New qBit Infostealer, Cybercriminals Utilize Microsoft’s App Installer to Deploy Malware, and a Google Exploit Restores Expired Cookies to Allow Persistent Access
This week: the customizable qBit Infostealer is released, cybercriminals utilize Microsoft App Installer to deploy malware that facilitates post-compromise payload deployment, and a Google exploit is found that can restore cookies and allow access even after a password change. All this plus the latest from data leak sites and two new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- qBit Stealer, a Customizable File Stealing Malware, Publicly Released
- Various Financially Motivated Cybercriminals Utilize Microsoft’s App Installer to Deploy Malware
- Infostealers Incorporate Google Exploit to Restore Expired Google Cookies, Allowing Persistent Access
- Latest Additions to Data Leak Sites
- CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
qBit Stealer, a Customizable File Stealing Malware, Publicly Released
Malware – File Stealer – Data Exfiltration – qBit Stealer – Mega.nz API – Industries/All
Threat Analysis
qBit Stealer, a malware developed in the Go programming language, emerged as a significant threat in the cyber landscape in late 2023. Initially introduced by the QBit Ransomware-as-a-Service (RaaS) group on 9 October 2023. However, on 5 December 2023, a link for the source code of qBit Stealer was released for free on a known cybercrime forum, and later, access to the same code was posted on various cybercrime forums.
Technical Capabilities
qBit Stealer exhibits several capabilities, including selective file targeting based on extensions, ability to upload files to Mega[.]nz using an advanced concurrency engine, and anti-debugging and anti-virtualization/sandbox features to evade detection.
Source Code Analysis
The source code of qBit Stealer includes several components, such as a batch script for generating the executable, a configuration file, and various Go files handling different functionalities like the main stealer logic and Mega API client.
qBit Stealer employs the NtQueryInformationProcess() function for anti-debugging, checking the “BeingDebugged” flag in the Process Environment Block (PEB). Additionally, it uses a list of predefined processes to detect virtualization or sandbox environments, terminating its process if such environments are detected.
Configuration and Customization
The qBit Stealer’s source code includes a configuration file (config.json), allowing customization of various parameters such as API credentials, file system paths, maximum file size, and targeted file extensions. This level of customization provides flexibility for different operational needs.
The configuration file consists of the following fields:
- API Credentials: This field contains the ID and password for authenticating with the Mega[.]nz API. The threat actor uses them to access the Mega[.]nz cloud storage service and upload stolen files.
- File System Path: This field specifies the initial file system path from which the stealer will search for files to exfiltrate. If not specified or inaccessible, it defaults to using all available drives.
- Stolen Folder Name: This field determines the folder name on the Mega[.]nz cloud where stolen files will be stored.
- Maximum File Size: This field defines the maximum size of files the stealer will upload. Files exceeding this limit will be excluded. This field is set to 150MB by default.
- Split Size: By default, files larger than 50MB will be split during uploading.
- Targeted File Extensions: This is a list of file extensions the stealer targets for exfiltration. The stealer exfiltrates only files with these extensions. By default, it targets .txt, .pdf, and .docx files.
Data Exfiltration Process
Before exfiltrating the data, qBit stealer creates a new Mega[.]nz API client instance. Then, it checks if “StolenFolderName” is specified in the configuration file. If it is not, it creates a folder in the %temp% directory and sets the folder name to the computer username.
qBit stealer targets paths specified in the configuration file. It walks through the specified paths and subdirectories, filtering files based on their extension and size. Without defined paths, it defaults to obtaining files from all available drives.
Next, the stealer compresses the stolen data into a “.tar.gz” file. If the size of this archive is more than the size specified in the configuration, it splits the file into smaller chunks. The code then uses goroutines to upload each split file concurrently. After the uploads are complete, a cleanup routine is initiated, waiting for 15 seconds and then attempting to remove the archive file.
The specific targeting of files by qBit Stealer aligns with the evolving tactics seen in ransomware attacks, particularly those involving double extortion. The threat of exposing sensitive data and encryption increases cybercriminals’ leverage. In the ransomware landscape, qBit Stealer could be a valuable tool for TAs seeking to exfiltrate critical data before initiating a ransomware attack, amplifying the potential harm to targeted entities.
Risk & Impact Assessment
The release of qBit Stealer’s source code in early December on various cybercrime forums significantly increases the risk of its adoption by various threat actors, including those with lower technical skills. This availability poses a substantial risk, as it lowers the barrier to entry for cybercriminals. This democratization of access could potentially increase the frequency and diversity of cyber attacks involving data theft.
The broad availability of qBit Stealer and its advanced capabilities amplify the risk profile. Organizations across various sectors could face heightened threats of targeted data theft, potentially leading to significant financial losses, reputational damage, and regulatory implications. The tool’s ability to evade detection increases the likelihood of successful breaches, making it a formidable challenge for existing cybersecurity defenses.
Considering the enhanced capabilities of qBit Stealer and its potential widespread adoption, there is a reasonable likelihood of a material impact on businesses’ operations, results of operations, or financial conditions. Cybersecurity incidents involving qBit Stealer could lead to substantial data breaches, exposing sensitive customer and corporate data. Such incidents incur direct financial costs and long-term indirect costs through reputational harm and loss of customer trust.
Source Material: Cyble, Decoding qBit Stealer’s Source Release and Data Exfiltration Prowess
Various Financially Motivated Cybercriminals Utilize Microsoft’s App Installer to Deploy Malware
Malware Installation Technique – Microsoft App Installer -Microsoft Teams – SEO Poisoning – Phishing – Storm-0569 – Storm-1113 – Sangria Tempest – Storm-1674 – Industries/All
Threat Analysis
Recently, financially motivated cybercriminals have been observed utilizing Microsoft’s App Installer as a vector for malware distribution to bypass standard security measures. Since mid-November 2023, several cybercriminals (Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674) have misused the App Installer URI protocol (ms-appinstaller:?source=’URI’) to facilitate the installation of malware via three infection chains: SEO-poisoned websites, Google ads, and Microsoft Teams. Additionally, multiple cybercriminals are also selling a malware kit as a service that abuses the MSIX file format and ms-appinstaller protocol.
SEO Poisoning:
The SEO poisoning technique has been a prominent infection chain utilized by threat actors like Storm-0569 and Sangria Tempest. Using search engine optimization techniques (SEO poisoning), these actors create or modify web content to rank high in search results for popular software downloads such as Zoom, Tableau, TeamViewer, and AnyDesk. Once clicking on a search engine result, unsuspecting users searching for these applications can be directed to fake landing pages that impersonate legitimate software providers. These pages contain links to malicious installers using the ms-appinstaller URI protocol (ms-appinstaller:?source=’URI’), leading to malware installation via the App Installer experience.
Google Ads:
Another observed infection chain involves using Google ads, as seen with threat actors like Storm-1113 and Sangria Tempest. These actors leverage Google’s advertising platform to display advertisements that mimic legitimate software offerings, redirecting users to malicious websites. Once on these sites, users are enticed to download applications that install malware through the App Installer URI protocol (ms-appinstaller:?source=’URI’) and the App Installer experience. This approach is notable as it exploits the Google ad ecosystem’s perceived legitimacy and trustworthiness.
Microsoft Teams:
The use of Microsoft Teams for phishing attacks, as employed by Storm-1674, represents a novel infection chain. This method involves sending messages through Teams actor-controlled tenants that contain links to Storm-113 provided fake landing pages, which spoof file-sharing services like OneDrive, SharePoint, and software download sites. Users are lured into downloading files or applications that may open an error message. Clicking on the button will install malware via the App Installer URI protocol (ms-appinstaller:?source=’URI’) and the App Installer experience. This technique is particularly effective in corporate environments where Teams is a trusted communication tool.
Post-App Installer Abuse
Following the successful utilization of the App Installer, the subsequent activities often include deploying secondary payloads to further compromise systems. These follow-on payloads include a variety of malware and tools aimed at data exfiltration, establishing persistent access, and potentially deploying ransomware. For instance, Storm-0569 has been observed using PowerShell and batch scripts to download additional malware like BATLOADER, which can lead to the deployment of Cobalt Strike Beacons and ransomware like Black Basta. Similarly, Sangria Tempest has used the initial foothold provided by EugenLoader to deploy the Carbanak backdoor and Gracewire malware, focusing on data theft and extortion.
On 28 December 2023, Microsoft updated CVE-2021-43890 to disable the ms-appinstaller URI protocol by default in App Installer version 1.21.3421.0 or higher. Users can no longer install an app directly from a web page using the App Installer. Instead, users will be required to download the MSIX package first to install it, ensuring that locally installed antivirus protections will run.
Customers may be vulnerable if:
- They have the EnableMSAppInstallerProtocol group policy set to “Not Configured” (blank) or “Enabled.”
- The version of App Installer installed on their PC is between version 1.18.2691 and 1.21.3421.
- Running the following OS builds, which contain a vulnerable version of the AppInstaller.
- OS update March 21, 2023: 19042.2788, 19044.2788, and 19045.2788
- OS update July 11, 2023: 20348.1850
- OS update March 28, 2023: 22000.1761
- OS update October 25, 2022: 22621.755
- Or using builds version 1.22.3452-preview or lower.
Risk & Impact Assessment
Utilizing Microsoft’s App Installer by cybercriminals presents significant risks and impacts across multiple dimensions. Firstly, there is the direct risk of malware infection, which can lead to data theft, financial loss, and disruption of operations. The nature of these attacks, using SEO and Google ads and leveraging trusted platforms like Microsoft Teams, increases the likelihood of a successful attack. This threat is particularly acute for organizations without procedures to install approved applications, like Zoom, Tableau, TeamViewer, and AnyDesk. The secondary payloads deployed post-App Installer pose additional risks of operational disruption and reputational damage. The risk level associated with these incidents can be considered high, given the potential for widespread impact and difficulty detecting and mitigating these sophisticated attacks.
The potential for a material impact on a company’s business operations, results of operations, or financial condition due to these cybersecurity incidents is significant. High-risk cybersecurity incidents can adversely affect a company’s stock price for up to a year following the incident, posing direct financial losses and long-term reputational damage, loss of customer trust, and potential legal liabilities. The repercussions can be even more pronounced for companies in sectors where trust and data security are paramount, such as finance, healthcare, and technology. The need for robust cybersecurity measures and incident response plans is critical, not only for protecting against immediate threats but also for safeguarding the organization’s long-term financial and operational stability.
Source Material: Microsoft Threat Intelligence, Financially motivated threat actors misusing App Installer
Infostealers Incorporate Google Exploit to Restore Expired Google Cookies, Allowing Persistent Access
Google OAuth2 Exploit – Lumma Infostealer – Infostealer Malware – MultiLogin Endpoint – Expired Cookie Regeneration – Credential Theft – Industries/All
Threat Analysis
In October 2023, a critical exploit was uncovered, significantly impacting the security of Google accounts. This exploit, discovered by a developer known as PRISMA, enabled the regeneration of expired Google cookies through token manipulation, allowing continuous access to Google services, even after resetting a user’s password. The exploit leveraged an undocumented functionality within Google’s OAuth2 system, specifically targeting an endpoint named “MultiLogin.” This discovery began a ripple effect as various info stealer developers rapidly integrated the exploit into their offerings.
The exploit boasted two key features: cookie regeneration and session persistence. Cookie regeneration enables the restoration of valid, expired cookies, enabling the persistence of sessions even when the user’s account password is changed. Furthermore, PRISMA expressed their willingness to collaborate or share insights on this newfound exploit.
Exploit Technical Analysis
The technical foundation of the exploit lies in its ability to target a MultiBearer authorization token obtained from the restore files. Upon initiating the process, a POST request is sent to “https://accounts.google[.]com/oauth/multilogin” with specific headers, including the previously obtained authorization token. This request triggers a response containing cookies in a JSON structure, which the script parses to extract relevant information. The extracted data is then formatted into Netscape cookie file format, facilitating the regeneration of stable and persistent Google cookies.
The MultiLogin endpoint is an internal mechanism for synchronizing Google accounts across services. It facilitates a consistent user experience by ensuring browser account states align with Google’s authentication cookies. This endpoint accepts account IDs and auth-login tokens, data essential for seamlessly managing simultaneous sessions or switching between user profiles.
Infostealer Incorporation
Lumma infostealer was among the first to incorporate PRISMA’s exploit, announcing on 14 November the integration of this exploit, which was a significant development in the malware’s capabilities. This integration was not just a simple adoption of the exploit; Lumma applied advanced encryption of crucial elements of the exploit, known as blackboxing, specifically the token:GAIA ID pair, which is central to the exploit’s functionality. This approach not only protected the methodology of the exploit but also made it more difficult for other malicious entities or security researchers to understand and mitigate the exploit.
Following Lumma’s successful exploit integration, several other infostealer groups rapidly adopted the same technique. Rhadamanthys, Risepro, Meduza, Stealc Stealer, and White Snake were notable among these. Each group announced their incorporation of the exploit between November and December 2023.
Risk & Impact Assessment
Incorporating the Google Chrome exploit by multiple infostealer groups presents significant risks and impacts on individuals and organizations. The primary risk lies in the exploit’s ability to facilitate password theft and maintain continuous access to Google accounts, even after password resets. The exploit’s capability to keep sessions valid during disruptions further exacerbates the risk. The risks of this exploit are far-reaching, which could result in unauthorized access and theft of sensitive data beyond credentials, potentially resulting in impacts related to financial loss and reputational damage. The widespread adoption of this exploit by various infostealers indicates a high likelihood of these risks materializing.
In assessing the material impact on a company’s business operations, results of operations, or financial condition, it’s crucial to consider the potential secondary use of stolen credentials. While the initial theft of passwords or continuous access may not constitute a material event in isolation, the subsequent use of these credentials for further malicious activities, such as deploying ransomware, could have a material impact.
Ransomware attacks can lead to significant operational disruptions, financial losses, and long-term reputational harm. Therefore, the risk posed by this exploit transcends the immediate unauthorized access and extends to the potential for more severe and damaging cyberattacks. Companies must evaluate this risk in the context of their cybersecurity posture and the potential cascading effects of compromised credentials leading to more severe incidents.
Source Material: CloudSEK, Compromising Google Accounts: Malwares Exploiting Undocumented OAuth2 Functionality for session hijacking; Hudson Rock,Breaking through the Infostealer Exploit and the Enigma of Cookie Restoration
Latest Additions to Data Leak Sites
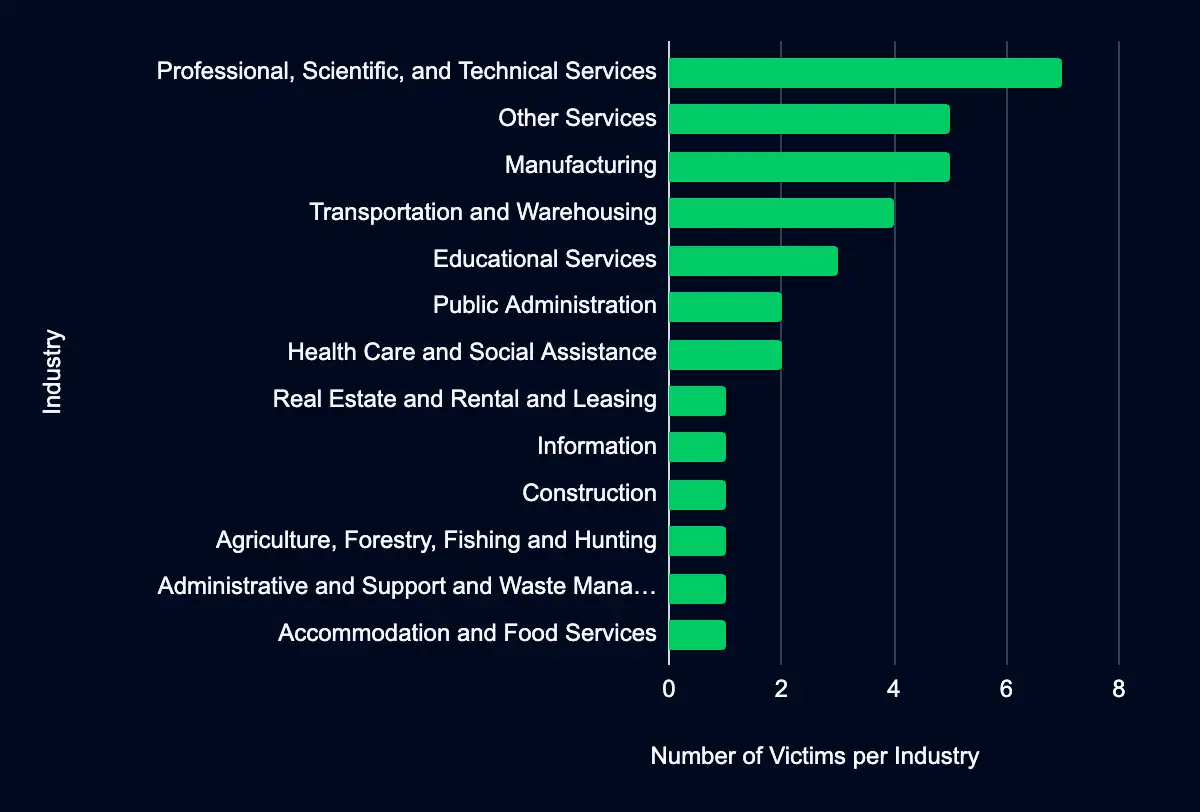
Professional, Scientific, and Technical Services – Other Services – Manufacturing – Transportation and Warehousing – Educational Services
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. Thirty-four organizations have been listed as victims in the past week, with a significant concentration in the United States, accounting for 53% of the total incidents. This geographic focus indicates the larger digital footprint or potentially perceived lucrative targets within the US. Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Professional, Scientific, and Technical Services leading the list, followed by Other Services, Manufacturing, Transportation and Warehousing, and Educational Services. This spread across various industries suggests a non-discriminatory approach by threat actors, possibly driven by opportunity-based targeting rather than specific sectoral preferences.
Lockbit, responsible for 44% of the incidents in the past week, has shown a marked preference for targeting organizations in the USA, which aligns with the overall trend of heightened activity in this region. Their focus has predominantly been on the Transportation and Warehousing and Public Administration sectors, suggesting a strategic choice possibly influenced by the potential for high-impact disruptions and lucrative ransom demands.
ALPHV, accounting for 26% of the incidents, has demonstrated a broader range of targets across the USA, Türkiye, and the Philippines, with a notable focus on the Professional, Scientific, and Technical Services sector. ALPHV’s additions suggest a more opportunistic approach, possibly capitalizing on the typically high-value data held by organizations in these sectors. ALPHV’s activities highlight their affiliate’s adaptability and willingness to diversify their targets geographically and sector-wise.
Though less frequent, the activities of Rhysida, Play, and Black Basta, accounting for a combined 18% of the total victims listed, provide insight into the diverse nature of threat actors in the ransomware ecosystem. Rhysida’s targeting of health care and educational institutions in Jordan and South Africa indicates a focus on sectors often under- resourced in cybersecurity defenses. Play’s targeting of real estate and legal services in North America suggests a niche focus, potentially driven by the perceived value of confidential data in these sectors. Black Basta’s attacks on various industries, including Administrative and Support Services and Law Firms, demonstrate their versatility and opportunism.
Our analysis strives to be comprehensive, utilizing the most current data available from our dark web monitoring platform. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we may have omitted victims we could not verify. As the data set does not include information about the industry, we do our best to classify the victims based on the NAICS industry classification system. This manual effort may introduce other discrepancies, such as misclassifying the industry. We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies. If you have questions or feedback about this intelligence, you can submit them here.
CISA Adds 2 CVEs to Known Exploited Vulnerabilities Catalog
Google Chromium CVE-2023-7024 – Spreadsheet::ParseExcel CVE-2023-7101
Within the past week, CISA added two CVEs to its Known Exploited Vulnerabilities catalog, impacting Google Chromium and the Spreadsheet::ParseExcel library. Threat actors can exploit these vulnerabilities to perform crashes, code execution, and remote code execution. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action by 23 January 2024.
CVE-2023-7024 impacts Google Chrome, specifically impacting versions before 120.0.6099.129. This vulnerability is a heap buffer overflow in the WebRTC framework, allowing a remote attacker to potentially exploit heap corruption via a crafted HTML page. The severity of this vulnerability is high, and it has been actively exploited in the wild. To mitigate potential threats, users should upgrade to Chrome version 120.0.6099.129/130 for Windows and 120.0.6099.129 for macOS and Linux.
CVE-2023-7101 impacts Spreadsheet::ParseExcel, a Perl module used for parsing Excel files, specifically version 0.65. This vulnerability is due to passing unvalidated input from a file into a string-type “eval,” particularly in the evaluation of Number format strings within the Excel parsing logic, leading to arbitrary code execution (ACE). Barracuda’s Email Security Gateway Appliance (ESG) was exploited using this vulnerability by the threat actor tracked as UNC4841, which led to the deployment of new SEASPY and SALTWATER malware variants. While Barracuda has deployed an automatic security update for its ESG appliances, no known patch or update is available to remediate CVE-2023-7101 within the open-source library. Organizations utilizing Spreadsheet::ParseExcel in their products or services are advised to review CVE-2023-7101 and take necessary remediation measures.
The discovery and subsequent mitigation of these vulnerabilities demonstrate the persistent challenge in software security: the need for constant vigilance and prompt response to emerging threats. The exploitation of CVE-2023-7024 and CVE-2023-7101 underscore the importance of a robust and agile security posture from vendors and users alike.
The addition of these CVEs to CISA’s catalog highlights specific risks associated with Google Chromium and Spreadsheet::ParseExcel but also underscores the broader theme of proactive security management in an ever-evolving digital landscape. Regular updates, strong authentication practices, and timely responses to identified vulnerabilities remain paramount in safeguarding against potential exploits and maintaining the integrity of networked systems.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-7024 | Chromium WebRTC | Google Chromium WebRTC, an open-source project providing web browsers with real-time communication, contains a heap buffer overflow vulnerability that allows an attacker to cause crashes or code execution. This vulnerability could impact web browsers using WebRTC, including but not limited to Google Chrome. | 2024-01-23 | Unknown | |
| CVE-2023-7101 | Spreadsheet:: ParseExcel | Spreadsheet:: ParseExcel | Spreadsheet::ParseExcel contains a remote code execution vulnerability due to passing unvalidated input from a file into a string-type “eval.” Specifically, the issue stems from the evaluation of Number format strings within the Excel parsing logic. | 2024-01-23 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share