CoralRaider Gets Social, VenomRAT Deployed by ScrubCrypt, and Nearly 50 New Data Leak Victims
This week: Vietnamese-linked CoralRaider carries out campaign targeting user data and social accounts, adversaries are increasingly utilizing malware-initiated vulnerability scanning, VenomRAT is being deployed by ScrubCrypt with new plugins, and nearly 50 new victims appeared on data leak sites. All this plus two new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- User Data and Social Media Accounts Focus of New Threat Actor CoralRaider
- Malware-Initiated Vulnerability Scanning Utilized More and More By Adversaries
- VenomRAT Deployed by ScrubCrypt Along with Various Plugins
- Latest Additions to Data Leak Sites
- CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
User Data and Social Media Accounts Focus of New Threat Actor CoralRaider
CoralRaider – Credential Theft – RotBot – XClient – Infostealer- Remote Access Trojan – LoLBins
Threat Analysis
A new threat actor named CoralRaider has been observed carrying out a malicious campaign. There is high confidence that CoralRaider is of Vietnamese origin due to messages observed within the threat actor’s Telegram C2 bot channels, the language preferences when naming their bots, payload binaries having Vietnamese words hardcoded within them, as well as the actor’s IP address being of Vietnamese origin. India, China, South Korea, Bangladesh, Pakistan, Indonesia, and Vietnam were all countries targeted by CoralRaider in the malicious campaign. Windows shortcut files were used as a way to gain initial access as part of the campaign. It was not revealed how the threat actor was able to deliver the LNK’s, it is likely that phishing was used to accomplish this step, as many threat actors implement that technique to send malicious LNK files.
The malicious attack by the threat actor starts when a user clicks on the malicious Windows shortcut file, triggering the download and execution of an HTML application file (HTA) from a server controlled by the attacker. Within the HTA file, an embedded obfuscated Visual Basic script is executed. This script, in turn, runs an embedded PowerShell script in the system memory. This PowerShell script decrypts and sequentially executes three additional PowerShell scripts. These scripts conduct various checks to evade virtual machines and analysis, bypass User Access Controls, disable Windows and application notifications, and ultimately download and launch RotBot malware.
RotBot, a remote access tool (RAT) compiled on January 9, 2024, is a variant of QuasarRAT. The malware runs on the victim’s machine disguised as the Printer Subsystem application spoolsv.exe to evade detection on the victim’s machine and performs reconnaissance. RotBot conducts various checks on the victim’s machine to avoid detection, these checks include IP addresses, ASN numbers, and enumeration of active processes. RotBot adjusts the internet proxy settings on the victim’s machine by manipulating the registry key. It proceeds to connect to a host on a legitimate domain, likely under the control of the threat actor, to retrieve the configuration file needed to connect to the Command and Control (C2) server. CoralRaider utilizes a Telegram bot as the C2 channel in this campaign.
Once connected to the Telegram C2, RotBot loads XClient stealer payload into the victim’s memory and executes its plugin. The XClient stealer plugin conducts checks to evade virtual machines and antivirus software, then proceeds to gather the victim’s browser data, including cookies, saved credentials, and financial details like credit card information. Furthermore, it collects data from social media accounts such as Facebook, Instagram, TikTok business ads, and YouTube, as well as application data from Telegram desktop and Discord. Screenshots of the victim’s desktop are captured and saved as PNG files in the temporary folder of the victim’s machine. The collected data from browsers and social media accounts is stored in a text file and archived into a ZIP file along with the PNG files. These files are then sent to the attacker’s Telegram bot C2 for exfiltration.
The XClient stealer sample that was observed in this campaign is a Dot Net executable which was compiled on Jan. 7, 2024. The XClient stealer employs three main functions to elude detection. It first conducts evasion tactics for virtual environments, detecting if the victim’s machine operates within VMware or VirtualBox. It also scans for the presence of a DLL named sbieDll.dll in the victim’s file system to identify Sandboxie environments. Additionally, the XClient stealer checks for active antivirus software, including AVG, Avast, and Kaspersky, running on the victim’s machine.
Upon successfully bypassing these checks, the XClient stealer proceeds to capture screenshots of the victim’s machine. These screenshots are saved with the “.png” extension in the victim’s temporary user profile folder before being transmitted to the Command and Control (C2) server via the URL “/sendPhoto.”
The XClient stealer is designed to steal various sensitive data from the victim’s system, including social media web application credentials, browser data, and financial information such as credit card details. It targets data from Chrome, Microsoft Edge, Opera, Brave, CocCoc, and Firefox browsers by referencing the absolute paths of their respective installation directories. The extracted browser data is then stored in a text file within the victim’s local temporary folder.
Moreover, the XClient stealer specifically targets Facebook data by intercepting and extracting various information from the victim’s Facebook account. It crafts custom HTTP header metadata, incorporating the stolen Facebook cookie and username, to send requests to Facebook APIs through various URLs. The XClient conducts verification to determine if the victim’s Facebook account is associated with a business or advertising profile. It employs regular expressions to search for access_token, assetID, and paymentAccountID. Leveraging the Facebook Graph API, XClient attempts to gather a comprehensive array of information from the victim’s account. Additionally, the XClient stealer gathers financial data from the Facebook business and advertising accounts of the victims.Target account friend list details and pictures are also retrieved by the stealer.
The XClient stealer additionally focuses on the victim’s Instagram and YouTube accounts, accessing them via URLs and acquiring diverse information such as usernames, badge counts, app IDs, account section lists, content, titles, data, actions, multi-page menu actions, menus, multi-page menu renderers, sections, and channel status. It further retrieves application data from the victim’s machine, specifically targeting the Telegram desktop and Discord applications. Moreover, XClient gathers data from the victim’s TikTok business account and verifies the presence of business advertisements.
The XClient stealer compiles the collected social media data from the victim into a text file within the local user profile’s temporary directory and generates a ZIP archive. These ZIP archives are then transmitted to the Telegram C2 via the designated URL “/sendDocument”.
Risk & Impact Assessment
The malicious activities carried out by CoralRaider pose a significant risk to organizations, given the threat actor’s sophisticated tactics and the potential for widespread impact. The risk associated with CoralRaider’s malicious campaign is heightened by the use of advanced malware such as RotBot and XClient stealer combined with the threat actor’s ability to evade detection measures. The likelihood of CoralRaider’s activities impacting an organization is moderate to high, considering the widespread distribution of malicious Windows shortcut files and the successful deployment of malware payloads observed in the campaign.
A cyberattack employed by CoralRaider could have moderate consequences for an organization which targets data exfiltration and social media account information. Financially, the impact could be low to moderate, encompassing costs associated with remediation efforts, system restoration, and potential legal liabilities.
However, operational disruptions stemming from compromised systems and data theft could result in significant revenue losses and damage to business continuity. Additionally, the reputational damage incurred by an organization as a result of a successful attack could erode stakeholder trust, leading to customer attrition and diminished brand value. The theft of sensitive data, including social media credentials and financial information, could have far-reaching consequences, including regulatory penalties, legal ramifications, and long-term damage to the organization’s competitive standing.
Source Material: Talos, CoralRaider targets victims’ data and social media accounts
Malware-Initiated Vulnerability Scanning Utilized More and More By Adversaries
Malware-initiated Scanning – Vulnerability Scanning – Vulnerability Exploitation – Command and Control – Mirai- Ivanti
Threat Analysis
Threat actors have recently been observed using infected hosts for malware-based scans of their targets rather than using direct scans. Scanning is the process when an attacker launches network requests to uncover potential vulnerabilities within targeted hosts. These hosts are potentially susceptible to the vulnerabilities (CVEs) that the attacker is targeting. Port scanning, vulnerability scanning, OS fingerprinting are different types of scans that attackers use. An example of a direct type of scan from an attacker would be when an attacker submits an HTTP POST request to ransomsite[.]com. The scan is aimed to detect and then exploit a vulnerability that a host has. If randomsite[.]com is susceptible to this vulnerability without any additional protective measures in place, the attack would be successful.
Palo Alto’s Unit42 has observed numerous instances of scanning where attackers have incorporated previously unseen URLs for payload delivery or C2 alongside exploit requests. This tactic aims to lower the chances of security vendors blocking subsequent payload or C2 URLs. Given that these URLs are new to security vendors, it’s crucial to detect and block such initial scanning requests, as vendors are unlikely to intercept subsequent requests. On January 12, 2024, Unit 42 identified scanning activity by a Mirai variant, which included the following malicious URL in its payload:
103.245.236[.]188/skyljne.mips
Similarly, on January 18, 2024, Unit42 detected scanning attempting to exploit Ivanti vulnerabilities, featuring the following malicious URL in its payload:
45.130.22[.]219/ivanti.js
In both cases above, it was observed that the scanning requests preceded the detection of subsequent malicious payload delivery or C2 URLs by a large margin. This underscores the effectiveness of scanning detection in promptly identifying and responding to emerging threats by blocking scanning activities and pinpointing malicious URLs.
Scanning attacks driven by malware infect a device and utilize its resources to conduct scans. Usually, once a device becomes compromised by malware, the malware sends signals to attacker-controlled C2 domains for instructions. Threat actors can then direct the malware to conduct scanning attacks. Then, the malware on the compromised device can initiate scanning requests to various target domains. An example of this is if a host becomes infected by a Mirai malware variant (SHA256: 23190d722ba3fe97d859bd9b086ff33a14ae9aecfc8a2c3427623f93de3d3b14). The Mirai variant will establish a connection to its C2 server at 193.47.61[.]75, where it will receive the directive to begin scanning.
Following this instruction, the threat initiates scanning requests to multiple targets using the infected device’s resources. The ultimate goal for the attacker is to identify and exploit vulnerable targets. Depending on the intended attack strategy of the threat actor, the targets may vary. For example, an attacker might focus on a particular entity such as a government, employing exploit attempts with multiple vulnerabilities relevant to the government’s website. Alternatively, the attacker might aim to exploit as many websites as possible for diverse purposes, such as propagating a botnet. In such cases, the attacker would broaden their scope to include a variety of different targets.
Attackers often target vulnerabilities found in routers, web application development or testing frameworks, as well as collaboration tools like email and calendar platforms due to their extensive adoption. Unit42 research has shown that attackers frequently focus on technology stacks related to collaboration, web development frameworks, and routers. Router attacks have been notably prevalent among attackers. Malware-initiated scans represent a less direct method compared to the more straightforward approach typically associated with attacker-initiated scans.
Risk & Impact Assessment
The rise of malware-initiated scanning attacks poses a significant risk to organizations worldwide. This threat introduces a new layer of complexity to cyber defenses, as it leverages infected hosts to conduct stealthy scans, potentially bypassing traditional detection mechanisms. The likelihood of this threat impacting an organization is high, given the increasing sophistication of various adversaries using this technique. The unwanted outcomes of such attacks include the exploitation of vulnerabilities, unauthorized access to sensitive data, and the potential compromise of critical systems. Furthermore, the stealthy nature of malware-initiated scanning attacks increases the difficulty of detection, prolonging the exposure window, and amplifying the risk of successful exploitation.
In terms of impact, a cyberattack facilitated by malware-initiated scanning from compromised hosts can have moderate consequences for an organization. If malicious activities sourcing from an organization’s network to another could have operational and legal impacts. Financially, the costs associated with mitigating the attack, recovering from data breaches, and addressing regulatory fines and legal fees can be substantial. Overall, the combined effects of financial losses, operational disruptions, and reputational harm underscore the critical importance for organizations to address and mitigate any compromised hosts within their network boundary.
Source Material: Palo Alto Unit 42, It Was Not Me! Malware-Initiated Vulnerability Scanning Is on the Rise
VenomRAT Deployed by ScrubCrypt Along with Various Plugins
Malware – Phishing – Malicious SVG Attachment – Malicious ZIP file – ScrubCrypt – VenomRAT – Remote Access Trojan- Plugins – Command and Control- NanoCore- XWorm- Remcos
Threat Analysis
The attack begins with the a phishing email asking the unsuspected user to confirm a delivery, along with an attached SVG file named “INV0ICE_#TBSBVS0Y3BDSMMX.svg.”
This SVG file contains base64-encoded data. Upon opening the SVG file, ECMAScript generates a new blob and employs “window.URL.createObjectURL” to deploy the decoded data as a ZIP file titled “INV0ICE_#TBSBVS0Y3BDSMMX.zip.” The file reveals an obfuscated batch file embedding its payload within the section labeled “——BEGIN X509 CRL—–.” The initial comment line suggests that this batch file originates from the BatCloak tool, notorious for deploying various malware strains through heavily obfuscated batch files since 2022.
The ECMAScript begins by copying a PowerShell execution file to “C:\Users\Public\xkn.exe” and utilizes this copy in subsequent commands. Each command incorporates parameters, specifically “-WindowStyle hidden -inputformat none -outputformat none -NonInteractive,” to mask its operations from the victim. It proceeds to decode the malicious data and stores it as “pointer.png,” which, after hex-decoding, is renamed to “pointer” and relocated to “C:\Users\Public\Libraries\pointer.cmd.” Upon executing “pointer.cmd,” it utilizes “cmd /c del” to erase all previously mentioned files.
The “pointer.cmd” file functions as the ScrubCrypt batch script, intentionally cluttered with numerous extraneous strings to obscure readability. Within it are two payloads encoded in Base64 format, employing AES-CBC decryption and GZIP compression for their extraction. By utilizing the PowerShell command “[System.Reflection.Assembly]::Load,” it accesses and executes the decrypted .NET assembly, initiating the execution of its code through its entry point method.
The initial payload serves two purposes: establishing persistence and loading the targeted malware. It verifies the current user’s membership in the built-in Administrator role within a Windows OS to configure persistence settings. Additionally, it checks for the presence of any debugging tools, terminating the program if detected to evade detection.
Should the user possess Administrator privileges, the program duplicates itself to “%AppData%/strt.cmd” and schedules a task named “OneNote 83701” through PowerShell. This task executes “strt.cmd” upon user login, operating with elevated privileges. If there are not any Administrator permissions, the program duplicates itself to the “StartUp” folder as “strt.cmd.”
Finally, it loads an assembly from an embedded resource labeled “P,” containing a compressed assembly, and invokes its entry point method to execute VenomRAT. The second payload within the ScrubCrypt batch script is designed for AMSI and ETW bypass functionalities.
VenomRAT
VenomRAT, a remote access Trojan (RAT) initially identified in 2020, derives from a modified version of the well-known Quasar RAT. It spreads via malicious attachments in spam emails, serving cybercriminals in unauthorized access and control of targeted systems. Similar to other RATs, VenomRAT empowers attackers with remote manipulation of compromised devices, facilitating a range of malicious activities discreetly. The core configurations of VenomRAT are Base64-encoded and AES-CBC encrypted.
Following system checks, VenomRAT establishes communication with its Command and Control (C2) server.
The initial transmission includes basic victim information, encompassing hardware specs, username, OS details, camera availability, execution path, foreground window name, and installed antivirus product. All C2 sessions use encryption with a designated certificate from its setup. Despite the apparent simplicity of VenomRAT’s primary program, it sustains communication channels with the C2 server to acquire additional plugins for various activities.
After receiving the “save_Plugin” directive, it decompresses and stores the data in the registry. The “save_Plugin” data includes a DLL file named “SendFile,” capable of parsing other “plug_in” files dispatched by the C2 server. If an existing plugin file shares the same name in the victim’s environment, it replaces it with the current data. Following decompression of the “plug_in” packet data, it analyzes the “Filename” to determine the appropriate PowerShell command for execution.
Upon reception of a “plugin” packet from the server, VenomRAT retrieves registry data for “SendFile.dll” and executes the contained payload. After receiving a “plugin” packet from the server, VenomRAT accesses the registry to retrieve the information for “SendFile.dll,” and executes the payload that is held within the plugin.
Plugin Breakdown Supplied by the VenomRAT C2 Server
Venom RAT v6.0.3
The initial plugin, integrated within ScrubCrypt, loads discreetly without leaving any execution files within the victim’s system, effectively concealing its presence. Following this, the second payload, named “ScrubBypass,” within the ScrubCrypt Batch file, uses heavy obfuscation to obscure its code flow, functions, and strings. ScrubBypass primarily focuses on patching the AMSI scan buffer and EtwEventWrite to accomplish AMSI and ETW bypass functionalities. The VenomRAT plugin, version 6.0.3, incorporates a Keylogger feature and stores its Command and Control (C2) server details on Pastebin. It gathers diverse data types, monitors the victim’s keyboard inputs, and consistently transmits stolen data to the C2 server.
NanoCore
NanoCore is a well-known Remote Access Trojan (RAT) initially detected in 2013. It has gained notoriety for its capability to remotely control a victim’s computer. Its continued prominence in cybercrime circles is attributed to the widespread dissemination of its leaked source code across underground forums. This plugin is disseminated to compromised devices through an obfuscated VBS file. The script saves the data for the next phase on the website “hxxps://nanoshield[.]pro/files,” which doubles as a Crypter service provider. Initially, it retrieves a JPG file and deciphers the targeted segment using the reversed URL as a parameter. The JPG file uses steganographic techniques to hide code within the image, hiding malware data encoded in Base64 between the markers <<BASE64_START>> and <<BASE64_END>>. Upon decoding the JPG file, a .NET executable was uncovered. This executable ensures persistence by configuring the registry key
“HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run”
and conducts checks for virtual environments. It proceeds to retrieve encoded data from the URL “nanoshield.pro/files,” reverses the data, substitutes the specific string “DgTre,” and leverages “RegAsm” to facilitate the execution of NanoCore.
XWorm
XWorm is a Remote Access Trojan (RAT) that propagates via removable drives such as USB flash drives, targeting Windows systems for infection. It has the capability to steal information or grant remote access. A file, “xwrm3.1.vbs” was discovered on VenomRAT’s C2 server. Alongside the VBS file, another “plug_in” was discovered comprising a batch script trying to initiate PowerShell commands. This script retrieves encoded data from the URL “hxxps://kisanbethak[.]com/K/Universallsningen.lpk.”
The next part of the PowerShell code is located towards the conclusion of the decoded “Universallsningen.lpk” file. Despite being filled with various extraneous comments intended to obscure analysis, the PowerShell script employs the Process Hollowing technique to infuse shellcode into a genuine process. After injection and verification of the environment, the shellcode initiates the ultimate malware, XWorm.
Remcos
Discovered in 2016, Remcos is a Remote Access Trojan (RAT), masquerading as genuine software for remote management while frequently being used for nefarious purposes. Offering threat actors full command over compromised systems, Remcos allows for the extraction of keystrokes, screenshots, credentials, and other confidential data. Commonly distributed through malicious documents or archive files, it often surfaces in phishing campaigns. This plugin was disseminated from VenomRAT’s Command and Control (C2) infrastructure via three distinct methods: an obscured VBS script dubbed “remcos.vbs,” ScrubCrypt, and Guloader PowerShell.
Stealer
Not only is this plugin distributed via the previously mentioned obfuscated VBS script, but it is also integrated into a .NET executable file obfuscated using SmartAssembly. Within this .NET executable, the next stage payload is decoded from the Resource file named “ach” and written into memory. It then duplicates itself into the TEMP folder and configures the copied file as a scheduled task named “Nano,” set to repeat every 10 minutes after the initial trigger.
The following stage payload is more direct, featuring a hardcoded array for the malicious DLL file designed to pilfer the victim’s sensitive data. This DLL file encapsulates its configuration within Base64 encoded data, encompassing the C2 hostname and the encryption certificate for communication. Continuously monitoring the user’s system, the DLL file targets specific crypto wallets, Foxmail, and Telegram data, executing the following tasks:
- Collects information regarding the victim’s system environment, including the PC name, username, antivirus software, disk details, and operating system version.
- Validates the presence of specific paths, including “%AppData%\atomic\Local Storage\leveldb,” “%AppData%\Electrum\wallets,” “%AppData%\Ethereum\keystore,” “%AppData%\Exodus\exodus.wallet,” “%AppData%\com.liberty.jaxx\IndexedDB,” “%AppData%\Zcash,” “%AppData%\Foxmail,” and “%AppData%\Telegram Desktop\Telegram.exe.”
- Checks for the existence of certain registry entries, such as “Software\Bitcoin\Bitcoin-Qt,” “Software\Dash\Dash-Qt,” and “Software\Litecoin\Litecoin-Qt.”
- Once the relevant data is gathered, it appends this information with the execution file path and sends it to the C2 server located at “markjohnhvncpure[.]duckdns.org.”
Risk & Impact Assessment
This described attack of VenomRAT malware being deployed with the ability of multiple plugins to follow poses a significant risk to organizations, characterized by its sophisticated attack methodology and diverse capabilities. The risk associated with this threat lies in its ability to infiltrate systems through phishing emails, leveraging stealth techniques such as obfuscation to evade detection. The multi-stage infection process, coupled with the deployment of various plugins, increases the likelihood of unauthorized access, data theft, and further malicious activities. While assessing the precise likelihood of this threat impacting an organization is challenging due to limited intelligence on the success rate of the phishing campaigns utilized, its complex nature and continuous development suggest a considerable risk.
The potential impact of a cyberattack facilitated such as this one is profound and wide-ranging. Financially, organizations could face substantial losses stemming from operational downtime, remediation efforts, legal expenses, and potential regulatory fines for compliance violations. The reputational damage resulting from a data breach or security incident could destroy stakeholder trust, tarnish the organization’s brand image, and lead to a loss of customers and business opportunities. Additionally, the theft or compromise of sensitive data could have long-term repercussions, including competitive disadvantage and increased susceptibility to targeted attacks. Given the combined effect of these impacts, organizations must prioritize efforts to mitigate the risks posed by VenomRAT malware and associated plugins promptly.
Source Material: Fortinet, ScrubCrypt Deploys VenomRAT with an Arsenal of Plugins
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Construction – Finance and Insurance – Information
Analysis
The landscape of data leak sites is diverse, with 14 identified in the last week. The analysis identifies Blacksuit, INC Ransom, and 8base as the dataset’s most prominently featured leak sites, indicating their pivotal roles in the cyber threat landscape.
Observing the activity on these sites offers invaluable insights into these cyber adversaries’ operational reach and influence. The prominence of “Blacksuit” and “INC Ransom” suggests a robust and persistent threat in the cyber domain, signaling the need for heightened awareness and preparedness among potential target organizations.
The number of listings on these sites reflects the aggressiveness of ransomware and data leak campaigns and highlights the diverse range of victims targeted by these groups. Understanding the distribution and emphasis of listings across these leak sites is critical for cybersecurity professionals and organizational decision-makers, as it provides a clearer view of the threat landscape and helps prioritize defensive strategies.
The analysis concerning industry distribution unveils that Manufacturing, followed closely by Professional, Scientific, and Technical Services, and Construction, stands out as the sectors most commonly represented across the analyzed leak sites. This pattern sheds light on the perceived value of the data held within these industries, making them attractive targets for cyber adversaries.
The report underscores the vital role of data-driven insights in understanding the cyber threat milieu, as evidenced by the analysis of leak site listings. While the report outlines key trends in terms of industry and geographic listings, it also cautions against overinterpreting the data without considering the broader cyber threat context. Ultimately, these findings should act as a guide, supplementing broader intelligence and strategic cybersecurity deliberations to fortify defenses against an evolving threat landscape.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed.
Additionally, we may have omitted victims we could not verify. Victims are classified based on the NAICS industry classification system. While we only list one industry classification per victim, it’s possible that a victim could fall under multiple industries classification, which may inadvertently skew results.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
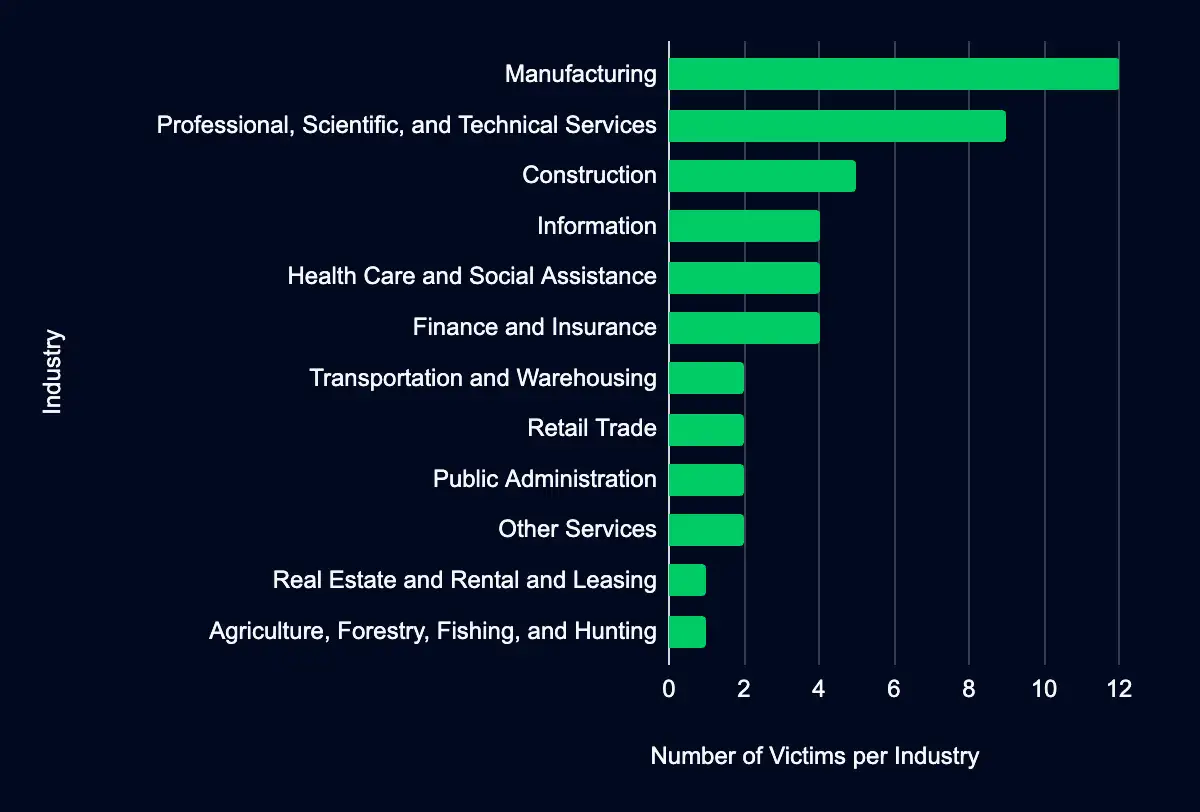
Understanding these trends is crucial for stakeholders within these industries. The prominence of Manufacturing and Professional, Scientific, and Technical Services on leak sites could indicate several risk factors, including but not limited to, the volume of sensitive or proprietary data held, the extent of digitalization and network connectivity within these sectors, or possibly the level of preparedness against cyber threats.
While the specific reasons behind the targeting of these industries remain speculative without further contextual analysis, the observed patterns underscore a clear message: entities within these sectors must prioritize cybersecurity. This entails adopting robust security measures, fostering a culture of cyber awareness, regularly assessing and updating cyber defense strategies, and preparing incident response mechanisms to address potential breaches.
For industries less represented in the data, this analysis should not breed complacency but rather serve as a call to maintain vigilance and adapt to the evolving cyber threat landscape. The dynamic nature of cyber threats necessitates a continuous, proactive approach to cybersecurity across all sectors, irrespective of their current level of representation on leak sites.
The geographic distribution of listings on identified leak sites unveils discernible patterns, with the United States leading, followed by Canada and Germany. This concentration suggests that entities within these countries may face a heightened risk of exposure in the context of data breaches and cyber threats, as evidenced by their prevalence in leak site disclosures.
CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
Android Pixel CVE-2024-29745 & CVE-2024-29748
Analysis
Within the past week, CISA added two (2) CVEs (CVE-2024-29745 and CVE-2024-29748) to its Known Exploited Vulnerabilities catalog, both impacting Google’s mobile phone Pixel. Threat actors can exploit these vulnerabilities to perform information disclosure and privilege escalation. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action by 25 April. Google has previously linked similar vulnerabilities to commercial spyware vendors.
CVE-2024-29748, which impacts Google Pixel, has a CVSS v3 score of 7.8, signifying a high severity, allowing information disclosure. Notably, Google states that this vulnerability may be under limited, targeted exploitation. However, the addition of this CVE to CISA’s Known Exploited Vulnerabilities catalog suggests that threat actor(s) are actively exploiting this vulnerability. Google’s response, involving the release of a patched firmware version on 5 April, highlights the urgency and necessity of timely updates in response to emerging threats.
CVE-2024-29745, impacting Google Pixel, has a CVSS v3 score of 5.5, signifying a medium severity, allowing information disclosure. Notably, Google states this vulnerability may be under limited, targeted exploitation. However, the addition of this CVE to CISA’s Known Exploited Vulnerabilities catalog suggests that threat actor(s) are actively exploiting this vulnerability. Google’s response, involving the release of a patched firmware version on 5 April, highlights the urgency and necessity of timely updates in response to emerging threats.
The discovery and subsequent mitigation of these vulnerabilities demonstrate a persistent challenge in network security: the need for constant vigilance and prompt response to emerging threats. The active exploitation of the vulnerabilities provides valuable insights into the evolving landscape of cybersecurity threats and defenses. It is a stark reminder of the real-world implications of such vulnerabilities, necessitating a robust and agile security posture from vendors and users alike.
In conclusion, the addition of these CVEs to CISA’s catalog highlights specific risks associated with Google Pixel but also underscores the broader theme of proactive security management in an ever-evolving digital landscape. Regular updates, strong authentication practices, and timely responses to identified vulnerabilities remain paramount in safeguarding against potential exploits and maintaining the integrity of networked systems.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share