Fake Website Impersonates Apple Apps, Midnight Blizzard Attacks Microsoft, Publicly-exposed RDP Gets Data Stolen and Ransomware in Three Hours
This week: we discuss a fake website targeting Apple computers catching victims, new details on the Microsoft attack by Midnight Blizzard, and a speedy exfiltration and ransomware technique. We also take a deeper look into the exploitation of Ivanti Connect Secure VPN and Ivanti Policy Secure. Lastly, we highlight the 70 new victims listed on data leak sites, and one important new CVE.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Stealer Targeting Apple Computers Spread Through Fake Websites Impersonating Apple Applications
- New Details Emerge in Midnight Blizzard’s Attack Against Microsoft
- Publicly Exposed RDP Leads to Data Exfiltration and Ransomware Deployment in 3 Hours
- Threat Actors Continue to Target Microsoft Teams to Deliver Malware
- New Details Emerge in UNC5221’s Exploitation of Ivanti Connect Secure VPN and Ivanti Policy Secure
- Latest Additions to Data Leak Sites
- CISA Adds CVE-2023-22527 to Known Exploited Vulnerabilities Catalog
Stealer Targeting Apple Computers Spread Through Fake Websites Impersonating Apple Applications
Malware – Atomic macOS Stealer – Stealer – Credential Theft – Data Theft – Malicious Websites – Industries/All
Threat Analysis
Threat actors have been distributing an updated version of Atomic macOS Stealer (AMOS) through malicious websites hosting fraudulent installers posing as genuine Mac applications, including Parallels Desktop, CleanMyMac, Arc Browser, and Pixelmato. While these malicious sites do not utilize SEO poisoning, there’s a possibility that threat actors may employ this technique in the future to target a larger audience. Furthermore, the developers have constantly refined it by adding multiple new features since its discovery in April 2023.
Atomic macOS Stealer (AMOS) exfiltrates sensitive data from multiple browsers, including auto-fills, passwords, cookies, and financial details from various wallets from Mac devices. However, AMOS goes beyond mere data theft. The developer of AMOS Stealer offers additional services for $3,000 a month, including a web panel, MetaMask brute-forcing, crypto checking, and a DMG installer. Notably, AMOS Stealer has joined the list of stealers that can revive expired cookies on Google Chrome.
Upon visiting a malicious website, downloading the file, and running it, a password prompt is presented to the user with a message requesting the system password. In addition to acquiring the system password, AMOS utilizes three system_profiler commands (SPSoftwareDataType, SPHardwareDataType, and SPDisplaysDataType) to generate a comprehensive report that includes information about software, hardware, and displays and subsequently saves it to a text file, employing a novel encryption method to conceal strings within the text file, decrypting and retrieving the actual strings dynamically at runtime.
The SPSoftwareDataType command retrieves data such as the macOS version, system software configuration, installed applications with versions, and information about software updates. The SPHardwareDataType command returns the Mac’s model, processor type and speed, memory specifications, storage information, and other hardware components. The SPDisplaysDataType command captures information about connected monitors, including their models and resolutions, graphics card details, and supported display modes.
Then, AMOS Stealer queries the /Cookies, /Network/Cookies, /Login Data, and /Web Data directories of Chromium-based browsers, such as Chrome, Safari, and Edge, on the victim’s system, looking for specific browser-related files to extract sensitive data. Additionally, the stealer executes a command to fetch the password linked to the label ‘Chrome’ from the macOS keychain, targeting the Google Chrome application.
Next, AMOS Stealer utilizes the fivenet() function to extract Mozilla Firefox data from the profile directory, including cookies, input history in web forms, cryptographic key data, and login and passwords for various websites. Subsequently, AMOS Stealer queries and reads files to extract information related to crypto-wallets, such as Electrum, Binance, and Exodus.
AMOS Stealer can also steal files using an AppleScript that utilizes the Finder application to organize and copy specific files to a folder named “fg” within the user’s home directory. The targeted files include Cookies.binarycookies from Safari’s Cookies folder and the note files NoteStore.sqlite, NoteStore.sqlite-shm, and NoteStore.sqlite-wal stored in the Notes folder. Additionally, the file grabber AppleScript scans through files on the Desktop and Documents folder, selectively copying files with the extensions txt, png, jpg, jpeg, wallet, keys, and key.
These file operations are subject to a cumulative size constraint of 10 megabytes, ensuring the “fg” folder’s total file size remains below 10 megabytes. Subsequently, all the gathered data is consolidated into a single directory. Following this, the stealer takes snapshots of the target’s computer and stores them in the same folder.
Finally, AMOS Stealer uses the sentdata() function to send the logs in a ZIP archive to the Command and Control (C2) server via port 80, employing the predefined UUID “1d67bafb-96d7-4864-aae0-e9854ff6db9b.” To date, all identified AMOS Stealer payloads used the same Command and Control (C2) server, previously reported by Malwarebytes on 10 January.
Risk & Impact Assessment
Atomic macOS Stealer presents a high risk, primarily by stealing credentials and sensitive data from browsers and crypto wallets. This capability significantly elevates the risk of unauthorized access and activities using compromised accounts, jeopardizing operational security and data confidentiality. Additionally, AMOS Stealer’s functionality to fetch comprehensive system profiles and access critical operational data compounds these risks. The data extraction capabilities of AMOS Stealer endanger user accounts and intellectual property, especially in sectors where proprietary data is a core asset. The risk level ranges from medium to high, depending on the nature of the stolen data and the operational context of the affected organization.
The implications of an AMOS Stealer infection are multifaceted and potentially severe. The immediate impacts include the likelihood of data theft, surveillance, and compromised operational security, which could reasonably lead to a material impact on a company’s business operations, results of operations, or financial condition. The loss of intellectual property and sensitive information leakage can result in long-term competitive disadvantages, financial losses, and erosion of customer trust. Additionally, the stealthy nature of the stealer may complicate detection and mitigation efforts, necessitating substantial resources for response and recovery. The broader implications of such an infection underscore the need for robust cybersecurity measures and heightened vigilance in organizational data protection strategies.
Source Material: Cyble, Uncovering Atomic Stealer (AMOS) Strikes and the Rise of Dead Cookie Restoration
New Details Emerge in Midnight Blizzard’s Attack Against Microsoft
Threat Actor – Password Spray – OAuth Abuse – Residential Proxy Network – Midnight Blizzard – Public Administration – Other Services – Information – Professional, Scientific, and Technical Services
Threat Analysis
On 12 January, Microsoft detected a nation-state attack on their corporate systems, identifying the threat actor as Midnight Blizzard, a Russian state-sponsored actor. The attack did not result from a vulnerability in Microsoft products or services. Currently, there is no evidence that Midnight Blizzard gained access to Microsoft customer environments, production systems, source code, or AI systems.
High-level Overview of Activity
- Launched password spray attacks from a residential proxy network to compromise accounts.
- Leveraged compromised accounts to access OAuth applications.
- Created new OAuth applications and a user account.
- Granted the user account access to mailboxes by assigning the Office 365 Exchange Online full_access_as_app role.
- Leveraged malicious OAuth applications to access mailboxes to identify information about themselves.
Initial Access
Based on current findings, starting in late November 2023, Midnight Blizzard operators used password spray attacks that successfully compromised a legacy, non-production test tenant account that did not have multifactor authentication (MFA) enabled. In this observed activity, the operators launched the attacks from a distributed residential proxy network, routing their traffic through many IP addresses used by legitimate users and restricting the number of password spray attack attempts and the accounts targeted.
Persistence
Leveraging their initial access, the operators identified and compromised a legacy test OAuth application with elevated access to the Microsoft corporate environment. Midnight Blizzard operators then created additional malicious OAuth applications and a new user account, granting consent to these malicious OAuth applications. They then used the legacy test OAuth application to grant them access to mailboxes by assigning the Office 365 Exchange Online full_access_as_app role.
Collection
Midnight Blizzard leveraged these malicious OAuth applications to authenticate to Microsoft Exchange Online and target Microsoft corporate email accounts, including members of their senior leadership team and employees in their cybersecurity, legal, and other functions, exfiltrating emails and attached documents. Based on the data accessed, Midnight Blizzard operators aimed to identify information about themselves.
Midnight Blizzard (APT29, UNC2452, and Cozy Bear) is a Russia-based threat actor attributed by the US and UK governments to the Foreign Intelligence Service of the Russian Federation (SVR). Midnight Blizzard primarily targets US and European governments, diplomatic entities, non-governmental organizations (NGOs), and IT service providers. Dating back to early 2018, they focus on collecting intelligence through longstanding and dedicated espionage of foreign interests. Midnight Blizzard is consistent and persistent in its operational targeting, and its objectives rarely change. Midnight Blizzard’s intelligence-gathering activities leverage various initial access, lateral movement, and persistence techniques to collect information supporting Russian foreign policy interests.
Their operations often utilize diverse initial access methods ranging from stolen credentials to supply chain attacks, exploitation of on-premises environments to laterally move to cloud environments, and exploitation of service providers’ trust chains to gain access to downstream customers. Midnight Blizzard is adept at identifying and abusing OAuth applications to move laterally across cloud environments and for post-compromise activity, such as email collection.
Risk & Impact Assessment
Midnight Blizzard presents significant organizational risks through its strategic initial access, persistence, and data collection methods. This actor’s capability to execute password spray attacks using a residential proxy network demonstrates their adeptness in evading detection and bypassing standard security measures like account lockout policies. The use of legacy, non-production test accounts lacking multifactor authentication (MFA) further underscores vulnerabilities in even well-secured environments.
Once initial access is established, Midnight Blizzard’s exploitation of OAuth applications for persistence highlights their advanced capability to maintain prolonged access within a network. This persistence is critical in enabling continuous data collection and reconnaissance activities, targeting sensitive corporate information. The group’s focus on high-value targets’ email accounts indicates a clear and present risk to sensitive internal communications.
The consequences could be extensive and multifaceted if Midnight Blizzard successfully executes their attack, resulting in the access and collection of critical internal communications and documents. This unauthorized access could lead to comprehensive surveillance, jeopardizing operational security and the confidentiality of strategic plans and discussions. There is also a risk to defensive measures, which could have long-term detrimental effects on cybersecurity. The broader implications of such an attack extend beyond immediate data loss, potentially compromising the trust and reliability of services, thus impacting customer confidence.
Given the nature of the attack and the targeted data, it is reasonably likely that a successful breach by Midnight Blizzard could materially impact an organization’s financial condition. The attack’s success will likely result in re-evaluating security protocols and infrastructure, necessitating considerable investment in cybersecurity enhancements. Additionally, there could be an impact on an organization’s reputation, and some organizations could face legal repercussions.
Source Material: Microsoft Threat Intelligence, Midnight Blizzard: Guidance for responders on nation-state attack
Publicly Exposed RDP Leads to Data Exfiltration and Ransomware Deployment in 3 Hours
Ransomware – Trigona Ransomware – RDP Exploitation – Netscan Tool – Lateral Movement – Rclone – Mega.io – Data Exfiltration – Credential Misuse – Industries/All
Threat Analysis
The DFIR Report observed a threat actor exploiting a publicly exposed Remote Desktop Protocol (RDP) host on one of their honeypots in late December 2022, leading to data exfiltration and the deployment of Trigona ransomware. Interestingly, the threat actor deployed several scripts but did not execute them, opting instead for RDP connections. The intrusion began when the threat actor accessed an exposed RDP host using valid credentials. Due to limited evidence, The DFIR Report could not pinpoint the actor’s initial access method.
Upon gaining access, the threat actor executed several discovery commands, such as whoami.exe, and deployed their arsenal onto the initial compromised host. The threat actor used the compromised RDP connection to deploy their arsenal, which included various batch scripts, executables, and the SoftPerfect Netscan tool. Two unused scripts enabled the creation of a new local user and adds it to the local administrators and Remote Desktop Users groups.
Approximately 20 minutes after initial access, the threat actor began lateral movement by establishing an RDP connection to one of the file servers. The threat actor then copied their toolkit to the file server. Following this, the threat actor staged Rclone on the initial compromised host, establishing several RDP connections to file and backup servers. Again, the actor did not use deployed batch scripts, including a tool named Remote Desktop Plus, opting for RDP connections.
Two other batch files, DefenderOFF.bat and DefenderON.bat, were designed to disable security tooling. The first script contained several registry entries intended to disable the built-in Windows Defender. The second script would reverse the changes and re-enable Windows Defender. Again, the threat actor did not execute these scripts; instead manually running some of the commands (or similar commands) on the system to disable defenses.
After disabling defenses, the threat actor-initiated network scans employing a highly customized version of Netscan, using a configuration file (netscan.xml) with pre-configured custom “Applications” referencing batch scripts and binaries dropped in the initial tool drop. The actor used Netscan as a centralized command tool to automate many actions, including removing Antivirus, adding new users, and modifying the firewall, all using PSEXEC. The copied netscan.xml also included recent scan histories. Additionally, two files in the tool drop appear to be output scans from previous intrusions unrelated to this incident. As Netscan enumerated the network, the threat actor identified network shares and explored them, accessing various documents through a web browser and using MS Paint to review image files on a remote system.
The threat actor then used RDP to drop two batch scripts to the Administrator’s Music folder on the initial compromised host and one of the file servers. Upon execution, these two batch scripts execute Rclone to exfiltrate files from the victim file shares. The threat actor used the Mega.io service as the remote exfiltration location for the stolen files.
Approximately 45 minutes after the data extraction, the threat actor altered their Remote Desktop Protocol (RDP) connection. They logged out and then logged in to the initial compromised host from a different IP address. Although the new IP and hostname deviate from the initial entry, it is essential to note that the threat actor possessed extensive knowledge of the network. They engaged with the previously compromised hosts and employed identical techniques as previously observed.
Both file share servers received the same Windows Defender disabling treatment as the initial compromised host. The threat actor also established an RDP connection with a backup server and executed the same Windows Defender disabling commands. The threat actor then, approximately two hours and 49 minutes after the initial access, staged a Trigona Ransomware binary (build_redacted.exe, it is not clear if this is the actual filename or if the file name included a name that can not be publicly disclosed) on each host they had access to. Following this, they initiated the ransomware binary on each host through their RDP sessions. The ransomware also initiated SMB connections to remote hosts, encrypting them as well. Consequently, the victim faced a dual extortion impact, encompassing both the exfiltration of sensitive data and the encryption of systems.
Risk & Impact Assessment
The deployment of Trigona Ransomware by the threat actor presents multifaceted organizational risks. Initially, the threat actor’s ability to gain access via an exposed RDP host using valid credentials demonstrates a critical susceptibility in network security protocols and access management. This susceptibility allowed unauthorized access and facilitated subsequent defense evasion tactics. The actor’s adeptness in lateral movement further underscores the risk of insufficient internal network segmentation and monitoring. The deployment of tools for data exfiltration signifies a high risk of sensitive data compromise, leading to potential breaches of confidentiality. Additionally, using ransomware for system and data encryption highlights a severe threat to data integrity and availability. These factors – from initial access to data encryption – cumulatively amplify the organizational risk.
Should an attack of this nature be successful, the consequences could be dire and multifaceted. The likelihood of data theft is high, considering the threat actor’s demonstrated capability in data exfiltration. Such a breach could expose sensitive organizational and client data, posing risks of identity theft, financial fraud, and reputational damage. The potential for ongoing surveillance within the network raises concerns about compromised operational security, leading to continuous unauthorized access to critical systems.
Furthermore, the encryption of systems and data disrupts business operations and could have severe implications. Given these factors, it is reasonably likely that a successful attack would cause a material impact on the company’s business operations, results of operations, or financial condition. The potential for substantial financial losses, cost of remediation efforts, and potential legal liabilities underscores the critical need for enhanced cybersecurity measures and vigilant monitoring to mitigate such threats.
Source Material: The DFIR Report, Buzzing on Christmas Eve: Trigona Ransomware in 3 Hours
Threat Actors Continue to Target Microsoft Teams to Deliver Malware
Phishing – Malware – DarkGate – Microsoft Teams Phishing – Command and Control Communication – Industries/All
Threat Analysis
A threat actor sent over 1,000 Microsoft Teams messages to several internal members of an unidentified organization, generating a “MessageSent” Teams event for each message sent. The malicious messages came from an external user using the domain “.onmicrosoft.com.” This domain appears to be authentic, and open-source research on the domain shows no reports of suspicious activity. Although these “MessageSent” Teams events do not include the IDs of the recipients, they do include the external user’s tenant ID. This tenant ID generated multiple “MemberAdded” events, which are generated when a user joins a chat in Teams.
These “MemberAdded” events identify recipients by their user ID but do not list the external user ID. However, these “MemberAdded” events contain a “ChatThreadId” field, which is also listed in the original “MessageSent” event. Three of the users who accepted the external chat downloaded a suspicious double extension file titled “Navigating Future Changes October 2023.pdf.msi.”
The malicious file, “Navigating Future Changes October 2023.pdf.msi”, attempted to beacon out to the domain hgfdytrywq[.]com, which, according to Palo Alto Networks, was confirmed to be a command-and-control (C2) domain for DarkGate in mid-October 2023. Additionally, the filename has a similar naming pattern to those listed by Palo Alto Networks, and DarkGate is known to use the double-extension file tactic.
While it’s unknown what actions the malicious file performs, based on the communication with a known DarkGate C2 server, it likely will result in a DarkGate infection. DarkGate is a malware first documented in 2017 but became more widely available to cybercriminals in the summer of 2023. It is a sophisticated modular malware that can perform various malicious actions, including keylogging, cryptocurrency mining, reverse shell, clipboard theft, and information stealing. It can download and execute files to memory, has a Hidden Virtual Network Computing (HVNC) module, and can escalate privileges. DarkGate is typically distributed through phishing campaigns and malvertising. DarkGate has been linked to several ransomware attacks, including Alphv, Lockbit, Akira, Snatch, Bianlian, Medusa, and the Everest ransom team.
Risk & Impact Assessment
The recent phishing campaign utilizing Microsoft Teams as a vector represents a significant organizational risk, primarily due to the trusted nature of the communication platform. The ability of the threat actor to infiltrate internal communications via seemingly legitimate Teams messages underscores a critical vulnerability in operational security. Utilizing the “.onmicrosoft.com” domain adds to the complexity, leveraging perceived authenticity to bypass standard security measures. While this is not a new vector for DarkGate, it is particularly alarming if External Access is enabled. Given DarkGate’s modular capabilities – including keylogging, data exfiltration, and reverse shell – the malware’s potential for follow-on malicious activity, including ransomware, within the organization’s network infrastructure poses a severe threat. It can lead to sustained information theft, undetected network presence, and potential lateral movement, compromising multiple facets of the organization’s digital environment.
Should the DarkGate attack achieve its objectives, the consequences could be multifaceted and severe. The likelihood of data theft is high, with sensitive information at risk. Surveillance capabilities in the malware could lead to ongoing operational security compromises, with long-term implications for business integrity and trust. The modular nature of DarkGate, capable of executing diverse malicious actions, raises the risk to compromised systems, including the exfiltration and encryption of systems and data. The potential impact on the company’s business operations is substantial, with risks ranging from operational disruptions, financial losses due to response measures and potential fines, to long-term reputational damage. If the attack is not promptly and effectively contained, it could materially impact the organization’s results of operations and financial condition, especially if critical data is exfiltrated or irretrievably lost.
Source Material: AT&T Cybersecurity, DarkGate malware delivered via Microsoft Teams – detection and response
New Details Emerge in UNC5221’s Exploitation of Ivanti Connect Secure VPN and Ivanti Policy Secure
Vulnerability Exploitation – Malware – Web Shell – Backdoor – Credential Stealer – Threat Actor – Ivanti Connect Secure CVE-2023-46805 and CVE-2024-21887 – CHAINLINE – BUSHWALK – LIGHTWIRE – FRAMESTING – ZIPLINE – WARPWIRE – IMPACKET – CRACKMAPEXEC – IODINE – ENUM4LINUX – UNC5221 – Industries/All
Threat Analysis
In Mandiant’s ongoing investigation into the exploitation of Ivanti Connect Secure VPN (CS, formerly Pulse Secure) and Ivanti Policy Secure (PS) appliances by UNC5221, they have published their most recent findings.
It is now known that after the initial exploitation of an appliance, UNC5221 leveraged a custom web shell that is being tracked as CHAINLINE. CHAINLINE is a Python-based web shell backdoor embedded in an Ivanti Connect Secure Python package that enables arbitrary command execution. CHAINLINE was found in the CAV Python package in the path /home/venv3/lib/python3.6/site-packages/cav-0.1-py3.6.egg/cav/api/resources/health.py, the same Python package modified to support the WIREFIRE web shell.
Unlike WIREFIRE, which modifies an existing file, CHAINLINE creates a new file called health.py, which is not a legitimate filename in the CAV Python package. UNC5221 also registered a new API resource path to support the access of CHAINLINE at the REST endpoint /api/v1/cav/client/health.
UNC5221 Also employed a mitigation bypass technique that led to the deployment of a custom webshell tracked as BUSHWALK. Successful exploitation would bypass the initial mitigation provided by Ivanti on 10 January 2024. After deploying BUSHWALK, the threat actor cleaned up their activity and restored the system to a clean state.
In addition to the BUSHWALK web shell, UNC5221 operators also deployed a variant of the LIGHTWIRE web shell that inserts itself into a legitimate component of the VPN gateway. The new variant uses the same GET parameters as the original LIGHTWIRE sample described in their first blog post.
An additional web shell was identified that is being tracked as FRAMESTING. FRAMESTING is a Python web shell embedded in an Ivanti Connect Secure Python package that enables arbitrary command execution. FRAMESTING was identified in the CAV Python package in the path /home/venv3/lib/python3.6/site-packages/cav-0.1-py3.6.egg/cav/api/resources/category.py, the same Python package modified to support the WIREFIRE and CHAINLINE web shells.
When installed, the threat actor can access the FRAMESTING web shell at the REST endpoint /api/v1/cav/client/categories with a POST request. The web shell employs two methods of accepting commands. It first attempts to retrieve the command stored in the value of a cookie named DSID from the current HTTP request. If the cookie is not present or is not the expected length, it will attempt to decompress zlib data within the request’s POST data. Lastly, FRAMESTING will pass the decrypted POST data into a Python exec() statement to dynamically execute additional Python code.
Based on Mandiant’s continuing analysis of the ZIPLINE passive backdoor, ZIPLINE communicates with its C2 server using a custom stateful binary protocol. The communication begins with the C2 server connecting to the compromised host and sending a message. Within the message is the structure of a signature. This signature is expected to be the string SSH-2.0-OpenSSH_0.3xx, followed by a structure that contains data for AES-128 and HMAC key generation. Next, the C2 sends an encrypted message that, once decrypted, follows a predefined structure. Although the message structure is designed to be flexible, this instance of the malware expects the first message to specify a length of 0x10. The commands the ZIPLINE backdoor can execute include uploading and downloading a file, creating a reverse shell or Proxy Server, or implementing a Tunneling Server.
Mandiant has identified multiple new variants of WARPWIRE credential stealer. Across these variants, their primary purpose has remained to exfiltrate plaintext passwords and usernames to a hard-coded C2 server. The main variation across these variants is how credentials are sent to the hard-coded C2. In most identified variants, a POST request that submits the credentials in either the POST params or body has replaced the GET request. However, some variants still utilize a GET request but now include the window.location.href as a submitted value.
Furthermore, the threat actors have used various open-source tools, including IMPACKET, CRACKMAPEXEC, IODINE, and ENUM4LINUX, to support post-exploitation activity on Ivanti Connect Secure VPN appliances. These tools are associated with internal network reconnaissance, lateral movement, and data exfiltration within a limited number of victim environments.
The threat actors used the built-in dsls command found on Connect Secure VPN appliances, executing a sequence of commands consistent with dumping the running configuration and cache after the initial exploitation of a Connect Secure VPN appliance. The actors saved the resulting output to a tar archive masquerading as a randomly generated 10-character CSS file within the directory /home/webserver/htdocs/dana-na/css/.
After the threat actor downloaded the configuration and cache dump from the server, they executed a sequence of commands by exploiting CVE-2023-46805 and CVE-2024-21887 to remove evidence of compromise. The command sequence deleted the staged configuration and cache dump. Then Timestomps the CSS directory with the modified and access timestamps of /tmp/testt. They then cleared the config_rest_server.log file of records showing exploitation attempts of CVE-2023-46805 and CVE-2024-21887. Then, remounted the file system in read-only mode, reverting it to its original state.
The threat actors also exfiltrated the CAV web server logs, staging them in /runtime/webserver/htdocs/dana-na/help/logo.gif. The threat actors executed a sequence of commands that redirects the GIF header into logo.gif and then appends the Base64-encoded contents of /data/var/dlogs/cav_webserv.log into the same file. The cav_webserv.log contains web requests and logs uWSGI maintains for the CAV REST API. Additionally, the threat actors made multiple modifications to the associated CAV Python package, including web shells such as WIREFIRE, CHAINLINE, and FRAMESTING.
The threat actors also manipulated the internal Integrity Checker Tool (ICT) by modifying the manifest file at /home/etc/manifest. The manifest file lists the system’s expected files and associated SHA256 hash. The internal ICT verifies the manifest file’s signature using a public key. In some instances, the threat actor failed to create a new digital signature of the manifest file, causing the internal ICT to fail and generate event ID SYS32042 in the system event log, indicating that the manifest file is bad.
Sometimes, the threat actor used logClear.pl, a legitimate system utility, to clear system logs (events, admin, access, diagnosticlog, policytrace, and sensorslog), generating event ID ADM20599 in the admin event log for each log type cleared.
Risk & Impact Assessment
The risks posed by the exploitation of Ivanti Connect Secure VPN and Ivanti Policy Secure appliances highlight a multifaceted threat landscape. Factors contributing to the heightened risk profile include vulnerability exploitation, deployment of multiple web shells such as CHAINLINE, BUSHWALK, LIGHTWIRE, and FRAMESTING, and bypassing existing security mitigations. These tactics indicate a high level of adversary sophistication and suggest that the affected organizations face significant risks of unauthorized access and persistence within their networks. The use of custom web shells and the execution of arbitrary commands elevate the risk of lateral movement, further entrenchment, and escalation of privileges, complicating detection and remediation efforts.
The possible consequences of a successful attack extend beyond immediate data theft to include long-term surveillance, compromised operational security, and potential breaches of sensitive intellectual property. The likelihood of these outcomes is alarmingly high, given the threat actor’s demonstrated capability to maintain stealth and bypass mitigation efforts. Organizations affected by these exploits are at risk of material impacts on their business operations, including disruption of critical services, erosion of customer trust, and potential financial liabilities stemming from regulatory fines or litigation.
Furthermore, the strategic targeting of Ivanti Connect Secure VPN and Ivanti Policy Secure appliances underscores the broader implications for security and infrastructure resilience. In sum, the success of this activity is not only reasonably likely but also poised to cause significant material impact on the affected companies’ operational and financial conditions.
Source Material: Mandiant, Cutting Edge, Part 2: Investigating Ivanti Connect Secure VPN Zero-Day Exploitation
Latest Additions to Data Leak Sites
Manufacturing – Professional Scientific and Technical Services – Information – Construction – Transportation and Warehousing
Analysis
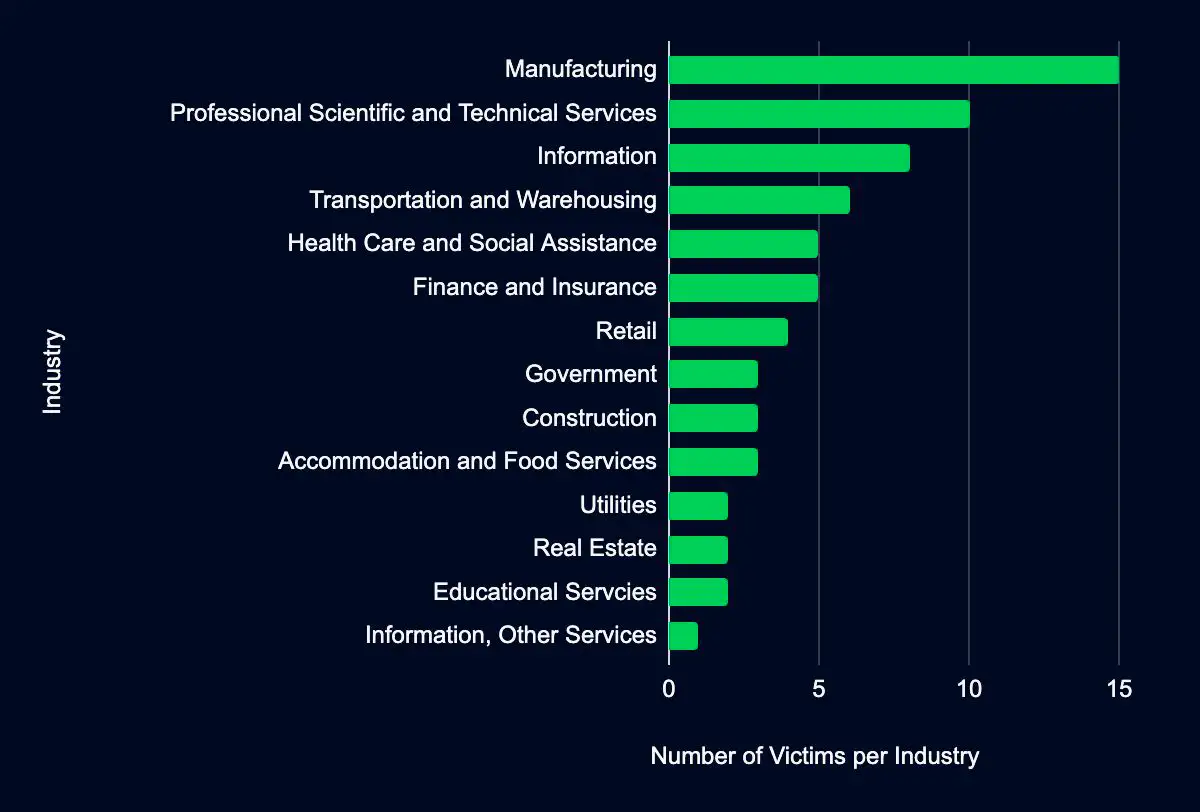
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. Seventy organizations have been listed as victims in the past week, with a marked concentration in the USA, accounting for 69% of the total incidents. This geographic focus may indicate a higher targeting preference in this region due to the large base of potential victims.
Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Manufacturing leading the list at 21%, followed by Professional Scientific and Technical Services (14%), Information (11%), Transportation and Warehousing (9%), and Health Care and Social Assistance (7%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base.
Black Basta, accounting for 20% of the incidents in the dataset, predominantly targeted organizations in the USA but also had victims in the UK, New Zealand, Japan, France, and Canada. While a notable number of their attacks are in the USA (7), their affiliate base likely accounts for their extensive geographical reach. The spectrum of industries Black Basta targets is equally varied, extending beyond Manufacturing, Utilities, and Finance and Insurance to encompass sectors such as Transportation and Warehousing, Professional Scientific and Technical Services, Information, Construction, and Accommodation and Food Services. This variety in targets underscores Black Basta affiliates’ opportunistic and versatile approach, possibly driven by the availability of opportunities across sectors.
8base, accounting for 11% of the incidents in the dataset, shows a somewhat diverse targeting pattern but not entirely without geographic or sector preferences. 8base’s targets include organizations primarily in France, indicating that 8base focused on this country. 8base’s victims were predominantly in Professional Scientific and Technical Services. However, they also had victims in the Manufacturing and Retail, Educational Services, and Agriculture, Forestry, Fishing, and Hunting sectors. This data suggests that while 8base is opportunistic, there is a slight inclination towards specific industries and regions.
For instance, their recent activities in France and their focus on the Professional Scientific and Technical Services sector indicate a strategy that balances opportunism with selective targeting, possibly influenced by the perceived value of data or the ability to pay ransom. Their activities still underscore the unpredictable nature of ransomware groups, but with a nuanced approach that considers both opportunity and potential payoff.
The activities of Medusa, Lockbit, Hunters International, and ALPHV account for almost 37% of the total incidents, offering valuable insights into the diversity of the ransomware threat landscape. Medusa and Lockbit exhibit a focused but dispersed approach, with all victims predominantly in the USA in industries such as Information, Transportation and Warehousing, and Manufacturing. This pattern suggests a focus on a specific geographic area but opportunistic in their sectoral preference, pointing towards a strategy that might prioritize opportunistic or easy targets over any particular industry or region.
Hunters International and ALPHV, collectively behind 12 of the 70 victims, highlight the role of consistently active players in the ransomware arena. Hunters International and ALPHV victims are predominantly in the USA and operate in Manufacturing and Professional Scientific and Technical Services. This pattern continues their historical preference for this geographical region and sectors, suggesting a focused targeting strategy, pointing towards a strategy that might prioritize these industries.
CISA Adds CVE-2023-22527 to Known Exploited Vulnerabilities Catalog
Atlassian Confluence Data Center and Server CVE-2023-22527
Within the past week, CISA added CVE-2023-22527 to its Known Exploited Vulnerabilities catalog, impacting the Atlassian Confluence Data Center and Server. Numerous outlets have reported that threat actors scan for vulnerable Atlassian Confluence Data Center and Server instances and exploit this vulnerability to perform remote code execution. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending that mitigation action be conducted by 14 February 2024.
Vulnerability CVE-2023-22527 impacts the Atlassian Confluence Data Center and Server, and it is unclear if it has been associated with any ransomware attacks. Organizations with vulnerable instances are at risk of remote code execution if successfully exploited.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
- Ensure Atlassian Confluence Data Center or Confluence Server is updated to the latest version.
- Ensure web access logs are being ingested for all critical internet-exposed servers, especially Atlassian Confluence Data Center and Confluence Server.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomeware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-22527 | Atlassian | Confluence Data Center and Server | Atlassian Confluence Data Center and Server contain an unauthenticated OGNL template injection vulnerability that can lead to remote code execution. | 2/14/2024 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share