WarzoneRAT is Back, Ransomware Has a New Agenda, XZ Backdoor Delivered by Trusted Source, and the Latest from Data Leak Sites
This week: a WarzoneRAT campaign is taken down by the FBI, Agenda Ransomware uses specialized PowerShell script to attack vCenters and ESXi, an open source software contributor plays the long con, and almost 80 new data leak victims.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
WarzoneRAT Campaign Discovered Following FBI Takedown
Malware – WarzoneRAT – Reflective loading – DLL sideloading – Command-and-Control – FBI Takedown
Threat Analysis
There were two scenarios for disseminating the WarzoneRAT (Avemaria) malware.
In the initial scenario, the infection process started with an archive file that was attached to a spam email, with the subject of the email being “taxorganizer2023.” Upon extraction of the archive file, a shortcut file masquerading as a PNG image, labeled “taxorganizer2023.png.lnk” was found. If an unsuspecting user executes this shortcut, it triggers a PowerShell command, initiating the download and extraction of an additional archive file. Subsequently, an HTA file contained within the extracted archive is executed. The HTA file, operating in memory, retrieves a PowerShell script from a remote server, which in turn downloads a VBScript file. Upon execution of the VBScript, a CMD file is deployed, executing another PowerShell script which is responsible for delivering the final payload, identified as WarzoneRAT, also known as Avemaria.
In the other scenario that was observed, a spam email attachment included a ZIP archive named “MY TAX ORGANIZER.zip,” which contained three distinct files: a genuine EXE, a malicious DLL, and a PDF file. When the user executed the legitimate EXE file, the malware employed DLL sideloading to load the malicious DLL, which was again identified as WarzoneRAT (Avemaria).
Technical Analysis
When a user mistakenly perceives an LNK shortcut file as an image file (“taxorganizer2023.png.lnk”) and executes it, the LNK file triggers the download of a PNG extension file named “taxorganizer2023.png” from a specified URL. Subsequently, it saves this PNG file with a ZIP file extension as “taxorganizer2023.zip” in the Downloads folder. After extracting the contents of the downloaded ZIP file to a designated location (C:UsersPublic), the process enters a loop to persistently verify the presence of a file named “taxorganizer2023.hta” within the directory. Upon finding the file, it executes the .hta file using Start-Process and then exits the loop. Following this, it deletes the downloaded ZIP file and forcibly terminates any active instances of Microsoft Edge (msedge.exe) and Command Prompt (cmd.exe) using taskkill.
Upon execution of the “taxorganizer2023.hta” file, it runs the VBScript code embedded within it. This VBScript code deobfuscates and retrieves a PowerShell script. The PowerShell script is then responsible for downloading a VBScript file named “Memory.vbs” from a specified URL and saving it in the root of the %appdata% directory, subsequently executing it using WScript.exe.
When the “Memory.vbs” file is executed, it performs several actions, including invoking functions, verifying the username, examining running processes, creating directories, retrieving PowerShell scripts, and setting up persistence mechanisms. From this two files are created within the Windows startup folder to maintain persistence. : “ORHYY.vbs” and “WindowsServices-VAQVU.lnk:. The shortcut file includes a target command-line to execute the “ORHYY.vbs” file, which contains a code that incorporates a sleep operation. This initiates the execution of the “VROLX.cmd” file that is located within the %appdata%\WindowsServices directory. The script then launches the “VROLX.cmd” file, consequently executing the PowerShell script “BTYSA.ps1.”
Finally, the PowerShell script “BTYSA.ps1” is executed, which involves copying the “RegSvcs.exe” file, de-obfuscating embedded content, dynamically loading the .NET injector payload, and injecting the main WarzoneRAT (Avemaria) malware payload into the “RegSvcs.exe” process. The script also includes additional PowerShell scripts that perform various tasks such as bypassing security measures, configuring Windows Defender, adjusting system preferences, and disabling Windows Firewall.
WarzoneRAT, also known as Avemaria, is a Remote Access Trojan (RAT) engineered to access and manipulate a victim’s computer system remotely. This malicious software empowers threat actors to carry out an array of unauthorized operations within the compromised system. Its malicious functionalities include but are not limited to data theft, privilege escalation, remote desktop manipulation, harvesting of email and browser credentials, keylogging, and other invasive activities.
Risk & Impact Assessment
The resurgence of WarzoneRAT (Avemaria) poses substantial risks to organizations and individuals. Tax-themed spam emails during the months of March and April can be especially effective for threat actors due to users believing they are legitimate emails. WarzoneRAT’s remote control capabilities also enable threat actors to access and exfiltrate sensitive information, compromising confidentiality and integrity.
Malicious activities facilitated by WarzoneRAT, such as privilege escalation and system manipulation, can disrupt organizational operations and impair business continuity. Successful infections of the RAT malware can result in financial losses stemming from data theft and remediation efforts and possibly ransom demands if ransomware was deployed after the malware initial infection.Incidents involving malware infections can damage an organization’s reputation, which can break trust among stakeholders and customers.
Source Material: Cyble, WarzoneRAT Returns with Multi-Stage Attack Post FBI Seizure
Agenda Ransomware Spreads to vCenters and ESXi through Specialized PowerShell Script
Agenda Ransomware – Qilin – VMWare vCenter – VMware ESXi – PowerShell- Ransomware
Threat Analysis
Agenda Ransomware, also identified as Qilin, has emerged as a significant cyber threat targeting virtualization infrastructure such as vCenters and ESXi servers. The ransomware spreads through a customized PowerShell script, posing serious risks to organizations’ data integrity and operations. The Agenda Ransomware group utilizes Remote Monitoring and Management (RMM) tools, alongside Cobalt Strike, to deploy ransomware. Additionally, the Agenda ransomware executable can spread through PsExec and SecureShell, exploiting various vulnerable SYS drivers for evading detection. The latest iteration of the Agenda ransomware incorporates various commands, some of which have changed from previous versions. When initiated using the command-line argument –spread-vcenter, Agenda employs a specialized PowerShell script integrated into the binary to disseminate across VMWare vCenter and ESXi servers. This has the potential to affect virtual machines and the entire virtual infrastructure, resulting in data and financial losses, as well as service disruptions within virtual environments.
In order to operate, Agenda requires users to input their credentials within the targeted vCenter or ESXi host, and to specify the path of the ESXi binary for propagation. Given that this occurs within an interactive shell, it suggests that threat actors may be the individuals inputting these credentials into the system upon deployment. The PowerShell script runs in-memory within an active PowerShell process, making its execution fileless, as the script itself will not be on the machine.
The script then checks if the dependencies are installed.It continues by establishing connections to the host names designated by the attacker and alters the root password for all ESXi hosts. The new password aligns with the one mandated by Agenda for execution. This effectively stops victims from accessing the compromised host even after encryption has been completed. File transfer would be enabled by SSH. After enabling SSH, it would continue to establish an SSH session, which would then be utilized for uploading the ESXi binary. After it is successfully uploaded the payload would be executed on the target machine, leading to a compromise of the system.
Risk & Impact Assessment
The deployment of Agenda ransomware onto VMWare vCenters and ESXi servers poses severe risks to organizations, including Data loss or encryption,which can lead to operational disruptions and financial losses The Compromise of sensitive information from employees and customers can impact regulatory compliance and reputational damage. The potential extortion demands from threat actors after ransomware is planted within a network can create financial strain and legal repercussions. The disruption of critical services and infrastructure can affect business continuity and customer trust.
Source Material: Trend Micro, Agenda Ransomware Propagates to vCenters and ESXi via Custom PowerShell Script
XZ Backdoor Discovered within CVE-2024-3094
CVE-2024-3094 – XZ Utils – Vulnerability Exploitation – Backdoor
Threat Analysis
On March 29th, reports emerged regarding the discovery of malicious code within XZ Utils, a widely deployed package found in major Linux distributions. This malicious code facilitated unauthorized remote SSH access. Notably, the GitHub project hosting this code is now suspended. Fortunately, the open-source community quickly identified the malicious code, which managed to infect only two recent versions of the package, 5.6.0 and 5.6.1, both released within the past month. It’s essential to note that stable versions of most Linux distributions remained unaffected.
The malicious payload accompanying the impacted XZ Utils versions operated within the same process as the OpenSSH server (SSHD). It tampered with decryption routines within the OpenSSH server, allowing specific remote attackers, having a particular private key, to transmit arbitrary payloads via SSH. These payloads were executed prior to the authentication step, effectively seizing control of the entire victim machine.
This supply chain attack came as a surprise to the open-source software (OSS) community, as XZ Utils had long been regarded as a trusted and thoroughly scrutinized project. The attacker had built a credible reputation as an OSS developer over multiple years. Moreover, the attacker employed highly obfuscated code to evade detection during code reviews, heightening the surprise and impact of the attack.
Due to the sophisticated nature of this attack and the use of highly future proof crypto algorithms (Ed448 vs the more standard Ed25519), it is probable that the attack may be related to a nation-state threat actor. The payload structure was observed as the following:
1. The payload is injected into the OpenSSH server (sshd process) due to liblzma, which contains the malicious code, being a dependency of specific builds of OpenSSH.
2. The payload intercepts the RSA_public_decrypt function, initially designed for RSA signature validation.
3. The malevolent interception code scrutinizes the RSA public modulus (“N” value) transmitted within the RSA struct (4th argument of RSA_public_decrypt). It’s important to note that this modulus is entirely controlled by the connecting SSH client, in this case, the attackers.
4. The nefarious interception code decrypts the last 240 bytes of the “N” value utilizing the ChaCha20 symmetric stream cipher, employing a hardcoded decryption key:
0a 31 fd 3b 2f 1f c6 92 92 68 32 52 c8 c1 ac 28
34 d1 f2 c9 75 c4 76 5e b1 f6 88 58 88 93 3e 48
As this key is hardcoded and symmetric, it can facilitate the decryption of network captures from actual attack attempts, providing insight into the commands transmitted from the attacker to the victim.
5. The decrypted information consists of 114 bytes of signature, which undergo validation through the application of the Ed448 asymmetric elliptic curve signing algorithm, using the specified Ed448 public key:
0a 31 fd 3b 2f 1f c6 92 92 68 32 52 c8 c1 ac 28
34 d1 f2 c9 75 c4 76 5e b1 f6 88 58 88 93 3e 48
10 0c b0 6c 3a be 14 ee 89 55 d2 45 00 c7 7f 6e
20 d3 2c 60 2b 2c 6d 31 00
Although the public key is known, only the attackers possess the corresponding Ed448 private signing key, guaranteeing that only they can produce legitimate payloads for the backdoor. Additionally, the signature is tethered to the host’s public key, indicating that a valid signature for one host cannot be utilized on another host.
6. Following the signature bytes is a NULL-terminated payload string (shell command). Upon successful verification of the signature, the payload string is executed as a shell command by directly passing it to system().
7. In the event of invalid data (such as a malformed payload or invalid signature), the original functionality of RSA_public_decrypt is seamlessly resumed. Consequently, detecting vulnerable machines over the network may be unfeasible for anyone other than the attackers.
The notable aspect of this supply chain attack lies in the attacker’s remarkable dedication, investing over two years to establish a credible presence as a legitimate maintainer. They actively volunteered to contribute to various open-source software (OSS) projects and consistently committed code across multiple projects, all in an effort to evade detection. The timeline has been identified below:
2021 – The GitHub user Jia Tan (JiaT75) created their account and commenced contributing to numerous projects. Throughout the year, JiaT75 made 546 commits, with the most dubious one being the libarchive project. Further details on this particular commit are provided below.
February 6th, 2022 – The user JiaT75 submitted their initial (legitimate) commit to the XZ repository. This commit focused on enhancing arguments validation for the LZMA and LZMA2 encode
June 27-28, 2023 – A series of modifications were implemented in XZ Utils, potentially laying the groundwork for an attack. Notably, support for ifunc implementation was integrated into crc64_fast.c. Interestingly, this patch was introduced by the original maintainer of the package, Lasse Collin, who credited Hans Jansen as the contributor. Andres Freund’s analysis suggests that this ifunc implementation might be one of the methods employed by the backdoor.
July 8, 2023 – JiaT75 initiates a Pull Request in oss-fuzz, a project dedicated to performing fuzz testing on XZ and other open-source software projects. This PR disables ifunc fuzzing, effectively hindering oss-fuzz from detecting the malicious alterations made in XZ.
February 15, 2024 – JiaT75 adds an ignore rule for build-to-host.m4 in the XZ repository’s .gitignore file. This script, soon to be included in actual release bundles, is executed during the package’s build process and contains malicious M4 macros that facilitate the installation of the backdoor on the victim’s machine.
February 23, 2024 – JiaT75 embeds the obfuscated binary backdoor into two test files within the XZ repository: tests/files/bad-3-corrupt_lzma2.xz and tests/files/good-large_compressed.lzma.
February 24, 2024 – JiaT75 releases version 5.6.0 of XZ Utils, which includes the malicious build-to-host.m4. At this stage, the malicious payload is fully functional, compromising any subsequent versions of XZ. Debian, Gentoo, and Arch Linux pull the malicious xz-utils version 5.6.0.
February 27, 2024 – Fedora withdraws the malicious xz-utils version 5.6.0.
March 5, 2024 – openSUSE removes the malicious xz-utils version 5.6.0.
March 9, 2024 – JiaT75 updates the backdoor’s binaries to an enhanced version and releases xz-utils version 5.6.1. This version is pulled by Fedora, Gentoo, and Arch Linux.
March 10, 2024 – openSUSE pulls the malicious xz-utils version 5.6.1.
March 11, 2024 – Alpine pulls the malicious xz-utils version 5.6.1.
March 26, 2024 – Debian pulls the malicious xz-utils version 5.6.1.
March 29, 2024 – Andres Freund publishes a comprehensive report detailing the malicious activity discovered in XZ utils on the oss-security mailing list.
March 30, 2024 – Lasse Collin, the original maintainer of xz-utils, issues an official announcement regarding the project’s compromise.
Risk & Impact Assessment
The CVE-2024-3094 vulnerability presents a significant risk to organizations, considering its potential for unauthorized remote access and arbitrary code execution on affected systems. The risk is elevated due to the exploitation of XZ Utils, a widely used package in major Linux distributions, which increases the attack surface and likelihood of successful exploitation. Furthermore, the sophistication of the attack, including interception of RSA encryption and obfuscated payload delivery, indicates a determined threat actor with advanced capabilities. While the exact likelihood of exploitation is challenging to determine, given the nature of the vulnerability and the availability of exploit details, organizations should consider the risk of exploitation as moderate to high.
A cyberattack exploiting CVE-2024-3094 could have severe impacts on organizations, both operationally and financially. Operationally, the unauthorized remote access and code execution capabilities granted by the vulnerability could lead to system compromise, data exfiltration, and further malicious activities within the network. Additionally, the exploitation of XZ Utils, a trusted and widely used package, could destroy trust in the integrity and security of open-source software, affecting the broader OSS community.
Financially, the impacts of a successful attack could be substantial, including costs associated with incident response, system remediation, and potential legal fees or fines resulting from compliance violations. Moreover, the reputational damage resulting from a security compromise could lead to loss of customer trust, damaged brand reputation, and ultimately, loss of business opportunities. The long-term implications of data theft or compromise could extend beyond immediate financial losses, impacting competitive advantage and regulatory compliance efforts.
The combined effect of these risks underscores the critical importance for organizations to prioritize remediation efforts and implement robust security measures to mitigate the threat posed by CVE-2024-3094. Failure to address this vulnerability promptly could leave organizations vulnerable to exploitation and subject to significant financial, operational, and reputational consequences.
Source Material: Jfrog, Zscaler, NIST
Latest Additions to Data Leak Sites
Information – Manufacturing – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Retail Trade – Transportation and Warehousing – Finance and Insurance – Educational Services
Overview
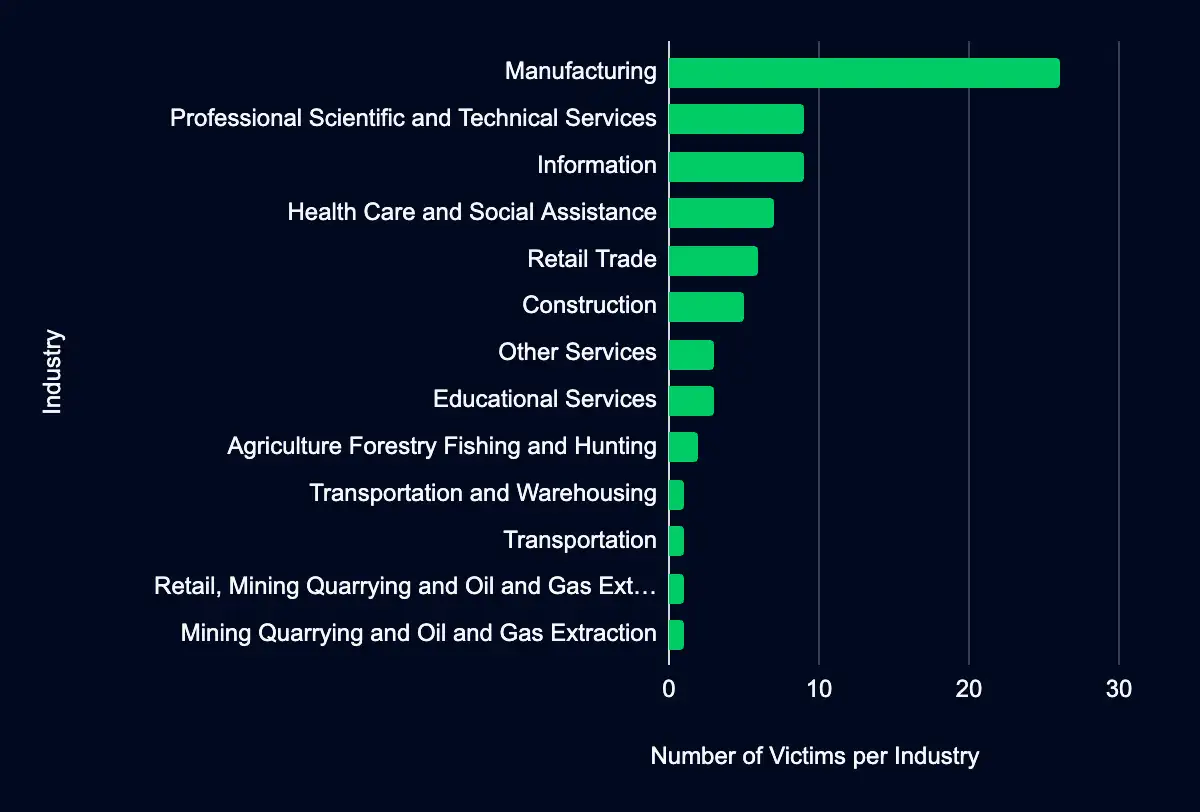
Over the past week, seventy-eight (78) new organizations were identified on data leak sites, impacting various industries, with the Manufacturing sector being the most involved, representing 33% of the organizations listed operating in this sector. The Professional Scientific and Technical Services sector follows with 12% of the total organizations listed. Geographically, most organizations listed are headquartered in the United States, accounting for 68%.
Regarding monitored leak sites, the data leak site operated by the Blackbasta ransomware group is observed as having the most organizations added, contributing to 22% of the reported leaks.
Analysis
The landscape of data leak sites is diverse, with fourteen significant data leak sites identified in the last week. Blackbasta’s leak site leads with 22% of the incidents, followed by Play at 18%, Lockbit at 17%, and Incransom at 8%. Other notable sites include Bianlian and Ransomhub, each with 5% of the incidents. The remaining sites, Akira, 8base, Dragonforce, Rhysida, Abyss, Everest, and Cactus contribute to a smaller fraction of the leaks but are still integral players in the ransomware and data extortion threat landscape.
The United States stands out as the most listed country, with 68% of the organizations headquartered in this region, underscoring its prominence in the threat actors’ focus Germany, Australia, and Mexico also appear next in line, indicating a diverse geographical spread in the organizations listed on these data leak sites.
The most active data leak site in the recent dataset is operated by the Blackbasta ransomware group, accounting for 17 of the 78 new additions. Blackbasta’s recent additions feature a broad array of industries, with a notable emphasis on Manufacturing (47%), Retail Trade (24%), and Professional Scientific and Technical Services (6%). These sectors are followed by Information, at 6%. This distribution suggests that Blackbasta does not limit its operations to traditionally high-value targets like finance or healthcare but adopts a more opportunistic approach, potentially exploiting specific vulnerabilities in these sectors.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed.
We have omitted victim organizations we could not verify via open-source research. Additionally, victims are classified based on the NAICS industry classification system. While we only list one industry classification per victim, it’s possible that a victim could fall under multiple industry classifications, which may inadvertently skew results.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share