 This is Part II of a III part series published by Deepwatch on the SolarWinds attack of 2020. In Part I, we examined the attack techniques and what they meant for enterprises. In this piece, we will use the MITRE ATT&CK Framework as a reference guide for describing and categorizing the methods used by the attackers.
New coverage and information on the SolarWinds attack continues to flood the media and cybersecurity collaboration channels. During the compilation and writing of this blog post, MITRE has since updated it’s framework to include additional techniques for identifying and detecting actors (https://attack.mitre.org/) (https://medium.com/mitre-attack/identifying-unc2452-related-techniques-9f7b6c7f3714).
Some companies who aren’t SolarWinds customers have claimed to be targeted by the same actor: (https://blog.malwarebytes.com/malwarebytes-news/2021/01/malwarebytes-targeted-by-nation-state-actor-implicated-in-solarwinds-breach-evidence-suggests-abuse-of-privileged-access-to-microsoft-office-365-and-azure-environments/), as well as several different variants of the malware attributed to the attack dubbed Teardrop and Raindrop (https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/solarwinds-raindrop-malware). This is a sophisticated campaign that Microsoft estimates required at least 1,000 engineers to enact. (https://www.zdnet.com/article/microsoft-solarwinds-attack-took-more-than-1000-engineers-to-create/)
TL;DR:
Both commercial and open source software vendors need to be vigilant and need to be held accountable for the protection of their Systems and Software Development Life Cycle to ensure cascading supply chain attacks do not have a downstream effect on their customer base. For enterprises, Least Privilege reigns and needs to be the rule, not the exception. MITRE ATT&CK, while valuable for establishing an overall taxonomy for describing attacker techniques, is unwieldy for most enterprises who want to summarize the front to back activities of an attack.
This is Part II of a III part series published by Deepwatch on the SolarWinds attack of 2020. In Part I, we examined the attack techniques and what they meant for enterprises. In this piece, we will use the MITRE ATT&CK Framework as a reference guide for describing and categorizing the methods used by the attackers.
New coverage and information on the SolarWinds attack continues to flood the media and cybersecurity collaboration channels. During the compilation and writing of this blog post, MITRE has since updated it’s framework to include additional techniques for identifying and detecting actors (https://attack.mitre.org/) (https://medium.com/mitre-attack/identifying-unc2452-related-techniques-9f7b6c7f3714).
Some companies who aren’t SolarWinds customers have claimed to be targeted by the same actor: (https://blog.malwarebytes.com/malwarebytes-news/2021/01/malwarebytes-targeted-by-nation-state-actor-implicated-in-solarwinds-breach-evidence-suggests-abuse-of-privileged-access-to-microsoft-office-365-and-azure-environments/), as well as several different variants of the malware attributed to the attack dubbed Teardrop and Raindrop (https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/solarwinds-raindrop-malware). This is a sophisticated campaign that Microsoft estimates required at least 1,000 engineers to enact. (https://www.zdnet.com/article/microsoft-solarwinds-attack-took-more-than-1000-engineers-to-create/)
TL;DR:
Both commercial and open source software vendors need to be vigilant and need to be held accountable for the protection of their Systems and Software Development Life Cycle to ensure cascading supply chain attacks do not have a downstream effect on their customer base. For enterprises, Least Privilege reigns and needs to be the rule, not the exception. MITRE ATT&CK, while valuable for establishing an overall taxonomy for describing attacker techniques, is unwieldy for most enterprises who want to summarize the front to back activities of an attack.
Intro
It seems every day brings a new development in the ongoing SolarWinds saga, whether it be related to technical details, actor attribution, new malware variants, or what it means to the cybersecurity industry as a whole. One thing is for sure: we’re failing.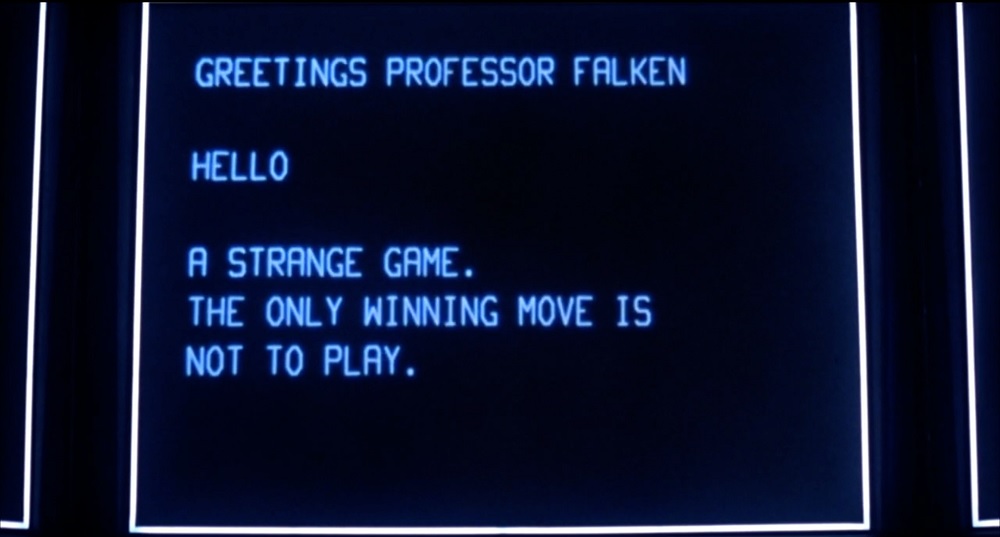 Falken’s Maze is a reference to the 1983 movie WarGames and refers to the first game on the list of games provided by the AI character Joshua. The hacker protagonist uses the game to figure out the intentions of the designer who engineered the system. In many ways, MITRE ATT&CK has grown into more of a maze than a roadmap for describing attacker methodologies. While the sub-techniques that came with Version8 of the framework are important, the practitioner can easily get lost in the complexity.
Is MITRE ATT&CK too complicated? Is it the right framework for the cybersecurity community to use to detect, respond, and describe complex nation-state sponsored attacks? We do not believe so and think the industry needs to get to something simpler and easier to digest.
Falken’s Maze is a reference to the 1983 movie WarGames and refers to the first game on the list of games provided by the AI character Joshua. The hacker protagonist uses the game to figure out the intentions of the designer who engineered the system. In many ways, MITRE ATT&CK has grown into more of a maze than a roadmap for describing attacker methodologies. While the sub-techniques that came with Version8 of the framework are important, the practitioner can easily get lost in the complexity.
Is MITRE ATT&CK too complicated? Is it the right framework for the cybersecurity community to use to detect, respond, and describe complex nation-state sponsored attacks? We do not believe so and think the industry needs to get to something simpler and easier to digest.
MITRE Framework Mapping
In recent years, the MITRE ATT&CK Framework has become an industry standard for describing and categorizing attack techniques. For those unfamiliar with the Framework or its purpose, this ATT&CK 101 post (https://medium.com/mitre-attack/att-ck-101-17074d3bc62) and the “Getting Started” page (https://attack.mitre.org/resources/getting-started/) are good resources to reference for background and insights. This MITRE ATT&CK framework is a solid mechanism to make sure security folks are all speaking the same language. At Deepwatch, we leverage the framework as one of the categorization techniques for our Content Library. This product is used by all of our customers and is part of the Deepwatch Analytics App for Splunk. As detailed in our first post, the adversary behind the SolarWinds attack used various techniques to gain initial entry, establish a foothold, and move laterally through victim networks. In this post, we will dissect each technique used by the adversary and leverage the taxonomy of the ATT&CK Framework to better understand how to detect and defend against complex scenarios such as the SolarWinds attack. We will be using Version 8 of the ATT&CK framework which includes “sub-techniques”. Given that software vendors cannot be trusted to ensure security across the board, enterprises need to prioritize least privilege access. They also need to focus on the visibility of systems and networks to ensure a quick response to complex attacks. The Deepwatch Security Research Team has identified (at this time) 10 different techniques used in the SolarWinds Attack dating back to March of 2020. These attack techniques (from left to right on the MITRE ATT&CK matrix) may include the following types of techniques.Mapping the red thread throughout the SolarWinds hack across the MITRE ATT&CK framework: (*click to view full-sized image*)
Pre-Attack: Reconnaissance (TA0043) and Resource Development (TA0042)
Reconnaissance (TA0043) and Resource Development (TA0042) can surmise that the adversaries specifically chose the SolarWinds platform for several reasons:- Trusted software and protocols
- Wide distribution and customer base
- Required account privileges
Establishing a Foothold: Initial Access (TA0001), Execution (TA00002), Persistence (TA0003)
The SolarWinds attackers knew that because the software was trusted by administrators across enterprises, it would be trivial to establish a digital beachhead in order to attack the companies they were targeting once the software was downloaded and installed. The most interesting aspect of this is that by design and default SolarWinds is a system that maps, monitors and configures entire enterprise networks. Compromising the SolarWinds systems is akin to having an insider in the control room of a nuclear power plant: all of the access that’s needed is automatically granted. This key technique is described by MITRE under Initial Access: Supply Chain Compromise (T1196) https://www.mitre.org/publications/technical-papers/supply-chain-attacks-and-resiliency-mitigations. No matter how mature an organization, defending against a supply chain compromise of this sophisticated nature is almost impossible. Even with processes for static code analysis, a software bill of materials, and testing/QA environments, a signed piece of code from a trusted vendor will almost always slip through the cracks.Digging In and Sticking Around: Defense Evasion (TA0005), Privilege Escalation (TA00004), Defense Evasion (TA0006)
This is probably my favorite part of the attack chain due to how unique it is. Oftentimes, the alarm bells go off or the attacker is simply unsuccessful in attempts to compromise the network, but as any red teamer will attest: once you get in, it’s how you stay in and cover your tracks that’s important. Beyond the initial attack, Indicators of Compromise (IoCs), and Tactics, Techniques, and Procedures (TTPs), details on the methods used for lateral movement are scarce. Because of the level of privilege needed for SolarWinds service accounts, not much privilege escalation was needed by the attackers to gain entry. (https://www.darkreading.com/endpoint/solarwinds-attack-reinforces-importance-of-principle-of-least-privilege/a/d-id/1340033) One of the brilliant ways the attackers obfuscated themselves (TA0006) was to disguise the C&C traffic as legitimate Orion Protocol traffic and make it look like the resources were sourced from Amazon Web Services (AWS). An analysis of the source code reveals that the attacker was deliberately using AWS terms to fool security teams into thinking that it was legitimate traffic: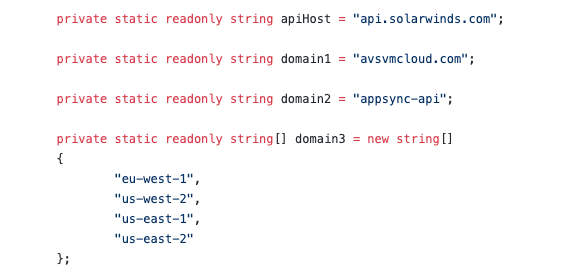 Note the use of AWS regions like “us-east-1” and the domain avsvmcloud[.]com to add subterfuge.
Another use of evasion techniques revolves around the comprehensive list of endpoint products and reverse engineering tools that the attackers know about, and have techniques for evading.
Note the use of AWS regions like “us-east-1” and the domain avsvmcloud[.]com to add subterfuge.
Another use of evasion techniques revolves around the comprehensive list of endpoint products and reverse engineering tools that the attackers know about, and have techniques for evading.
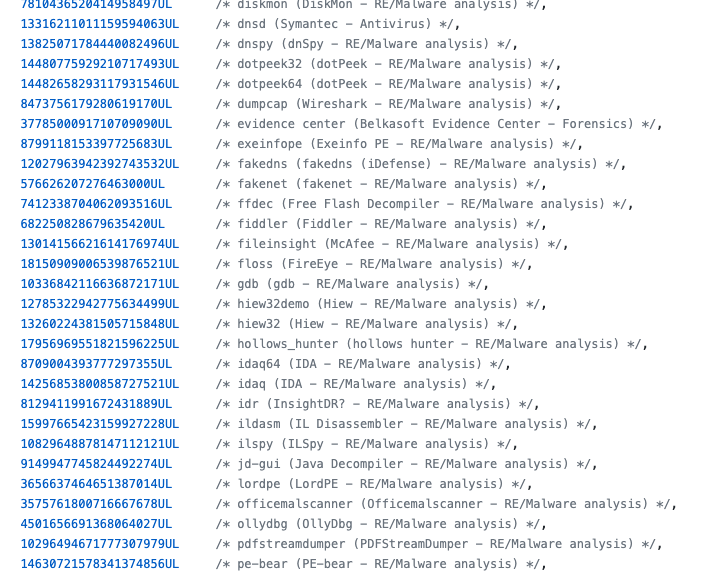 These tools include companies that were directly targeted including Microsoft, MalwareBytes, and FireEye.
These tools include companies that were directly targeted including Microsoft, MalwareBytes, and FireEye.
Share