Expression Injection, Social Engineering, and Expanding Exploits: Ivanti RCE, Scattered Spider Tactics, and Ransomware Trends Define This Week in Cyber Threats
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Breaking the Chain: How Expression Injection and Misconfigurations Led to Ivanti EPMM RCE
- Retail Under Siege: Scattered Spider’s Social Engineering Ramps Up in 2025
- Ransomware and Data Extortion Trends (May 12 – 18)
- Exploited Vulnerabilities in SAP, DrayTek, Google, ZKTeco, Synacor, Srimax, MDaemon, and Ivanti Products Added to CISA’s Catalog
Breaking the Chain: How Expression Injection and Misconfigurations Led to Ivanti EPMM RCE
The Rundown
In May 2025, WatchTowr Labs uncovered two critical vulnerabilities in Ivanti’s Endpoint Manager Mobile (EPMM) platform: CVE-2025-4427 and CVE-2025-4428. These flaws, when exploited together, allow attackers to bypass authentication and execute arbitrary code on affected systems without valid credentials. The vulnerabilities stem from issues in third-party open-source libraries integrated into EPMM, not from Ivanti’s proprietary code. Ivanti has released patches to address these vulnerabilities in versions 11.12.0.5, 12.3.0.2, 12.4.0.2, and 12.5.0.1 of EPMM.
The exploitation of these vulnerabilities poses significant risks to organizations, as attackers can gain unauthorized access and control over mobile device management systems. Given the critical nature of these flaws, it’s imperative for businesses using Ivanti EPMM to apply the recommended patches promptly. Additionally, implementing access controls, such as filtering API access through built-in Portal ACLs or external web application firewalls, can mitigate potential threats.
This incident underscores the importance of regular security assessments and prompt patch management in enterprise environments. Organizations should remain vigilant, especially when utilizing third-party components within their infrastructure, to ensure the integrity and security of their systems.
Source Material: WatchTowr
Retail Under Siege: Scattered Spider’s Social Engineering Ramps Up in 2025
The Rundown
A cybercriminal group known as Scattered Spider (also tracked as UNC3944) has shifted its focus from UK to US retailers, using deceptive social engineering tactics to breach major companies. The group is notorious for impersonating employees during IT help desk calls to gain unauthorized access to systems. Recently, luxury brands like Dior, Harrods, and Marks & Spencer have been compromised, with Dior’s breach exposing sensitive customer data in China and South Korea.
Scattered Spider has evolved its operations over time. While previously linked to high-profile attacks on MGM Resorts and Caesars Entertainment, the group has now pivoted to targeting retail, often deploying ransomware through a new partner group using the DragonForce ransomware-as-a-service platform. Their motives appear to be a mix of financial gain and notoriety, with their attacks often timed and targeted to create maximum media exposure and impact.
Cybersecurity experts warn that these attacks are increasingly strategic, exploiting long-standing vulnerabilities in retailers’ systems. Businesses are advised to implement proactive defenses, particularly against social engineering. Recommendations include removing password reset responsibilities from IT help desks, enforcing multifactor authentication, using tools like Microsoft Entra for secure password resets, and training employees to recognize and report suspicious activity—especially unexpected MFA prompts. These steps can help organizations detect and block intrusions before damage is done.
Source Material: DarkReading
Ransomware and Data Extortion Trends (May 12–18)
The Rundown
Ransomware and data extortion activity experienced a slight decline between May 12 and 18, marked by a 9% reduction in the number of listed victim organizations compared to the previous week.
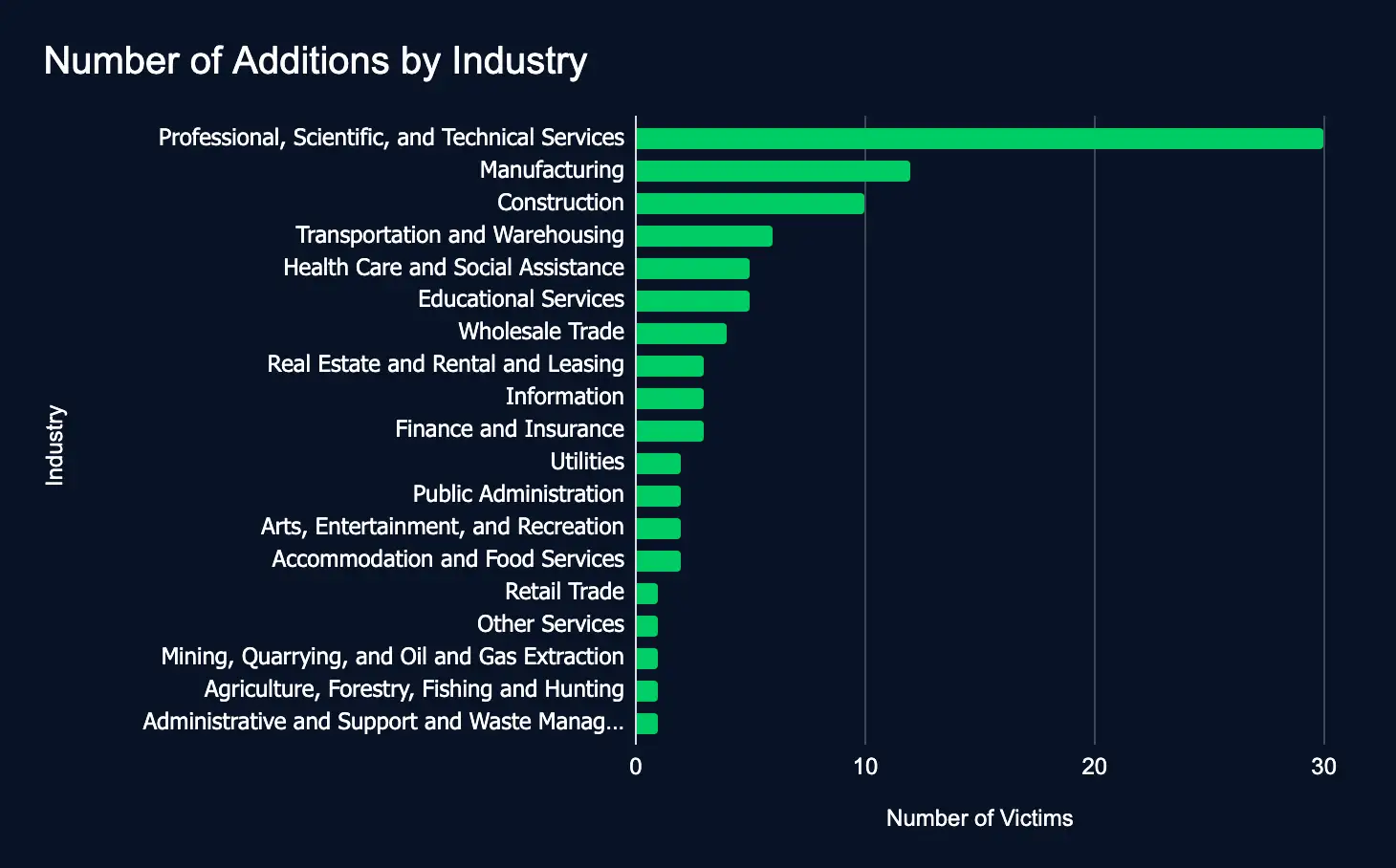
During the reporting period, 94 organizations across 19 industries were listed on 17 ransomware and data extortion leak sites—representing a slight decrease from the 103 victims reported the previous week.
This week’s slight decrease in ransomware and data extortion listings indicates a steady level of threat actor activity, rather than a significant drop or surge. Notably, consistent targeting of key sectors—such as Professional Services, Manufacturing, and Construction—across regions including the United States, Canada, Germany, and Spain, points to a strategic expansion in scope. Security teams should view this as an indication of sustained threat actor activity and align their detection, response, and hardening strategies to effectively counter the increasing scale and sophistication of these campaigns.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Construction
- Most affected countries:
- United States
- Canada
- Germany
- Spain
- Most active leak sites:
- Safepay
- Qilin
- Play
- INC Ransom
- Crypto24
Industry Impact
The Adversary Tactics and Intelligence team classified these organizations by sector using NAICS standards. While every effort has been made to ensure accuracy, determining the operating sector can be challenging due to companies operating in multiple sectors.
The chart below depicts the distribution of new data leak site listings across 17 industries, representing the majority of the 20 sectors defined by the North American Industry Classification System (NAICS). This week, the Professional Services sector was the most affected, comprising 32% of new listings. Manufacturing followed at 13%, with Construction accounting for 11%, collectively representing the top three targeted sectors.
Exploited Vulnerabilities in SAP, DrayTek, Google, ZKTeco, Synacor, Srimax, MDaemon, and Ivanti Products Added to CISA’s Catalog
The Rundown
Between May 15 and 21, nine critical vulnerabilities affecting products from SAP, DrayTek, Google, ZKTeco, Synacor, Srimax, MDaemon, and Ivanti were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
These vulnerabilities, if left unaddressed, present a significant risk to organizational security, potentially exposing systems to active exploitation.
Given the broad adoption of the impacted technologies across industries, the associated threats are substantial. The likelihood of exploitation by both state-sponsored and financially motivated threat actors remains high. As such, immediate and prioritized remediation is imperative to maintain operational resilience and protect critical infrastructure from compromise.
SAP | NetWeaver CVE-2025-42999
- Vulnerability Description: SAP NetWeaver Visual Composer Metadata Uploader contains a deserialization vulnerability that allows a privileged attacker to compromise the confidentiality, integrity, and availability of the host system by deserializing untrusted or malicious content.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-15
- Recommended Mitigation Due Date: 2025-06-05
DrayTek | Vigor Routers CVE-2024-12987
- Vulnerability Descriptions: DrayTek Vigor2960, Vigor300B, and Vigor3900 routers contain an OS command injection vulnerability due to an unknown function of the file /cgi-bin/mainfunction.cgi/apmcfgupload of the component web management interface.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-15
- Recommended Mitigation Due Date: 2025-06-05
Google | Chromium CVE-2025-4664
- Vulnerability Description: Google Chromium contains an insufficient policy enforcement vulnerability that allows a remote attacker to leak cross-origin data via a crafted HTML page.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-15
- Recommended Mitigation Due Date: 2025-06-05
ZKTeco | BioTime CVE-2023-38950
- Vulnerability Description: ZKTeco BioTime contains a path traversal vulnerability in the iclock API that allows an unauthenticated attacker to read arbitrary files via supplying a crafted payload.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-19
- Recommended Mitigation Due Date: 2025-06-09
Synacor | Zimbra Collaboration Suite (ZCS) CVE-2024-27443
- Vulnerability Description:Zimbra Collaboration contains a cross-site scripting (XSS) vulnerability in the CalendarInvite feature of the Zimbra webmail classic user interface. An attacker can exploit this vulnerability via an email message containing a crafted calendar header, leading to the execution of arbitrary JavaScript code.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-19
- Recommended Mitigation Due Date: 2025-06-09
Srimax | Output Messenger CVE-2025-27920
- Vulnerability Description:Srimax Output Messenger contains a directory traversal vulnerability that allows an attacker to access sensitive files outside the intended directory, potentially leading to configuration leakage or arbitrary file access.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-19
- Recommended Mitigation Due Date: 2025-06-09
MDaemon | Email Server CVE-2024-11182
- Vulnerability Description: MDaemon Email Server contains a cross-site scripting (XSS) vulnerability that allows a remote attacker to load arbitrary JavaScript code via an HTML e-mail message.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-19
- Recommended Mitigation Due Date: 2025-06-09
Ivanti | Endpoint Manager Mobile (EPMM) CVE-2025-4427, CVE-2025-4428
- Vulnerability Description:
- CVE-2025-4427: Ivanti Endpoint Manager Mobile (EPMM) contains an authentication bypass vulnerability in the API component that allows an attacker to access protected resources without proper credentials via crafted API requests. This vulnerability results from an insecure implementation of the Spring Framework open-source library.
- CVE-2025-4428: Ivanti Endpoint Manager Mobile (EPMM) contains a code injection vulnerability in the API component that allows an authenticated attacker to remotely execute arbitrary code via crafted API requests. This vulnerability results from an insecure implementation of the Hibernate Validator open-source library.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-19
- Recommended Mitigation Due Date: 2025-06-09
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share