticate to targets’ systems and deploying various tools for further malicious activity highlight their advanced skill set and resources.
Risk & Impact Assessment
Given the sophisticated nature of Peach Sandstorm’s operations, the risk and impact to organizations, particularly in the satellite, defense, and pharmaceutical sectors, is substantial. The group has demonstrated a high likelihood of continued activity targeting these sectors, leveraging a blend of publicly available and custom tools to facilitate intelligence collection supporting Iranian state interests. There is a significant risk to the confidentiality of an organization’s assets and systems, as Peach Sandstorm has been observed harvesting and exfiltrating data from compromised environments, using legitimate credentials harvested from password spray attacks to authenticate to and maintain persistence in targets, and deploying a range of tools for further malicious activity.
UNC3944 (Scattered Spider) Diversifies TTPs to include SMS Phishing, Calling Help Desk Employees, Ransomware, and Extortion
UNC3944 – Smishing – Vishing – Ransomware – Data Exfiltration – Information – Accommodation and Food Services – Finance and Insurance – Retail Trade
Overview & Background
A blog post from Mandiant titled “Why Are You Texting Me? UNC3944 Leverages SMS Phishing Campaigns for SIM Swapping, Ransomware, Extortion, and Notoriety” details the evolving threat landscape orchestrated by the financially motivated threat cluster, UNC3944. The blog post aims to shed light on the group’s recent shift in strategies, from primarily focusing on SIM-swapping attacks to incorporating ransomware deployments and extortion in their operations. The blog post analyzes the group’s tactics, techniques, and procedures (TTPs), emphasizing their activities in 2023, and leverages a rich dataset derived from various intrusions orchestrated by UNC3944, providing a deep dive into their modus operandi, including their phishing campaigns and exploitation of cloud resources.
UNC3944 has been a threat cluster active since at least 2022, leveraging phone-based social engineering and SMS phishing campaigns, commonly called smishing, to escalate access to victim organizations. The group operates partly in cybercriminal communities on Telegram and underground forums, utilizing them to acquire tools, services, and support to augment their operations. UNC3944 TTPs overlap with those reported under the names “0ktapus,” “Scatter Swine,” and “Scattered Spider.” Initially focusing on enabling SIM swapping attacks to support secondary criminal operations, the group has broadened its horizons in mid-2023 to include ransomware deployments in victim environments, signaling a diversification in their monetization strategies. This shift has seen them expand their target industries beyond telecommunications and business process outsourcing companies, including hospitality, retail, media and entertainment, and financial services. Their deep understanding of Western business practices and reliance on publicly available tools and malware purchased from underground forums have been notable characteristics of their operations.
Threat Analysis
UNC3944 exhibits a range of notable TTPs that underscore their sophisticated approach to conducting operations. A significant part of their strategy is stealing valid credentials to gain unauthorized access to targeted organizations. They employ a multi-faceted approach, leveraging phone-based social engineering (vishing) and SMS phishing (smishing) techniques. However, UNC3944 doesn’t rely exclusively on smishing and social engineering to obtain valid credentials. They have been observed using publicly available credential theft tools and expending significant effort searching through internal systems to identify privileged credentials.
After obtaining credentials, UNC3944 operatives have been known to place calls directly to victim organizations, often impersonating the employee to have help desk employees reset the account’s multifactor authentication (MFA) code and/or password. During these calls, UNC3944 provided verification information requested by the help desk employees, often asking to repeat questions and pausing for significant lengths before answering, likely due to the threat actor searching for the answer to the question posed by looking through notes or other sources. In one incident, they obtained account credentials that may have been exposed on a laptop used by an IT outsourcing company contracted by the victim organization. This laptop was infected only a few weeks prior with RECORDSTEALER credential theft malware delivered through a fake software download.
The group utilizes sophisticated phishing pages designed to harvest credentials from unsuspecting victims. These pages are meticulously crafted to appear as belonging to the targeted organization and frequently use single sign-on (SSO) or service desk lures. Registered domains typically include the victim organization name and “-sso” or “-servicenow” in the domain name. In some cases, these domain names appeared to have the names of internal systems. Based on this, it’s plausible that UNC3944 leveraged access to victim environments to develop tailored target-specific phishing campaigns.
UNC3944 uses three phishing kits, EIGHTBAIT and two unnamed kits, similar in visual and structural aspects. EIGHTBAIT sends captured credentials to an actor-controlled Telegram channel. Additionally, it can deploy AnyDesk to a victim’s system, indicating it was developed to target non-mobile systems and not expressly designed for smishing campaigns. UNC3944 used EIGHTBAIT between late 2021 and mid-2022. The first unnamed kit was observed in Q3 2022 and appears to have been built using a webpage copied from a targeted organization and a generic authentication theme. Notably, UNC3944 used this kit in recent extortion intrusion attempts. The second unnamed kit, first observed in mid-2023, has been used in parallel with the first unnamed phishing kit. Despite the similarities between the two kits, minor changes to the kit’s code suggest that the theme used by the first unnamed kit was retrofitted into a new tool.
UNC3944 has demonstrated creative, persistent, and increasingly effective methods to target and compromise cloud resources. They have been observed creating unmanaged virtual machines within victims’ cloud environments, using them as launchpads for further attacks. Their strategy facilitates deeper penetration into victim networks and allows them to evade detection, as security teams often overlook these virtual machines. Their operations, characterized by a high operational tempo, involve accessing critical systems and exfiltrating large volumes of data within a short timeframe, often overwhelming security response teams. The group maintains a low profile by leveraging commercial, residential proxy services, which enable them to access victim networks from geographically plausible locations, further aiding in their evasion tactics.
UNC3944 operates with clear financial motivations through various means, including extortion via data exfiltration and disclosure and ransomware deployment. Their objectives have expanded, initially focusing on SIM swapping attacks and later diversifying to target various industries, including hospitality and financial services, aiming to exfiltrate sensitive data and disrupt business operations. The group showcases high capabilities, leveraging a deep understanding of Western business practices and utilizing a range of tools, both publicly available and acquired from underground forums, to facilitate their operations. Their knowledge and resources enable them to adapt and respond to the changing landscape, indicating a high level of sophistication and posing a significant threat to organizations globally.
Risk & Impact Assessment
UNC3944’s operations pose a substantial risk to organizations globally, notably in the telecommunications, hospitality, and financial services sectors. Leveraging diverse tactics, techniques, and procedures, including social engineering, credential theft tools, and phishing kits, threatens data and information systems’ confidentiality, integrity, and availability. Their adeptness at impersonating employees and bypassing multifactor authentication mechanisms amplifies the risk, potentially granting them unauthorized access to critical systems and the ability to disclose sensitive information. The impact of their activities is profound and far-reaching, characterized by swift network penetrations and extensive data exfiltration. UNC3944’s aggressive tactics, such as deploying ransomware and engaging in extortion, can disrupt organizational operations significantly, potentially leading to the loss or destruction of vital data and systems. Their focus on targeting cloud resources, coupled with a deep understanding of Western business practices and a knack for acquiring tools from underground forums, showcases their high level of sophistication. This activity suggests that their operations can have severe, long-lasting repercussions on organizations, including substantial financial losses and reputational damage.
Bumblebee Loader Resurfaces in New Campaign, Evolves Techniques to Compromise Networks
Bumblebee Loader – WebDAV – Phishing – LNK & ZIP Files – Industries/All
Overview & Background
A new blog post from Intel 471 titled “Bumblebee Loader Resurfaces in New Campaign,” provides an in-depth analysis of the recent activities of the Bumblebee Loader, a malware utilized as a loader to install other malware payloads and establish a foothold into an organization’s network. The blog post aims to offer a detailed account of the new techniques adopted by threat actors in distributing the malware and the updates made to enhance its capabilities. The analysis is based on the data derived from Intel 471 Malware Intelligence systems, which have tracked the malware’s resurgence, focusing on its deployment strategies involving Web Distributed Authoring and Versioning (WebDAV) servers and the utilization of spam emails to disseminate malicious payloads.
Bumblebee Loader first surfaced in September 2021 and witnessed a surge in its usage in late March 2022, following the shift of threat actors from using the BazarLoader to Bumblebee. The malware, used by initial access brokers who sell access to victims, has been linked to several high-profile ransomware groups, including the now-defunct Conti and Akira. Bumblebee facilitates initial breaches in high-value enterprise environments, providing a loader for payloads from tools like Cobalt Strike, Metasploit, and Sliver.
Threat Analysis
In the latest campaign orchestrated by the operators of Bumblebee Loader, a series of sophisticated techniques have been employed to distribute the malware and secure initial footholds in high-value enterprise environments. The campaign leverages Web Distributed Authoring and Versioning (WebDAV) servers, explicitly utilizing the services of 4shared, a file-hosting service that allows managing and editing files on remote servers. The threat actors distributed Bumblebee payloads through malicious spam emails containing Windows shortcut (.LNK) and compressed archive (.ZIP) files that house .LNK files. These files, when launched, execute a series of commands to download the Bumblebee malware hosted on WebDAV servers. The first command mounts a network drive to a WebDAV folder.
The malware itself has seen significant updates, transitioning from using the WebSocket protocol to a custom Transmission Control Protocol (TCP) for its communication mechanisms. A notable introduction is the Domain Generation Algorithm (DGA), which generates new command and control (C2) servers, eliminating the hard-coded C2 servers and adding a layer of complexity that makes the malware more resilient and challenging to disrupt. The DGA operated with a 64-bit static seed value, generated 100 new domains with a “.life” top-level domain (TLD), and iterated until it resolved a DGA domain to an IP address and successfully checked in.
The threat actors’ intentions behind this operation appear multifaceted, encompassing financial gains through the initial access market selling to ransomware affiliates and cybercriminals. The objective is to target high-value enterprise environments, utilizing the malware as a loader for various payloads, facilitating initial breaches, and establishing a foothold in the organizations’ networks. The capabilities demonstrated in this campaign underline a high degree of sophistication and resourcefulness. The threat actors have shown adeptness in leveraging advanced evasion techniques, exploiting legitimate services, and innovating distribution methods to bypass behavioral detection systems. Using varied command sequences and execution methods indicates a calculated approach to determining the most effective tactics for evasion, showcasing a deep understanding of cybersecurity environments and a readiness to adapt to emerging threats.
Risk & Impact Assessment
Using Bumblebee Loader in cyber-attacks presents significant global risks and consequences for corporate networks. Firstly, Bumblebee Loader allows unauthorized access, which puts the confidentiality of corporate data at risk. Attackers can compromise sensitive information like personal details and proprietary data, leading to a loss of trust and possible legal action. Secondly, the malware enables the introduction of secondary payloads, creating a range of threats that can compromise the integrity and availability of corporate environments, including remote access, lateral movement across networks, data theft or encryption, resource exploitation for cryptomining, and incorporating devices into botnets, presenting a multifaceted threat landscape. Lastly, using Bumblebee Loader in ransomware attacks could lead to essential systems and data unavailability, resulting in operational disruptions, financial losses, and forcing organizations to consider ransom payments to regain access.
Cyber Espionage Group Intensifies Activities, Uses New Linux Backdoor, and Cobalt Strike
Earth Lusca – SprySOCKS – Cobalt Strike – Vulnerability Exploitation – Linux
Overview & Background
A blog post from Trend Micro titled “Earth Lusca Employs New Linux Backdoor, Uses Cobalt Strike for Lateral Movement” details the recent activities and tactics of the Earth Lusca threat group, emphasizing their deployment of a new Linux backdoor and the utilization of Cobalt Strike for lateral movements within compromised networks. The blog post aims to shed light on the sophisticated techniques employed by Earth Lusca, offering a deep dive into the functionalities and characteristics of the newly discovered Linux backdoor, dubbed SprySOCKS, and the group’s lateral movement strategies. The blog post analyzes the intricate details of the SprySOCKS backdoor, including its architecture, command and control protocols, and the various commands it can execute, leveraging information obtained through meticulous analysis of encrypted files found on the threat actor’s server.
Earth Lusca is a threat actor that has been active since at least 2021. It is suspected to be a China-based cyber espionage group. Earth Lusca has targeted various organizations, including government institutions, news media outlets, gambling companies, educational institutions, COVID-19 research organizations, telecommunications companies, religious movements banned in China, and cryptocurrency trading platforms. The group has been observed operating in multiple countries, including Australia, China, Hong Kong, Mongolia, Nepal, the Philippines, Taiwan, Thailand, Vietnam, the United Arab Emirates, Nigeria, Germany, France, and the United States. Earth Lusca’s tools and techniques are similar to other Chinese threat groups, such as APT41 and the Winnti Group, but they operate separately. The group has been known to use malware that other Chinese threat groups commonly use. In addition to cyber espionage activities, Earth Lusca has also been involved in financially motivated attacks, targeting cryptocurrency payment platforms and exchanges.
Threat Analysis
In the first half of 2023, Earth Lusca escalated its cyber-espionage activities, primarily targeting countries in Southeast Asia, Central Asia, and the Balkans, with sporadic attacks in Latin American and African nations. The group has aggressively targeted public-facing servers of government departments involved in foreign affairs, technology, and telecommunications. They exploit server vulnerabilities, including a series of noted CVEs (listed here), to infiltrate networks, following which they deploy web shells and install Cobalt Strike for lateral movement. Their modus operandi includes exfiltrating documents and email account credentials and further deploying advanced backdoors like ShadowPad and the Linux version of Winnti for long-term espionage activities.
The attack’s initial phase involves deploying a loader component named “mandibule.” Based on a publicly available Linux ELF injector, this loader is responsible for decrypting and executing the primary payload, SprySOCKS, which is encrypted using an AES-ECB cipher with a hardcoded password. The loader sets persistence by copying itself and the encrypted second stage to the /usr/sbin/ directory and initiating itself as a service using chkconfig or systemd. It disguises its process name as “kworker/0:22” to avoid suspicion during system process monitoring.
The SprySOCKS component, derived from the open-source Windows backdoor Trochilus, is a Linux-targeted backdoor with functionalities re-implemented for Linux systems. It uses a command-and-control (C&C) protocol that the RedLeaves backdoor uses. The backdoor facilitates various commands, including system information collection, initiating interactive shells, listing network connections, and creating SOCKS proxies. It communicates with the C&C server using TCP, sending packets that contain base64-encoded, AES-ECB-encrypted messages. The SprySOCKS backdoor is likely still being developed, as indicated by different version numbers in various payloads.
The Earth Lusca group operates with the primary intention of intelligence collection, aiming to gather sensitive information for political, economic, or strategic advantages. Their objectives are clear: to gain unauthorized access to government systems, exfiltrate sensitive data, and maintain a network presence for ongoing espionage activities. The group showcases high capabilities, leveraging various tools and techniques, including developing new malware variants and exploiting several vulnerabilities to achieve their objectives. Their knowledge and skills in cyber espionage are evident from the meticulous planning and execution of their operations, which involve multi-faceted threats with several components working in tandem to infiltrate and compromise targeted networks.
Risk & Impact Assessment
The Earth Lusca group’s escalated activities in the first half of 2023 pose a pronounced risk to governmental organizations globally, particularly in Southeast Asia, Central Asia, and the Balkans. The group leverages sophisticated malware components and exploits known vulnerabilities to compromise the confidentiality, integrity, and availability of sensitive data and critical information systems. Their tactics include the exfiltration of sensitive documents and email credentials, potentially leading to unauthorized disclosure of personal and proprietary information. Data integrity is under threat, with the group capable of initiating improper information modification or destruction, thereby threatening the non-repudiation and authenticity of the information. Moreover, their aggressive tactics jeopardize the availability of information systems, disrupting operations and potentially leading to unreliable access to vital information. The group’s operations signify a material threat to targeted organizations and their assets, with repercussions including unauthorized system access, sensitive data exfiltration, data modification, and disruption of normal operations, posing a substantial threat to the organization’s mission and functions.
Snatch Affiliates TTPs
Snatch Ransomware – RDP – Purchase Access – Cobalt Strike – Industries/All
Overview & Background
A joint Cybersecurity Advisory from the FBI and CISA titled “Snatch Ransomware Targeting U.S. Entities” details the tactics, techniques, and procedures (TTPs) the Snatch ransomware group employs. The advisory aims to equip stakeholders with the necessary information to defend against the sophisticated strategies deployed by this threat actor. Drawing from data accumulated through FBI investigations from September 2022 to June 2023, the advisory analyzes the various indicators of compromise (IoCs) associated with Snatch. It further analyzes the MITRE ATT&CK tactics and techniques leveraged by the group, providing a detailed breakdown across several tables for a granular understanding. Moreover, it outlines potential mitigations, offering actionable insights and recommendations to enhance cybersecurity posture and thwart possible attacks orchestrated by Snatch.
The Snatch ransomware group, active since 2018, operates a ransomware-as-a-service (RaaS) model and has been notorious for its aggressive cyber-attacks targeting various entities globally. Leveraging many tactics, including brute force attacks to compromise credentials and exploiting vulnerabilities in Remote Desktop Protocol (RDP), the group has exhibited a high level of technical acumen in orchestrating sophisticated cyberattacks. A cornerstone in their modus operandi is the utilization of malicious and legitimate email domains to spearhead phishing attacks. Snatch threat actors communicate with their victims through email and the Tox communication platform, a peer-to-peer instant messaging and video-calling protocol that ensures secure communication.
Threat Analysis
Since its inception in 2018, the Snatch ransomware group has operated under a ransomware-as-a-service (RaaS) model, which involves a collaborative effort between the group and its affiliates. Snatch provides the ransomware and leak site, while the affiliates are responsible for orchestrating the attacks, each employing various tactics, techniques, and procedures (TTPs) as they see fit. This collaborative approach aims to achieve financial gains through extortion, leveraging unauthorized access to systems and data to exfiltrate sensitive information from targeted entities. The victims are then pressured to meet ransom demands to regain access to their critical data and systems and to prevent the leaking of sensitive data.
Snatch affiliates showcase a high level of technical skill, utilizing a range of TTPs, albeit not uniformly across all attacks. During reconnaissance, they may gather information on the victim’s network to facilitate targeted attacks. The resource development stage may involve acquiring infrastructure, such as Virtual Private Servers, to support operations. To gain initial access, affiliates primarily exploit the Remote Desktop Protocol (RDP) vulnerabilities to gain administrator credentials. However, they have been observed using valid accounts from criminal forums and marketplaces.
To maintain persistence, affiliates employ various credential access approaches, such as brute force password guessing. They may use various discovery techniques, including querying the registry and process discovery, to gather information about the system and configuration. Lateral movement in the network is facilitated potentially through the Remote Desktop Protocol. Before deploying the Snatch ransomware to encrypt data, affiliates spent up to three months on a victim’s system, moving laterally using RDP and collecting data from files and folders.
During the early stages of ransomware deployment, affiliates attempt to disable antivirus software and run an executable. Upon initiation, the Snatch ransomware payload queries and modifies registry keys, uses various native Windows tools to enumerate the system, finds processes, and creates benign processes to execute Windows batch files. Sometimes, the program attempts to remove all the volume shadow copies from a system. After the execution of the batch files, the executable removes the batch files from the victim’s filesystem.
It is important to note that while these TTPs are associated with Snatch ransomware attacks, they may not be exclusive to them and can be observed in other ransomware incidents, given the affiliates’ autonomy to choose from a range of ransomware families for their operations.
Risk & Impact Assessment
All organizations face a substantial risk of falling victim to ransomware attacks orchestrated by affiliates of Snatch, a threat exacerbated by the ransomware-as-a-service (RaaS) model, which diversifies the tactics, techniques, and procedures used by threat actors. The potential loss of confidentiality and availability of data or information systems is significant, given the focus on unauthorized access and data exfiltration and encryption, posing a severe threat to the mission and functions of targeted organizations. This loss could lead to substantial financial repercussions, including considerable impacts on net sales, revenues, or income from continuing operations due to potential operational disruptions, system recovery costs, legal consultations, and regulatory fines. Furthermore, the ability to disrupt operations could extend the impact to clients and partners, eroding trust and potentially leading to business loss. The leakage of sensitive data compounds these issues, threatening long-term negative repercussions on market standing and financial health.
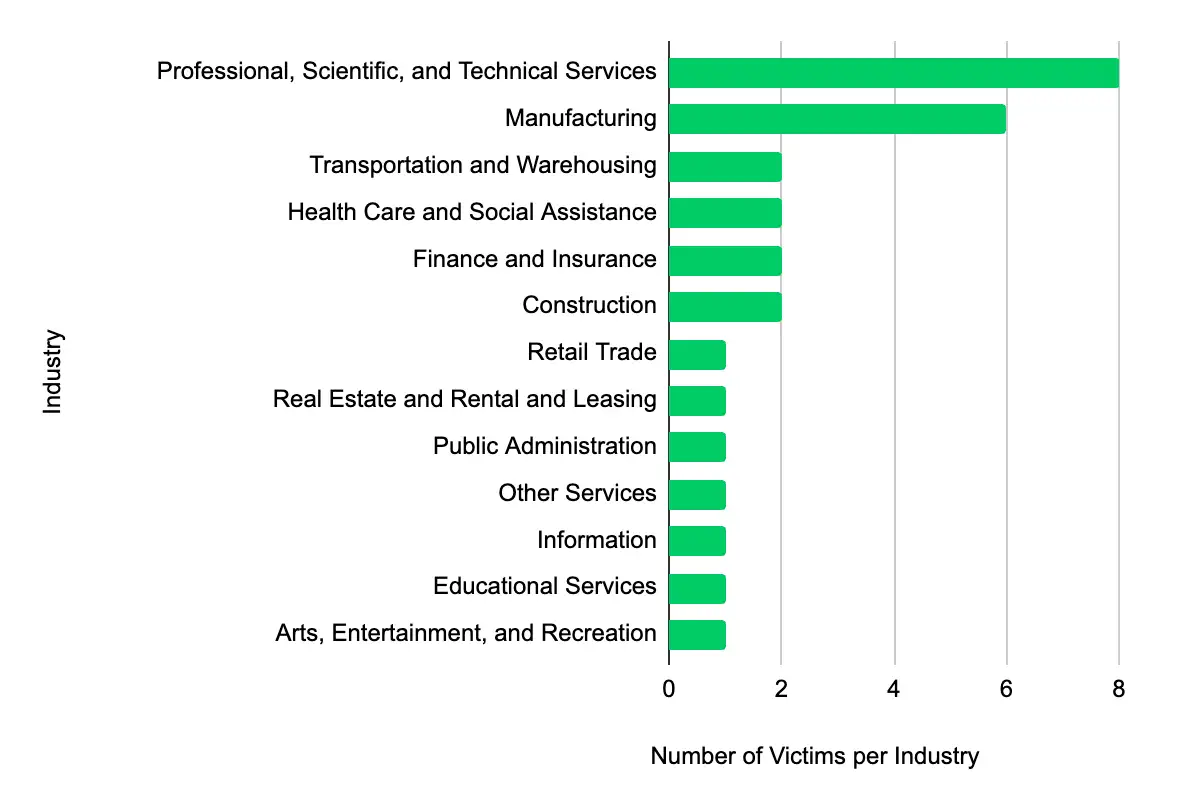
Latest Additions to Data Leak Sites
Professional, Scientific, and Technical Services – Manufacturing – Information – Retail Trade – Real Estate and Rental and Leasing
In the past week, monitored data extortion and ransomware threat groups added 29 victims to their leak sites. Of those listed, 16 are based in the US. Professional, Scientific, and Technical Services was the most popular industry listed, with eight victims. This industry is followed by six in Manufacturing and two in Transportation and Warehousing, Health Care and Social Assistance, and Finance and Insurance. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 10 CVEs to its Known Vulnerabilities Catalog
Within the past week, CISA added ten CVEs to the catalog, affecting products from Owl Labs, MinIO, Zyxel, RealTek, Adobe, Laravel, and Samsung. Threat actors can exploit these vulnerabilities for code and command execution, retrieve passcode hash, deactivate passcode protection mechanism, device control, and privilege escalation. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action occur between 5 and 10 October 2023.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-26369 | Adobe | Acrobat and Reader | Adobe Acrobat and Reader contains an out-of-bounds write vulnerability that allows for code execution. | 10/5/23 |
| CVE-2022-22265 | Samsung | Mobile Devices | Samsung devices with selected Exynos chipsets contain a use-after-free vulnerability that allows malicious memory write and code execution. | 10/9/23 |
| CVE-2014-8361 | Realtek | SDK | Realtek SDK contains an improper input validation vulnerability in the miniigd SOAP service that allows remote attackers to execute malicious code via a crafted NewInternalClient request. | 10/9/23 |
| CVE-2017-6884 | Zyxel | EMG2926 Routers | Zyxel EMG2926 routers contain a command injection vulnerability located in the diagnostic tools, specifically the nslookup function. A malicious user may exploit numerous vectors to execute malicious commands on the router, such as the ping_ip parameter to the expert/maintenance/diagnostic/nslookup URI. | 10/9/23 |
| CVE-2021-3129 | Laravel | Ignition | Laravel Ignition contains a file upload vulnerability that allows unauthenticated remote attackers to execute malicious code due to insecure usage of file_get_contents() and file_put_contents(). | 10/9/23 |
| CVE-2022-31459 | Owl Labs | Meeting Owl | Owl Labs Meeting Owl contains an inadequate encryption strength vulnerability that allows an attacker to retrieve the passcode hash via a certain c 10 value over Bluetooth. | 10/9/23 |
| CVE-2022-31461 | Owl Labs | Meeting Owl | Owl Labs Meeting Owl contains a missing authentication for critical functions vulnerability that allows an attacker to deactivate the passcode protection mechanism via a certain c 11 message. | 10/9/23 |
| CVE-2022-31462 | Owl Labs | Meeting Owl | Owl Labs Meeting Owl contains a use of hard-coded credentials vulnerability that allows an attacker to control the device via a backdoor password (derived from the serial number) that can be found in Bluetooth broadcast data. | 10/9/23 |
| CVE-2022-31463 | Owl Labs | Meeting Owl | Owl Labs Meeting Owl contains an improper authentication vulnerability that does not require a password for Bluetooth commands, as only client-side authentication is used. | 10/9/23 |
| CVE-2023-28434 | MinIO | MinIO | MinIO contains a security feature bypass vulnerability that allows an attacker to use crafted requests to bypass metadata bucket name checking and put an object into any bucket while processing `PostPolicyBucket` to conduct privilege escalation. To carry out this attack, the attacker requires credentials with `arn:aws:s3:::*` permission, as well as enabled Console API access. | 10/10/23 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share