Information Security professionals over the years have developed technical methodologies to enhance the functions within the security program, such as threat hunting for detection and response.
Frameworks such as the NIST Cybersecurity Framework, HITRUST, and MITRE ATT&CK have been developed to help provide structure to security programs from which to baseline standards, guidelines, and regulations. Frameworks and models also allow information security professionals to manage risk, which is the ever-shifting target in cybersecurity that requires constant human oversight.
Security teams have to manage threats that are known and unknown. Therefore, understanding the tactics, techniques, and procedures (TTPs) of a threat actor helps establish baselines, or use cases, as mechanisms to fight the adversary in cybersecurity. And one of the first to the information security community was the development and definition of the cybersecurity kill chain.
What Is the Cyber Kill Chain?
The term kill chain comes from a military concept that uses stages to outline the structure of an attack. “Breaking” the opponent’s kill chain refers to the ability to block an attack at any stage.
In 2011 computer scientists at Lockheed-Martin corporation adapted this concept to develop the intrusion (cyber) kill chain framework which describes the steps used by attackers during cyber-based attacks.
The seven stages (phases) include: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control (C2), and Action on Objectives.
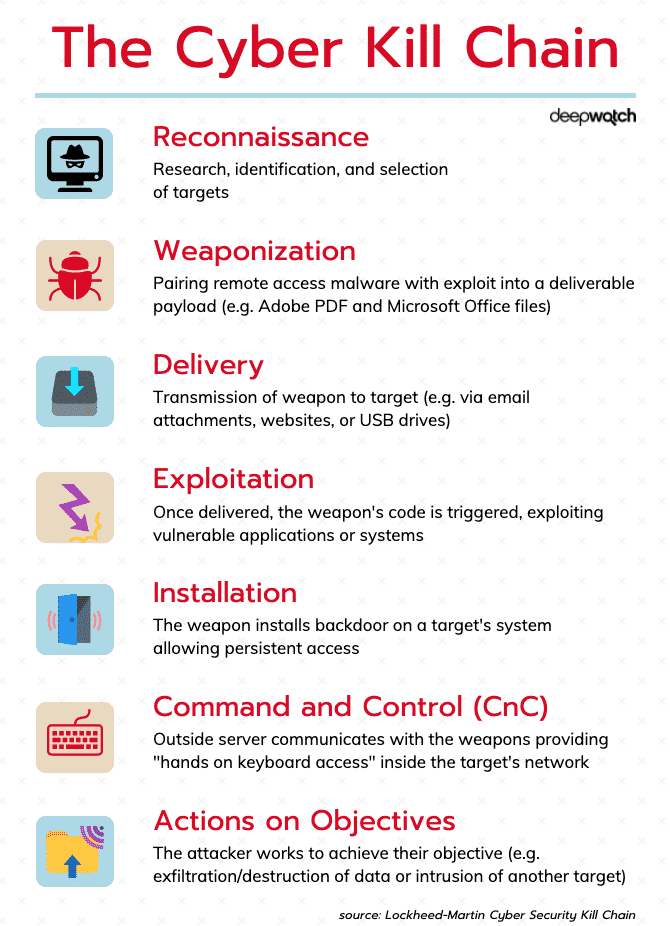
This model is used by cybersecurity organizations as a way to understand the sequence of events involved in an external attack on an organization’s IT environment. For instance, SecOps (Security Operations) teams can correlate security alerts with the phase that corresponds to the detected activity. Not only does this provide, at a glance, how far along a potential attack is, it can also assist security teams with putting strategies and technologies in place that will “kill” or stop the attack before it moves to the next phase.
The Seven Phases
1. Reconnaissance
This is the intelligence-gathering phase. The intruder selects a target, researches it, and looks for vulnerabilities within the target network. They review available information and resources about an organization and its public-facing assets. Any of the following can be used to develop a list of potential targets:
- Company websites
- News articles
- Social media
Threat actors will then make a decision as to which potential targets are worth the effort.
They tend to choose targets that are considered to be relatively unprotected, unguarded, or neglected and which they believe hold valuable data and information.
2. Weaponization
The intruder analyzes the gathered information and plans the weapon to be used in the cyber-attack. For example, a deliverable payload, a type of weaponized file created to do something for the intruder, may be embedded into a PDF or Word document. In another example, a malicious URL that redirects users to a malware-laden website can be put inside an email. Individuals within an organization may be targeted through social-engineering attacks such as phishing.
3. Delivery
In this phase, the payload (weapon) is transmitted to the target via a communication vector.
Delivery can be accomplished using any of the following vectors:
The key to the intruder’s success is to deliver the payload undetected.
4. Exploitation
Once inside the system, the intruder will attempt to move laterally to other systems/accounts on the network. The goal is to increase the permission level in order to reach more data. Some techniques that may be used are:
- Exploiting password vulnerabilities
- Credential extraction
- Brute force attacks
- Targeting other system vulnerabilities
5. Installation
The installation (or persistence) phase describes the actions taken by a threat actor to establish a backdoor into the targeted system. This gives the threat actor sustained and persistent access to the target – thus providing them a way to access the system whenever they desire.
With this access intruders may:
- Install tools
- Create script files
- Modify security certificates
- Look for additional vulnerabilities
The attackers will attempt to keep their presence secret.
6. Command and Control (CnC)
Command-and-Control (CNC) occurs when an exploited host sends outbound beacons to an Internet-based controller in order to establish a communications channel. Once CNC is established with an exploited target, threat actors will have access to the target system and possibly the entire network itself. These channels allow the threat actor to issue commands to the malicious software that had been installed on the target (or targets).
7. Actions on Objectives
Intruders take action to achieve their goals, such as:
- data exfiltration
- data destruction
- encryption for ransom
They may attempt to cause confusion (such as masking the activity) in order to meet their objectives.
Conclusion
The seven phases of the cyber kill chain are important for information security teams and users alike. A strong security program consists of 1) protective controls, or preventative technologies, to secure the network, data, and users, and 2) 24/7/365 monitoring, detection and response to actively secure the network should a security event occur along any of the phases of the Cyber Kill Chain.
Deepwatch can provide outsourced cybersecurity services to support both goals using best-in-class security technologies. It is critical to be able to detect activity during any of the seven phases. With an extended team of experts managing detection and response for you, including day-to-day alert management and proactive threat hunting, using the right tools, such as a SIEM like Splunk, you can identify the threat behavior during each stage, and resolve threats fast to defend your network against system and/or data breaches.
Source
Lockheed Martin Cyber Kill Chain: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
↑
Share