DIY Malware Bypasses AV, SAP Flaw Enables Remote Attacks, and CISA Adds New Exploited Vulnerabilities Amid Rising Ransomware Activity
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Click, Paste, Infiltrate: The DIY Malware That Outsmarted Your Antivirus
The Rundown
Lumma Stealer, a malware-for-hire, is making waves with a surprisingly simple infection method. Attackers are using fake CAPTCHA pages that convince users to copy and run a Windows command—an act that secretly launches malware installation. It’s a social engineering trick that bypasses traditional malware defenses by using the target’s own hands to carry out the attack.
Analyst Note: Deepwatch Security Operations Center (SOC) analysts have noted a sustained increase in social engineering attempts leveraging deceptive CAPTCHA challenges. In light of this trend, organizations are strongly encouraged to enhance end-user security training—specifically focusing on emerging tactics such as fake CAPTCHA prompts and so-called “Clickfix” techniques—to mitigate risk and strengthen human-layer defenses.
Once installed, Lumma Stealer harvests sensitive data like browser credentials and cryptocurrency wallets. What makes this method particularly dangerous is its ability to sidestep antivirus tools and detection systems, since the user initiates the malicious action themselves. Sophos notes that this trend signals a shift toward low-tech, high-impact strategies.
For business leaders, the lesson is clear: user awareness and behavior are as critical as firewalls and software updates. Training staff to question unusual prompts—especially ones that ask them to run commands—can be the difference between a secure network and a costly breach.
Source Material: Sophos
Critical SAP NetWeaver Flaw Exposes Enterprises to Remote Attacks
The Rundown
A critical vulnerability, CVE-2025-31324, has been identified in SAP NetWeaver’s Visual Composer Framework (version 7.50). This flaw allows unauthenticated users to upload arbitrary files to the server via the /developmentserver/metadatauploader endpoint, leading to potential remote code execution and full system compromise. Attackers have been observed exploiting this vulnerability to deploy web shells, such as helper.jsp and cache.jsp, enabling persistent access and command execution on the compromised systems.
In incident response cases and telemetry, attackers have utilized this vulnerability to deploy reverse shell tools and a reverse SSH SOCKS proxy, leveraging various network infrastructures. These actions facilitate unauthorized access and data exfiltration, posing significant risks to affected organizations. Given the severity and ease of exploitation, immediate attention and remediation are crucial.
To mitigate this threat, organizations using SAP NetWeaver should prioritize reviewing and applying the official security guidance and patches provided by SAP. It is essential to ensure that vulnerable endpoints are secured and exposed systems are identified and assessed for potential compromise. Organizations should also deploy advanced threat detection and prevention tools capable of identifying exploitation attempts and related malicious network activity. Engaging with cybersecurity professionals or incident response teams can further support efforts to evaluate exposure, contain threats, and strengthen overall security posture.
Source Material: PaloAlto Unit42
Ransomware and Data Extortion Trends (May 5–11)
The Rundown
Ransomware and data extortion activity includes a slight decrease between May 5 – 11, with a 43% increase in listed organizations compared to the previous week.
During the reporting period, 103 organizations spanning 14 industries were listed on 11 ransomware and data extortion leak sites—a major increase from the 72 victims observed the previous week.
The sharp increase in ransomware and data extortion listings this week signals an escalation in threat actor activity rather than a decline. This surge, particularly impacting key sectors like Professional Services, Finance and Insurance, and Manufacturing across regions such as the United States, Canada, Germany, and Austria, suggests a deliberate shift toward broader and more aggressive targeting. Security teams should view this spike as a clear indicator of rising operational tempo and adapt their detection, response, and hardening strategies accordingly to counter the growing scale and sophistication of these attacks.
Key Trends:
- Most affected industries:
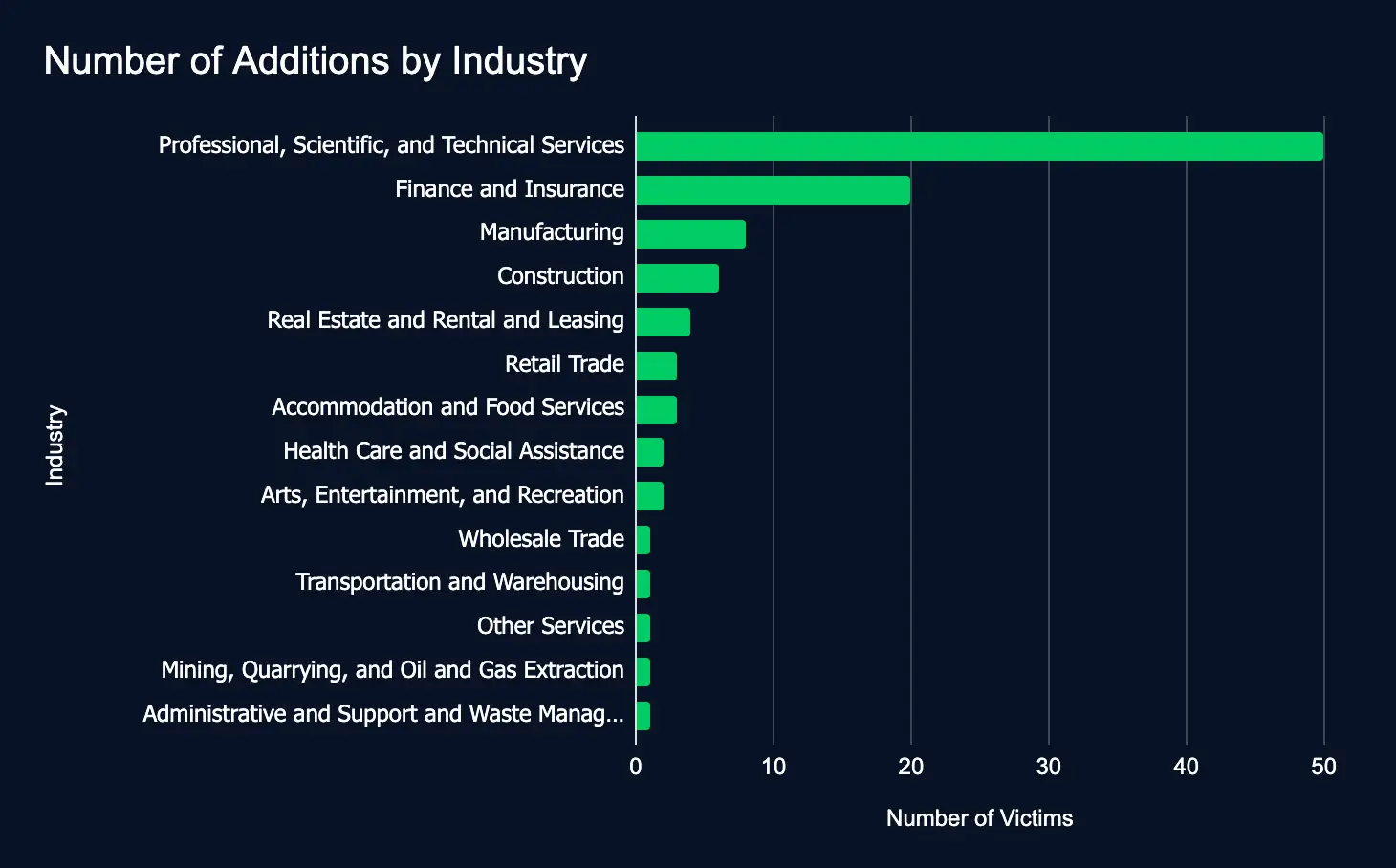
- Professional, Scientific, and Technical Services
- Finance and Insurance
- Manufacturing
- Most affected countries:
- United States
- Canada
- Germany
- Austria
- Most active leak sites:
- Leakeddata
- Play
- Qilin
Industry Impact
The Adversary Tactics and Intelligence team classified these organizations by sector using NAICS standards. While every effort has been made to ensure accuracy, determining the operating sector can be challenging due to companies operating in multiple sectors.
The chart below depicts the distribution of new data leak site listings across 14 industries, representing the majority of the 20 sectors defined by the North American Industry Classification System (NAICS). This week, the Professional Services sector was the most affected, comprising 49% of new listings. Finance and Insurance followed at 19%, with Manufacturing accounting for 8%, collectively representing the top three targeted sectors.
Exploited Vulnerabilities in TeleMessage, Microsoft, and Fortinet Products Added to CISA’s Catalog
The Rundown
Between May 8th and 14th, seven critical vulnerabilities impacting TeleMessage, Microsoft, and Fortinet products were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog. If not promptly addressed, these flaws could expose organizations to significant cyber threats.
Given the widespread use of the affected technologies, these vulnerabilities pose serious risks to operational security. With a heightened likelihood of exploitation by both state-sponsored and criminal threat actors, accelerated remediation is essential to maintain resilience and safeguard critical infrastructure.
TeleMessage | TM SGNL CVE-2025-47729
- Vulnerability Description: TeleMessage TM SGNL contains a hidden functionality vulnerability in which the archiving backend holds cleartext copies of messages from TM SGNL application users.
- Exploitation Details: The vulnerability arises from the TeleMessage archiving backend storing cleartext copies of messages from TM SGNL users. This behavior contradicts the application’s advertised feature of “End-to-End encryption from the mobile phone through to the corporate archive.” As a result, messages that users believed were securely encrypted could be accessed in plaintext form on the backend servers
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.Absent mitigating instructions from the vendor, discontinue use of the product.
- Date Added to catalog: 2025-05-12
- Recommended Mitigation Due Date: 2025-06-02
Microsoft | Windows CVE-2025-32709, CVE-2025-30397, CVE-2025-32706, CVE-2025-32701, CVE-2025-30400
- Vulnerability Descriptions:
- CVE-2025-32709: Microsoft Windows Ancillary Function Driver for WinSock contains a use-after-free vulnerability that allows an authorized attacker to escalate privileges to administrator.
- CVE-2025-30397: Microsoft Windows Scripting Engine contains a type confusion vulnerability that allows an unauthorized attacker to execute code over a network via a specially crafted URL.
- CVE-2025-32706: Microsoft Windows Common Log File System (CLFS) Driver contains a heap-based buffer overflow vulnerability that allows an authorized attacker to elevate privileges locally.
- CVE-2025-32701: Microsoft Windows Common Log File System (CLFS) Driver contains a use-after-free vulnerability that allows an authorized attacker to elevate privileges locally.
- CVE-2025-30400:Microsoft Windows DWM Core Library contains a use-after-free vulnerability that allows an authorized attacker to elevate privileges locally.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-13
- Recommended Mitigation Due Date: 2025-06-03
Fortinet | Multiple Products CVE-2025-32756
- Vulnerability Description: Fortinet FortiFone, FortiVoice, FortiNDR and FortiMail contain a stack-based overflow vulnerability that may allow a remote unauthenticated attacker to execute arbitrary code or commands via crafted HTTP requests.
- Exploitation Details: Fortinet has confirmed that CVE-2025-32756 has been exploited in the wild, particularly targeting FortiVoice systems. Attackers have been observed sending specially crafted HTTP requests to vulnerable systems, leading to remote code execution.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-14
- Recommended Mitigation Due Date: 2025-06-04
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share