Every couple of years, or months, a vulnerability comes to light that is just so egregious that everyone in IT has to sit up and take notice. It can be for its uniqueness (STUXNET) or for its wide ranging impact (Mirai) and sometimes it’s a little bit of both. Enter stage left our new friend the ZeroLogon vulnerability.
I won’t go into the technical details of the ZeroLogon vulnerability here, as it’s well publicized and has been talked about a lot.
- https://www.deepwatch.com/blog/zerologon-vulnerability/
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-1472
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472
- https://www.databreachtoday.com/microsoft-issues-updated-patching-directions-for-zerologon-a-15090
But I do want to provide a layman’s view of the exploit, what to be concerned about, and how to detect and ultimately prevent it.
What is the ZeroLogon vulnerability?
Lucain Constantin has a good explanation write up at CSO Online:
But in really broad strokes, there is a coding flaw in an application called NetLogon. Specifically, the issue is in the NetLogon Remote Protocol (MS-NRPC) which is used to authenticate on domain-based networks.
The flaw is in the implementation of cryptography of passwords being passed through MS-NRPC.
From Lucain:
“Tervoort figured out that because of this implementation error for 1 in 256 keys, applying AES-CFB8 encryption to an all-zero plaintext will result in all-zero ciphertext. In the context of MS-NRPC, the attacker impersonating a client can send a challenge during the handshake made up of 8-bytes of zeros and keep retrying for 256 times until the server will accept it, bypassing authentication.”
So, send eight (8) zeros (0) as a password for a known user a couple of times from inside the network and I bypass authentication. Got it.
Before worrying about how bad this is, we need to concern ourselves with how prevalent it is, and should we be worried about it.
How prevalent is NetLogon in Windows environments?
It’s been in every release of Windows operating systems since Windows 3.11. NetLogon is the process that allows a Windows machine to authenticate to a domain controller, to allow the system on the network, and to provide users access to shared drives, folders, documents, etc. NetLogon also provides users the ability to reset their Active Directory credentials.
So you can’t simply turn it off across your enterprise.
What is the potential impact of the ZeroLogon vulnerability in your environment?
From TrendMICRO:
“This vulnerability allows a hacker to take control of a domain controller (DC), including the root DC. This is done by changing or removing the password for a service account on the controller. The hacker can then simply cause a denial of service or take over and own the entire network.”
Sounds bad, doesn’t it? Frankly, it’s really bad. But before we collectively run for the hills, we have to dig a little deeper.
How likely is it that the ZeroLogon vulnerability will be a problem?
Here we come to the crux of the issue, also from TrendMICRO:
“For attackers to exploit this vulnerability, they must be able to set up a TCP session with a DC. If they are inside of the network physically, they could be at a user’s desk or at an open port in a location such as a conference room. These exploits qualify as insider attacks – the most expensive attacks for a business today. They can be established from outside of the network so long as they can gain a foothold somewhere to establish the TCP session to the controller.”
This is an insider attack. Meaning that in order for the Zerologon vulnerability to be successful, it HAS to be able to authenticate to your domain controller(s). In other words, some script kiddy from the outside world should be blocked by your exterior defenses well before she or he can take advantage of this vulnerability with an exploit.
Is this something to be concerned about? Absolutely! But it is not a world ending or life altering security event. It’s important to think about ZeroLogon in this way because though it is bad, your best defense against it is standard security hygiene. The defenses you already have in place, your network and access controls, endpoint and mobile capabilities, and a continuing focus on the improvement of your security capabilities will hold the door.
There is a chance that someone or something is already inside your network and can take advantage, but why would they choose ZeroLogon? Ransomware or some other mainstream malware may be easier to deploy and make the hacker more money. I can see ZeroLogon being used to get into devices or drives that contain sensitive information, but hackers could also do that via lateral movement and other privilege escalations.
Now that we have discussed the prevalence, impact, and likelihood, let’s finish up with the bad news.
How can I detect or prevent ZeroLogon?
Short answer: you can’t, at least not directly.
There are currently no detections or rules in place that would detect an active ZeroLogon “attack.” The action is an authenticated logon from a Windows device to an existing domain controller. This happens hundreds to thousands of times each day in a network and can’t be detected uniquely at this time.
Microsoft released a summation of their advice for dealing with ZeroLogon:
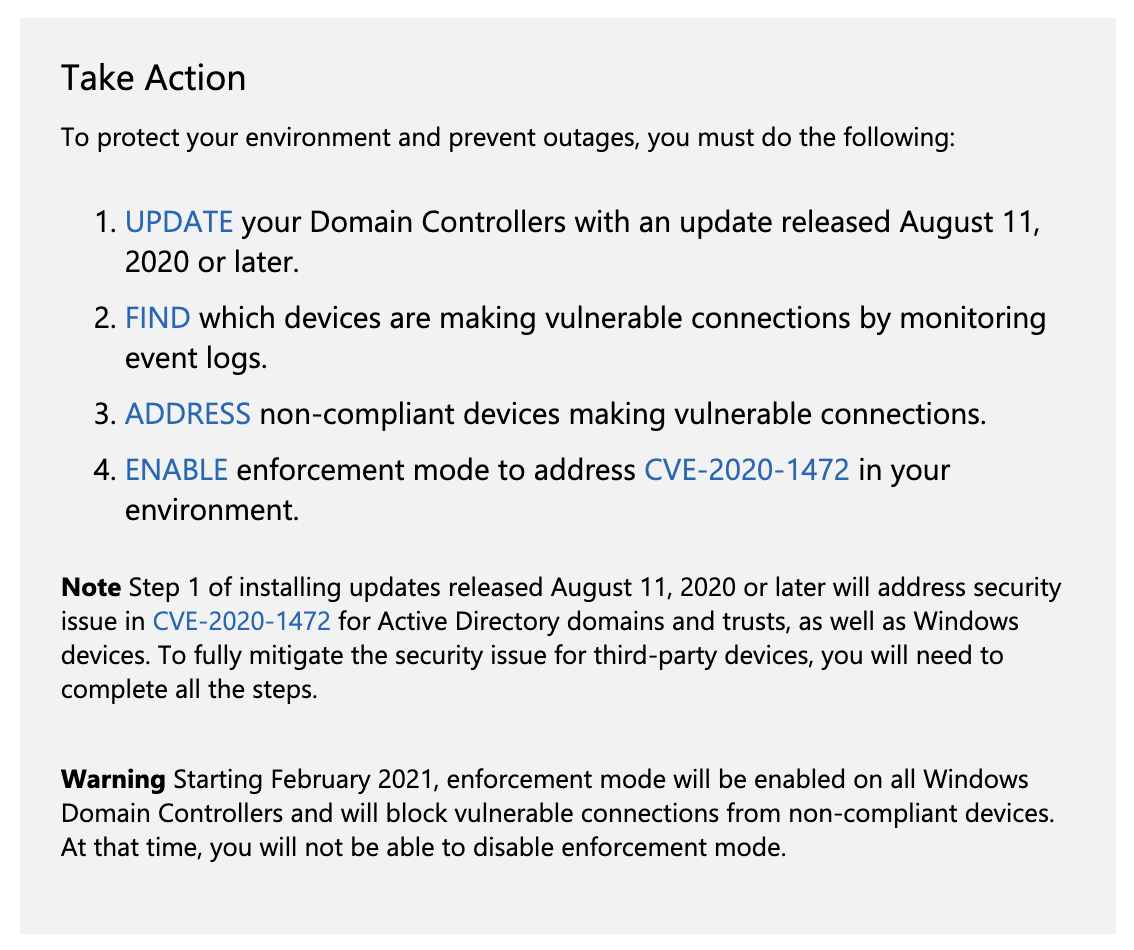
Patches for CVE-2020-1472 can be found here:
We encourage you to install the required patches on all of your Domain Controllers. This patch is more of a debug patch. It doesn’t fix the problem, it provides more logs for analysis based on a number of windows event codes.
Cisco Talos also mentions:
“To protect against this vulnerability, Microsoft recommends blocking non-signed or sealed connections entirely. SNORTⓇ users can use SID 55802 in alert mode to test that this is working properly. This rule specifically looks for those bad flags, so users can identify any systems in need of attention before Microsoft’s second phase of this patch goes live in January. “
This means that there is a detection (testing rule) for a properly configured Windows Domain Controller. This should not be confused with the detection of ZeroLogon.
Now for the good news.
What can I do about ZeroLogon?
The answer is Basic Security Hygiene! Continue to do the things you should already be doing and are largely already in place. These are the best defenses against the ZeroLogon vulnerability.
However, you do need to answer some questions to determine your current Security Hygiene.
- Do you have solid externally facing detection and protection systems?
- Do you have endpoint detection tools like Antivirus and Endpoint Detection and Response?
- Do you have network segmentation between low trust and high trust areas of your network?
- Do you have some form of individualized Network Access Control?
- Are you sure you have full visibility on the systems that are on your network, are there any EOL operating systems?
- Do you have visibility around vulnerabilities that exist within your network?
- Do you have a process to prioritize and understand the risk to your business related to these vulnerabilities?
- Do you have some form of UEBA?
There are three important things to take from the list above.
You need more than one of the items on the list. You don’t need them all to be enabled, but you definitely need more than two of them.
Strong Visibility. See number one above.
When was the last time you audited the installation and configuration of the technologies you do have? Are they properly set up? Have you evolved them along with your security posture and maturity?
This exploit takes advantage of a vulnerability through what looks like standard traffic communication that happens on a continual basis. You can’t detect the ZeroLogon vulnerability directly. You have to look around and limit the areas where it might be. This requires both visibility across your environment and an ability to correlate logs and reports from a variety of differing sources.
ZeroLogon is a perfect example of the need for an experienced Security Operations team that is capable of not only working to direct the securing or patching (hardening) of critical devices, but also to monitor the area and the connections to that environment. Your security team needs to be able to understand not only the infrastructure, but also where some of the weakest areas of that infrastructure are. As ZeroLogon is likely an insider threat scenario. It takes experience and eyes on glass to effectively combat it.
Again, it takes experience and eyes on glass to deal with the ZeroLogon vulnerabilityeffectively. If you don’t have enough people, time, or budget to deal with it effectively, consider contacting a Managed Security Services Provider… ahem Deepwatch. We’d be glad to talk you through how we deploy, and more importantly collaborate with you to understand your needs, outcomes, and capabilities, to effectively use our named squads to protect and defend your environment.
↑
Share