Behind the CAPTCHA, Beyond the Flood: Interlock RAT, Record DDoS Attacks, and Citrix Exploits Shape the Mid-Year Threat Landscape
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Behind the CAPTCHA: Unmasking Interlock RAT’s Latest Tactics
The Rundown
Researchers from The DFIR Report, working with Proofpoint, have identified a new version of the Interlock RAT (Remote Access Trojan), a tool used by cybercriminals to remotely control infected systems. Unlike earlier JavaScript-based versions, this new variant uses PHP and has been distributed widely since May 2025. The malware spreads through websites compromised with hidden scripts that redirect visitors into a fake “human verification” process. Victims are tricked into running malicious PowerShell commands, which eventually install the PHP-based RAT onto their machines.
Once installed, the RAT executes with stealth and sophistication. It collects a wide range of system information, including software, services, user roles, drives, and network details all packaged into JSON data and sent back to the attackers. The RAT can interactively explore the environment further and even identify backup-related systems. It abuses legitimate services like Cloudflare Tunnels for its command and control operations, masking its activity and maintaining reliable access. It also uses hardcoded backup servers to ensure resilience if the primary channel is interrupted.
The malware grants attackers full control, allowing them to download and execute files, run shell commands, and ensure the RAT remains active by embedding itself into the system’s startup processes. The campaign shows evidence of hands-on keyboard activity, meaning attackers directly interact with compromised systems and even move laterally via RDP (Remote Desktop Protocol). This evolving threat targets multiple industries indiscriminately and showcases the Interlock group’s growing technical sophistication, particularly in blending social engineering with layered malware deployment and stealthy persistence tactics.
Source Material: The DFIR Report
Record-Breaking DDoS Attacks Define Q2 2025 Cyber Threat Landscape
The Rundown
In Q2 2025, Cloudflare observed a record-breaking surge in Distributed Denial of Service (DDoS) attacks, blocking more attacks in the first quarter than in all of 2024. Network-layer attacks increased by over 500% year-over-year, with HTTP-layer attacks rising by 118%. A significant portion of these attacks targeted Cloudflare itself in a sustained 18-day campaign, demonstrating the growing scale and persistence of malicious actors aiming to disrupt internet services.
The report highlights an alarming increase in hyper-volumetric attacks, those exceeding 1 Tbps or 1 billion packets per second. In Q2 alone, Cloudflare mitigated hundreds of these extreme events, including one that peaked at 7.3 Tbps, the largest in internet history. These incidents illustrate the capability of attackers to launch short, high-intensity bursts of traffic capable of overwhelming unprotected systems in seconds.
Despite the prominence of massive attacks, most DDoS events remain small in size but are still dangerous due to their ability to cripple systems that lack sufficient defense. The majority of attacks last less than 10 minutes, making manual response infeasible. Cloudflare’s findings emphasize the need for automated, always-on mitigation tools. For businesses, investing in proactive and scalable DDoS protection is essential to maintain service continuity and protect brand integrity in the face of increasingly sophisticated threats.
Source Materials: Cloudflare
Ransomware and Data Extortion Trends (July 8-14)
The Rundown
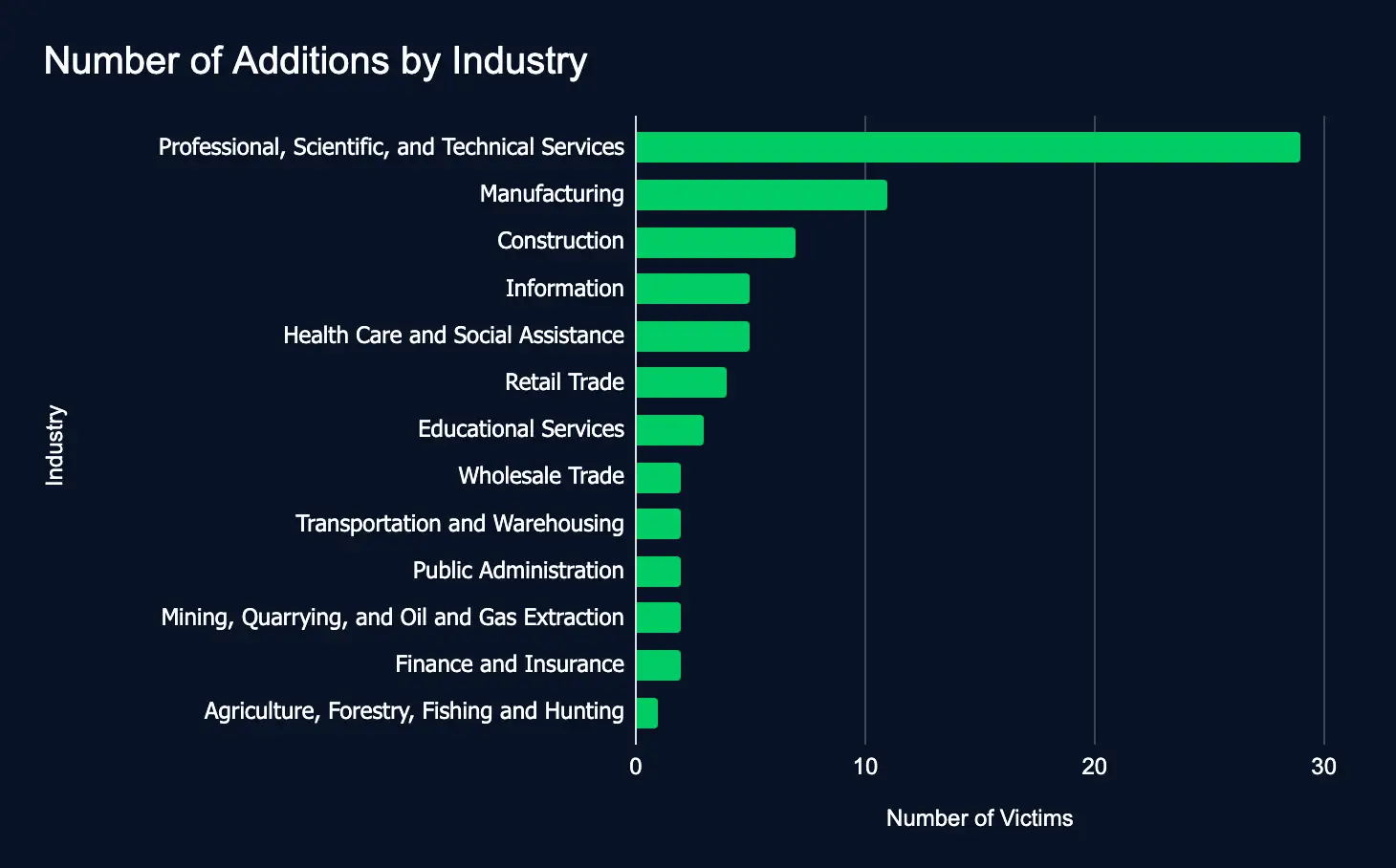
Between July 8 and 14, ransomware and data extortion activity increased, with 75 victim organizations reported across 16 leak sites, a 17% increase from the previous week’s total of 64. While this increase may suggest a small uptick, it more likely reflects a short-term stabilization in threat actor operations rather than a meaningful increase in overall attack volume.
Key sectors such as Professional Services, Manufacturing, and Construction remained prime targets, emphasizing ongoing focus on high-value industries. A notable share of impacted organizations were based in strategic regions, including the United States, Canada, and Brazil, indicating that geographic targeting remains a consistent priority. For business leaders, these trends reinforce the persistent, calculated nature of ransomware threats. Despite fluctuations in weekly figures, the risk to critical sectors remains high, underscoring the need for ongoing investment in prevention, detection, and incident response capabilities.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Construction
- Most affected countries:
- United States
- Canada
- Brazil
- Most active leak sites:
- INC Ransom
- Play
- Akira
Exploited Vulnerabilities in Citrix and Wing FTP Products Added to CISA’s Catalog
The Rundown
Between July 10 and July 16, CISA added two high-severity vulnerabilities affecting Citrix and Wing FTP products to its Known Exploited Vulnerabilities (KEV) catalog, confirming their exploitation in active threat campaigns targeting diverse systems.
If left unpatched, these flaws present serious security risks by enabling attackers to gain initial access and potentially escalate their intrusion. Given the widespread adoption of these technologies across various sectors, successful exploitation could result in major operational disruptions and reputational harm.
With mounting interest from both state-sponsored and financially motivated threat actors, swift remediation is essential. Any delay in addressing these vulnerabilities significantly increases the risk of compromise and the potential for broader organizational and business impacts.
Citrix | NetScaler ADC and Gateway CVE-2025-5777
- Vulnerability Description: Citrix NetScaler ADC and Gateway contain an out-of-bounds read vulnerability due to insufficient input validation. This vulnerability can lead to memory overread when the NetScaler is configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) OR AAA virtual server.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-10
- Recommended Mitigation Due Date: 2025-07-11
Wing FTP Server | Wing FTP Server CVE-2025-47812
- Vulnerability Description: Wing FTP Server contains an improper neutralization of null byte or NUL character vulnerability that can allow injection of arbitrary Lua code into user session files. This can be used to execute arbitrary system commands with the privileges of the FTP service (root or SYSTEM by default).
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-07-14
- Recommended Mitigation Due Date: 2025-08-04
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share