Infostealer Circulated Through Facebook, Magnet Goblin Deploys Malware, PLUS 3 Common Post Network Device Tactics and eRAT
This week: Python-based infostealer, Snake, gets deployed via Facebook Messenger, Magnet Goblin exploits vulnerabilities to deploy malware, a look into the 3 most common post network device compromise tactics, and an eRAT phishing campaign gets delivered – all this and over 40 new data leak victims.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Snake, A Python-based Infostealer Previously Distributed via Facebook Messenger
- Magnet Goblin Exploits 1-Day Vulnerabilities to Deploy Nerbian Malware Family
- The 3 Most Common Post Network Device Compromise Tactics
- Phishing Campaign Delivers New Remote Access Trojan (RAT)
- Latest Additions to Data Leak Sites
- CISA Adds CVE-2024-27198 to Known Exploited Vulnerabilities Catalog
Snake, A Python-based Infostealer Previously Distributed via Facebook Messenger
Malware – Infostealer – Phishing – Vietnamese Threat Actor – Snake Infostealer – Python Scripting – Social Media Messages – GitLab – Telegram Bot API – Industries/All
Threat Analysis
According to Cybereason, the threat actor maintains three different infostealer variants, dubbed Snake. Based on their analysis, the main differences between the variants are that variants 1 and 2 are regular Python scripts. In contrast, the third variant is an executable assembled by PyInstaller. While the infection chains for all three variants are similar, the infection chain described below is specific to the most recent infection chain employed by variant one.
In one previously observed infection chain, the threat actor sent direct messages via Facebook messenger, targeting businesses with fake complaints or business opportunities. The Facebook message lures victims into downloading archived files, such as RAR or ZIP files, which executes a two-stage infection chain, ultimately resulting in an unidentified infostealer infection.
The archived file initiates the first stage, which contains a batch script that attempts to download a ZIP archive named achung3.zip via the cURL command, placing the downloaded archive under the directory C:\Users\Public, renaming it as myFile.zip. Then, the batch script spawns the PowerShell command “Expand-Archive” to extract the batch script vn.cmd from within the ZIP archive.
The batch script vn.cmd initiates the second stage, a downloader responsible for downloading and executing the Snake Infostealer. At the beginning of this script, there are various “set” commands configuring a variable to a specific character, typically to deobfuscate the code at run time. However, this version appears to have no obfuscation. In other versions of the second stage downloader vn.cmd, the script utilizes this obfuscation, indicating obfuscation is version-dependent.
Next, the vn.cmd script opens Google Chrome to the homepage of the Chinese E-Commerce site Alibaba. Then, three files are downloaded from GitLab. The first file is renamed WindowsSecure.bat and saved to the Startup Folder. This batch script maintains persistence on the victim’s machine by executing the third file (Snake Infostealer) every time a user logs in.
The second file, renamed Document.zip, is an archived file containing bundled Python packages. These packages enable the execution of the third file without the victim’s machine needing to have the required Python packages installed.
The third file, renamed Project.py, is the obfuscated Snake Infostealer responsible for harvesting credentials from various browsers. Once the download is complete, the vn.cmd script then proceeds to execute Snake Infostealer with the Python module extracted from Document.zip.
As mentioned previously, there are three variants of the Snake Infostealer. The first variant is the Python script named project.py, discussed above. This variant (Variant 1) contains nested obfuscation, in which the hex value is compressed with various compression methodologies.
Variant 1 identifies the victim’s machine location by creating an HTTP(S) request to ipinfo[.]io. This IP data provider correlates IP addresses to their geolocation, retrieving the country and IP address of the machine. Once Variant 1 retrieves the victim’s machine location, it begins to harvest credentials. First, it identifies the relevant directory paths of browsers within the victim’s machine, specifically targeting seven different browsers, such as Google Chrome, Microsoft Edge, and Mozilla Firefox.
Then, Variant 1 dumps the cookies and credentials from the browsers to the disk and copies it to potentially three different files, cookiefb.txt, cookie.txt, and password.txt, saved in folders in the temp directory. Aside from cookies and credential information, Snake Infostealer also dumps cookies for Facebook, saving them to the cookiefb.txt file.
Then, it archives these files into a ZIP archive with the naming convention country + ip address.zip. Then, it attempts to exfiltrate the archived file via Telegram Bot API’s sendDocument, which allows the API to send general files. Variant 1’s main() function appears to contain two sendDocument API calls with different bot tokens and chat IDs, indicating the ZIP archive is sent to two different chat rooms. In addition, the methodologies for executing this POST request are also different.
The second Snake Infostealer variant (Variant 2) attempts to achieve the same goal of harvesting credentials stored in the victim’s browsers. While Variant 2’s infection chain is similar to Variant 1’s, it differs in downloading Snake Infostealer. In addition, the second stage batch script downloads the three files, Lib-jae.py, obfuscated Snake Infostealer; Python39.zip, a Python module package; and WindowsSecure.bat, a batch script for persistence saved to the Startup folder.
Variant 2’s initial payload is staged, and its execution fetches the final base64 payload from the command and control (C2) infrastructure, a GitHub or GitLab repository. Once the fetch is successful, the execution decodes the base64 final payload and implements the class RitCucki.
The Python class RitCucki also depends on the strings stored in a file scriptcall, fetching the scriptcall from the same GitHub repository as the final Python payload. This additional obfuscation step can hinder the analysis if one of the files is missing. Even with the final stage payload, it’s difficult to determine the script’s intention without the file containing a set of strings.
Additionally, compared to Variant 1, this variant has a few notable script structure differences. Unlike Variant 1, Variant 2’s Python script content is Object-Oriented Programming (OOP) based code. Variant 2 also utilizes a RitCucki class that is responsible for preparing and conducting credential harvesting from the relevant Browsers. The contents of the code appear deliberately muddled in comparison to Variant 1, as many of the instance methods and variable names are less intuitive and likely used to obfuscate the code.
Another modification from Variant 1 is that this variant only identifies three browsers, Coc Coc Browser, Google Chrome, and Microsoft Edge.
Similar to Variant 1 and 2, the third Snake Infostealer variant (Variant 3) utilizes multiple downloaders to deploy the infostealer. However, unlike Variant 1 and 2, Variant 3 is a Python Executable, which appears to be assembled by PyInstaller. PyInstaller assembled executables are larger than the average executable, and Variant 3’s size is over 13 MB.
The decompiled main script is the same as Variant 2’s staged payload, where it attempts to download a Python script containing the RitCucki class, suggesting that Variant 3 is the executable version of Variant 2. This is also evident from the code in the instance method called “critduplicatetzz” in the RitCucki class, which contains commented-out code responsible for creating persistence within the environment for an executable version of this Python infostealer. It appears that the developer of Variant 2 intended for threat actors to have the option to choose between script or executable format.
All three Python Infostealers aim to steal stored credentials in targeted browsers. However, there are several critical differences between the three variants.
Variant 1 is distinct in its use of a GET request to ipinfo[.]io for geolocation, obfuscating data via compression, and singularly targeting browsers like Brave, Chromium, Mozilla Firefox, and Opera. Variants 2 and 3 share obfuscation of function and variable names and the use of staged payloads, showcasing advanced evasion and delivery techniques. Unique to Variant 3 is its bundling by PyInstaller, marking a different assembly approach.
Despite these differences, all variants share common traits: they do not require locally installed Python packages, ensure persistence through the Startup Folder, and target a range of browsers, including Coc Coc, Google Chrome, and Microsoft Edge, highlighting a unified objective to harvest data across popular platforms while exhibiting variant-specific operational nuances.
According to publicly available information, Variant 2 was first discovered in February 2023, while Variant 1 was discovered in June 2023. It is possible that Variant 2 was the original version, with Variant 1 being the latest version of the Snake Infostealer. If Variant 1 is indeed the most recent version, this could explain the increase in the number of browsers Variant 1 targets.
While we have described one observed infection chain, there are variations in the infection chains, including:
- Alternatives to the primary Snake Infostealer command control (C2) locations, such as GitHub or GitLab, include uncommon non-file sharing domains. However, threat actors have also been observed utilizing Google Workspace.
- While many Snake Infostealer downloaders are BAT or CMD scripts, there are other variations, such as executables, malicious Microsoft Documents, malicious MSI files, or VBScript.
- While recent Snake Infostealers, especially Variant 1, utilize Telegram Bot API to exfiltrate credentials, not all do. Exfiltration to Discord or other C2 servers listed in the host file stored in GitLab or GitHub has been observed.
- In Variant 1, the Python script is embedded with code to remove the Snake Infostealer-related scripts. However, different versions of Variant 1 rely on downloading another Python script, rmv.py, dedicated to deleting the files. Variants 2 and 3 do not appear to remove evidence at this time.
- As described above, Variant 1 relies on two downloader BAT scripts before downloading Snake Infostealer. However, some rely only on the Stage Two file, which attempts to download Python Infostealer immediately.
Regarding the actors behind Snake Infostealer, some evidence may suggest that the developer(s) or affiliates are Vietnamese-speaking individuals. Some of the BAT scripts observed in the analysis contain the Vietnamese language. Additionally, the indicator removal Python script rmv.py also contains comments written in Vietnamese.
The threat actor also utilizes naming conventions that suggest close ties to the Vietnamese language. For example, Variant 1 contains function names indicating that this may have been developed by a Vietnamese-speaking threat actor.
Some GitHub and GitLab repository names or account names utilize Vietnamese naming conventions. For example, one of the GitLab account aliases was Khoi Nguyen, which appears to be a common name in Vietnam and a common alias used within the community. Some Snake Infostealer file names also utilize generic Vietnamese names, like hoang.exe or hoangtuan.exe.
Furthermore, all variants target the Coc Coc Browser, a well-known Vietnamese Browser used widely by the Vietnamese community. The choice of this browser also indicates that there is or was a demand to target the Vietnamese community, especially for Variants 2 and 3, as it is assumed they are earlier variants and only target three browsers, including Coc Coc Browser.
Risk & Impact Assessment
The Snake Infostealer poses a considerable risk to organizations, given the potential for various infection chains and the ability to harvest credentials. The risk associated with Snake Infostealer is notably high due to its multi-variant nature, demonstrating the threat actor’s commitment to evolving tactics to evade detection and enhance success rates.
Employing multiple infection chains, including social media platforms for initial contact and multiple downloaders, increases the likelihood of successful infiltration. The varying obfuscation techniques across its versions further complicate detection efforts, thereby improving the potential for this infostealer to impact targeted organizations.
The impact of Snake Infostealer on an organization can be severe, given its primary function to exfiltrate sensitive credentials. If successful, the infostealer can lead to unauthorized access to critical systems and confidential data, posing significant risks. Financial repercussions may include the cost of incident response and potential regulatory fines. The reputational damage from such a breach could lead to lost business, decreased customer trust, and tarnished business relationships.
Moreover, strategically targeting organizations through Facebook Messenger and widely used browsers commonly used within corporate environments to steal credentials could result in a threat actor accessing a wide array of valuable data, amplifying its impact on an organization’s operational security and competitive standing.
Source Material: Cybereason, Unboxing Snake – Python Infostealer Lurking Through Messaging Services
Magnet Goblin Exploits 1-Day Vulnerabilities to Deploy Nerbian Malware Family
Vulnerability Exploitation – Threat Actor – Malware – Credential Theft – Magnet Goblin – Nerbian Malware – WARPWIRE – Ligolo – Ivanti Connect Secure CVE-2023-46805 & CVE-2023-21887 – Magento CVE-2022-24086 – Qlik Sense CVE-2023-41265, CVE-2023-41266 & CVE-2023-48365 – Industries/All
Threat Analysis
On 10 January 2024, Ivanti published a security advisory regarding two vulnerabilities (CVE-2023-46805 and CVE-2023-21887) in Ivanti Connect Secure VPN. Numerous threat actors quickly adopted these vulnerabilities, resulting in a wide range of malicious activities, which we have reported in this Customer Advisory. Check Point’s tracking of Ivanti Connect Secure VPN appliances’ exploitation activity led them to identify a distinct threat activity cluster, which Check Point tracks as Magnet Goblin.
Magnet Goblin, a financially motivated threat actor, uses a custom malware family called Nerbian. This family includes NerbianRAT, a cross-platform RAT with versions for Windows and Linux, and MiniNerbian, a small Linux backdoor. Based on Check Point’s analysis of the Linux version of NerbianRAT, other previously unattributed attacks appear to be linked to Magnet Goblin.
These previously unattributed attacks described by other security vendors all showed a clear methodology of quickly adopting 1-day vulnerabilities, including Magento vulnerability CVE-2022-24086 and Ivanti Connect Secure vulnerabilities CVE-2023-46805 chain with CVE-2024-21887 and CVE-2024-21888 chained with CVE-2024-21893. Evidence also links Magnet Goblin to the exploitation of Qlik Sense vulnerabilities CVE-2023-41265, CVE-2023-41266, and CVE-2023-48365, but this evidence is weaker.
Magento Exploitation Campaign
Throughout 2022, Magnet Goblin targeted Magento servers and, in some cases, leveraged them as command and control (C2) servers for other campaigns. To establish a foothold in compromised Magento servers, the operators deployed MiniNerbian. Foregenix and Sansec linked Magento exploitation attacks in September 2022 to MiniNerbian variants, suggesting they were financially motivated. The Sansec report provides one example of how the operators leveraged CVE-2022-24086: a MiniNerbian installation command was inserted into the sales_order_address table.
Ivanti Exploitation Campaign
In this campaign, conducted in January 2024, Magnet Goblin actors downloaded and deployed the Linux version of NerbianRAT. In this threat activity cluster, described in a Darktrace report, the actors also downloaded various payloads from actor-controlled infrastructure, including a custom variant of the WARPWIRE JavaScript credential stealer and Ligolo, an open-source tunneling tool. Following the exploitation, the NerbianRAT Linux version was downloaded from three actor-controlled servers (http://94.156.71[.]115/lxrt, http://91.92.240[.]113/aparche2, and http://45.9.149[.]215/aparche2) and contacted the IP 172.86.66[.]165.
WARPWIRE Credential Stealer
WARPWIRE, a stealer recently disclosed by Mandiant, is quite simple and sends VPN credentials to an external server over HTTP requests. The leaked VPN credentials are sent to a potentially compromised Magento server in the variant attributed to Magnet Goblin. However, WARPWIRE appears to be used by more than one threat actor.
Infrastructure Analysis
Analysis of the malware infrastructure involved in the Magneto and Ivanti campaigns reveals several other tools Magnet Goblin actors employ. Some of those are described in other reports and include additional tools for Linux, such as the tunneling tool Ligolo. However, Magnet Goblin’s arsenal is not limited to Linux.
Their Windows tools appear to include the Remote Monitoring & Management tool (RMM) software ScreenConnect, downloaded from an actor-controlled server, which has been associated with the exploitation of Qlik Sense, leading to the download of similar tools, including ScreenConnect and AnyDesk.
In addition to possible links to the Qlik Sense exploitation, other files visible on Nerbian-associated servers suggest the actors likely attempted to exploit Apache ActiveMQ servers. This is demonstrated in an XML file downloaded from the server, which matches the format of the ActiveMQ remote XML used to trigger the exploitation.
BAT deployment scripts also showed other ties to Anydesk usage, utilizing a compromised Magento server. This BAT script downloads and executes AnyDesk and was downloaded from another server, which is also associated with ScreenConnect payloads.
The Nerbian Malware Family
NerbianRAT was first publicly disclosed by Proofpoint on 11 May 2022, with two samples submitted to VirusTotal in the same month. Proofpoint’s report details the delivery of the Windows version via COVID-19 phishing lures used to target a limited number of organizations, mainly located in Europe. Like other Magnet Goblin tools, the Windows version utilizes a compromised Magento server as a C2. While the goal of this campaign isn’t clear, it was distributed using a domain (who-international[.]com) that is possibly associated with other cybercrime campaigns.
Upon its initial execution, NerbianRAT goes through a duplicate process check; if it succeeds, it forks itself, which is the only anti-debugging/anti-analysis trick embedded within the RAT. Following this check, NerbianRAT begins the main initialization process.
In its initialization, the malware follows several steps to collect basic information, generate a bot ID, load a hardcoded IP address into two global variables, decrypt the global working directory variable and set it as %TEMP%, search for the file rgs_c.txt, read its contents and try to parse it, and, finally, load a public RSA key that is later used to encrypt the network communication.
After its initialization, NerbianRAT loads its configuration from the file tmp/debconf.socket. The configuration contains a broad set of values, demonstrating the threat actor’s efforts to customize the backdoor. The NerbianRAT Linux version’s configuration is similar to the Windows version.
Much of the configuration is dedicated to the malware C2 mechanisms, determining its hours of activity, how often it reaches out to its C2 server, and similar functions. For example, there are parameters to start and end the work time, which are used to determine the hours in which NerbianRAT attempts to connect to its C2 server. After loading the config file, it proceeds to communicate with its C2.
Unlike the Windows version, the Linux NerbianRAT utilizes raw TCP sockets for its C2 communication, sending data blobs back and forth in a custom protocol. This means that the C2 server logic is also rewritten to communicate with this version of the backdoor. AES encryption is the primary encryption used when communicating with its C2 server. However, depending on the data transmitted, RSA can also be leveraged.
The malware can run in two states, during or outside working hours. If the time is during working hours, it sends the C2 the same data mentioned above. If the server approves that data, it sends a valid action for the backdoor to execute. If the time is outside the working hours stated in the config, but an alive signal field is set, it continuously sends a ping to the C2 server containing the data collected earlier and some of the config fields.
Conditions must be met for the buffer received from the C2 server to be valid. If all of those conditions are met, the data is parsed and will result in one of several actions, such as running a Linux command, sending the last command’s result and cleaning up the result file, or updating the start and end worktimes and saving the config file.
The diverse actions available to the operators allow for greater flexibility to operate at different times and levels of complexity. This enables the malware to remain stealthy yet active on the infected machine.
MiniNerbian is a simplified version of NerbianRAT with one primary function — command execution. Its code appears to be shared with NerbianRAT. However, MinNerbian isn’t simply a stripped-down version of NerbianRAT with some parts excised but rather a new malware strain with similar functions, such as the encryption libraries and string decryptions.
MiniNerbian has a small configuration, consisting of only 4 fields, such as the sleep time between requests, whether to make requests all day or only at certain hours, and which command and control (C2) server to use.
One of the main differences is the MiniNerbian communication method, which uses HTTP and passes data by sending POST requests to the C2’s /dashboard/ endpoint. In contrast, NerbianRAT sends data over raw sockets.
MiniNerbian supports only three “actions,” a request command from the C2 is executed and returned to the server, updating its internal time flag, with two possible returns to the C2 depending on the flag state, working for the whole day or only at certain times, and finally, updating its configuration.
Risk & Impact Assessment
The exploitation of one-day vulnerabilities by Magnet Goblin presents a considerable risk to organizations. The risk level associated with this threat actor is heightened due to its demonstrated capability to swiftly leverage newly disclosed vulnerabilities, as seen in its recent campaign exploiting Ivanti Connect Secure VPN and Magento vulnerabilities in 2022.
Furthermore, Magnet Goblin targets vulnerable publicly facing servers, increasing the risk for organizations with exposed assets and suggesting a strategic and persistent threat to capitalize on any delay in vulnerability remediation.
Given its history, opportunistic approach, and proven success in exploiting these vulnerabilities before widespread patching, Magnet Goblin will likely target organizations with vulnerable, publicly-facing servers, necessitating organizations to prioritize the swift patching of exposed servers.
The impact of an attack by Magnet Goblin on an organization can be multifaceted and severe. Financially, the consequences could be substantial, involving direct losses from theft, costs associated with incident response, and potential regulatory fines, significantly if personal or sensitive data is compromised. Operational impacts could include disruption of services, the necessity for system restoration, and the loss of availability, all of which could lead to significant downtime. From a reputational standpoint, being a victim of such a targeted attack could undermine stakeholder confidence, lead to loss of customers, and negatively affect market position.
Additionally, the potential for further malicious activities, such as credit card information theft, data exfiltration, or lateral movement within the network, could pose long-term security risks and necessitate comprehensive and costly security overhauls. Given these risks and impacts, organizations must recognize the threat posed by Magnet Goblin and take proactive measures to mitigate their attacks.
Source Material: Checkpoint, MAGNET GOBLIN TARGETS PUBLICLY FACING SERVERS USING 1-DAY VULNERABILITIES
The 3 Most Common Post Network Device Compromise Tactics
Network Device Compromise – Vulnerability Exploitation – Threat Actor – Malware – Network Device Firmware Modification – SNMP Reconfiguration – Cisco IOS XE Software CVE-2023-20198 & CVE-2023-20273 – BadCandy – BlackTech – Chinese Threat Actor – Industries/All
Threat Analysis
Cisco Talos has observed several ransomware groups and Advanced Persistent Threat actors (APTs) continuing to exploit network devices to gain initial access. Advanced Persistent Threat actors (APTs) use highly sophisticated tactics to exploit network devices for espionage purposes. However, some of these attacks are likely aimed at pre-positioning actors for future attacks, such as disruptive or destructive attacks. While ransomware threat actors exploit network devices to gain initial access and extort their victims.
These attacks are mainly carried out on aging network infrastructure devices that have long since reached end-of-life, have critical unpatched vulnerabilities sitting on them, or both. Unfortunately, many of these older devices weren’t designed with security in mind. Traditionally, network infrastructure sits outside the security ecosystem, making monitoring network access attempts increasingly difficult.
Adversaries, particularly APTs, are capitalizing on this scenario to conduct hidden post-compromise activities once they have gained initial access to the network. The goal is to gain a greater foothold, conceal their activities, and hunt for sensitive data and intelligence to assist them with their intentions. Talos has observed three common post-compromise activities: modifying device firmware, uploading outdated firmware, or removing or bypassing security measures.
Device Firmware Modification
Talos has observed Advanced Persistent Threat actors (APTs) modifying network device firmware on older devices, adding functionality to gain a greater foothold on the network. The added functionality could include implants or modifying how the device captures information.
An example is the recent exploitation of CVE-2023-20198 and CVE-2023-20273, which impact the Cisco IOS XE Software Web Management User Interface. In one observed attack, threat actors deployed an implant Talos called “BadCandy,” which consisted of a configuration file “cisco_service.conf,” which also defines the new web server endpoint (URI path) used to interact with the implant. This endpoint receives specific parameters that allow the actor to execute arbitrary commands at the system or IOS level.
Another example is from September 2023, when BlackTech was observed modifying router firmware to allow the installation of a modified bootloader. This helps it bypass certain security features while creating a backdoor to the device. The Threat Intel team covered this activity in a report titled “BlackTech Compromised International Subsidiaries Replaced Router Firmware to Target US and Japan Headquarters.”
Uploading Outdated Firmware
If threat actors cannot modify the existing firmware, or they need additional levels of access that they don’t currently have, adversaries have been observed uploading an older firmware version that has a known vulnerability with a working exploit. Once the vulnerable firmware version has been uploaded, they reboot the device and exploit the now-unpatched vulnerability. This tactic provides the threat actor with a device that can be modified with additional functionality to exfiltrate data.
Bypassing or Removing Security Measures
Talos has also observed threat actors removing anything blocking their access to fulfill their goals. If, for example, they want to exfiltrate data, but there’s an access control list (ACL) that blocks the actor from accessing the data, they may modify the ACL or remove it from the interface. Alternatively, they may install operating software that does not apply an ACL against an actor’s IP address, regardless of the configuration. Other security measures threat actors attempt to circumvent include disabling remote logging, adding user accounts with escalated privileges, and reconfiguring SNMP community strings.
The BadCandy campaign exemplifies how an actor can circumvent security measures. In this campaign, the adversary created miniature servers (virtualized computers) inside of compromised systems, creating a base of operations for them. This tactic allowed the threat actors to intercept and redirect traffic and add and disable user accounts. These new accounts enabled the threat actor to have persistent access, even if the organization were to reboot the device and erase the active memory.
Additional Campaign Objectives
In their original threat advisory, Talos provided a non-exhaustive list of the activities they have observed threat actors take on network infrastructure devices, highlighting the fact that threat actors are taking steps to understand and control targeted environments.
Examples Talos has observed include threat actors performing actions, such as a “show config,” “show interface,” “show route,” “show arp table,” and a “show CDP neighbor,” giving the threat actors a picture of a router’s perspective of the network, and an understanding the foothold they have. Other campaign objectives include:
- Creation of a “hub-and-spoke” VPN topology designed to allow the interception of targeted network segments’ traffic through the VPN.
- Capturing network traffic for future retrieval, frequently limited to specific IPs or protocols.
- Using infrastructure devices to deliver attacks or maintain command and control (C2) in various campaigns.
Risk & Impact Assessment
The exploitation of aging network infrastructure by ransomware groups and Advanced Persistent Threat (APT) actors presents a significant risk to organizations. The threat stems from the actors’ ability to leverage tactics to exploit vulnerabilities in vulnerable or outdated network devices, often overlooked in cybersecurity defenses. Exploitation facilitates initial access, enabling further malicious activities such as espionage, data exfiltration, or pre-positioning for future attacks.
Given the observed prevalence of these tactics and the commonality of aging infrastructure across various industries, the likelihood of an organization being impacted is considerable. Organizations with insufficiently monitored or updated network devices are mainly at risk, highlighting the critical need for vigilance and updated cybersecurity practices.
The impact of such a threat on an organization can be multifaceted and severe. If threat actors gain access to a network device, they can modify its firmware or manipulate security measures to establish persistent access, disrupt operations, or steal sensitive information. The operational impact can be immediate and crippling, with potential service outages, loss of data integrity, and compromised network functionality. The costs associated with incident response, system restoration, regulatory fines, and possible ransom payments can be substantial from a financial perspective.
Additionally, the reputational damage from such a breach could lead to lost business and diminished trust among customers and partners. In the long term, the strategic impact could include losing competitive advantage and increasing vulnerability to future attacks. Prioritizing network infrastructure security is imperative to mitigate these risks and protect organizational assets and reputation.
Source: Cisco Talos, The 3 most common post-compromise tactics on network infrastructure
Phishing Campaign Delivers New Remote Access Trojan (RAT)
Phishing Campaign – Malware – Public Cloud Misuse – Email Command and Control – Infostealer – Keylogger – Remote Access Trojan – Java Archive (JAR) File Misuse – STRRAT – eRAT – VCURMS – Industries/All
Threat Analysis
Recently, a phishing campaign was observed delivering a malicious Java downloader file (.jar) intending to spread STRRAT and a new remote access trojan (RAT) we are calling eRAT. The threat actors utilized public services like Amazon Web Services (AWS) and GitHub to host malicious files and used a commercial code protector to avoid detection. Furthermore, eRAT uses email as its command and control (C2), hence the moniker eRAT, with the receiving email utilizing ProtonMail (sacriliage@proton[.]me).
One observed phishing email was sent to staff members. It was sent from the email address “remittance@finiance[.]com,” with the subject “Remittance Summary.” The body of the email was simple: “Find attached payment advice for remittance. Kindly revert,” with a button that masqueraded as a PDF file attachment titled “Payment Advice.pdf.”
Clicking the button results in the download of a JAR file named Payment-Advice.jar hosted at bankofindustry[.]s3[.]us-east-2[.]amazonaws[.]com. As observed with a JAR decompiler, this downloaded file contains many obfuscated strings, closely resembling obfuscated code produced by the legitimate obfuscation tool known as “Sense Shield Virbox Protector.” Furthermore, if the file is run after a specific date, it causes a notification to appear regarding the expiration of the trial for Virbox Protector.
One of the class names in the JAR file is labeled “DownloadAndExecuteJarFiles,” which downloads two additional JAR files to an actor-provided path and executes them. Another class, labeled “sense loader,” selects the appropriate native loader module from the resources based on the current operating system during the execution process.
The first file (explorer.jar) is the remote access trojan STRRAT, which has a wide range of capabilities, such as serving as a keylogger and extracting credentials from browsers and applications. STRRAT utilizes two string obfuscation tools: Allatori Java and Branchlock. The configuration file is contained in its resource, which, when decoded, reveals information about the command and control server and ID “Khonsari.” While this alone does not provide proof of attribution, Khonsari is a Persian language surname that can also be found among the Iranian diaspora.
The second file (Windows.jar) is a new remote access trojan (RAT) we are calling eRAT because it receives instructions and sends information through email. During the initialization step, the RAT replicates itself into the Startup folder with MyStartupProgram.jar to ensure that it runs automatically when Windows starts. It then alerts the actor that the victim is online and establishes a schedule to periodically check the mailbox.
If eRAT locates an email with content, it first checks for emails with subject lines containing the victim’s computer name and volume ID.
If an email is sent that includes this information in the subject line, the RAT checks the body of the email for specific commands or strings, such as “get information,” “search,” “upload,” “download,” “shell,” “recovery,” or “start keylogger.”
The strings “recovery” and “start keylogger” reference the VCURMS infostealer and a keylogger malware. When eRAT receives an email with the string “recovery,” it executes a PowerShell command to download the respective file, st.jpg, hosted on AWS at riseappbucket[.]s3[.]ap-southeast-1[.]amazonaws[.]com, deploying it to the %USERPROFILE%\AppData\cookie directory with the name st.jar. The primary purpose of the infostealer is to steal system information, such as network, computer, and hardware.
Additionally, the infostealer gathers account information from apps and collects browser data, such as cookies, autofill data, browsing history, and passwords. The collected data is stored in the directory at %USERPROFILE%/<username>. However, despite similarities to Rude Stealer, VCURMS sends the stolen data through email.
When eRAT receives an email with the string “start keylogger,” it executes a PowerShell command to download the respective file, kl.jpg, downloading it to %USERPROFILE%\AppData\cookie directory with the name klog.jar. This file is responsible for recording keystrokes. To retrieve the logged keystrokes, the threat actor sends an email with the body containing the string “get keylogger,” resulting in an email being sent with the logged keystrokes as an attachment.
In addition to installing keyloggers and password recovery malware, additional strings allow the threat actor to execute shell commands (shell), search for files (search), and upload and download files (upload/download).
For instance, when eRAT receives an email containing the shell string and a command, it will read and execute it using cmd.exe /c, returning the results via email. If eRAT receives an email with the search string and keywords, the RAT looks for file names matching the keywords, returning the results to the actor via email.
The threat actor could then send an email with the upload string and a file name and location, resulting in eRAT compressing the file and sending an email with the file as an attachment. The threat actor could also send the download string with an attachment with a .jpg file extension, and eRAT would download the attachment to the infected device.
A high-level overview of the infection chain is as follows:
- Phishing email with a button that downloads a JAR file.
- The JAR file executes PowerShell commands to download eRAT and STRRAT remote access trojans.
- Threat Actor communicates with eRAT via email and can download VCURMS infostealer, a keylogger, execute shell commands, exfiltrate files, or download a file.
Risk & Impact Assessment
The recent phishing campaign distributing STRRAT and the newly identified eRAT presents a substantial risk to organizations, especially considering the sophisticated use of legitimate services like AWS and GitHub for hosting malicious payloads. The actors’ deployment of a commercial code protector to evade detection compounds the threat. Given these tactics and the use of a novel RAT that employs email for command and control communications, the likelihood of an organization falling victim to this campaign is markedly increased.
Organizations with inadequate email filtering, insufficient employee training on phishing, or lacking robust endpoint protection are particularly vulnerable. The risk is amplified by the malware’s capability to bypass conventional detection frameworks, thereby increasing the probability of successful infiltration and persistence within target networks.
The impact on an organization compromised by this campaign could be profound and varied. The dual use of STRRAT and eRAT allows for various hostile activities, from keylogging and credential theft to persistent remote access and data exfiltration. Specifically, the ability of eRAT to receive commands via email and execute various malicious activities can lead to significant operational disruption, sensitive data compromise, and unauthorized access to internal systems.
For example, the theft of credentials and sensitive information could facilitate further lateral movements within the network or lead to significant data breaches. The operational impacts might include disruption of critical business processes, financial loss due to theft or fraud, and the costs associated with incident response and system recovery.
From a reputational standpoint, being the victim of such an attack could erode trust among clients and partners, potentially leading to a loss of business and long-term damage to the organization’s standing in the market. Given these potential consequences, organizations must actively assess their vulnerability to such threats and implement comprehensive security measures to mitigate the associated risks.
Source: Fortinet, VCURMS: A Simple and Functional Weapon
Latest Additions to Data Leak Sites
Information – Health Care and Social Assistance – Manufacturing – Retail Trade – Construction – Accommodation and Food Services – Real Estate and Rental and Leasing – Professional, Scientific, and Technical Services – Finance and Insurance – Educational Services
The landscape of data leak sites is diverse, with nine significant data leak sites identified in the last week. Trigona’s leak site leads with 27% of the incidents, followed by Lockbit at 17%. Other notable sites include Qilin and 8base, each with 10% of the incidents. The remaining sites, Blacksuit, Meow, Hunters International, Bianlian, and Akira, contribute to a smaller fraction of the leaks but are still integral players in the ransomware and data extortion threat landscape.
The Information sector appears to be the most listed industry, representing 22%, with 56% of the organizations operating in this sector. This is followed closely by Health Care and Social Assistance at 17%. Other significant industries include Manufacturing, Retail Trade, and Construction, each showing a notable number of organizations operating in these sectors. These trends highlight key vulnerabilities and potential targeting patterns within these sectors, suggesting a need for heightened security measures.
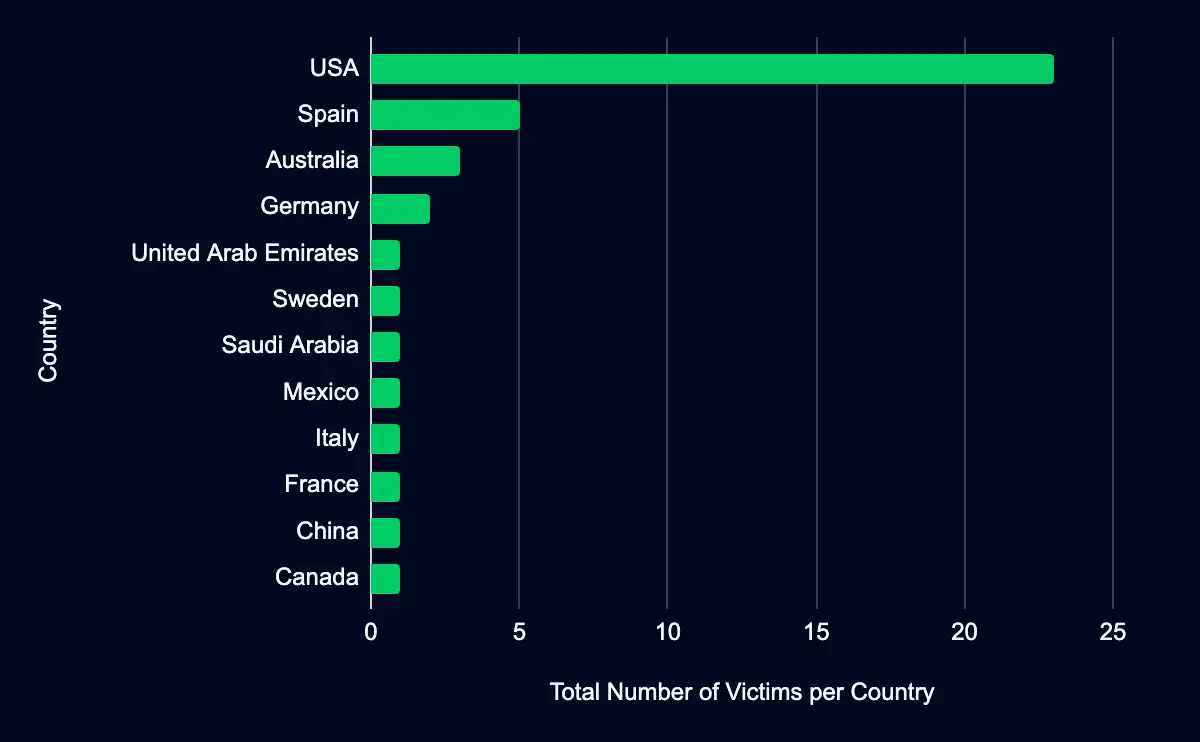
The United States stands out as the most listed country, with 56% of the organizations headquartered in this region, underscoring its prominence in the threat actors’ focus. Spain, Australia, and Germany also appear prominently, indicating a diverse geographical spread in the organizations listed on these data leak sites.
The most active data leak site in the recent dataset is operated by the Trigona Ransomware group, accounting for 11 of the 41 new additions. Trigona’s recent additions feature a broad array of industries, with a notable emphasis on Manufacturing (27%), Construction (18%), and Accommodation and Food Services (18%).
These sectors are followed by Retail Trade and Professional, Scientific, and Technical Services, each at 9%. This distribution suggests that Trigona does not limit its operations to traditionally high-value targets like finance or healthcare but adopts a more opportunistic approach, potentially exploiting specific vulnerabilities in these sectors.
The analysis of recently added organizations reveals a significant portion of the organizations are headquartered in the United States, accounting for 36%, followed by Spain (27%) and Australia (18%). The presence of these organizations in diverse geographical regions may indicate Trigona’s global reach and ability to execute attacks across different legal jurisdictions, complicating cybersecurity defense and response efforts.
Trigona’s prominence in the data leak landscape might suggest a high level of organization and technical capability. The variety in sectors and countries could imply an advanced targeting mechanism and possibly a well-structured intelligence-gathering phase before launching attacks. Understanding these patterns is crucial for anticipating future threats and advising potentially targeted sectors on bolstering their defenses.
Organizations within the most targeted industries should be proactive in their cybersecurity measures, implementing sector-specific best practices to mitigate the risk of falling victim to Trigona. However, while these organizations are listed on Trigona’s leak site, there is a remote possibility that some may not be victims of Trigona’s ransomware and data extortion operations.
Lockbit’s leak site is the second most active in the recent dataset, constituting a significant portion of the new entries, accounting for seven of the 41 additions.
Lockbit’s recent postings show a concentrated pattern, mainly targeting the Information sector (43%) and Health Care and Social Assistance sector (29%). This focus on data-rich industries suggests a strategic choice likely driven by the high value and sensitivity of the data held by organizations in these sectors. Educational Services (14%) and Accommodation and Food Services (14%) among the targeted sectors indicate a broader range of interests, potentially exploiting specific sectoral vulnerabilities.
Their recent additions also show a pronounced emphasis on the United States, which accounts for an overwhelming 86% of the listed entities. This intense focus may suggest a particular familiarity with or strategic focus on American organizations, possibly due to perceived vulnerabilities or high-value targets within this region. The singular listing of a Chinese organization points to Lockbit’s capability and willingness to operate across diverse jurisdictions.
The operational profile of Lockbit, with its targeted sectoral focus and geographical concentration, hints at a sophisticated understanding and selection of targets, likely underpinned by detailed reconnaissance and initial access strategies. Lockbit’s continuing prominence in the data leak domain reflects its significant role in the broader cyber threat landscape, emphasizing the need for a targeted defensive strategy.
Given the acute focus on specific sectors, organizations within the Information and Health Care domains should prioritize advanced cybersecurity measures and sector-specific defenses to mitigate the risk of compromise. The heavy targeting of US-based entities underscores the importance of region-specific cybersecurity frameworks and collaborative defense mechanisms.
Qilin and 8base, each contributing four new additions to the data leak site dataset, stand out as key platforms. Organizations listed on Qilin and 8base’s leak site collectively demonstrate a varied industry focus, which might indicate a broader or more opportunistic targeting strategy. Qilin listed one organization in the Manufacturing, Information, Health Care and Social Assistance, and Finance and Insurance sectors. On the other hand, 8base’s recent additions featured two organizations operating in the Information sector and one each in the Professional, Scientific, and Technical Services and Agriculture, Forestry, Fishing, and Hunting sectors.
The activities of Qilin and 8base span multiple countries, indicating a lack of a singular geographical focus. This widespread approach might reflect a strategy to exploit global vulnerabilities, diversifying their risk and maximizing potential impact. The distribution of organizations across various regions underscores their capability to orchestrate and execute cyber operations globally.
Given the diverse targeting strategy of Qilin and 8base, organizations across all sectors should consider broadening their cybersecurity measures, implementing robust defenses, and maintaining heightened awareness of potential threats.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed.
Additionally, we may have omitted victims we could not verify. Additionally, victims are classified based on the NAICS industry classification system. While we only list one industry classification per victim, it’s possible that a victim could fall under multiple industries classification, which may inadvertently skew results.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds CVE-2024-27198 to Known Exploited Vulnerabilities Catalog
JetBrains TeamCity CVE-2024-27198
Within the past week, CISA added the vulnerability CVE-2024-27198 to its Known Exploited Vulnerabilities catalog, impacting JetBrains TeamCity servers. Threat actors can exploit this vulnerability to bypass authentication mechanisms to perform administrative-level actions.
It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities. CISA recommends mitigative action by 28 March 2024. Despite speculation that this vulnerability was exploited in a ransomware attack, CISA states that it is unknown if ransomware actors have exploited this vulnerability.
Analytical findings are based on CVE additions to CISA’s Known Exploited Vulnerabilities Catalog. Due to the catalog lacking much-needed context, we collect additional open-source reporting and internal data where possible. However, we cannot fully determine the reliability and credibility of all open-source reporting used.
Despite our analysis, notable intelligence gaps, such as the breadth and scope of exploitation attempts and all known post-exploitation activity, limit our understanding of exploitation activity. Addressing this gap requires proactive threat hunting and incident response to identify exploitation events associated with this vulnerability.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA, Deepwatch, Rapid7
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share