Github Abuses, Ivanti Connect Secure VPN Compromises, New Cloud Hacking Tool FBot, and Phemedrone Infostealer Targets Microsoft Windows Defender SmartScreen
This week: ATI dives deep into the abuse of Github by threat actors, we look at the compromise of Ivanti Connect Secure VPN to deploy web shells and backdoors, examine a new hacking tool called FBot that hijacks cloud, and look at a new infostealer that targets Windows Defender Smartscreen vulnerability. All this plus the latest from data leak sites and four new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- The Various Ways Threat Actors Abuse GitHub for Malicious Purposes
- Espionage Threat Actors Exploited Ivanti Connect Secure to Deploy Web Shells, Backdoors, and Credential Harvester
- FBot, the Hacking Tool Designed to Hijack Cloud, SaaS, and Web Services
- New Infostealer Campaign Exploits Windows Defender SmartScreen Vulnerability (CVE-2023-36025)
- Latest Additions to Data Leak Sites
- CISA Adds 4 CVEs to Known Exploited Vulnerabilities Catalog
The Various Ways Threat Actors Abuse GitHub for Malicious Purposes
GitHub Abuse – Payload Delivery – Command and Control – Dead Drop Resolver – Exfiltration – Industries/All
Threat Analysis
GitHub, a platform primarily intended for collaborative software development and version control, has been and still is abused by threat actors to exploit the inherent trust and functionalities of a widely respected and used platform. GitHub’s extensive ecosystem, designed to facilitate coding, storing, and sharing software code, inadvertently offers a fertile ground for abuse. The platform’s reliability, global accessibility, and integral role in many software development pipelines make it an attractive tool for malicious purposes.
GitHub’s design, inherently focused on collaboration and sharing, has inadvertently made it a target for abuse by cybercriminals and Advanced Persistent Threats (APTs). The various features and aspects of GitHub that contribute to its attractiveness as a platform for malicious activities include:
- Its ease of use and accessibility. The ease with which threat actors can create new accounts and upload new content allows them to set up their operations quickly and with little technical barrier.
- Its anonymity and user account policies. GitHub allows users to create multiple accounts with minimal verification, giving threat actors anonymity. Threat actors can abuse this feature to create and manage numerous repositories for hosting malicious content while making it harder to trace the repositories to a known threat actor.
- It has a trusted reputation. Threat actors capitalize on this trust to bypass initial layers of security, as content hosted on GitHub is likely not subject to the same level of suspicion as content from less reputable sources.
- Its hosting and code management features enable malicious code to be stored and managed just as legitimate code, benefiting from GitHub’s robust infrastructure. GitHub has been used as a repository for malware, hosting pages that facilitate phishing attacks, and managing components of a larger malicious infrastructure.
- Its integration with development workflows. Many organizations integrate GitHub directly into their development pipelines. This integration allows threat actors to insert malicious code into software projects directly or through dependencies, potentially impacting large numbers of end-users.
- GitHub Pages and GitHub Actions. These features, designed for automating workflows and publishing web content, can be repurposed for malicious activities. GitHub Pages can host phishing sites, while GitHub Actions can automate and orchestrate complex attack sequences.
Threat actors can abuse GitHub for their infrastructure in four primary categories: payload delivery, DDR, full command and control (C2), and exfiltration. These infrastructure schemes are not mutually exclusive and can be combined. However, they do not rely on the exploitation vulnerabilities in GitHub services but instead leverage existing features.
Payload delivery is the most prevalent scheme in GitHub abuse. This scheme involves delivering malicious code to a target system and exploiting GitHub’s services to host malicious content, including legitimate open-source projects and data owned by threat actors. Threat actors, including cybercriminals and state-sponsored groups, have consistently been observed for several years using GitHub for payload delivery. Payload delivery abuse instances can be categorized into staging and infection-focused scenarios.
Staging via GitHub services refers to storing and delivering malicious code to a target system, regardless of the initial infection. Delivery mechanisms may occur via an alternative attack vector, such as (spear)phishing or vulnerability exploitation. In this context, malicious code can include legitimate open-source projects used as part of the attack chain or code and data owned by them or other threat actors. In contrast, in infection-focused scenarios, GitHub assumes a pivotal role in the initial infection process, achieved through methods like repository poisoning or creating fake repositories. Recent examples include:
- BitRAT Campaign (January 2023): Excel spreadsheets used as bait to distribute BitRAT. Malicious macros in the spreadsheet drop and execute payloads hosted on GitHub.
- HookSpoofer (March 2023): Utilizes GitHub to load auxiliary DLLs as part of its infection chain.
- DuckTail Campaign (March 2023): Targets Facebook’s Business Ads platform, downloads payload from GitHub.
- Metamorfo Campaign (August 2023): A phishing campaign that involved the download of a PowerShell script from GitHub.
- GitHub Repository Cloning (August 2022): a threat actor targeted approximately 35,000 of the most popular GitHub repositories, cloning them and inserting malicious code.
Threat actors can use GitHub as a dead drop resolver (DDR) by posting URLs, domains, or IP addresses in various formats, including encrypted files. Threat actors posting URLs, domains, or IP addresses, even in an open format, have a minimal immediate risk of GitHub removing the content, as it is difficult to discern malicious intent. Recent examples include:
- BlueDelta Campaign (September 2023): Uses GitHub Pages hosting HTTP redirect scripts, mimicking legitimate identifiers.
- SmoothOperator Attack (March 2023): Retrieves icon files from GitHub for C2 URL extraction.
- Hydra Variant (February 2023): Fetches a file from GitHub containing a JSON object with a list of C2 servers.
- Drokbk Malware (December 2022): Utilizes GitHub API to search for specific repositories for C2 server location.
Threat actors and malware using GitHub for Full C2 refers to a scenario where the threat actors and malware do not engage in direct communication but rely on GitHub as an “abstraction layer.” Recent examples include:
- HAMMERTOSS Backdoor (APT29, July 2015): Utilizes daily GitHub Pages URLs for retrieving encrypted instructions.
- Lazarus Group Campaign (January 2022): Uses GitHub for C2 communication and module loading.
- SLUB Backdoor (March 2019): Retrieves commands from GitHub gists, posts output in a private Slack channel.
GitHub’s use for exfiltration is less common compared to other schemes. Reasons for this include accessing data from open GitHub services appears less suspicious than actively posting information to GitHub, GitHub imposes file-size limits in repositories, issuing warnings for files exceeding 50 MB, while files added via the browser are restricted to 25 MB, and storing large files in GitHub’s Large File Storage (LFS) incurs additional charges. Using GitHub for exfiltration involves uploading gathered victim data to GitHub repositories, often through the GitHub API. Recent examples include:
- PowerShell Empire (2015): Features a GitHub exfiltration capability.
- Kimsuky Group (March 2023): Uploaded gathered victim data to GitHub in log file format.
- Rust-based Infostealers (January 2023): Utilize exposed ports on Codespaces instances to upload exfiltrate data as a JSON file.
- Source Code Exfiltration: Exfiltration of source code from internal GitHub repositories to personal or unapproved repositories is a significant risk, particularly in the context of insider threats and scenarios where threat actors seek to steal intellectual property by targeting source code.
GitHub is just one of several code repositories and version control platforms. Other platforms include GitLab, BitBucket, Codeberg, and Gitee. However, it is likely the most widely used platform. These other platforms, offering similar capabilities and advantages, are frequently abused for malicious purposes, primarily payload delivery. Threat actors may use these other platforms after conducting a thorough reconnaissance, adapting to the service usage patterns of their victims.
Abusing platforms like GitHub for malicious purposes serves to evade detection and complicates the detection process. Detecting such abuse within a specific environment depends on various factors, including the availability of logs and other resources, the organizational structure, and risk tolerance. There is no one-size-fits-all solution; instead, customers should consider a combination of detection strategies in addition to file-based detections. While organizations can apply specific detection strategies in a production environment, others are better suited for threat hunting.
Risk & Impact Assessment
The abuse of GitHub for malicious purposes presents multifaceted risks and impacts to organizations. These risks are not limited to direct security breaches but extend to broader implications affecting operational integrity, trust, and compliance. Firstly, the infiltration of malware into an organization’s systems via GitHub can lead to unauthorized access, data breaches, loss of intellectual property, and compromise of sensitive information. Secondly, given GitHub’s integration into many development workflows, the platform’s misuse poses a significant risk of supply chain attacks. Such attacks can have cascading effects, impacting not just a single organization but its partners and customers. Thirdly, abusing GitHub’s trusted status can lead to undetected malicious activity, undermining the security of organizational assets. Lastly, organizations may face compliance and legal risks if their infrastructure is unknowingly involved in hosting or distributing malicious content via GitHub.
Several factors are considered in assessing the material impact of GitHub’s abuse on a company’s business operations, results of operations, or financial condition. The scale and sophistication of the attack, the sensitivity of the data or systems targeted, and the organization’s reliance on GitHub for its operations are critical determinants. For companies heavily reliant on GitHub for software development and code management, the risk of a significant breach or a supply chain attack could materially impact business continuity and operational efficiency. Such breaches could lead to substantial financial losses, including remediation costs, fines for compliance violations, and loss of business due to reputational damage. For organizations where GitHub plays a less central role, the impact might be less severe but still noteworthy, especially regarding potential data breaches and legal ramifications. It is reasonably likely that an advanced, well-executed abuse of GitHub could materially impact a company’s operations, especially for those with high dependence on GitHub for their software development lifecycle.
Source Material: Recorded Future (PDF) Flying Under the Radar: Abusing GitHub for Malicious Infrastructure
Espionage Threat Actors Exploited Ivanti Connect Secure to Deploy Web Shells, Backdoors, and Credential Harvester
Vulnerability Exploitation – Malware – Ivanti Connect Secure CVE-2023-46805 & CVE-2024-21887 – LightWire – WireFire – WarpWire – ZipLine – UNC5221 – UTA0178 – Web Shell – Credential Harvesting – Backdoor -Cyber Espionage – Industries/All
Threat Analysis
Recently, we published a Customer Advisory detailing the exploitation of two zero-days in Ivanti Connect Secure VPN, now tracked as CVE-2023-46805 and CVE-2024-21887. In this ongoing investigation, Mandiant recently shared additional details, highlighting five malware families deployed by the threat actors (tracked as UNC5221 by Mandiant and UTA0178 by Volexity). The malware allows the threat actors to circumvent authentication and provide continued access to compromised devices. Currently, the number of organizations impacted by the exploitation is unknown. However, based on the language used in reports and specific known facts, we assume that post-exploitation activity occurred in a limited number of organizations.
We now know that following the successful exploitation of the zero-days (CVE-2023-46805 and CVE-2024-21887), the threat actors modified a Perl module used to execute a Perl script (sessionserver.pl) to remount the filesystem as read/write due to specific sections of the file system being read-only, then the script restores the original mount settings. This Perl script enabled the deployment of a dropper dubbed ThinSpool. Mandiant also observed the threat actors (UNC5221/UTA0178) leveraging the PySoxy tunneler and BusyBox to aid in post-exploitation activity.
According to Mandiant, ThinSpool is a dropper, written in shell script, that writes the web shell LightWire to a legitimate Connect Secure file (compcheckresult.cgi). If the appliance undergoes an update, ThinSpool re-adds the malicious web shell code to the legitimate file, enabling persistence on compromised devices. Additionally, ThinSpool attempted to evade Ivanti’s Integrity Checker by adding entries into files associated with the built-in tool, but these attempts failed.
LightWire is a web shell written in Perl CGI that enables arbitrary command execution. LightWire intercepts requests to compcheckresult.cgi where one of the parameters contains Base64-encoded and RC4-encrypted ciphertext. This ciphertext is decoded, interpreted, and executed as Perl code.
In addition to LightWire, Mandiant identified another web shell dubbed as WireFire. WireFire is written in Python and exists as trojanized logic to a component of the Connect Secure appliance. WireFire can download files to the compromised device and execute arbitrary commands. WireFire contains logic inserted before authentication that responds to specific HTTP POST requests to /api/v1/cav/client/visits. If form data entry “file” exists, the web shell saves the content to the device with a specified filename; if not, the web shell decodes, decrypts, and zlib decompress any raw data existing after a GIF header to execute as a subprocess. The output of the executed process will be zlib compressed, AES-encrypted with the same key, and Base64-encoded before being sent back as JSON with a “message” field via an HTTP 200 OK response. However, Mandiant does not describe if the threat actors deployed WireFire in conjunction with or separately from LightWire or how many compromised appliances it was deployed to.
In addition to deploying web shells, the threat actors harvested credentials by modifying a legitimate JavaScript file to insert malicious code dubbed WarpWire. This code targets credentials submitted during the web login to access layer 7 applications, like RDP, which are sent via an HTTP GET request to the command and control (C2) server in the following format: hxxps://symantke[.]com/?<username>&<password>. Unfortunately, Mandiant does not describe how many or which compromised appliances the threat actors deployed WarpWire to.
Mandiant also discovered a passive backdoor dubbed ZipLine to intercept network traffic. Once an incoming connection is registered, it checks if the process name is “web.” If so, the backdoor will retrieve up to 21 bytes from the connected host, verifying if it contains the string “SSH-2.0-OpenSSH_0.3xx.” If this string is present, ZipLine will receive an encrypted header specifying one of five commands to execute. These commands enable the backdoor to upload or download a file, establish a reverse shell, or create a proxy or tunneling server.
Upon initialization, ZipLine copies /etc/ld.so.preload to /tmp/data/root/etc/ld.so.preload, which will be executed if the process name is “dspkginstall.” ZipLine then copies itself to /tmp/data/root/home/lib. Upon termination, ZipLine first checks if the process name is tar. If the process name is tar, the backdoor executes different functionalities based on the provided parameters: -xzf, –exclude, or ./installer.
If the threat actors use the parameter -xzf, ZipLine executes the command: echo <formatted_sha256_string> >> ./installer/bom_files/<file_name>, which computes its own SHA256 hash, formats the line <sha256> ./root<self_fpath>, and then appends this string to each file within the ./installer/bom_files directory.
If the threat actors use the parameter –exclude, ZipLine will add itself to the Ivanti Integrity Checker Tool’s exclusion_list to evade detection.
If the threat actors use the parameter ./installer, ZipLine executes four sed commands, which delete specific lines from /pkg/do-install and ./installer/do-install.
sed Commands used to delete specific lines from /pkg/do-install and ./installer/do-install:
- sed -i ‘/retval=$(exec $installer $@)/d’ /pkg/do-install
- sed -i ‘/exit $?/d’ /pkg/do-install
- sed -i ‘/retval=$(exec $installer $@)/d’ ./installer/do-install
- sed -i ‘/exit $?/d’ ./installer/do-install
Again, Mandiant does not describe how the threat actors deployed ZipLine or how many compromised appliances had been infected with ZipLine.
As this is an ongoing investigation, Mandiant has not linked this activity to a previously known group, nor can they assess the origin of this threat actor. However, targeting edge infrastructure with zero-day vulnerabilities has been a consistent tactic espionage actors use to enable their operations. The exploitation of zero days, combined with Volexity’s findings, leads Mandiant to hypothesize this is an espionage-motivated APT campaign.
Risk & Impact Assessment
The exploitation of Ivanti Connect Secure VPN by the threat actors presents multifaceted risks to organizations. The vulnerabilities allow unauthorized access and control, potentially leading to unauthorized access, data breaches, and intellectual property theft. The deployment of web shells like LightWire and WireFire further amplifies the risk by enabling persistent access and command execution. It could result in long-term access going undetected within the network. Additionally, using WarpWire for credential harvesting poses significant risks of lateral movement within the network, potentially escalating to more sensitive systems and data. The cumulative impact of these risks includes potential loss of sensitive data, erosion of client trust, regulatory and legal consequences, and substantial remediation costs. Moreover, the targeted nature of the attack and its potential linkage to state-sponsored espionage increases the risk profile.
Given the nature and sophistication of the attack, there is a reasonable likelihood of a material impact on affected organizations’ business operations, results of operations, or financial condition. Organizations that have not yet detected or remediated the intrusion face the ongoing risk of data exfiltration and operational disruption. The long-term presence of threat actors in the network can lead to significant operational setbacks, including downtime, loss of competitive advantage, and damage to reputation. Financially, the costs associated with incident response, system upgrades, legal liabilities, and potential fines for regulatory non-compliance can be substantial. For companies in sectors where data security is paramount, the impact could extend to loss of market confidence and long-term financial repercussions. Therefore, organizations must assess their exposure to these vulnerabilities and take immediate action to mitigate the risks.
Source Material: Mandiant, Cutting Edge: Suspected APT Targets Ivanti Connect Secure VPN in New Zero-Day Exploitation
FBot, the Hacking Tool Designed to Hijack Cloud, SaaS, and Web Services
Hacking Tool – FBot – Cloud Hijacking – SaaS Hijacking – Web Services Hijacking -Credential Harvesting – AWS API Key Generation – Sendgrid API Key Generation – Industries/All
Threat Analysis
FBot, a newly identified Python-based hacking tool, targets services, such as widely used cloud services, like Amazon Web Services (AWS), and popular Software as a Service (SaaS) platforms like Office365. Additionally, it targets payment services like PayPal, email marketing, and communication services, including Sendgrid and Twilio. The capabilities include generators for random IP addresses and AWS and Sendgrid API keys, as well as various validators, checkers, and scanners.
The developer designed FBot to hijack cloud, SaaS, and web services, with a secondary focus on obtaining accounts to conduct spamming attacks. Actors can use the credential harvesting features to obtain initial access, which they can sell to other parties. However, it is currently unknown how threat actors access FBot, as no distribution channels have been identified, indicating that FBot is likely the product of private development work and may be distributed through a smaller-scale operation.
FBot, a Python-based hacking tool, exhibits unique characteristics that differentiate it from other cloud hacking tools. Its technical design and functionalities reveal a sophisticated tool in its approach to targeting cloud services and SaaS platforms. FBot does not use the widely-used Androxgh0st code but has similarities with the Legion cloud infostealer regarding functionality and design. FBot has a smaller footprint than similar tools, indicating possible private development and a more targeted distribution approach. Furthermore, SentinelOne has been unable to identify a distribution channel dedicated to FBot, differentiating the tool from other cloud infostealers often sold on Telegram. The developer may distribute builds through a smaller-scale operation, which aligns with the theme of cloud attack tools being bespoke ‘private bots’ tailored for the individual buyer, a theme prevalent among AlienFox builds.
FBot has three functions dedicated to AWS account attacks: API key generation, checking email configuration details, and EC2 service quota checks. The AWS API Key Generator generates a random AWS access key ID by appending 16 randomly selected alphabetic characters to the standard AKIA prefix. Then, it generates a secret key from 40 randomly selected alphabetic characters. However, this feature is unlikely to succeed at brute forcing account credentials due to the possible number of access key and password combinations.
The second AWS feature is a Mass AWS Checker, which checks for AWS Simple Email Service (SES) email configuration details, including the maximum send quota and rate, as well as how many messages have been sent in the past 24 hours, likely to maximize spamming efforts against the targeted account. It also creates a new user account with the username iDevXploit and the password MCDonald2021D#1337 and elevates privileges for the new account by attaching the AdminsitratorAccess policy. Unlike other cloud attack tools, FBot does not delete the compromised account the attacker used to gain access.
The final AWS feature is an AWS EC2 Checker, with the description Get EC2 VCPU Limit. This function reads a list of AWS identities from a text file and then uses these values to check the targeted account’s EC2 service quotas. The FBot menu highlights that this can be used to check vCPU details. The function’s result describes the account’s EC2 configurations and capabilities, such as what type of EC2 instances can run. The script will also iterate through a list of specified AWS regions, rerun the query for each region, and logs the result to a text file.
The PayPal Validator feature validates PayPal account status by contacting a hardcoded URL (www.robertkalinkin[.]com/index.php) with an email address read from an input list to validate whether an email address is associated with a PayPal account. The script initiates the PayPal API request via this hardcoded website. Currently, all known FBot samples use this website to authenticate the PayPal API requests, as well as several Legion Stealer samples. The PayPal Validator crafts the request to this site with a fake item ID and phony customer details, then parses the response for a status message indicating success.
FBot also targets the SaaS platforms Sendgrid and Twilio. The Sendgrid feature is a Sendgrid API Key Generator, which generates a Sendgrid key formatted like SG.{22 characters from [A-Z0-9-_]}.{1 more character from previous range}. The Twilio feature takes the Twilio SID and Twilio Auth Token as input, separated by a pipe (“|”), then checks the SID & auth token combination for details about the account, including the balance and which currency and a list of phone numbers connected to the account.
Risk & Impact Assessment
FBot’s emergence as a Python-based hacking tool, mainly targeting cloud services and payment systems, may introduce considerable organizational risks. Its credential harvesting and hijacking cloud, SaaS, and web services directly threaten the security of these systems. Companies using AWS, PayPal, Sendgrid, and Twilio face heightened risks of unauthorized access and operational disruptions. The impacts of such breaches are not limited to immediate financial losses but extend to operational disruptions and reputational damage due to compromised data integrity and client trust.
The presence of FBot in an organization’s network infrastructure is reasonably likely to have a material impact on business operations. The tool’s focus on cloud and payment services directly threatens these sectors’ operational functionalities. The potential for threat actors to hijack these services for malicious purposes may result in financial losses and necessitate costly mitigation efforts, including legal liabilities and system restoration. Overall, the risk posed by FBot is not only a direct security concern but also a critical factor in the broader context of an organization’s operational stability and financial health.
Source Material: SentinelOne, Exploring FBot | Python-Based Malware Targeting Cloud and Payment Services
New Infostealer Campaign Exploits Windows Defender SmartScreen Vulnerability (CVE-2023-36025)
Malware – Infostealer – Vulnerability Exploitation – Microsoft Windows Defender CVE-2023-36025 – Phemedrone Stealer – GitHub Abuse – Industries/All
Threat Analysis
Recently, Trend Micro discovered a campaign exploiting CVE-2023-36025, a security feature bypass vulnerability in Microsoft Windows Defender SmartScreen. Exploiting this vulnerability allowed the threat actors to deploy a previously unknown infostealer, Phemedrone, through a multi-stage infection process.
Phemedrone, like most infostealers, targets data from web browsers, cryptocurrency wallets, and messaging apps, including Telegram, Steam, and Discord. It can take screenshots and gather detailed system information such as hardware, location, and operating system details. The stealer then exfiltrates the stolen data to the threat actors via Telegram or their command-and-control (C2) server. Furthermore, Phemedrone, first released in late August 2023, is publicly available on GitHub and Telegram and written in C#.
Microsoft patched CVE-2023-36025 on 14 November 2023. However, this vulnerability has been widely demonstrated, and proof-of-concept (PoC) exploit codes have been shared on social media, contributing to its exploitation in various malware campaigns. Due to its active exploitation in the wild, the Cybersecurity and Infrastructure Security Agency (CISA) added it to its Known Exploited Vulnerabilities (KEV) catalog.
This Phemedrone Stealer campaign initiated its infection chain using malicious Internet Shortcut files (.url) [VT link]. The threat actors crafted these files to exploit CVE-2023-36025 to deploy additional payloads to execute the subsequent stages. However, the exact method of distributing these .url files is unknown, but potential vectors include phishing emails (through links or attachments), drive-by downloads, or fake browser updates and software cracks.
Upon the user interacting with the malicious .url file, it connects to an actor-controlled server to download and execute the initial loader, a control panel item file (pdf3.cpl), leveraging the Windows Control Panel process binary (control.exe) to run pdf3.cpl which has been renamed ControlPanelMarker.dll (VT link). When the Windows Control Panel process binary executes the .cpl file, it, in turn, calls rundll32.exe to execute ControlPanelMarker.dll. This malicious DLL executes an Invoke Expression PowerShell command to download and run a file named DATA3.txt from GitHub [VT Link].
DATA3.txt is an obfuscated loader that uses PowerShell string and digit manipulation techniques to mask its contents. DATA3.txt contains a series of PowerShell commands that, when executed, download a ZIP file (maybe DATA3.zip/VT Link) hosted on the same GitHub repository to a hidden directory created using the Windows attribute utility attrib.exe. This zip archive contains three files: WerFaultSecure.exe, a legitimate Windows Fault Reporting binary; Wer.dll, a malicious binary sideloaded when WerFaultSecure.exe is executed; and Secure.pdf, an RC4-encrypted loader [VT Link].
When WerFaultSecure.exe sideloads the malicious DLL wer.dll, it decrypts and runs the loader (Secure.pdf) and achieves persistence by creating scheduled tasks. The malicious DLL utilizes techniques such as VMProtect packing and protection, API hashing, and string encryption to evade detection and complicate reverse engineering.
The DLL maintains persistence by creating the directory C:\Users\Public\Libraries\Books and copies WerFaultSecure.exe, wer.dll, and Secure.pdf from the current execution directory to this location. It then executes the schtasks.exe command, scheduling the WerFaultSecure.exe to run at 90-minute intervals.
The DLL then advances to the next stage, wherein the encrypted loader (Secure.pdf) is decrypted, utilizing an undocumented function in advapi32.dll. It then uses two functions from Activeds.dll to allocate memory and relocate the decrypted content. Finally, it calls VirtualProtect to modify the memory region of the decrypted buffer to Executable-Read-Write. The DLL then uses API callback functions to redirect the execution flow to the next stage, executing the loader.
The actor used a utility known as Donut (GitHub Link), embedding it directly into the loader. This open-source shellcode enables the execution of VBScript, JScript, EXE files, DLL files, and .NET assemblies in memory. For the final payload execution, Donut is configured to load and execute Phemedrone Stealer in memory and delete the original reference to deter memory scanners.
When executed, the stealer initializes its configuration and decrypts certain items, such as a Telegram API token, chat ID, and a mutex. Additionally, Phemedrone Stealer performs checks to ensure that it doesn’t operate concurrently with another instance of itself.
The stealer then gathers extensive system information and statistics, including geolocation data, hardware information, sensitive data from web browsers, and details about installed antivirus products. Then, the stealer exfiltrates a ZIP-compressed data stream, sending a Telegram API HTTP POST request; this data stream is sent as a “document” through this request.
The stealer also generates a summary report detailing the data collected and exfiltrated. This report includes information about the compromised system and user data, encompassing various items, including geolocation, hardware specifications, the number of passwords, cookies, credit cards, extensions, wallets, and files collected and exfiltrated, and installed security solutions and locations.
At this time, the Adversary Tactics and Intelligence team has been unable to locate any data stolen by Phemedrone Stealer for sale on cybercriminal marketplaces. However, this does not mean that organizations have not been impacted. The threat actor may post stolen data for sale later after processing them, or they may have no intention of reselling it, choosing instead to use the data to conduct further malicious operations.
Risk & Impact Assessment
The exploitation of CVE-2023-36025 by this Phemedrone Stealer campaign presents a multifaceted risk to organizations. The primary risk lies in the unauthorized access and exfiltration of credentials from web browsers, cryptocurrency wallets, and messaging applications. This data breach can significantly impact confidentiality, integrity, and availability. The sophisticated evasion techniques employed and the use of legitimate services like GitHub for payload delivery amplify the risk by reducing the likelihood of early detection. Additionally, the campaign’s ability to gather extensive system information poses a risk of detailed reconnaissance, potentially facilitating further targeted attacks. The impact of such a campaign can range from financial losses due to stolen credentials and fraud to reputational damage and loss of customer trust.
While the initial theft of credentials is a serious security concern, it may not directly result in a material impact on an organization’s operations or financial condition. The real threat emerges when these credentials are used for unauthorized access within corporate environments, leading to more severe actions like data breaches, ransomware, or espionage. These subsequent malicious activities can substantially disrupt operations and incur significant financial losses, legal repercussions, and reputational damage. Hence, the material impact becomes markedly significant and likely when the stolen credentials facilitate further intrusions and sophisticated network attacks, underscoring the need for vigilant monitoring and prompt response to unauthorized activities.
Source Material: Trend Micro, CVE-2023-36025 Exploited for Defense Evasion in Phemedrone Stealer Campaign
Latest Additions to Data Leak Sites
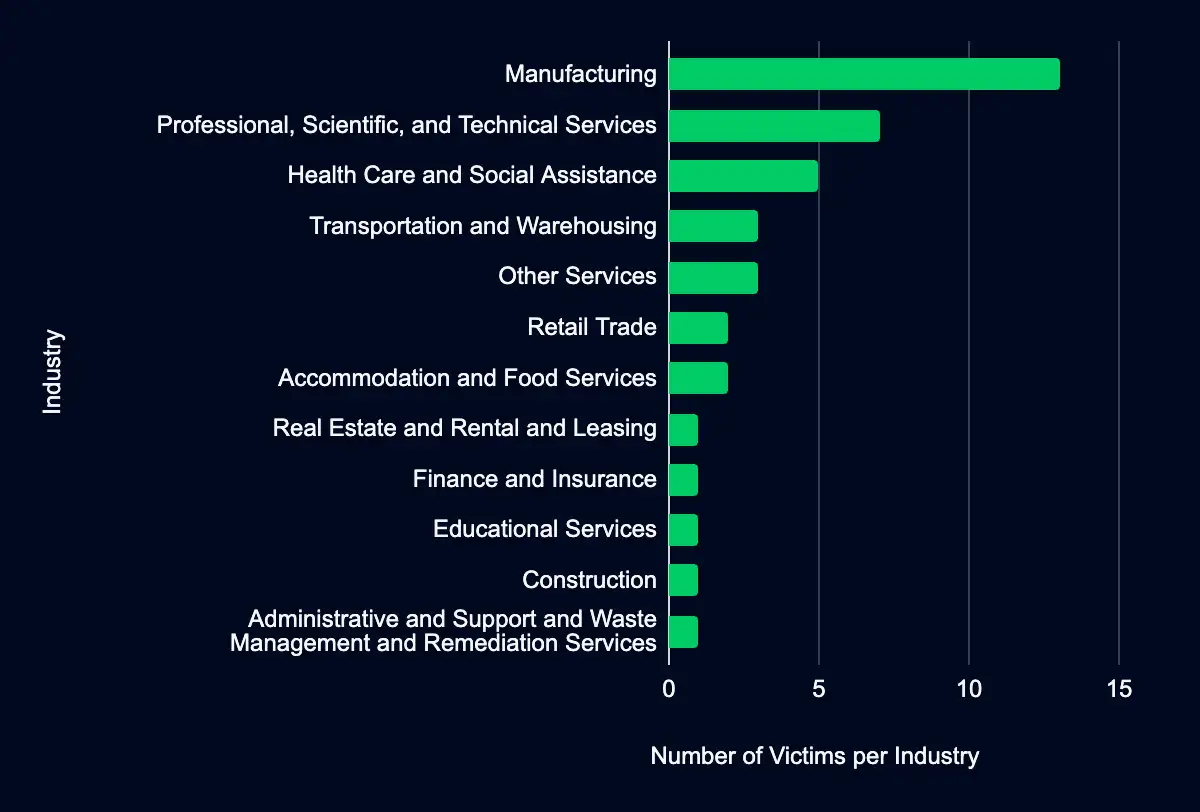
Manufacturing – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Transportation and Warehousing – Other Services
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. Forty organizations have been listed as victims in the past week, with a marked concentration in the USA, accounting for 55% of the total incidents. This geographic focus may indicate a higher targeting preference in this region. Regarding industry targeting, the data reveals a diverse range of sectors being affected, with manufacturing leading the list at 33%, followed by Professional, Scientific, and Technical Services (18%), Health Care and Social Assistance (13%), Transportation and Warehousing (8%), and Other Services (8%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base.
Lockbit
Lockbit, accounting for 23% of the incidents in the dataset, predominantly targeted organizations in the USA but also had victims in Europe, Asia, and Africa. While a notable number of their attacks are in the USA (5), their large affiliate base likely accounts for their extensive geographical reach. The spectrum of industries Lockbit targets is equally varied, extending beyond Manufacturing and Other Services to encompass sectors such as Professional, Scientific, and Technical Services and Accommodation and Food Services. This variety in targets underscores Lockbit affiliates’ opportunistic and versatile approach, possibly driven by the availability of opportunities across sectors.
ALPHV/Blackcat
ALPHV, accounting for 18% of the incidents in the dataset, shows a somewhat diverse targeting pattern but not entirely without geographic or sector preferences. ALPHV’s targets include organizations primarily in Canada, indicating that an ALPHV affiliate (or affiliates) focused on this country. ALPHV’s victims were predominantly in the Professional, Scientific, and Technical Services and Manufacturing sectors. However, they also had victims in the Finance and Insurance and Construction sectors.
This data suggests that while ALPHV is opportunistic, there is a slight inclination towards specific industries and regions. For instance, their recent activities in Canada and their focus on the Professional, Scientific, and Technical Services and Manufacturing sectors indicate a strategy that balances opportunism with selective targeting, possibly influenced by the perceived value of data or the ability to pay ransom. Their activities still underscore the unpredictable nature of ransomware groups, but with a nuanced approach that considers both opportunity and potential payoff.
Other Groups
The activities of Cactus, 8base, and Qilin account for a larger fraction of the total incidents, collectively responsible for 33% of the cases, offering valuable insights into the diversity of the ransomware threat landscape. Cactus exhibits a focused but dispersed approach with all victims located in the USA in various industries such as manufacturing, retail trade, health care, and social assistance. This pattern suggests a focus on a specific geographic area but opportunistic in their sectoral preference, pointing towards a strategy that might prioritize opportunistic or easy targets over any particular industry or region. 8base and Qilin, collectively behind eight of the 40 victims, highlight the role of smaller yet consistently active players in the ransomware arena. 8base victims operated mainly in manufacturing, indicating a potential niche targeting strategy. Qilin’s victims from the Retail Trade, Professional, Scientific, and Technical Services, and Accommodation and Food Services sectors also suggest a specific targeting approach, possibly influenced by the perceived value of these sectors.
CISA Adds 4 CVEs to Known Exploited Vulnerabilities Catalog
Citrix NetScaler ADC and NetScaler Gateway CVE-2023-6548 – Citrix NetScaler ADC and NetScaler Gateway CVE-2023-6549 – Google Chromium V8 CVE-2024-0519 – Laravel CVE-2018-15133
In the past week, CISA added 4 CVEs to its Known Exploited Vulnerabilities Catalog, impacting Citrix, Google, and Laravel products. These vulnerabilities can have severe consequences, including remote code execution, command injection, and denial-of-service. Explore the report and grasp CISA’s mitigation recommendations.
The two vulnerabilities (CVE-2023-6548 & CVE-2023-6549) impacting Citrix NetScaler ADC and NetScaler Gateway are the second and third vulnerabilities in Citrix appliances that Citrix has disclosed in the last four months. Notably, in October, Citrix patched CVE-2023-4966, a critical flaw in NetScaler appliances called “CitrixBleed” that was widely exploited by various threat actors. Fortunately, the impact of these two vulnerabilities is not expected to be as significant as CitrixBleed. According to Citrix, these vulnerabilities have been exploited in the wild. However, Citrix did not share any details about in-the-wild exploitation. CISA has set a mitigation due date for CVE-2023-6548 of 24 January and a mitigation due date for CVE-2023-6549 of 7 February.
The vulnerability (CVE-2024-0519) impacting Google Chromium V8 results from an out-of-bounds memory access vulnerability. As is custom for Google, they will not release details of the exploitation until a majority of users have updated their browsers. However, based on limited information, leveraging this vulnerability could enable a threat actor to remotely exploit a user’s web browser by visiting a malicious web page, requiring social engineering to direct the victim to that page. Successful exploitation may allow the threat actor access to sensitive information such as passwords, credit card numbers, or other personal data stored in the user’s browser. Furthermore, the attacker could also cause the browser to crash, leading to further exploitation or denial of service attacks. CISA has set a mitigation due date of 7 February.
The final vulnerability (CVE-2018-15133) added this week impacts the Laravel Framework and allows for remote code execution. A threat actor can only exploit this vulnerability if they have accessed the application encryption key (APP_KEY environment variable). Numerous publicly available exploits and publications on the vulnerability’s technical details significantly lower the barrier for threat actors to exploit it. CISA has set a mitigation due date of 6 February.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2018-15133 | Laravel | Laravel Framework | Laravel Framework contains a deserialization of untrusted data vulnerability, allowing for remote command execution. This vulnerability may only be exploited if a malicious user has accessed the application encryption key (APP_KEY environment variable). | 2/6/24 | Unknown |
| CVE-2024-0519 | Chromium V8 | Google Chromium V8 contains an out-of-bounds memory access vulnerability. Specific impacts from exploitation are not available at this time. | 2/7/24 | Unknown | |
| CVE-2023-6549 | Citrix | NetScaler ADC and NetScaler Gateway | Citrix NetScaler ADC and NetScaler Gateway contain a buffer overflow vulnerability that allows for a denial-of-service when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. | 2/7/24 | Unknown |
| CVE-2023-6548 | Citrix | NetScaler ADC and NetScaler Gateway | Citrix NetScaler ADC and NetScaler Gateway contain a code injection vulnerability that allows for authenticated remote code execution on the management interface with access to NSIP, CLIP, or SNIP. | 1/24/24 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share