Silver Sparrow – Huh?
Silver Sparrow is malware that was discovered by Red Canary detection engineers. As security professionals, we’re used to most malware being targeted for Windows operating systems. This is due to the fact that Windows just has a larger amount of targets available for a hacker to be successful. However, this is actually a macOS piece of malware that leverages a strain of macOS malware using LaunchAgent. This previously undetected strain of malware is unique in that this particular variant of malware does not behave similarly to recent macOS malware recently found in the wild.
This malware is a little more mysterious than others due to its unusual target, which appears to be targeting Apple’s new M1 ARM64 architecture. Given that versions of this malware are compatible with the new M1 chip, combined with its ability to infect at high rates, poses a sophisticated threat payload delivery capability on a global scale. Red Canary stated that it’s “…an activity cluster that includes a binary compiled to run on Apple’s new M1 chips…”
What Happened
Luckily, all known instances of Silver Sparrow macOS malware didn’t include a payload. This is a positive outcome considering that it made its way to about 40,000 Macs. If thinking like an attacker, one could derive that the malware developer was staging for a larger scale payload deployment in mass. In most attacks, an attacker usually follows a series of steps which follow along the line of a type of reconnaissance to delivering a payload which then opens up a multitude of opportunities to perform bad activity.
Since the payload wasn’t actually included in the malware, this indicates that a potential large scale plan was being acted upon. Think of it like the most basic military strategy in war:
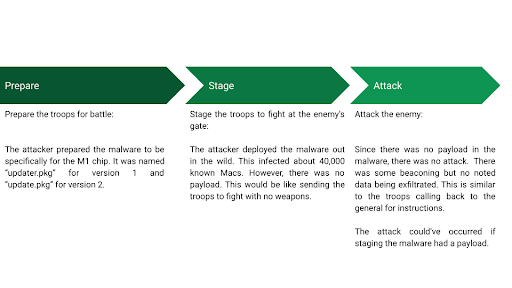
As noted in the diagram, the last part in this scenario wasn’t performed by the actor successfully. It appeared that the attacker was still in the staging phase. All 40,000 could’ve been used for a myriad of bad activities such as DDoS, large scale data exfiltration, or a mix of whatever the actor wanted. If Silver Sparrow wasn’t detected, more Macs could’ve been infected which makes the actor’s “army” larger and better for a wide-spread attack.
Resolution
Apple acted quickly to remediate its vulnerability by revoking the certificates used on the bad actor’s developer accounts used to assist in delivering the malware onto victim’s devices. This essentially halts any new devices from being infected by Silver Sparrow macOS malware and any other type of program written by the malware’s creator if they use those same accounts and if the same tactics are used. However, it’s unknown if something similar is still happening without anyone noticing.
Recommendations
Besides Apple remediating the malware as mentioned above, most Endpoint Detection and Response (EDR) solutions now have signatures in place for detecting and protecting against this malware. Ensure that your network has the most updated version of EDR signatures, all security patching has been applied for the OS, and as always, don’t click on anything from any email coming from someone you don’t know as that is the easiest way of delivering malware to a computer.
What’s Next
Deepwatch is continuously monitoring this across all our customer environments. As a part of our normal process, malware such as this is at first analyzed to gather as much information as possible, a retrospective analysis follows and any response actions are then applied.
As a more advanced solution, Deepwatch also investigates variants of malware with high priority such as this. This includes looking at malware that is similar to the originally reported one. We do this as a proactive measure to ensure that the unknowns have been addressed with appropriate due diligence. In other words, we’re geeks that love going down the rabbit hole. We love finding things that weren’t found before and applying solutions before anyone else.
Supporting Information
- www.deepwatch.com
- https://redcanary.com/blog/clipping-silver-sparrows-wings/
- https://www.theverge.com/2016/9/26/13057980/microsoft-windows-10-400-million-devices
- https://www.theverge.com/2017/4/4/15176766/apple-microsoft-windows-10-vs-mac-users-figures-stats
- https://blog.malwarebytes.com/mac/2021/02/the-mystery-of-the-silver-sparrow-mac-malware/
- https://mitre-attack.github.io/attack-navigator/
- https://www.macrumors.com/2021/02/22/apple-revokes-silver-sparrow-certificates/
- https://www.virustotal.com/gui/file/1decb4070db4dfe5d68ba502cf3a67de96a69ea6f3acfa4454795f96472ccc0d/details
- https://www.virustotal.com/gui/file/c7dd06b20b64b64d3b155b6b77c2778a08ef6a6c0396d7537af411258e57af1e/details
- https://www.virustotal.com/graph/embed/gf76ca103637d4041952a42affccd0a0cd4c3e7f06343463bbcb6864f3644b0e0
Share