Androxgh0st Spooks Targets, Iranian APT Spear Phishing, North Korean ScarCruft Campaign Planning, and Critical Vulnerabilities in Confluence
This week: Androxgh0st targets AWS, Office 365, SendGrid, and Twilio, Iranian threat actors are targeting universities and research centers through spear phishing, campaign planning by North Korean ScarCruft is exposed, and massive attempts are made at a vulnerability in Confluence Data Center and Confluence Server –all this plus the latest from data leak sites and three new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Androxgh0st Targets AWS, Office 365, SendGrid, and Twilio for Spamming, Web Shell Deployment, Exploits SMTP for Malicious Activities
- Iranian Operators Target High-Profile Individuals at Universities and Research Centers in Spear Phishing Campaign
- ScarCruft Likely Planning Future Campaign to Target Korean-Speaking Consumers of Threat Intelligence
- Massive Exploitation Attempts Observed Targeting Critical Vulnerability In Confluence Data Center and Confluence Server
- Latest Additions to Data Leak Sites
- CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
Androxgh0st Targets AWS, Office 365, SendGrid, and Twilio for Spamming, Web Shell Deployment, Exploits SMTP for Malicious Activities
Hacking Tool – Vulnerability Exploitation – PHPUnit CVE-2017-9841 – Laravel Framework CVE-2018-15133 – Apache Web Server CVE-2021-41773 – Androxgh0st – Spamming – Web Shell – SMTP Abuse – Industries/All
Threat Analysis
Based on open-source reporting, Androxgh0st is actively exploiting multiple vulnerabilities, specifically CVE-2017-9841 (PHPUnit), CVE-2018-15133 (Laravel Framework), and CVE-2021-41773 (Apache Web Server), and targeting exposed Laravel environment files (.env) to spread and facilitate spamming operations. Many cloud services such as AWS, Office 365, SendGrid, and Twilio use the Laravel .env files as a repository for environment variables, which are key-value pairs that store sensitive or configuration-specific information. Androxgh0st has numerous functions that abuse the Simple Mail Transfer Protocol (SMTP). These functions include scanning and utilizing exposed credentials and Application Programming Interfaces (APIs) and deploying web shells. According to Fortinet’s data, on 17 January alone, the AndroxGh0st.Malware IPS signature was triggered 36,541 times and averages about 40,000 events daily.
Exploitation of CVE-2017-9841 (PHPUnit)
Websites using the PHPUnit module that have the /vendor folders publicly accessible may be vulnerable to CVE-2017-9841 and are subject to Androxgh0st sending malicious HTTP POST requests to the uniform resource identifier (URI) /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php. This PHP page executes PHP code submitted through a POST request. Threat actors likely use Androxgh0st to download malicious files, like coinminers and webshells, to the website’s host system. Furthermore, actors can create an unauthorized page to provide backdoor access to the website, allowing them to download additional malicious files to conduct their operations and access the website’s databases.
Laravel Framework Targeting and Exploitation
Androxgh0st establishes a botnet to scan for websites using the Laravel web application framework and identify publicly exposed root-level .env files. These .env files contain environment variables that include confidential information, such as credentials and configuration-specific information. Many cloud services such as AWS, Office 365, SendGrid, and Twilio use the Laravel .env files as a repository for environment variables.
If .env files are exposed, Androxgh0st will issue a GET request to the /.env URI to access the sensitive data. Alternatively, Androxgh0st may issue a POST request to the same URI with a POST variable named 0x[] containing data frequently used as an identifier for the threat actor. A successful response from either of these methods allows the threat actors to search for usernames, passwords, credentials, or a combination of these that would allow access to services such as email via SMTP and AWS accounts.
Androxgh0st can also access the Laravel application key for the website If the threat actors successfully identify the Laravel application key. They will attempt exploitation of CVE-2018-15133 by encrypting a PHP payload with the application key and crafting an HTTP GET request with the payload as an XSRF token cookie.
Exploitation of CVE-2021-41773 (Apache Web Server)
Androxgh0st can also scan web servers running Apache HTTP Server versions 2.4.49 or 2.4.50, which are vulnerable to CVE-2021-41773. This vulnerability allows threat actors to map URLs to sensitive files outside the root directory through a path traversal attack. If these files are not protected by the “request all denied” configuration and Common Gateway Interface (CGI) scripts are enabled, this could allow for remote code execution.
Post-Exploitation Activity
If threat actors obtain credentials for any services using the above methods, they may use these credentials to access sensitive data or use these services to conduct additional malicious activity. For example, when threat actors successfully identify and compromise AWS credentials from a vulnerable website, they have been observed attempting to create new users and user policies with admin privileges. Additionally, Andoxgh0st actors have been observed creating new AWS instances to conduct additional scanning activity. In some cases, the exploitation of CVE-2017-9841 has resulted in the deployment of various malware families, like XMRig coinminer.
Risk & Impact Assessment
The pervasive nature of Androxgh0st, exploiting vulnerabilities like CVE-2017-9841, CVE-2018-15133, and CVE-2021-41773, presents substantial risks to organizations. The primary risk is unauthorized access to sensitive data, which could result in account compromise. These compromises risk the exposure of client and proprietary data and pose a risk of intellectual property theft. Furthermore, Androxgh0st’s ability to deploy web shells and create unauthorized backdoor access escalates the threat, potentially leading to prolonged and undetected presence in the network. This persistent access could affect critical operational functionalities, resulting in operational downtime and financial losses. Abusing SMTP functions for malicious activities amplifies the risk of hijacking resources to facilitate widespread phishing attacks. Additionally, the reputational damage from such compromises could lead to a loss of customer trust and potential legal repercussions, especially for organizations subject to stringent data protection regulations.
The techniques of Androxgh0st are sophisticated enough to warrant a significant concern about material impacts on a company’s operations. The malware’s ability to target commonly used frameworks and web servers means many businesses could be at risk. When sensitive data is accessed or compromised, companies may face immediate operational disruptions and long-term impacts on their financial condition. The costs associated with remediation, legal liabilities, and loss of business due to customer mistrust could be substantial. Furthermore, if threat actors succeed in using compromised AWS credentials to create new instances for further malicious activities, the financial implications could escalate rapidly, given the potential for cloud resource misuse and associated costs. Companies should be acutely aware of these risks, as Androxgh0st’s capabilities align with threat vectors that are reasonably likely to cause material impacts on business continuity, operational integrity, and financial stability.
Source Material: CISA, Known Indicators of Compromise Associated with Androxgh0st Malware; Fortinet, Androxgh0st Malware Attack
Iranian Operators Target High-Profile Individuals at Universities and Research Centers in Spear Phishing Campaign
Spear Phishing – Malware – Threat Actor – Mint Sandstorm – Phishing Link – RAR Archive – Backdoor – MediaPl – MischiefTut – Educational Services – Other Services
Threat Analysis
Since November 2023, operators attributed to a subgroup of the Islamic Revolutionary Guard Corps (IRGC), tracked as Mint Sandstorm, have targeted high-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the United Kingdom, and the United States in a spear phishing operation to maintain persistence and steal information for intelligence collection purposes. In a limited number of cases, operators employed new post-intrusion tradecraft, including using a new, custom backdoor called MediaPl.
To initiate contact with targets, the operators impersonated high-profile individuals, including a journalist at a reputable news outlet. In some cases, they used an email address that resembled the personal email account belonging to the individual they sought to impersonate. In other instances, they used legitimate but compromised email accounts of individuals they sought to impersonate. Initial emails contained no malicious content and asked if the target would be willing to review an article about the Israel-Hamas war.
If targets agreed to review the article or document referenced in the initial email, operators followed up with an email containing a link to a malicious domain. Domains, such as cloud-document-edit[.]onrender[.]com, hosted a RAR archive (.rar) file that purportedly contained the draft document the operators asked the targets to review. If opened, this .rar file decompresses into a double extension file (.pdf.lnk) with the same name. When launched, this file ran a curl command to retrieve malicious files from actor-controlled subdomains of glitch[.]me and supabase[.]co.
Microsoft observed multiple files downloaded to targets’ devices in this campaign, notably several .vbs scripts. In several instances, Microsoft observed a renamed version of NirCmd. This legitimate command line tool allows a user to perform several actions on a device without displaying a user interface on a target’s device.
Persistence
Sometimes, the threat actor used a malicious file, persistence.vbs, to persist in the targets’ environments. Persistence.vbs added a file, typically named a.vbs, to the CurrentVersion\Run registry key when run. In other cases, operators created a scheduled task to reach out to an actor-controlled subdomain of supabase[.]co and download a .txt file.
Collection
Activity observed in this campaign suggests that the operators wrote data from targets’ devices to a series of text files, notably one named documentLoger.txt. In addition to this activity, in some cases, Mint Sandstorm dropped MischiefTut or MediaPl custom backdoors.
MediaPl
MediaPl, configured to masquerade as Windows Media Player, is a custom backdoor that sends encrypted communications to its C2 server. As the backdoor masquerades as an audio and video media player, operators typically drop a DLL file in C:\\Users\\[REDACTED] \\AppData\\Local\\Microsoft\\Media Player\\MediaPl.dll. When the operators run MediaPl.dll with the path of an image file provided as an argument, it launches the image in the Windows Photo application and parses it for C2 information. Communications to and from MediaPl’s C2 server are AES CBC encrypted and Base64 encoded. As of this writing, MediaPl can terminate itself, pause and retry communications with its C2 server, and launch command(s) it has received from the C2.
MischiefTut
MischiefTut is a custom backdoor implemented in PowerShell that can run reconnaissance commands, write outputs to a text file, and, ostensibly, send outputs back to actor-controlled infrastructure. MischiefTut can also be used to download additional tools on a compromised system.
Risk & Impact Assessment
Microsoft attributed this campaign to the Islamic Revolutionary Guard Corps (IRGC). Its primary objective is to collect intelligence from individuals at universities and research institutions specializing in Middle Eastern affairs. This campaign poses a significant risk of exposing sensitive information that could provide strategic insights into policy-making and academic research related to the Middle East. This data could be leveraged to anticipate and counter international policies on the Middle East and strategically shape diplomatic relations and negotiations, altering the geopolitical climate. This information could also be leveraged to influence operations, future espionage operations, and inform internal strategic decisions. Therefore, taking appropriate measures to protect this information from being compromised is crucial. Such exposure could undermine the credibility of these institutions, leading to potential reputational damage in the global academic and policy community. Additionally, the need to counteract these sophisticated cyber threats may divert resources and focus away from primary research activities. While data alteration seems unlikely, the unauthorized access and potential exfiltration of information could give adversaries strategic insights, indirectly influencing policy and research developments related to the Middle East.
Source Material: Microsoft Threat Intelligence, New TTPs observed in Mint Sandstorm campaign targeting high-profile individuals at universities and research orgs
North Korean Threat Actor Likely Planning Future Campaign to Target Korean-Speaking Consumers of Threat Intelligence
Malware – Threat Actor – ScarCruft – RokRAT – Backdoor – Spear Phishing – Malicious LNK Files – Industries/All
Threat Analysis
While investigating campaigns targeting experts in North Korean affairs from South Korea’s academic sector and a news organization focused on North Korea attributed to ScarCruft, SentinelOne recovered malicious files likely intended for a future campaign, one of which delivers the RokRAT backdoor, a fully-featured backdoor equipped with capabilities that enable its operators to surveil targeted entities. The backdoor uses public Cloud services such as pCloud and Yandex Cloud for command-and-control, disguising malicious communication as legitimate network traffic.
The infection chain for inteligence.lnk involves the execution of PowerShell code that:
- First, extract and display a decoy PDF document (inteligence.pdf) contained in inteligence.lnk.
- Secondly, it downloads a hex-encoded file (story.txt) from a prominent cloud hosting provider.
- Finally, it decodes the story.txt file and executes the decoded content in a thread. However, at this time, story.txt implements a benign shellcode that opens notepad.exe. Furthermore, inteligence.lnk does not run a Windows Batch script or an external PowerShell script.
The infection chain for news.lnk reveals a fully operational file whose implementation and functionality are very similar to that performed by inteligence.lnk, with a modification:
- First, it executes PowerShell code that downloads a file named story3.txt from a remote server.
- Then, story3.txt displays a decoy document.
- Third, story3.txt executes the shellcode embedded in news.lnk instead of downloading it from a remote hosting provider.
- Finally, unlike inteligence.lnk, the shellcode embedded in news.lnk deploys the RokRAT backdoor.
Both LNK files deploy the same decoy document – a publicly accessible research report on the Kimsuky threat group by Genians, a South Korean cybersecurity company. The report is written in Korean and was published on 30 October 2023.
Targeting personnel interested in threat intelligence on the Kimsuly group indicates that ScarCruft may have an objective to collect closed-source threat intelligence on this group. This data could benefit ScarCruft and other North Korean groups, aiding them in identifying operational security lapses to improve future operations.
Campaign Targeting South Korea’s Academic Sector and a South Korean News Agency. On 13 December 2023, ScarCruft operators impersonated a North Korea Research Institute member, sending a spear phishing email to an expert in North Korean affairs. The email had an attached ZIP archive file, which contained nine files. The files masqueraded as presentation materials from a fabricated event — a human rights expert discussion meeting.
Seven of the nine files are benign Hangul Word Processor (HWP) and PowerPoint documents, while two are malicious LNK files. All files have names related to human rights in North Korea. Furthermore, the LNK files disguise themselves as Hanword documents using the Hangul Word Processor icon. The LNK files exceed 48 MB and implement a multi-stage infection chain that deploys the RokRAT backdoor.
The LNK files execute PowerShell code that performs the following actions:
- First, locate the executing LNK file based on its file size.
- Then, extract from the LNK file a decoy document, a Windows Batch script named 111223.bat, and a PowerShell script named public.dat.
- Third, the PowerShell code displays the decoy document and executes 111223.bat.
- 111223.bat then executes a PowerShell script stored in public.dat, which decodes and executes another hex-encoded PowerShell script embedded in public.dat.
- The decoded script embedded in public.dat downloads an encrypted ZIP archive from a prominent Cloud hosting provider, decrypts the file, and executes the decrypted content.
- Finally, the ZIP archive implements shellcode that deploys the RokRAT backdoor.
Risk & Impact Assessment
The malicious ScarCruft files (inteligence.lnk and news.lnk) infection chains exemplify moderate sophistication, increasing the likelihood of successful malware deployment. ScarCruft has demonstrated capabilities that include using deceptive file names, leveraging legitimate cloud services for command-and-control operations, and deploying multi-stage infection chains. These tactics increase the likelihood of avoiding detection and bypassing standard security measures and suggest meticulous planning and resource allocation indicative of a well-funded and skilled adversary.
The potential targets, primarily Korean-speaking targets likely interested in Kimsuky threat intelligence, are at a heightened risk due to their specific interests and access to sensitive information. Given that these entities likely do not face attacks of this nature, their vulnerability to such attacks is elevated. However, these targets are typically more security-conscious, and future campaigns may be less successful. The probability of a successful malware deployment is further compounded by the observed evolutions in ScarCruft’s operational tactics, aimed at evading detection based on their previously known techniques.
Should ScarCruft’s campaign successfully breach its targets, the consequences could be far-reaching and severe. The primary concern is the exfiltration of sensitive data. Furthermore, the backdoor’s surveillance capabilities present a significant threat, potentially leading to a continuous compromise of operational security. Intellectual property, particularly in the form of intelligence research and unpublished reports, is at risk of theft, which could have extensive long-term repercussions for the credibility and competitive standing of the affected organizations. Additionally, this campaign could extend beyond immediate data theft to establishing a long-term presence within the targeted networks for ongoing espionage activities. Given the strategic nature of the information held by the targeted entities, the material impact on their business operations, results of operations, or financial condition could be substantial.
Source Material: SentinelOne, ScarCruft | Attackers Gather Strategic Intelligence and Target Cybersecurity Professionals
Massive Exploitation Attempts Observed Targeting Critical Vulnerability In Confluence Data Center and Confluence Server
Vulnerability Exploitation – Atlassian Confluence Data Center and Confluence Server CVE-2023-22527 – Industries/All
Threat Analysis
Two security research outlets have observed threat actors exploiting a recently disclosed critical vulnerability impacting Atlassian Confluence Data Center and Confluence Server, tracked as CVE-2023-22527 (CVSS score: 10.0), within three days of public disclosure. The vulnerability allows unauthenticated threat actors to achieve remote code execution on vulnerable installations.
As early as 22 January, according to the Shadowserver Foundation, nearly 40,000 exploitation attempts targeting CVE-2023-22527 have been recorded from more than 600 unique IP addresses. The activity is currently limited to “testing callback attempts and ‘whoami’ execution,” suggesting opportunistic scanning for vulnerable servers, potentially for follow-on exploitation. Most IP addresses are from Russia (22,674), followed by Singapore (9,638), Hong Kong (3,002), and the US (1,936). Additionally, The DFIR Report tweeted their observations of an exploitation attempt against Confluence, capturing a POST request to execute whoami.
According to the Shadowserver Foundation data, over 11,000 Atlassian instances are internet accessible as of 22 January. However, it’s unknown how many of them are vulnerable to CVE-2023-22527. Based on a technical analysis conducted by Project Discovery, the vulnerability has the potential to allow unauthenticated threat actors to execute arbitrary code and system commands by injecting OGNL expressions into the Confluence instance.
The vulnerability affects Confluence Data Center and Server versions 8.0.x, 8.1.x, 8.2.x, 8.3.x, 8.4.x, and 8.5.0 through 8.5.3. Atlassian has released a fix for Confluence Data Center and Server versions 8.5.4 (LTS), 8.6.0 (Data Center only), 8.7.1 (Data Center only), and later versions. However, these fixes are not the most up-to-date versions and do not protect your instance from other non-critical vulnerabilities. The latest Confluence Data Center and Confluence Server fixes are version 8.5.5 (LTS) and 8.7.2 for Data Center only.
Risk & Impact Assessment
While initial exploitation events have likely centered on identifying vulnerable instances, the sheer number of events suggests that threat actors will identify vulnerable systems for exploitation, posing significant risks to organizations. Successful exploitation would result in remote code execution to facilitate post-exploitation activity, which could include deploying malware, such as remote access trojans, backdoors, and ransomware, and result in data exfiltration. This activity could affect critical operational functionalities, resulting in operational downtime and financial losses. Additionally, the reputational damage from such attacks could lead to a loss of customer trust and potential legal repercussions, especially for organizations subject to stringent data protection regulations.
The CVE-2023-22527 vulnerability poses a significant risk of exploitation, which can cause severe concerns for any company’s operations. As Confluence is widely used, many businesses could be vulnerable to exploitation. If threat actors gain access to sensitive data or compromise it in any way, companies may face immediate operational disruptions and long-term impacts on their financial condition. The costs associated with remediation, legal liabilities, and loss of business due to customer mistrust could be substantial. Furthermore, if cybercriminals successfully exploit the vulnerability, the financial implications could escalate rapidly, given the potential for ransomware deployment. Therefore, companies must be aware of these risks, as exploiting this vulnerability can significantly impact business continuity, operational integrity, and financial stability.
Source Material: Twitter(X), Shadowserver Foundation, & The DFIR Report
Latest Additions to Data Leak Sites
Manufacturing – Professional Scientific and Technical Services – Information – Construction – Transportation and Warehousing
Ransomware groups listed 46 organizations on their data leak sites in the past week, with over half from the USA. The Manufacturing sector was listed the most, followed by the Professional, Scientific, and Technical Services sector.
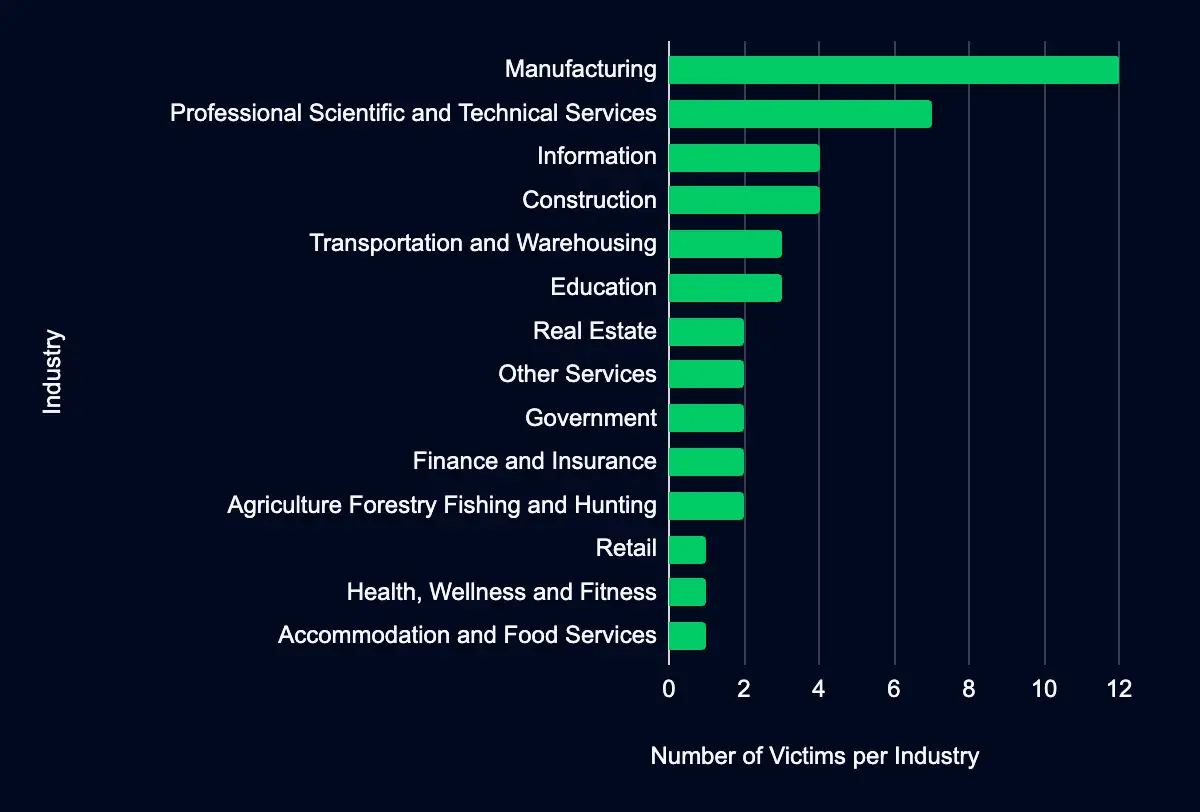
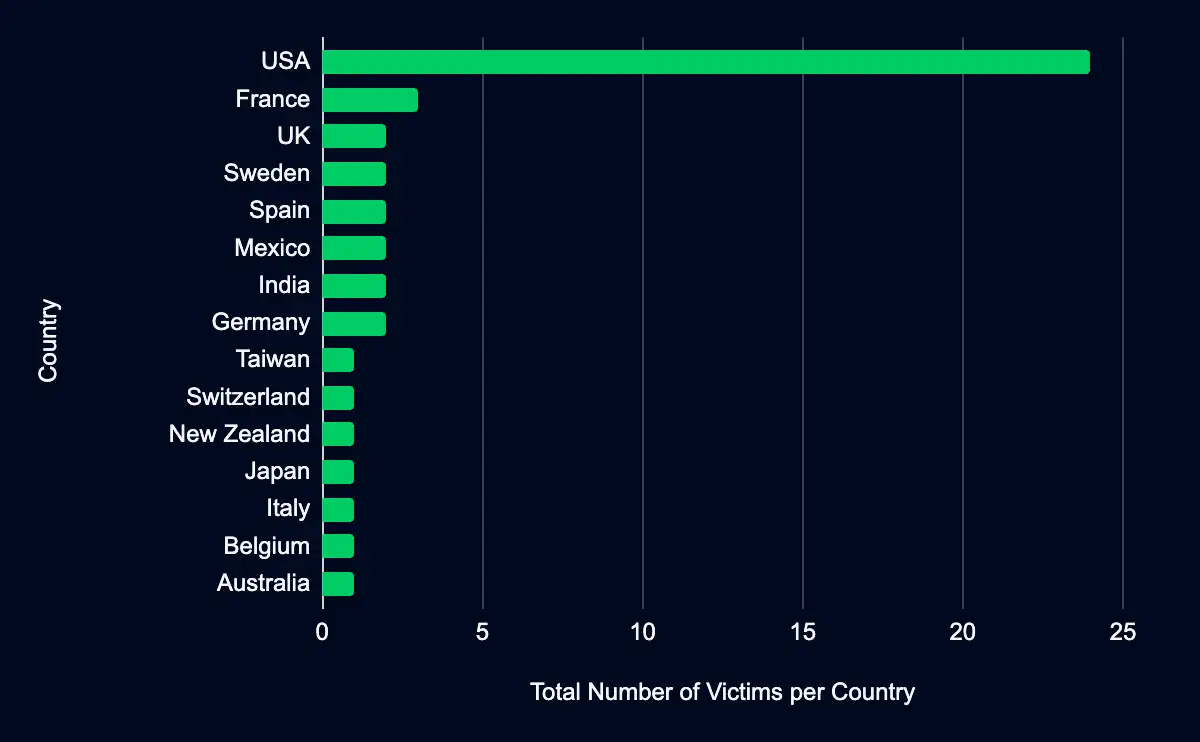
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. Forty-six organizations have been listed as victims in the past week, with a marked concentration in the USA, accounting for 52% of the total incidents. This geographic focus may indicate a higher targeting preference in this region. Regarding industry targeting, the data reveals a diverse range of sectors being affected, with manufacturing leading the list at 26%, followed by Professional, Scientific, and Technical Services (15%), Information (9%), Construction (9%), and Transportation and Warehousing (7%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base.
CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
Ivanti Endpoint Manager Mobile (EPMM) and MobileIron Core CVE-2023-35082 – VMware vCenter Server CVE-2023-34048 – Apple CVE-2024-23222
Within the past week, CISA added 3 CVEs (CVE-2023-35082, CVE-2023-34048, and CVE-2024-23222) to its Known Exploited Vulnerabilities catalog, impacting Ivanti, VMWare, and Apple products. Threat actors can exploit these vulnerabilities to perform remote code execution, authentication bypass, or code execution when processing maliciously crafted web content. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending that mitigative action be completed by February 8, 12, and 13.
Analytical findings are based on intelligence reporting from CISA. To corroborate and verify CISA’s reporting, we collect additional open-source reporting and internal data where possible. However, we cannot confirm all exploitation events nor fully determine the reliability and credibility of all open-source reporting used.
CVE-2023-35082
This vulnerability (CVE-2023-35082) impacting Ivanti Endpoint Manager Mobile (EPMM), formerly MobileIron Core, contains an authentication bypass vulnerability that allows unauthorized users to access restricted functionality or resources of the application. However, the risk of exploitation depends on the individual customer’s configurations. The vulnerability affects Endpoint Manager Mobile (EPMM) versions 11.8, 11.9, 11.10, and MobileIron Core versions 11.7 and below. Based on CISA’s data collection, this vulnerability has been exploited by ransomware threat actors. CISA has set a mitigation due date of 8 February.
Exploitation of CVE-2023-35082 allows a remote unauthenticated threat actor to access the API endpoints on an internet-exposed management server. A threat actor can use these API endpoints to perform various operations, including disclosing personally identifiable information (PII) and modifying the platform. Additionally, a threat actor could chain these vulnerabilities if a separate vulnerability is present in the API. For example, CVE-2023-35081 could be chained with CVE-2023-35082 to allow a threat actor to write malicious webshell files to the appliance.
Successful exploitation may result in an entry in the Apache HTTP logs showing a request to a targeted API endpoint containing /mifs/asfV3/API/v2/ in the URL path with an HTTP response code of 200. Blocked exploitation attempts will show an HTTP response code of either 401 or 403. Note that log entries containing /mifs/asfV3/api/v2/ in the path indicate exploitation of CVE-2023-35082, whilst log entries containing /mifs/aad/api/v2/ in the path indicate exploitation of CVE-2023-35078.
CVE-2023-34048
This vulnerability (CVE-2023-34048) impacting VMware vCenter Server results from an out-of-bounds write vulnerability in the implementation of the DCERPC protocol that allows a threat actor to conduct remote code execution. Based on CISA’s data collection, it’s unknown if ransomware threat actors have exploited this vulnerability. CISA has set a mitigation due date of 12 February.
According to Mandiant, A Chinese espionage group has exploited this vulnerability since late 2021. Based on their analysis, the actors exploit CVE-2023-34048 to deploy a backdoor. This backdoor allowed the actor to retrieve cleartext credentials for all ESXi hosts attached to the server. Then, using the compromised credentials, the actors logged in to ESXi hosts, deploying a backdoor. After the backdoor was dropped on the ESXi hosts, the actors connected directly to the hosts via the backdoor. Then, with access to the ESXi hosts via the backdoor, the actors exploited CVE-2023-20867 to allow for command execution and file transfer.
CVE-2024-23222
The final vulnerability (CVE-2024-23222) added this week impacts Apple’s WebKit in multiple Apple products and allows for code execution when processing maliciously crafted web content. Unfortunately, no further information is available on this exploitation. One possibility is threat actors creating malicious web content that, when viewed by the user, results in code execution, allowing the threat actor to deploy a coinminer or other malware. Based on CISA’s data collection, it’s unknown if ransomware threat actors have exploited this vulnerability. CISA has set a mitigation due date of 13 February.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomeware Campaign |
|---|---|---|---|---|---|
| CVE-2023-35082 | Ivanti | Endpoint Manager Mobile (EPMM) and MobileIron Core | Ivanti Endpoint Manager Mobile (EPMM) and MobileIron Core contain an authentication bypass vulnerability that allows unauthorized users to access restricted functionality or resources of the application. | 2/8/24 | Known |
| CVE-2023-34048 | VMware | vCenter Server | VMware vCenter Server contains an out-of-bounds write vulnerability in the implementation of the DCERPC protocol that allows an attacker to conduct remote code execution. | 2/12//24 | Unknown |
| CVE-2024-23222 | Apple | Multiple Products | Apple iOS, iPadOS, macOS, tvOS, and Safari WebKit contain a type confusion vulnerability that leads to code execution when processing maliciously crafted web content. | 2/13/24 | Unknown |
Source Material: CISA, Ivanti, VMWare, Apple, Rapid 7 (CVE-2023-35082), and Mandiant (CVE-2023-34048)
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share