FOG Ransomware Tactics Uncovered, Dual Threats Delivered via Phishing, and New Broadcom, Qualitia, Commvault, and SAP Vulnerabilities Added to CISA’s Catalog
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Dissecting Fog: Tactics and Tools of a Modern Ransomware Threat
The Rundown
The DFIR Report’s latest publication, “Navigating Through the Fog,” unveils a significant cybersecurity threat linked to the Fog ransomware group. In December 2024, investigators discovered an open directory associated with this group, containing a comprehensive suite of malicious tools. These tools facilitated various stages of cyberattacks, including reconnaissance, exploitation, credential theft, and command-and-control operations.
Notably, the attackers exploited compromised SonicWall VPN credentials to gain initial access, employed tools like DonPAPI and Certipy for credential extraction and Active Directory exploitation, and used AnyDesk for persistent remote access. The presence of Sliver C2 components and Proxychains indicates sophisticated methods for maintaining control and evading detection.
The victims of these attacks spanned multiple industries—technology, education, and logistics—across various regions, including Europe and South America. This broad targeting underscores the attackers’ opportunistic approach and the widespread vulnerability of organizations to such threats. The use of publicly available tools and open directories for staging attacks highlights a growing trend in cybercrime, where threat actors leverage readily accessible resources to orchestrate complex intrusions.
For business leaders, this report serves as a stark reminder of the evolving cyber threat landscape. The exploitation of common vulnerabilities and the use of legitimate tools for malicious purposes emphasize the need for robust cybersecurity measures. Organizations should prioritize securing remote access points, regularly update and patch systems, and invest in comprehensive monitoring solutions to detect and respond to suspicious activities promptly. Staying informed about emerging threats and adopting a proactive security posture are crucial steps in safeguarding against such sophisticated cyberattacks.
Source Material: The DFIR Report
Double Trouble: How One Phishing Email Delivers Two Cyber Threats at Once
The Rundown
Cofense’s recent analysis reveals a sophisticated phishing campaign that combines credential harvesting with malware distribution, posing a significant threat to businesses. Attackers send emails that appear to be legitimate file deletion notices from trusted file-sharing services like files.fm. These emails prompt recipients to click on a link, leading to a genuine-looking download page. Once the user downloads and opens the attached PDF, they are redirected to a counterfeit Office365 login page designed to steal their credentials. Simultaneously, the PDF may contain malware that infects the user’s system, providing attackers with unauthorized access.
This dual-threat approach is particularly concerning because it exploits the trust users place in familiar services and the urgency conveyed in the message. By leveraging legitimate platforms to host malicious content, these phishing emails can bypass standard security measures, making them more effective. The combination of credential theft and malware installation increases the potential damage, allowing attackers to access sensitive information and compromise organizational systems.
To defend against such threats, businesses should implement multi-factor authentication (MFA) to add an extra layer of security beyond passwords. Regular employee training on recognizing phishing attempts is crucial, as human error remains a significant vulnerability. Additionally, deploying advanced threat detection systems that can identify and block sophisticated phishing campaigns is essential. By adopting a proactive and layered security strategy, organizations can better protect themselves from evolving cyber threats.
Source Material: Cofense
Ransomware and Data Extortion Trends (Apr. 21 – 27)
The Rundown
Ransomware and data extortion activity includes a sharp increase between April 21 – 27, with a 40% decrease in listed organizations compared to the previous week.
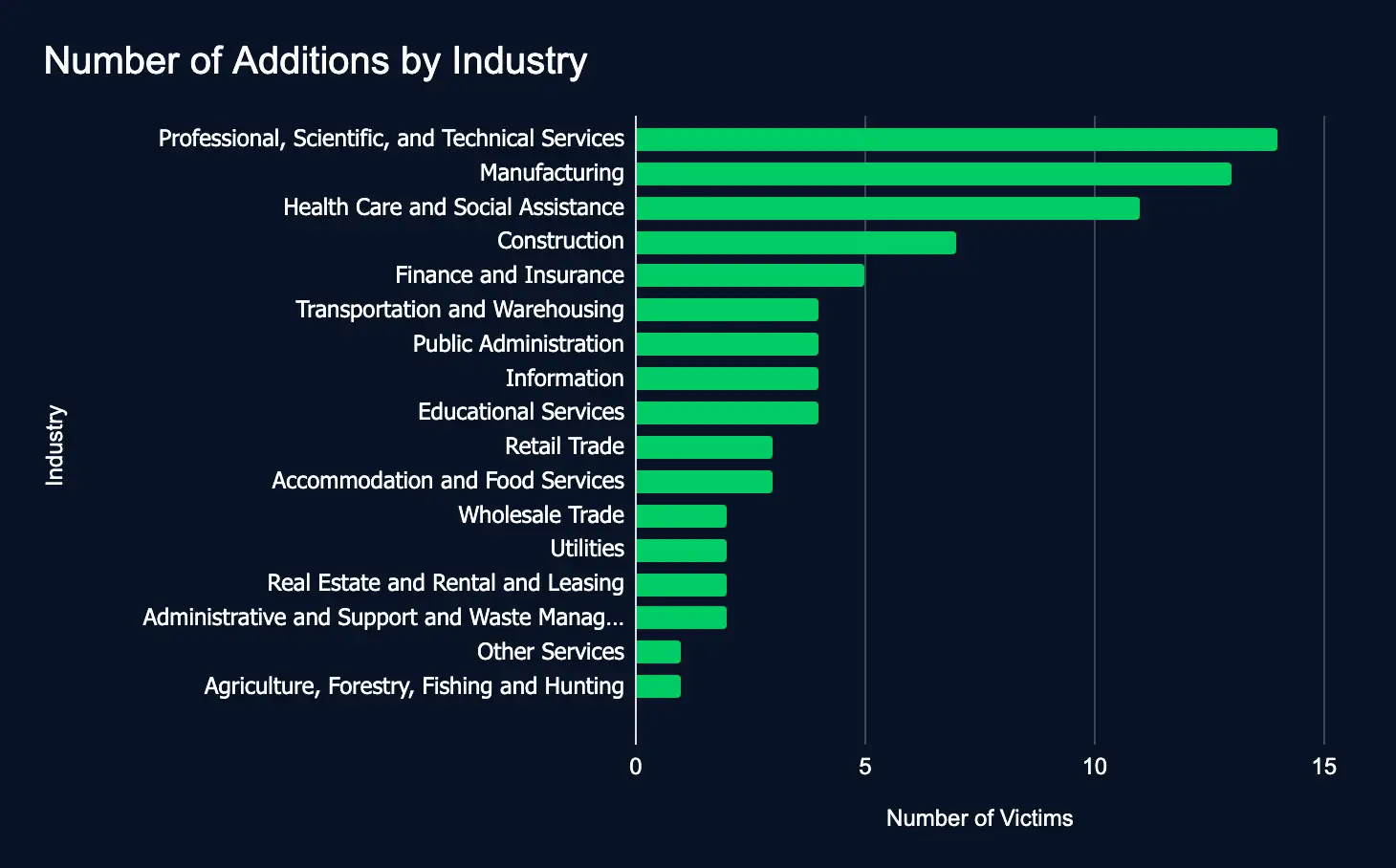
In the reporting time frame, 82 organizations across 17 industries were listed on 15 ransomware and data extortion leak sites, marking a sharp decrease from the previous week’s 136 victims.
The decrease of 54 ransomware Data Leak listings from the previous week should not be misconstrued as a diminished threat. Rather, it signals a shift toward more sophisticated and targeted attack strategies. This evolving threat landscape necessitates that organizational leadership align cybersecurity initiatives with broader business continuity and resilience planning.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Health Care and Social Assistance
- Most affected countries:
- United States
- Italy
- Canada
- Most active leak sites:
- Akira
- Play
- Lynx
Exploited Vulnerabilities in Broadcom, Qualitia, Commvault, and SAP Products Added to CISA’s Catalog
The Rundown
Between April 24th and 30th, 4 critical vulnerabilities affecting Broadcom, Qualitia, Commvault, and SAP products were added to CISA’s Known Exploited Vulnerabilities catalog. If left unpatched, these vulnerabilities could leave organizations vulnerable to cyberattacks.
These vulnerabilities present substantial risks to organizations that depend on widely adopted technologies. In light of the increased likelihood of exploitation by state-sponsored and cybercriminal actors, expedited remediation efforts are imperative to ensure operational security and resilience.
Broadcom | Brocade Fabric OS CVE-2025-1976
- Vulnerability Description: Broadcom Brocade Fabric OS contains a code injection vulnerability that allows a local user with administrative privileges to execute arbitrary code with full root privileges.
- Exploitation Details: Through a flaw in IP Address validation, a local user, assigned one of the pre-defined admin roles or a user-defined role with admin-level privileges, can execute arbitrary code as if they had full root level access. This vulnerability can allow the user to execute any existing Fabric OS command or can also be used to modify the Fabric OS itself, including adding their own subroutines. Even though achieving this exploit first requires valid access to a role with admin privileges, this vulnerability has been actively exploited in the field.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-28
- Recommended Mitigation Due Date: 2025-05-19
Qualitia | Active! Mail CVE-2025-42599
- Vulnerability Description: Qualitia Active! Mail contains a stack-based buffer overflow vulnerability that allows a remote, unauthenticated attacker to execute arbitrary or trigger a denial-of-service via a specially crafted request.
- Exploitation Details: If a remote attacker sends a crafted request, it may be possible to execute arbitrary code or cause a denial of service (DoS).
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-28
- Recommended Mitigation Due Date: 2025-05-19
Commvault | Web Server CVE-2025-3928
- Vulnerability Description: Commvault Web Server contains an unspecified vulnerability that allows a remote, authenticated attacker to create and execute webshells.
- Exploitation Details: Exploiting this vulnerability requires a bad actor to have authenticated user credentials within the Commvault Software environment. Unauthenticated access is not exploitable.According to the Commvault advisory: “Webservers can be compromised through bad actors creating and executing webshells.”
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-28
- Recommended Mitigation Due Date: 2025-05-19
SAP | NetWeaver CVE-2025-31324
- Vulnerability Description: SAP NetWeaver Visual Composer Metadata Uploader contains an unrestricted file upload vulnerability that allows an unauthenticated agent to upload potentially malicious executable binaries.
- Exploitation Details: Attackers craft malicious HTTP POST requests to upload files, such as JSP web shells, into directories like j2ee/cluster/apps/sap.com/irj/servletjsp/irj/root/. These files can then be executed remotely via HTTP GET requests, granting attackers the ability to execute arbitrary commands on the server.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-04-29
- Recommended Mitigation Due Date: 2025-05-20
Recommendations
ATI recommends that mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share